Developers must be more aware of their tools than ever before as development cycles adjust to new frontiers like CI/CD (Continuous Integration / Continuous Delivery) and the new wave of shift-left development. DevSecOps is no exception, especially given the ever-changing nature of security threats and compliance requirements
Here is our list of the best DevSecOps Tools:
- Intruder EDITOR’S CHOICE This cloud-based service offers options for external attack surface scanning, internal vulnerability scanning, and Web application and API testing for development and Operations teams. Get a 14-day free trial.
- SOOS (FREE TRIAL) This cloud platform offers open-source vulnerability scanning (SCA) and dynamic application security testing for both development and operations teams. Access a 30-day free trial.
- Aqua Security A security platform for cloud-native apps that includes full CI/CD integration and thorough vulnerability scanning. This solution is acceptable regardless of the size of your organization due to the wide range of available versions, including a free version for basic use.
- Aikido Security This platform of preventative scanning and testing services provides an ideal mix of assurance systems for DevOps teams creating and running Web applications and cloud SaaS packages.
- SonarQube Another static code analysis tool that is free and open-source, with premium versions that build on the free version’s rudimentary but useful capabilities.
- Codacy An enterprise-grade automated code review tool that provides thorough vulnerability reporting using static code analysis.
- Checkmarx A premium DevSecOps toolset worth the high business costs is made up of a trio of testing and vulnerability alerting modules.
- JFrog Artifactory This package provides software development support with a stress on in-house development with lifecycle management. Available for Linux, Windows Server, and cloud.
- Prisma Cloud A DevSecOps application security testing tool tailored to cloud-based projects.
- ThreatModeler One of the best threat modeling solutions on the market, with CI/CD integration and professionally built threat diagram tools.
- Acunetix A DevSecOps testing tool that is specifically focused on web application testing, with a collection of over 7,000 identified vulnerabilities.
- CyberRes Fortify An AI-driven static code analysis tool plus a collection of plugins for IDE and CI/CD integration make up this excellent DevSecOps platform.
- IriusRisk Another threat modeling solution similar to ThreatModeler, but with a fully functional free version that interfaces with draw.io to produce useful diagrams.
Relying on older software could jeopardize your DevSecOps initiatives, both during development and delivery, therefore finding better and newer solutions is a must.
Because testing is where the bulk of vulnerabilities are discovered, most 3rd party DevSecOps products will continue to focus on this step. However, the smartest technologies include cleanup and security alerts earlier in the process to avoid problems from spreading further down the line. Furthermore, techniques such as threat modeling enable you to identify potential security problems before they even make it through the design phase.
The Best DevSecOps Tools
Our methodology for selecting DevSecOps tools
We reviewed the market for DevSecOps systems and assessed the options based on the following criteria:
- Security testing for applications under development
- A vulnerability manager for Web applications in operation
- Integration into CI/CD pipelines
- Dynamic and static testing methods
- Detection of open-source content with known security flaws
- A free trial or a demo for an opportunity to examine the service before buying
- Value for money from a DevSecOps tool that is offered at a reasonable price
1. Intruder (FREE TRIAL)
Intruder is a vulnerability scanner that operates from an external stance and the system also provides options for internal vulnerability scanning and Web application and API testing. DevOps teams can use this system to assess APIs for inclusion in a development project and then set it up as a continuous tester. The system will also operate protective scans through the lifecycle of your live Web applications and APIs.
Key Features:
- Attack Surface Scanning: Identifies vulnerabilities across your digital assets.
- Internal Vulnerability Scanning: Provides in-depth internal system assessments.
- CI/CD Pipeline Integration: Seamlessly integrates with continuous integration and deployment workflows.
- API Assessments: Specialized evaluations for APIs, enhancing their security.
- Dynamic Testing: Offers DAST for comprehensive web application security.
Why do we recommend it?
The Intruder package provides vulnerability scanning and optional DAST instances for Web application and API testing. This package, therefore, is very flexible and buyers only pay for the services that they really need, adding on licenses when necessary. Configurations suit development and operations.
Intruder scans your whole infrastructure, including web apps and APIs. Regular vulnerability and proactive emerging threat scans minimize exposure to hackers. Dynamic Application Security Testing (DAST) can be added on to any edition. This extra feature provides security assessment for web applications and APIs and can be used for development projects and for applications that are already live.
You can use the scanner to test any third-party APIs that you plan to use for your project. The tool can be integrated into a CI/CD pipeline and connected to code repositories for automated continuous testing. The DAST tool can also keep assuring your Web applications in the wild. Your systems can be hosted on your own servers or on Azure, AWS, or GCP.
The main functions of the Intruder system are vulnerability and attack surface management. The frequency, depth and coverage of scans depend on your subscription. The Essential plan provides a monthly scheduled external scan with unlimited ad hoc scans, which are ideal for meeting compliance needs. The Pro edition provides unlimited scheduled external and network scans which can also be run on demand, and plenty of integrations to simplify your workflow. The Premium plan adds the services of a ‘rapid response’ team to the Pro edition.
Integrations with third-party tools make the Web application and API testing services particularly interesting for DevOps teams, providing a DevSecOps system. The systems that this package can exchange data with include Slack, Jira, Gitlab, Github, ServiceNow, and Zapier. You can store your functions on AWS, GCP, or Azure.
Who is it recommended for?
The main service of Intruder is its vulnerability scanning system. So, the package isn’t just of interest to DevOps teams who have Web applications to manage because all other types of businesses need risk assessments for their systems.However, the DevSecOps features of the DAST add-on make Intruder particularly appealing to Web application developers.
Pros:
- Comprehensive Coverage: Scans entire infrastructure, providing thorough security analysis.
- Dynamic Addition: DAST can be added to enhance web application and API security.
- DevOps Integration: Seamlessly integrates into CI/CD pipelines and code repositories.
- Platform Flexibility: Supports hosting on multiple cloud platforms like AWS and Azure.
- Versatile Plans: Offers varied subscription plans catering to different organizational needs.
Cons:
- Extra Cost for DAST: DAST is not included in the basic plan and incurs additional charges.
- Installation Requirements: Internal scanning necessitates endpoint agent installation.
Access the vulnerability scanner dashboard through the Intruder website. Internal scanning requires the installation of agents on all endpoints but if you only use the attack surface scanner, you don’t need to install anything. Assess Intruder with a 14-day free trial.
EDITOR'S CHOICE
Intruder is our top pick for a DevSecOps tool because it allows you to buy the exact number of tests to match your API and Web application count. Add on more as your asset base expands. Attack surface scanning and internal vulnerability scanning for the core services of this package and the DAST service can be added on for DevOps scenarios.
