
Comparitech researchers have identified multiple vulnerabilities that could increase the impact of a phishing attack on all Windows users running up to and including Windows 10 – despite previously being patched by Microsoft.
Vulnerabilities reported to be exploited by Chinese state-sponsored espionage group APT41.
What is the issue?
Comparitech researchers uncovered multiple security vulnerabilities on Windows 10 that can be exploited through Microsoft’s help documentation file extension and the programs used to open them.
Attackers can trick Windows users into downloading and opening malicious files through, for example, an email link or attachment. Windows’ default program used to open these files will execute code stored in the file, which can be used to launch an attack.
Help documentation on a Windows device was originally stored in compiled HTML files (CHM), denoted by the .chm file extension.
When you clicked on the “Help” option in a program, it would load help documentation in a viewer similar to a web browser complete with search, an index, and other navigation tools.
Microsoft now considers .chm files to be potentially dangerous. In fact, they are blocked by Outlook, Microsoft’s email client.
But there is one program that exists on nearly every Windows machine that still opens .chm files, and this is where our researchers focused their investigation. A program called HtmlHelper, which runs under the process name hh.exe, can open and execute CHM files. Unless you’ve altered your default programs, when you click on a CHM file, HtmlHelper will open and render it using Internet Explorer 7.
Attackers can place malicious content inside a CHM file and trick victims into opening it. HtmlHelper contains several vulnerabilities and bypasses many of Windows 10’s security policies, according to our research. Researchers confirmed such attacks work on all modern Windows operating systems including the latest version of Windows 10 as of the time of writing.
What is the threat?
Attackers could remotely log into your Windows PC and enjoy unfettered access. In a worst case scenario this could mean cybercriminals…
- Rifle through your personal and work files – opening yourself up to identity theft, blackmail or sextortion
- Use ransomware to lock you out
- Plant malware such as a keylogger to potentially unlock access to services like your online banking
- Hijack your machine and use for nefarious purposes such as cryptojacking
- Launch further attacks within your network and distribute malware to your contacts
Are hackers abusing HtmlHelper and CHM files?
Yes!
Malicious CHM files have been used by several major hacking groups and advanced persistent threat (APT) organizations.
Notably, APT41 from China has targeted organizations in at least 14 countries. They are a state-sponsored threat actor that routinely uses spear phishing and infected CHM files to compromise victims. Their targets include the healthcare, telecom, and high tech sectors, and their goal is often to steal intellectual property.
It’s not just major hacking groups and high-profile targets though; the use of malicious CHM files are well documented.
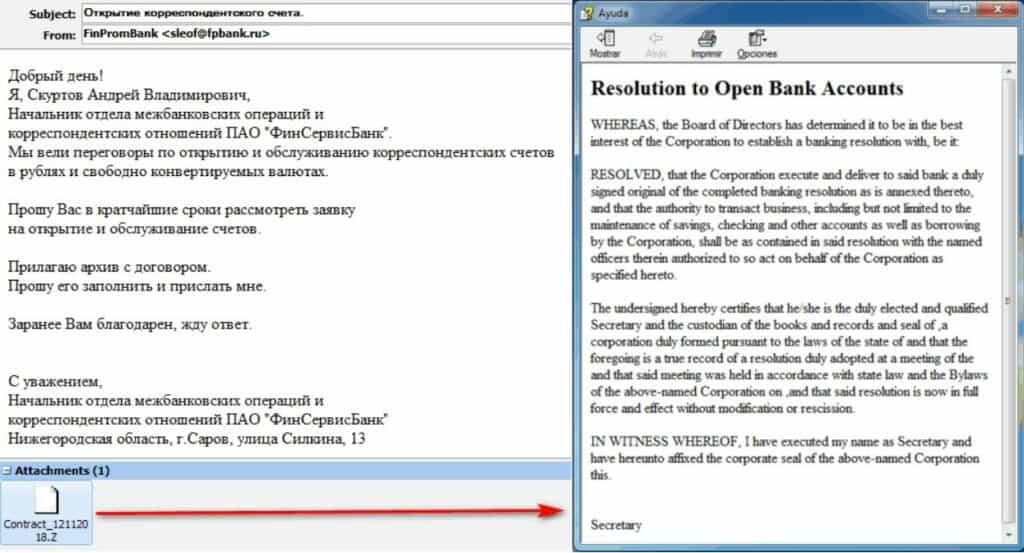
A typical spear phishing attempt would be an email with a malicious CHM file attached.
