Practically every organization has internet connectivity or some part of its IT infrastructure facing the outside world. This greatly increases the risk of a cyber-attack. Cybersecurity risk management can help mitigate this risk and should form an integral part of an organization’s business and security processes.
If you’re doing business today and have any IT footprint you have to be doing security as part of it. You are basically playing Russian Roulette and it is only a matter of time before you are hit.
- David Kelly, founder of cybersecurity company TrustedSec
Evaluating risk isn’t always easy. Many businesses now choose to use specialist software that can help them to objectively assess risk.
Here is our list of the best risk assessment software:
- Riskonnect Active Risk Manager EDITOR’S CHOICE This risk management platform that helps organizations identify, assess, and mitigate risks effectively. Its assessments focus on the risks that change requests create and that also extends to acquisitions. Based in the cloud.
- Fusion Risk Management This SaaS package is suitable for use by large organizations and helps identify technology-related risks and the steps that would be needed to mitigate each of them.
- SAI360 IT Risk & Cybersecurity This risk assessment package integrates with ITIL-based IT asset management systems. Delivered from the cloud.
What is Cybersecurity risk management?
Cybersecurity risk management is the continuous process of identifying, analyzing, evaluating, and addressing an organization’s cybersecurity threats. Emphasis should be made on “continuous” because cybersecurity risk management is not a one-time, solve-and-move-on kind of process. Instead, it is a non-stop process that is repeated over and over again throughout the lifetime of a network.
For one, hackers and malicious users continue to find novel ways of attacking a network. This means administrators need to stay on top of the latest attack methods – for each type of device on the network. They then need to update their defenses as soon as they realize a new hacking or attack tactic is being used.
Also, network and endpoint defense solutions – be they software or hardware solutions – may become obsolete. Therefore, apart from being regularly upgraded, they need to be monitored to see if their configurations effectively prevent threats – both before and after a risk assessment has been done and later, as part of the cybersecurity risk management process.
Finally, it should be pointed out that although the IT security team is responsible for implementing threat avoidance and prevention policies and solutions, the security of a network depends on the cooperation of every user on it.
All these steps are part of cybersecurity risk management.
What is cybersecurity risk assessment?
Cybersecurity risk assessment is the starting point of any cybersecurity risk management campaign. Businesses need to do these assessments to understand how great a risk their networks are in. They achieve this by first identifying which assets are vulnerable and then tackling the issue of securing them in the order of their riskiness.
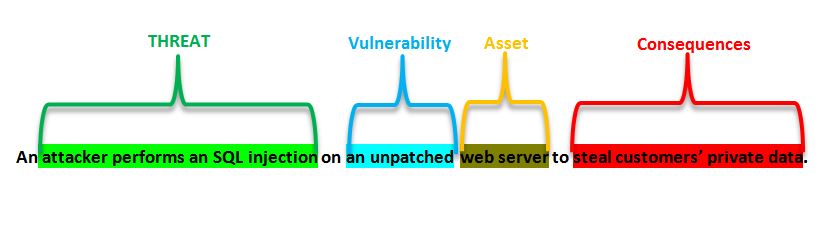
Therefore, a cybersecurity risk assessment identifies every digital asset that could be the target of a cyber-attack – like hardware, software, data, and intellectual property – and then determines the various risks that could affect them.
What are the steps involved in a cybersecurity risk assessment?
A business needs to define its key business processes and objectives and the information technology (hardware and software) assets used to serve as input to the cybersecurity risk assessment.
Next, cyber-attack methods and types are identified that could adversely affect these very IT assets. An analysis is then done to determine the likelihood of such attacks occurring and their impact on the business processes. Finally, the results from this analysis are saved to serve as threat-level indicators for auditing, compliance, and progress reporting.
Once the security team has a clear picture of the overall risk status, they can make informed decisions about how to mitigate the risks – including implementing defense solutions, plugging security holes, patching out-of-date technology, and retiring legacy systems.