Download: Get a 14-day FREE Trial
Official Site: https://portal.intruder.io/free_trial
OS: Cloud-based
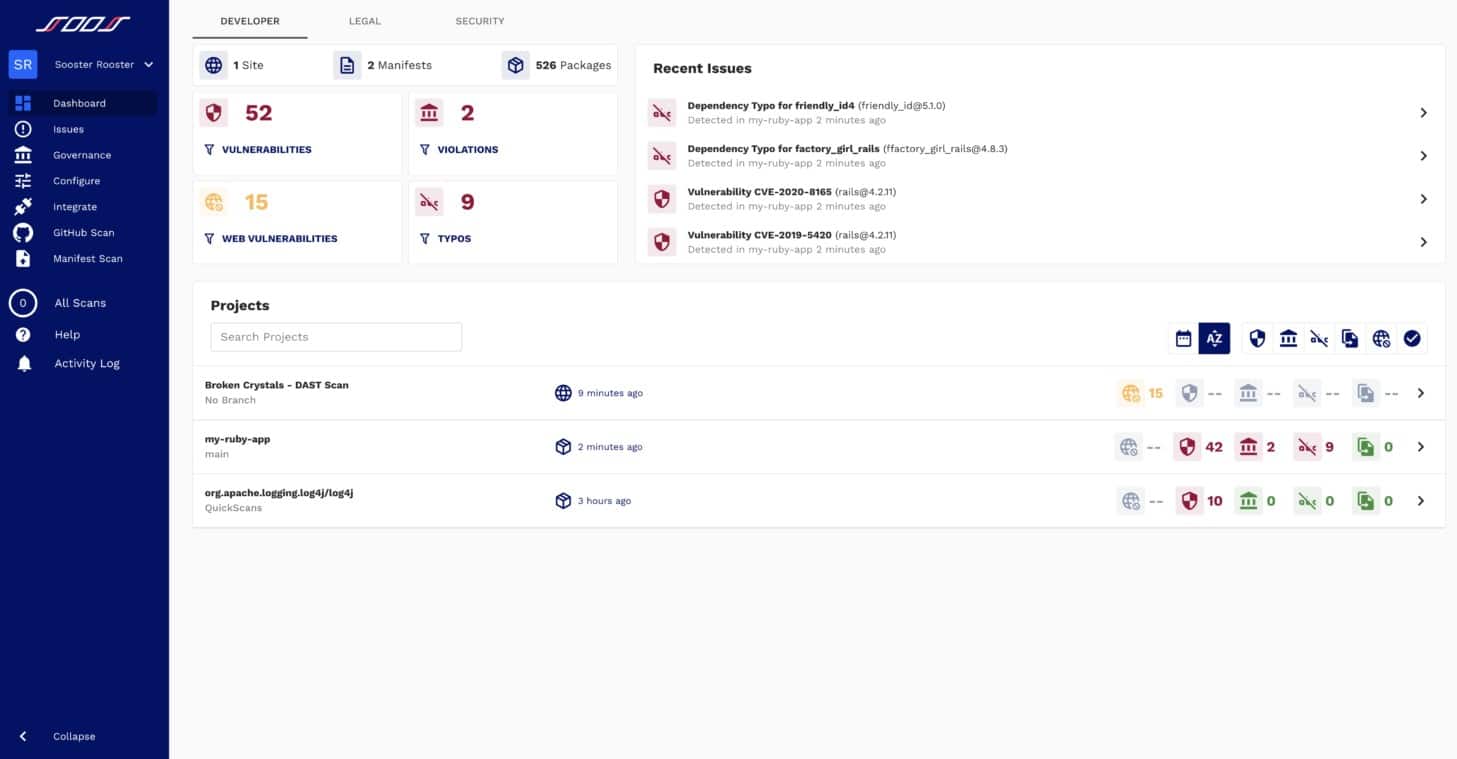
2. SOOS (FREE TRIAL)
SOOS is a SaaS package that offers software composition analysis (SCA) and a higher plan that adds in dynamic application security testing. The two modules operate in concert. The SCA system acts as a vulnerability scanner for open-source code and the DAST package tests new code in Web applications under development.
Key Features:
- Software Composition Analysis: Evaluates open-source components for vulnerabilities.
- Dynamic Testing: Provides DAST for real-time application security analysis.
- Continuous Testing: Facilitates ongoing security checks throughout development.
- On-Demand Scanning: Offers flexible scanning options as per need.
- Unlimited Access: Allows unrestricted user and project integration.
Why do we recommend it?
The SOOS system provides SCA and DAST methods for Web application security checks. The tool can be used for testing in development and vulnerability scanning for operations. The system is a SaaS package and so you don’t need to host any software on your own servers.
The SCA checks all code for open-source content. The system knows the latest versions of the open-source systems and can identify out-of-date systems. Newer versions of these packages are developed whenever a vulnerability is detected. So, keeping any system up to date, including those that are open source, is vital for security.
The DAST system runs your new code and looks at the way it reacts to standard hacker tricks to see whether the module contains exploits. The service runs inside Docker containers, so any security errors in the new system cannot damage the operating system of the host that runs it.
Both the SCA and DAST services can be integrated into Web application development managers. These include Jenkins, GitLab, Bamboo, and Azure DevOps. The testers will also interface to bug trackers, such as GitHub Issues, Bitbucket, and Jira. This interoperability means that the DAST and SCA services can be set up in continuous testing mode, making them part of a CI/CD pipeline.
Both the SCA and the DAST are of use once Web applications are in production. Operations technicians can launch both modules in domain scanner mode to check on live systems. These checks can be run on demand or they can be set up on a schedule to run periodically, such as once a night, to report on the current status of all functioning Web applications.
Who is it recommended for?
This package is designed for use by businesses that build and run We applications, which include mobile applications and SaaS platforms. There is a free version, called the Community Edition, which is a plug-in for GitHub., However, that only implements SCA and not DAST. The top plan serves SBOM environments.
Pros:
- Comprehensive SCA: Thoroughly assesses open-source components.
- Flexible Testing Options: Supports both continuous and on-demand security testing.
- DevOps Integration: Easily integrates with various development and management systems.
- Cloud-Based Platform: Offers a highly flexible and scalable cloud-based solution.
- Broad Compatibility: Supports a wide array of development environments and tools.
Cons:
- Better for Larger Teams: More suited to the needs of larger development groups.
- Limited Trial Version: The trial period could be extended for a more thorough evaluation.
SOOS offers a flat price for an unlimited number of uses and projects. Thus, your costs are nailed down from the start and you don’t have to worry about how many times you use the testing system or limit the number of technicians that can get access to it. The combination of SCA and DAST helps you lock down potential exploits before your code is released. Ongoing scanning during the lifetime of your Web applications means your operations team won’t get caught out by hacker activity.
A big marketing advantage that SOOS has over its rivals is that it has a set subscription rate per month and not a rising rate for larger teams., There are also no limits on the number of projects that a single subscription can be used for.