What has Microsoft done?
Microsoft now blocks CHM files in its email client Outlook and acknowledges they are dangerous. But CHM files are still opened by HtmlHelper by default in most modern Windows operating systems, including the latest version of Windows 10 as of time of writing.
Microsoft patched out some of the vulnerabilities that allow CHM files to be used by hackers for remote code execution back in 2014. Those actions include blocking ActiveX and not allowing CHM files to be opened from Edge or Internet Explorer. However, our researchers found they were still able to reproduce exploits that Microsoft said were patched.
Microsoft told Comparitech researchers that the HtmlHelper vulnerability they reported “does not meet the definition of a security vulnerability for servicing.” When Comparitech asked why this was the case, a Microsoft spokesperson replied with the following statement:
“The issue described does not meet our criteria for servicing because it relies on social engineering or a device to already be compromised. We encourage customers to practice good computing habits online, including exercising caution when clicking on links to web pages, opening unknown files, or accepting file transfers.”
How can Windows users protect themselves?
Don’t open CHM files you don’t recognize.
Researchers strongly suggest organizations remove hh.exe (HtmlHelper) from all client and server machines.
If you believe a CHM file is not malicious, you can first decompile it to read the content before opening it normally. Use this command:
hh.exe -decompile folder file.chm
Additional Technical Information
The proof-of-concept attacks that our research team was able to reproduce on a fully updated Windows 10 machine include:
- NTLM Hash leak
- Remote code execution
- Bypass system policies to download files from third parties
… and several more.
To reproduce attacks, researchers created malicious CHM files using this tutorial on Github.
Comparitech researchers reported to Microsoft multiple CHM-related vulnerabilities found in HtmlHelper on Windows 10. Researchers performed proof-of-concept exploits on all of the following vulnerabilities:
NTLM Hash Leak
NTLM, or NTHash, is how Windows encrypts and stores passwords on PCs. A hash of the password is stored rather than the plaintext password. Normally, to log into Windows, the user types in their password, Windows hashes it using NTLM, and if the output matches the hash stored on the system, the user is authenticated and logged in.
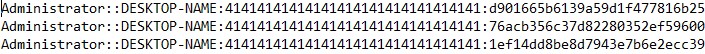
An NTLM hash leak occurs when one of these hashes is stolen. Attackers can then use the hash to authenticate themselves and escalate privileges. The hashes can also be used in pass-the-hash attacks in which the attacker authenticates a remote server or service with the hash of the user’s password instead of typing in the plaintext.

Researchers found hackers can steal hashes using HtmlHelper, which renders content in Internet Explorer 7. IE7 hasn’t been updated in over a decade, yet it’s the default option used by HtmlHelper and can’t be changed. It has no hash leak prevention.
Researchers reproduced the attack using an infected CHM file. They used HtmlHelper on the file to expose the NTLM hash. Researchers were then able to either intercept the hash or send it to a third-party server.