How to perform cybersecurity risk management – the whole process
The first step in the cybersecurity risk management process is defining the scope – which can range from a single server for the entire network and even extend beyond it to include the cloud. The wider the scope is, the more complex an undertaking it becomes to ensure its security.
Examples of scope would be a business unit, a network segment, or a location. It could also be a payment processing system or client-facing application.
An important fact here would be gaining the full support of all the stakeholders covered by the scope. Their input, suggestions, and expert opinions help identify processes, applications, and hardware at risk. They can even assist with resolving issues and threats without impacting the business processes. Most importantly, they won’t be irritated by the process itself.
Once the scope is known, it is time to start the cybersecurity risk management process, which consists of the following steps:
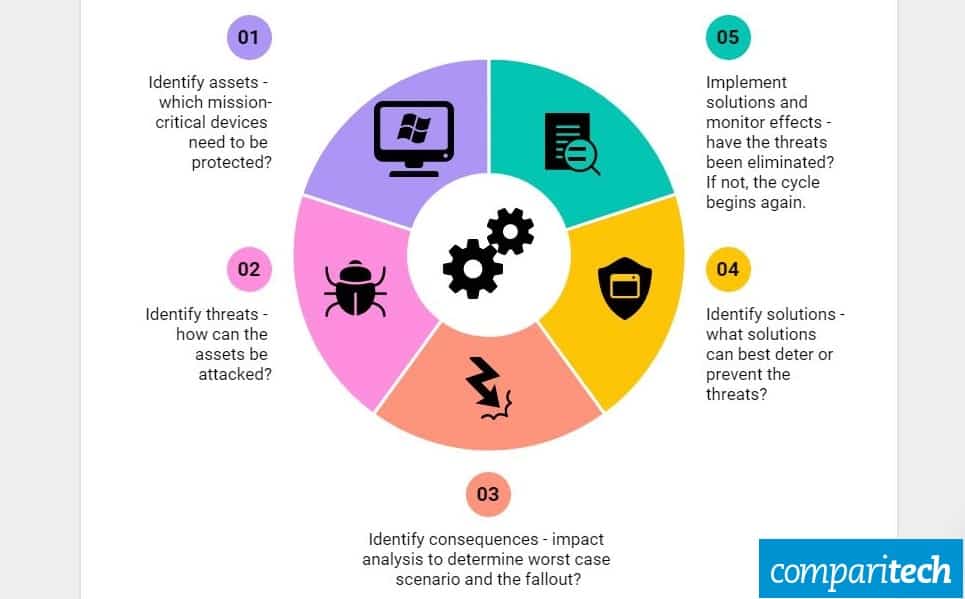
1. Identify assets
Assets need to be identified before they can be protected. This initial step identifies all the applications, services, and devices that are crucial to the business – or support mission-critical processes.
Devices that face the internet but are not part of these critical processes can also be considered since they can be hijacked to serve as staging devices to perform attacks from behind the defense perimeter.
2. Identify threats
Once each critical digital asset has been identified, it is time to identify all the threats that could be made against them.
Each software, laptop, server, POS machine, and mobile device is assigned a threat level depending on how prone or exposed it is to threats. The higher the threat level it is ranked, the higher priority the device is assigned.
Assign each software, laptop, server, POS machine, and mobile device a threat level depending on how prone or exposed it is to threats. Once the scope has been defined, it is time to identify the risks facing each device in the scope, the dangers that each one faces, and its effect on the overall performance of the business’ core process.
The threats could be posed from viruses, hacks, user inexperience, policy laxness, or old versions of unpatched solutions.
3. Identify consequences
Next, it is time to analyze the impact of having each system or device down for specific amounts of time. This is, of course, taking into consideration that not all issues can be resolved in minutes or hours. Therefore, the consequence analysis should consider – and even simulate – the impact of a system or device being offline for an undetermined amount of time would ensue.