You can try out the SOOS package with a 30-day free trial.
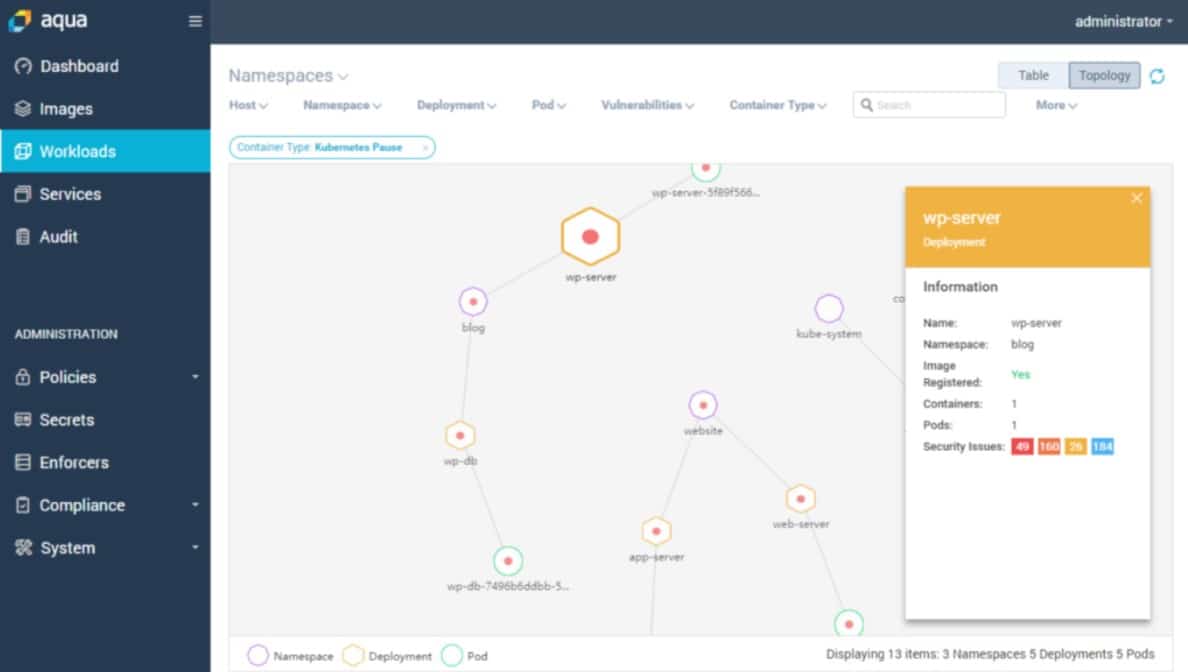
3. Aqua Security
Aqua Security is a three-pronged cloud-native application security platform that focuses on app security, IaaS, and VM/container security. The latest scanning software can detect security flaws, malware, and secrets that have been exposed. To prevent unintentional breaches, you can also set up dynamic policies for deployment.
Key Features:
- Triple-Threat Protection: Ensures security across apps, infrastructure, and containers.
- Real-Time Scanning: Identifies vulnerabilities, malware, and exposed secrets instantly.
- Policy Enforcement: Dynamic policies prevent accidental breaches effectively.
- CI/CD Harmony: Seamlessly integrates with continuous integration and deployment processes.
- Compliance Assurance: Regular checks to ensure adherence to security standards.
Why do we recommend it?
Aqua Security tests cloud-native apps for security weaknesses. The security system provides preventative configuration scanning, live cloud threat detection, and Kubernetes configuration scanning. The package does include a Cloud Infrastructure Entitlements Management (CIEM) module, which is a typical element of CNAPPs. It protects cloud systems and Web applications together.
With full CI/CD integration and extensive scanning in real-time scenarios, the solution is also built for automated security. You may also create a whole vulnerability management procedure that includes detection, remediation, testing, and deployment.
This solution is ideal for large enterprises where the CI/CD pipeline is critical to the development process – internal security and deployment security are also major considerations.
Aqua Security is a free version for testing features in a non-production setting to see whether it’s the appropriate match for you. Furthermore, the premium product portfolio is divided by company size, with the Team version for small enterprises, the Advanced version for medium-large firms, and the Enterprise version for multinational corporations.
Who is it recommended for?
This service is useful for businesses that operate cloud systems. That can include SaaS packages provided by others or those constructed by the company. Similarly, Web apps developed by the company or part of third-party systems can be protected with this security package.
Pros:
- Flexible Security: Adaptable to various cloud-native environments for robust protection.
- Automated Workflows: Facilitates seamless security deployment and management.
- Enterprise-Ready: Tailored solutions for different organizational sizes, ensuring scalability.
Cons:
- Costly for Startups: More suitable for larger enterprises due to high entry costs.
- Limited Team Features: The Team version, while comprehensive, may fall short for growing businesses.
The Team version costs $849 per month and includes all features, but the Advanced version costs $2,099 per month and only expands the capacity of the base product.
Many features, such as built-in remediation and workload protection systems, are available in the Enterprise version, but you’ll need to contact Aqua directly for a tailored offer on cost.
4. Aikido Security

Aikido Security is a new platform that threads together the services provided by open-source projects. The aim of this system is to provide security testing for Web applications under development and preventative vulnerability scanning for applications that are live. Thus, it is an ideal DevSecOps tool. The only feature that is lacking from this platform is a Cloud Workload Protection Platform (CWPP) for live application security threat detection.
Key Features:
- SAST and DAST: Incorporates both static and dynamic testing for web applications.
- Pipeline Testing: Integrates testing into the CI/CD pipeline for continuous security.
- Source Code Analysis: Offers thorough analysis of open-source code components.
- Cloud Security Management: Includes CSPM to manage cloud security posture effectively.
- IaC Scanning: Provides scanning for Infrastructure-as-Code deployments.
Why do we recommend it?
Aikido Security provides scans and tests for Web applications before they go live. Once those applications are live, the package will continuously scan them looking for security weaknesses. This is a preventative security system that provides advice on configuration changes that will block typical hacker attacks.
There are nine categories of vulnerability management and security testing systems in the Aikido Security package. A tenth utility in the platform is an expansion slot that enables users to plug in their preferred third-party security testing tool.
The utilities in the Aikido Security system can be integrated into an automated code development management system because it can interface to code repositories, such as GitHub, and exchange instructions and data with Jira. You should use the SCA module to examine all open-source systems for security weaknesses before allowing them to be integrated into your system.
The two security testing systems in the package are static application security testing (SAST) and dynamic application security testing (DAST). The first of these scans code for well-known security errors and the second runs code in a sandbox with a range of inputs, analyzing outputs. As a rule, you would use SAST for code that you can access and DAST for compiled packages and APIs that you can’t read. This means that you could use SAST for your own code and DAST for the APIs that are called within your code and that belong to someone else.