Remote command execution
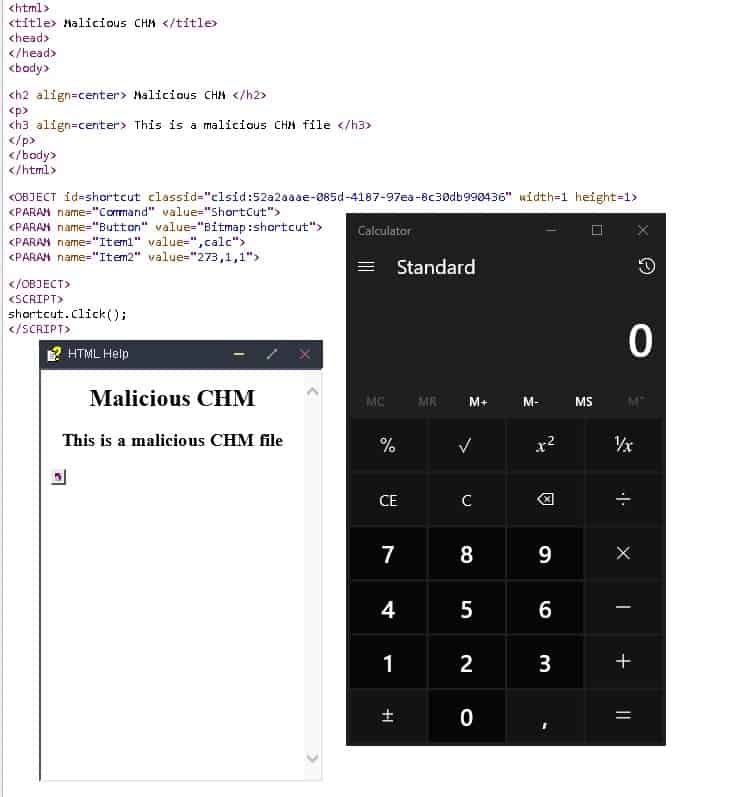
Attackers can execute any malicious command on the target machine using an infected .htm file. The .htm file is converted to CHM, which executes commands without any additional approval from the user.
Researchers launched the calculator app through a CHM file as proof of concept:
ActiveX
ActiveX, a software framework made by Microsoft, has long been deprecated. But because HtmlHelper renders everything in Internet Explorer 7, it still supports ActiveX.
Researchers could run any basic commands on ActiveX without approval by the user. Although security warnings popped up in some instances, users could simply click Yes to continue.
When it was still in use, ActiveX made it possible for websites to embed videos and games and allow users to interact with certain types of elements in the browser, such as toolbars. But Microsoft now strongly discourages use of ActiveX because vulnerabilities in it can be used to steal data, install malware, or remotely hijack a device.



Comparitech’s analysis of malicious CHM files is a commendable resource, offering invaluable insights into this often-overlooked security threat. Their thorough examination and practical recommendations significantly contribute to enhancing cybersecurity awareness and preparedness.
People need to understand that Windows has file types that are considered “executable by design”, meaning they can run arbitrary code with the same rights of the current user and same integrity level of the calling process (program in execution)… a full list of such files can be found at:
https://support.microsoft.com/en-us/office/blocked-attachments-in-outlook-434752e1-02d3-4e90-9124-8b81e49a8519
although a few of them might not currently be able to run anything, like for instance a ‘.scf’ and ‘.theme’ file, it´s possible they could in older Windows. Microsoft has blacklisted and blocked them for a reason, and when you are able to download them from the Internet, programs use OS feature to flag the file came from a remote source: the famous “Mark of the web” and that contains info about the source and the Security zone (see Windows security zones scheme) which is by default the “Internet”, so whenever the user tries to open such files, which of course include .CHM, it displays a security warning. That said, if the user accepts it, we assume he fully trusts the file and source, so he/she is the only to blame if the file install malware. There are “easier” file types compared to CHM, like BAT and HTA which attackers can write code using Notepad and no need for compilation or installing programs/features. This is because CHMs downloaded from the web simply won´t work (displays an empty page). This is a by design issue and was introduced to the OS on purpose, back in 2005 (very old stuff!) to protect the system from potential vulnerabilities. So, the conclusion is that if the user can be tricked into running CHMs he could in thesis be tricked into running anything, including EXE. Regarding IE7, it´s just an emulation mode for backwards compatibility and users can set other modes, ranging from IE5 to 11. the IE security reflects the current security of the OS as it´s a Windows component and as long as you keep it updated, IE will also be up to date with patches.