Once your code is ready to launch as a commercial Web application, you would run the CSPM, IaC, Container scanning/Kubernetes checking, secrets detection, and dependency scanning for malware units.

Who is it recommended for?
This is a tool for DevSecOps teams. You would use this system if you create and market Web applications. You would need to be managing Web applications and making them available for other companies to use in order to benefit from this tool. The users of Web applications and cloud platforms need a cloud workload protection platform and a cloud infrastructure entitlement management, which aren’t included in this package.
Pros:
- Comprehensive Testing: Combines SAST and DAST for thorough security analysis.
- DevOps Friendly: Seamlessly integrates with development tools and processes.
- Third-party Code Assessment: Evaluates external code for potential vulnerabilities.
- Proactive Security: Offers continuous scanning for system hardening and security.
- Project Management Integration: Facilitates smoother project workflows with tool integration.
Cons:
- No Live Threat Detection: Lacks capabilities for detecting real-time security threats.
- Limited Free Edition: Free version constraints in team size and feature access.
Aikido Security offers a Free edition for a 3-member team and that includes access to most of the testing systems for Web development and live systems. The paid plans add on integration mechanisms that enable these testing tools to be set up to run automatically. Those three higher plans also have more user accounts and project capacity with progressively more expensive editions.
Use the Free Edition to trial the Aikido Security platform. You can try it for free.
5. SonarQube
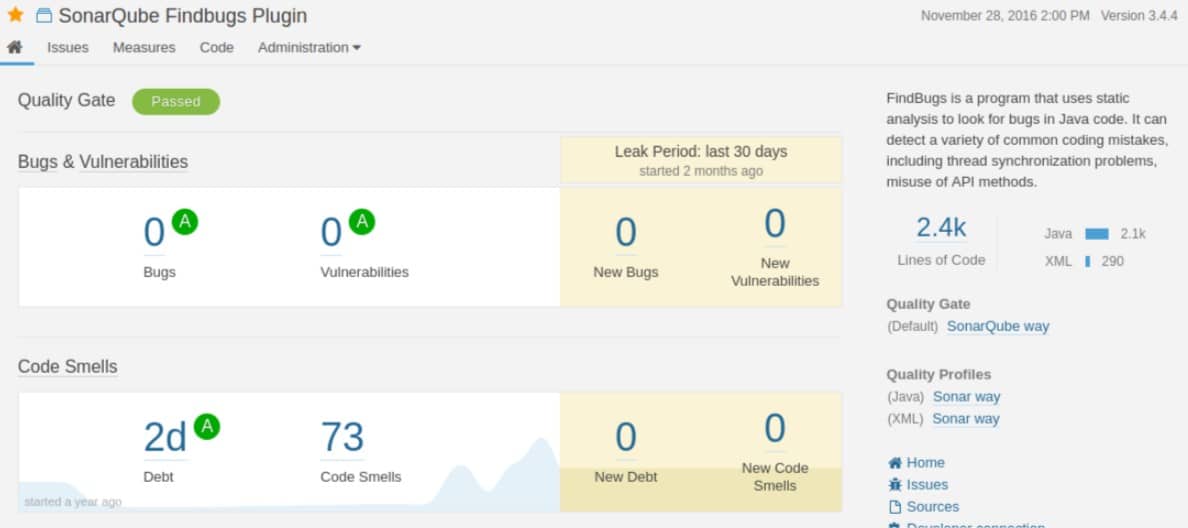
SonarQube is a static code analysis tool that comprehensively examines your code for security threats and vulnerabilities. Security Hotspots, which are possible security concerns that require human evaluation, and Security Vulnerabilities, which are automatically discovered issues that demand prompt intervention, are the two types of issues detected by the software.
Key Features:
- Static Code Analysis: Thoroughly examines code for security vulnerabilities and best practices.
- Open-Source Foundation: Offers a free, open-source version with premium upgrade options.
- Data Sanitization: Ensures safe handling of user-provided data.
- Compliance Tracking: Monitors and reports on adherence to regulatory standards.
- CI/CD Integration: Integrates with continuous integration and deployment processes for real-time code analysis.
Why do we recommend it?
SonarQube is similar to Codacy in that it is more concerned with best practices in coding than security testing. However, security recommendations form part of the remit of the system. The system will connect to your repositories and bug reporters to form part of a development pipeline.
The base program is open-source and free, however, there is a paid version that adds security features to the base. Taint Analysis, for example, is a premium tool that checks user-provided data to sanitize problematic content before it is sent to important systems. Another premium feature is compliance tracking, which guarantees that your code meets all legal criteria.

Who is it recommended for?
This platform has more utilities for development teams than for operations technicians. So, although it could be used on live systems, it isn’t the best in that situation. It is very strong at ensuring code is well-written, decomposed, and correctly documented with security scanning built in.
Pros:
- Continuous Monitoring: Actively scans and monitors code for vulnerabilities and inefficiencies.
- Versatile QA Tools: Provides a range of quality assurance tools and options for thorough testing.
- Multi-Language Support: Compatible with multiple programming languages and frameworks.
- Developer-Friendly: Tailored for development teams, focusing on code quality and security.
Cons:
- Data Visualization: Could benefit from more diverse and advanced data visualization options.
SonarQube is open-source and free, and the base version covers all of the essential capabilities for DevSecOps. A Developer Edition, which starts at $150, offers further programming language compatibility as well as the Taint Analysis tool.
An Enterprise edition, which starts at $20,000, adds reporting tools and compliance tracking measures. Finally, a Data Center version, which starts at roughly $130,000, includes all of the capabilities but is optimized for optimum scalability and component redundancy.
6. Codacy
Codacy is an automated code review solution with a static code analysis tool that can help developers spot security flaws early on in the development process. This feature significantly reduces long-term security vulnerabilities and aids in other development areas such as style guidelines and duplication problems.
Key Features:
- Automated Reviews: Streamlines code evaluation with automatic analysis.
- Git Sync: Integrates directly with Git repositories for smoother workflow.
- Code Quality Focus: Highlights issues in code format and duplication.
- Security Insights: Early detection of security vulnerabilities through static analysis.
- Flexible Hosting: Options for both cloud-based and on-premises deployment.
Why do we recommend it?
Codacy is a software development assessment system. It includes an SCA and also looks for issues such as formatting and function duplication. The duplication checker would be useful for businesses that require a high degree of modularity, identifying common processes that can be split out into functions.
More than 40 languages are supported by the solution, which can also be integrated with a Git repository for more flexible development. Other possibilities include automatic live code reviews, which will notify you if security flaws are discovered. The software can alternatively be self-hosted behind a firewall for ultimate security, which provides all of the capabilities while retaining complete security.
Who is it recommended for?
This tool is suitable for use by a development team manager that needs to verify code. It is more focused on code quality than function security. The tool doesn’t include a continuous tester for security issues but it can be integrated into a Git repository for code quality scanning.
Pros:
- Intuitive Interface: Simplifies navigation and usage for developers.
- Early Detection: Identifies potential security threats at the initial stages.
- Git Compatibility: Enhances code quality with simple Git integration.
- Hosting Versatility: Supports both cloud and self-hosted setups for tailored security.
Cons:
- Extended Trial Desired: Users would benefit from a longer evaluation period.
The Pro version costs $15 per month (on an annual basis), whereas the self-hosted option requires a custom quote from Codacy. Both, however, come with the full feature set, including the static code analysis tool, which is ideal for DevSecOps.
Both the Pro and self-hosted versions of Codacy provide a 14-day free trial. Furthermore, if you contact Codacy directly, the solution is allegedly free for open-source development teams.
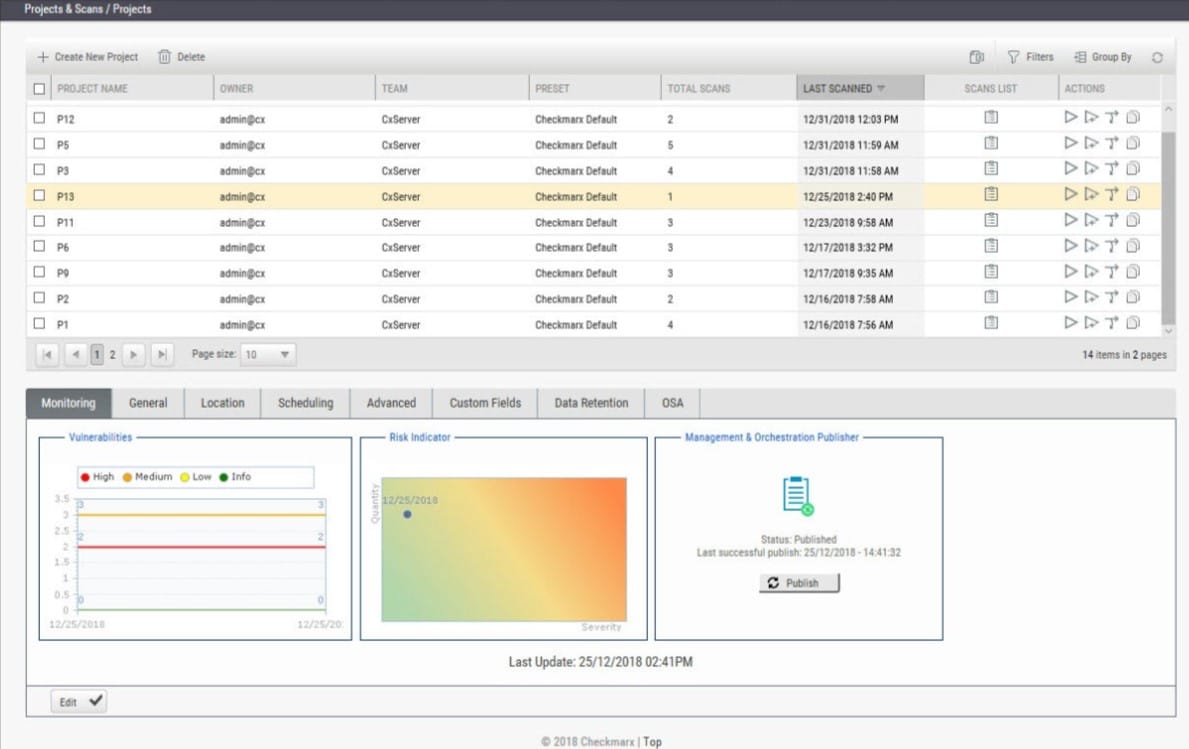
7. Checkmarx
Checkmarx comes with a set of modular utilities for scanning and testing your source code for security issues. The first is the CxSAST (Static Application Security Testing) software, which checks your source code while you’re developing it and reports any problems.
Key Features:
- Code-Level Insight: Delivers comprehensive source code vulnerability assessments.
- Open-Source Scrutiny: Specialized scanning for security in open-source components.
- Seamless Integrations: Works with GitLab and AWS for a unified experience.
- Unified Testing Hub: Centralizes security testing across the organization.
- Comprehensive Support: Offers extensive enterprise-level assistance and training.
Why do we recommend it?
The Checkmarx platform offers modules that implement all of the major application testing strategies and it also offers a plan, called Checkmarx One, that includes all of them. The system provides SCA for open-source content and its testing systems implement both static (SAST) and dynamic (DAST) methods. The package also includes Infrastructure-as-Code (IaC) verification.
Other modules, such as Software Composition Analysis (CxSCA), run a security check on the open-source code you use in projects. These modules can be packaged into the Application Testing Platform, which has all of the features of an orchestration platform for automated CI/CD integration.
Who is it recommended for?
The utilities in the Checkmarx One package are comprehensive and would be suitable for a large DevOps operator. For example, this service can check on cloud services that construct SaaS systems and also delivery systems, such as containers. This platform might be a little too expensive for small companies.
Pros:
- Dynamic Testing Capabilities: Supports both DAST and SAST for thorough analysis.
- Automated Auditing: Streamlines security checks with automated processes.
- Enterprise Focused: Designed for large-scale DevSecOps teams with complex needs.
Cons:
- Opaque Pricing: Necessitates direct contact for pricing details, adding an extra step.
Checkmarx’s products are designed for enterprise-level DevSecOps teams, and their high quality is reflected in their pricing. The software also integrates with a number of popular CI/CD systems and supports a wide range of programming languages. A standard license costs roughly $59k per year and includes 12 developers.
8. JFrog Artifactory

JFrog Artifactory is a platform that supports DevOps efforts through services such as repository management and version control. The tool focuses on the management of binaries rather than code, so you would pair it up with a code repository, such as GitHub. It can be used to manage different adaptations of the same code that are compiled to on different operating systems.
Key Features:
- Binary Management: Centralizes control over binary storage and delivery.
- Document Control: Manages records and archives efficiently.
- Secure Delivery: Ensures the safe distribution of binaries across platforms.
Why do we recommend it?
This package provides secure binary management for the SDLC and includes a method to rollout those assets to different platforms on many sites and even to third-party hosts. Manage versions and archives with this service and centralize your documentation for each program as its development progresses through to release.
I found this package is particularly useful for managing Kubernetes frameworks and containers. It will store and document your Infrastructure-as-Code elements. The documentation that the system generates automatically amounts to metadata and this can be searched. The platform provides the Artifactory Query Language (AQL) for this purpose.
Although this tool is an important element of an SDLC support system, it doesn’t constitute a full DevOps framework. JFrog Artifactory interfaces with your other DevOps tools to form a part of a development and asset management service. The JFrog brand also provides coordinating modules that will link to Artifactory seamlessly. These include JFrog Xray for source code analysis and JFrog Connect for remote monitoring and management of live systems.
This service groups together related assets, such as code, containers, and setup scripts that amount to an installation package. This group needs to be kept together through the development service and tested as a package rather than just focusing on the core code.
Who is it recommended for?
JFrog Artifactory is particularly recommended for enterprise-level software development environments. It supports over 30 package and file types and integrates with various build tools, enabling full control and enhanced automation of build pipelines. This universality makes it suitable for organizations that deal with diverse software components.
Pros:
- Versatile Deployment: Offers SaaS, cloud, and on-premises options for flexibility.
- CD/CI Integration: Seamlessly integrates into existing DevOps frameworks.
- Comprehensive Management: Oversees development units’ relationships for streamlined processes.
Cons:
- Additional Tools Required: Needs external code repository and project management tools for full functionality.
There are three deployment options for Artifactory. There are three plans for its SaaS version, which is priced per month, starting at $150 for 25 GB of base consumption. The package has the same price when it is activated as a service on AWS, Azure, or Google Cloud Platform. The on-premises version is available for Linux and Windows Server and is offered in four plans with an annual subscription rate. The lowest plan, called Pro, cost $3,500 per year. You can register for a free demo of the JFrog Cloud Platform.
9. Prisma Cloud
If you’re working in the cloud, Prisma Cloud offers a wonderful automated security platform that’s ideal for DevSecOps projects. Vulnerabilities, misconfigurations, and compliance violations are detected throughout your codebase, including within git repositories.
Key Features:
- Automated Scanning: Conducts thorough security assessments automatically.
- Open-Source Reliance: Leverages open-source technology for enhanced security.
- Instant Feedback: Offers real-time alerts on security issues for quick mitigation.
- Policy Customization: Allows users to edit and implement security policies easily.
- Git Harmony: Integrates seamlessly with Git repositories for continuous scanning.
Why do we recommend it?
Prisma Cloud is a product of Palo Alto Networks, which is one of the leading providers in cybersecurity, so for companies that value the reputation of their software suppliers, that brand should be recommendation enough. Palo Alto has reconfigured the platform recently to make it a CNAPP, which includes access controls for cloud systems.
For optimum security coverage based on open-source foundations, Prisma is paired with another solution called Bridgecrew. It may be used as a complete git repository vulnerability management solution, scanning your live DevOps environment and providing automated feedback on found security concerns.
Who is it recommended for?
This platform has all of the elements needed by DevOps teams to develop and support Web applications and cloud services, such as SCA and IaC scanning. The recent addition of a CIEM makes this a suitable system for businesses that use third-party SaaS services as well.
Pros:
- Automated Remediation: Prioritizes automated detection and fixing of security threats.
- Compliance Insights: Capable of identifying and alerting on compliance issues.
- Git Integration: Enhances vulnerability management with Git compatibility.
- Thorough Vulnerability Management: Excels in detecting and managing security vulnerabilities efficiently.
Cons:
- Large-Scale Bias: More advantageous for extensive DevOps setups due to its complexity and pricing structure.
Prisma Cloud is an enterprise-level solution with enterprise-level pricing, but it uses a credits-based licensing business model that allows you to change expenses as needed. The program is separated into two versions: a Business version that costs roughly $90 per credit and an Enterprise version that costs $180 per credit and extends on the base features suite. You can also contact the company directly to request a free trial.
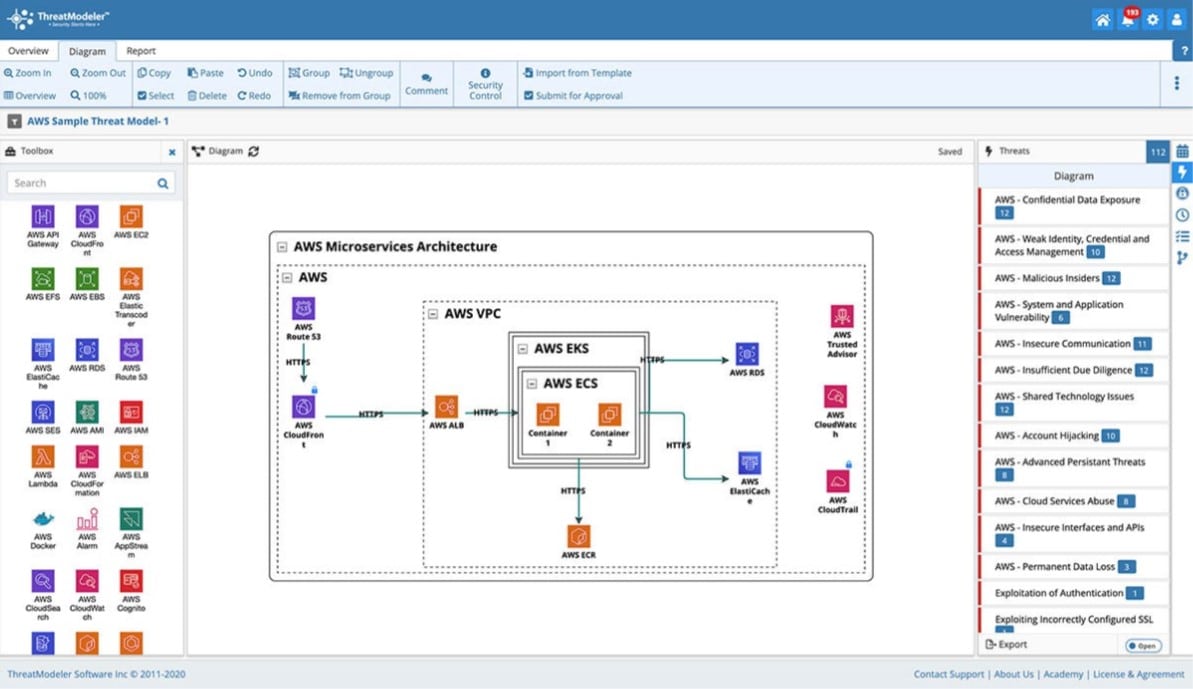
10. ThreatModeler
ThreatModeler is a security testing tool that automates threat modeling and remediation. You can use a customized threat library for each project to conduct security testing and generate entire threat models. The tool may also scan your environment for missing security controls and automatically mitigate threats.
Key Features:
- Automated Threat Modeling: Streamlines the process of identifying potential security threats in development projects.
- Extensive Integration Options: Integrates with popular tools like Jenkins, Azure, Bamboo, and CircleCI.
- IDE Support: Offers an Integrated Development Environment for automated test generation.
- AI-Driven Execution: Utilizes artificial intelligence for efficient test execution and analysis.
- Modular Pricing: Provides flexible pricing options to suit various organizational needs.
Why do we recommend it?
ThreatModeler is a rapidly expanding DevSecOps platform that offers modules for IoT, mobile app, container, and cloud service security scanning. The tool creates a test environment for all components and then rescans for security weaknesses as new components are added. Think of this as a sandbox for new apps.
The tool has comprehensive Jenkins and JIRA interoperability to allow enterprise-level CI/CD pipeline integration. There are several scalable solutions available, but the DevOps Edition includes the CI/CD link required for your development workflow.
Who is it recommended for?
This is a DevSecOps package and it provides a development environment through its proprietary framework. This is an interesting system management package that imposes an entire pipeline management infrastructure rather than just a testing point. Startup developers would find it easier to begin with this system rather than established businesses that would have to adapt their working practices.
Pros:
- Customizable Threat Libraries: Allows tailoring threat libraries for specific projects, enhancing relevance.
- User-Friendly Interface: Simplifies threat modeling with an intuitive interface.
- Comprehensive Integration: Seamlessly integrates with a range of development and project management tools.
- Enterprise-Focused: Offers scalable solutions ideal for larger, enterprise-level environments.
Cons:
- Basic Interface: Some users may find the interface somewhat simplistic or lacking advanced features.
The tool’s base price for a 12-month license is roughly $4,000. To acquire a personalized demo and quote for the ThreatModeler DevOps Edition, which includes full CI/CD integration, you must contact the ThreatModeler company directly.
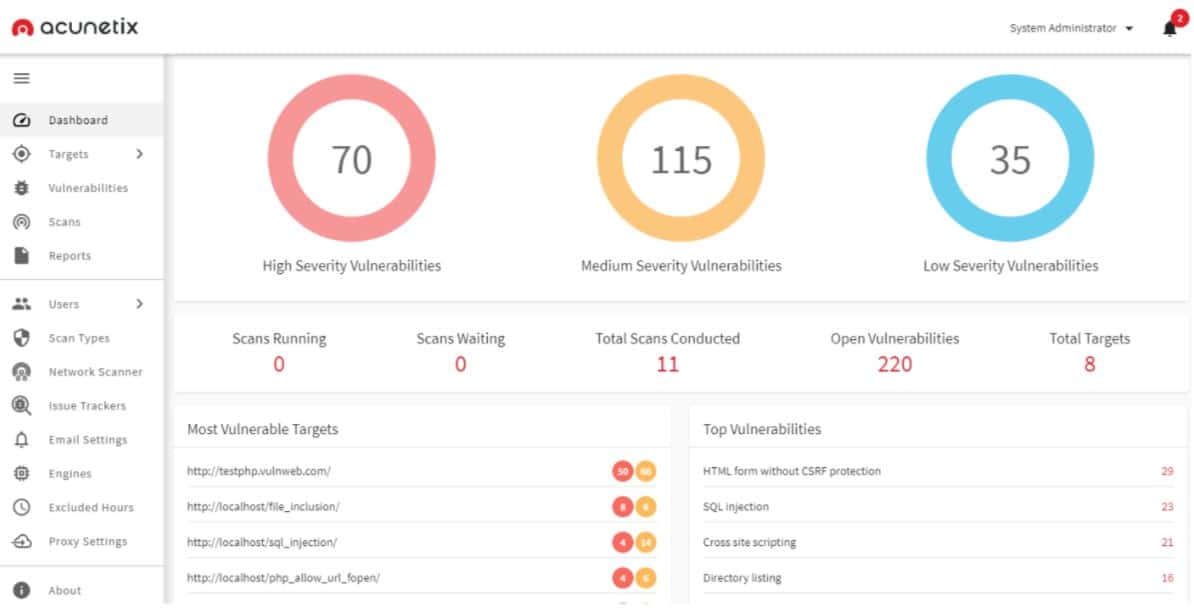
11. Acunetix
Acunetix is a web application security DevSecOps tool that scans and tests your web apps against a database of over 7,000 vulnerabilities. Furthermore, the program may detect a variety of vulnerabilities, such as SQL injection and XSS openings, by examining your source code with a feature called the AcuSensor.
Key Features:
- Web Application Focus: Specializes in security testing and scanning for web applications.
- Comprehensive Vulnerability Catalog: Features an extensive database of known exploits for thorough scanning.
- Efficient Scanning: Offers fast and effective security checks for applications.
- Flexibility: Available as a web-based service with on-site hosting options.
Why do we recommend it?
Acunetix operates as a vulnerability scanner, however, behind the scenes, that scanning is implemented with DAST and IAST, which are two methods frequently used for continuous testing in a CI/CD pipeline. So, the package could be used to verify applications before releasing them.
Premium editions of the program add support for APIs and multiple interacting websites and web applications to the solution’s basic features. With on-site hosting, AD-based user administration, and git repository support, the Enterprise version even allows for custom development integration.
Who is it recommended for?
This system is more of a tool for operations assurance. However, it can be integrated with development project management tools, such as JIRA and Jenkins and it can connect to code repositories for automated scanning. That means you can also use this tool for development testing.
Pros:
- Application Security Emphasis: Designed specifically for robust application security.
- Tool Integration: Integrates with a wide array of other security tools for comprehensive coverage.
- Automated Response: Employs automation for immediate threat response and issue escalation.
- Misconfiguration Detection: Capable of detecting and alerting on security misconfigurations.
Cons:
- Trial Availability: A trial version for testing the platform would be beneficial for potential users.
The solution’s Standard edition, which starts at $4,500, offers all of the basic functions you’ll need for your web app DevSecOps testing. The Premium edition, which starts at $7,000, includes continuous scanning support and various additional capabilities. Finally, for Enterprise needs, a customized estimate for the Acunetix 360 solution with on-site hosting can be quoted from the company directly.
12. CyberRes Fortify
CyberRes Fortify is an enterprise-level application security platform that uses AI-driven scans to swiftly find and resolve security problems. Furthermore, the solution automates testing in a live CI/CD integrating environment and includes a suite of plugins for IDE development, Jenkins integration, and other features that enable modular deployments wherever the product is required.
Key Features:
- Application Security Testing: Provides AI-driven scans to quickly identify and resolve security issues.
- Vulnerability Scanning: Offers thorough scanning for vulnerabilities in application code.
- Static Code Analysis: Specializes in analyzing static code for potential security threats.
- Granular Control Plugins: Enables detailed control over security processes with plugins.
- On-Site Hosting Option: Provides the option for on-premises hosting for enhanced security control.
Why do we recommend it?
The CyberRes Fortify platform has strong development support features. It includes software supply chain assurance and SCA for code inputs and then DAST and SAST processes for security testing before release. This tool also provides IaC security scanning and it can be applied to mobile apps as well as Web applications.
The software analyzer, which can be hosted on-site for optimal security, is the product’s key selling point. This solution employs a number of analyzing engines to examine inputted code and detect any potential flaws. This configuration can be fed specific rules to provide context for the scan and performed using a CLI or IDE.
Who is it recommended for?
This is a very strong DevSecOps platform with more emphasis on DevSec than SecOps. It will verify third-party code and implement continuous testing on repositories. Its DAST and SAST systems could also be applied to vulnerability scanning for live applications, similar to the processes implemented by Acunetix.
Pros:
- Advanced Analysis Tools: Utilizes AI and multiple analysis engines for deep code examination.
- CI/CD Integration: Seamlessly integrates with continuous integration and deployment environments.
- Static Code Focus: Strong emphasis on static code analysis for early threat detection.
- Flexible Hosting: Offers both cloud-based and on-premises hosting options.
Cons:
- Extended Trial Period: A longer trial period would allow for a more comprehensive evaluation of the platform.
Fortify offers a 15-day free trial on their website. You’ll need to contact the company directly for a customized quote on pricing for the full product and individual plugins.
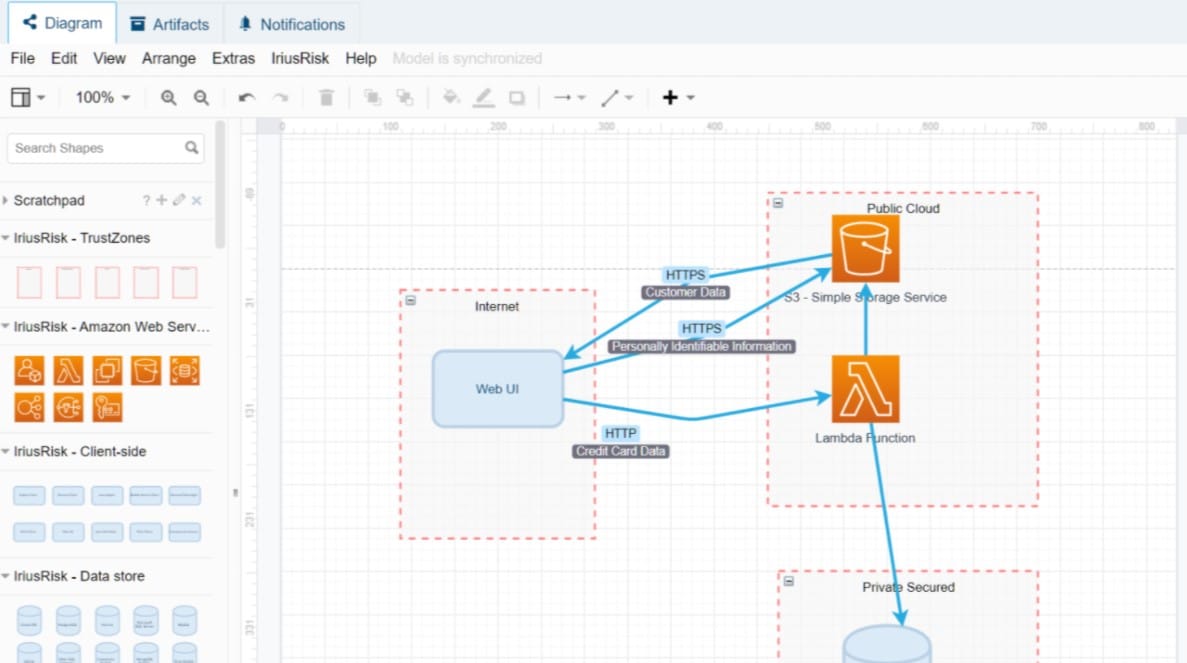
13. IriusRisk
Another automated threat modeling technology, IriusRisk, helps you to detect and plan for security vulnerabilities in your DevSecOps initiatives. Threats and countermeasures can be represented and exported in various ways for improved visibility. IriusRisk excels in the free version, which connects with draw.io to eliminate costs while maintaining adequate threat modeling features.
Key Features:
- Automated Threat Modeling: Facilitates the creation and analysis of security threat models.
- Diverse Export/Import Options: Offers a variety of options for exporting and importing threat models.
- API Access: Provides API access for extended functionality and integration.
- AWS Subscription Option: Available as a subscription service through AWS.
- Workflow Management: Includes tools for managing security workflows and processes.
Why do we recommend it?
IriusRisk is a similar service to the ThreatModeler package. This tool includes a system planner in which you design all of the modules in your application and show their hosts and interfaces to each other. The threat assessor then assesses the model as each module is developed.
There are premium versions available, including an Enterprise version that further expands the software’s capabilities. If you do a lot of large-scale projects, the subscription upgrade can be worth it because you get better importing and exporting features and API access for an unlimited number of threat models. The price of an AWS subscription version is lower, and the solution is limited to a maximum of 5 models, but it includes all Enterprise capabilities.
Who is it recommended for?
This is more of a tool for development teams. However, the model that you create can be stored and triggered on a schedule to rescan an application environment while it is live, creating a tailored vulnerability scanner. With this strategy, you turn this Development assurance system into a DevSecOps tool.
Pros:
- Intuitive Modeling Tools: Offers user-friendly tools for creating and analyzing threat models.
- Scalability: The Enterprise version is particularly suited for large-scale projects.
- Free Version Available: Includes a free version that offers basic threat modeling capabilities.
- Planning Focus: Ideal for planning and threat modeling in development projects.
Cons:
- Limited Use Cases: More tailored towards planning and threat modeling, with limited applicability beyond these areas.
As previously stated, the standard solution is free to log into and access through the company website, making it ideal for evaluating the basic capabilities before deciding whether to remain with the free version or upgrade. For a tailored quote on pricing for the Enterprise version, you’ll need to contact the sales team directly, although the AWS version is roughly $110 per month, depending on your AWS setup.
DevSecOps tools FAQs
What are the 4 components of DevSecOps?
Implementing DevSecOps involves four components:
- Software specifications should include security requirements by default
- Include frequent testing in the development process
- Integrate security testing into the development process
- Automate security testing in the CI/CD pipeline
What is DevSecOps example?
DevSecOps involves integrating security requirements into the specification of all software and then testing software security at every stage of the DevOps lifecycle. For example, A security design review is the first step in implementing Dev SecOps. Other examples lie with automated security testing that is built into the CI/CD pipelines and vulnerability scanning for Web applications that are live.
What is SDLC in DevSecOps?
SDLC is the software development lifecycles. SDLC does not end when software is delivered to operations because it continues through operations as a process for software maintenance. Thus, building security considerations (Sec) in to the development (Dev) and operation (Ops) of software creates DevSecOps. This involves including security requirements in software specifications and testing for security during development, deployment, and operations.