4. Identify solutions
Now that the devices, threats, and consequences have been identified and analyzed, it is time to find temporary (short-term) and permanent (long-term) solutions to address and prevent them. The answers could be tested while identifying the consequences in the previous step. Ideally, this is done in a test or dummy network.
Examples of solutions can be patching software, training users, implementing new IT policies, installing antiviruses, and tightening access control.
Four strategies can be adopted while arriving at the ideal solution:
- Treatment – finding security tools and best practices to resolve the issue causing the risk; examples include installing firewalls, proxy servers, and antimalware.
- Tolerance – accepting the risk is unavoidable and deciding to tolerate its existence; this calculated risk should fall within established risk acceptance criteria.
- Termination – completely cutting the system, software, or hardware out and redesigning affected processes to run without them.
- Transferal – reducing the risk by dividing the risk with another party; examples here could be outsourcing security to a technology company or buying insurance.
5. Implement solutions and monitor progress and effectiveness
Any identified resolutions should be implemented as soon as possible. They should start protecting against threats immediately.
Once the testing has been completed successfully, the solutions can be moved into the production environment.
Most software solutions for monitoring cybersecurity risks have dashboards that show risk exposure levels. In the rare case that they don’t, there are many application, server, and network monitoring tools that can be used to track the health of assets.
Either way, round-the-clock monitoring should be implemented to make sure the solutions provided are indeed helping in the resolution of threats. If there are lapses in policies, weak defenses, or unforeseen (new) perils have been identified, the whole process goes back to the first step, and the cybersecurity risk management process starts over again.
This is to say that these five steps are part of an endless risk management cycle that is repeated until all identified threats have been resolved. And then – even when there are no more issues – the process still needs to run to make sure no new problems pop up down the line.
Best practices for endpoint security
Endpoints make up a majority of the devices on most businesses’ networks. As a result, they include most of the users’ devices that connect to the infrastructure and thus pose the highest chance of being targeted by malicious attackers. Examples include laptops, servers, mobile devices, and virtual environments – all of which can be targeted.
Therefore, it makes sense to point out a few best practices for improving a business’ endpoint security:
- Investing in the right technology for each endpoint type – they need to find the best solution to defend each device; this is especially true if they directly contribute to the mission-critical processes and face the internet.
- Taking cloud computing into consideration – cloud computing is taking over; security plans need to include cloud computing technology. So too, should risk management.
- Bringing IT and users together – no policy implementation or software user management solution will stop users from making mistakes when it comes to enforcing security; every user and stakeholder needs to be aware of the process and come on board as a team player.
- Monitor solutions and policies and tweak them as needed – again, this is not a one-time solution; the whole process needs to be repeated with monitoring results determining if any corrections need to be made before the complete loop starts again.
And then, there are direct actions that need to be taken to ensure the security of the endpoints themselves, like:
- Regular and scheduled patching of operating systems and applications as well as upgrading of hardware.
- Inventorying of software and hardware assets; monitoring to ensure only authorized devices are connected to the network.
- Monitoring software and licensing usage, deleting illegal (pirated) solutions, removing new solutions, and looking for cost-effective alternatives to existing ones.
- Managing configurations and integrations so every device can contribute to the safety of another; after all, any network’s security is as strong as its weakest link – an unsecured device.
- Implementing a robust backup solution for the shortest disaster recovery time possible.
- Managing the reimaging, redeployment, and decommissioning of assets to ensure optimal performance all around and at all times.
Two more tools for cybersecurity management
While on the topic of best practices for cybersecurity management procedures, and before we have a look at software solutions, let’s have a look at two more tools that can be of help to administrators and IT security teams:
The NIST Cybersecurity Framework
The first tool is the National Institute of Standards and Technology or NIST Cybersecurity Framework (CF). It is a list of standards, guidelines, and practices designed to help organizations better manage and reduce cybersecurity risks from all types of threats – including malware, password theft, phishing, DDoS, traffic interception, social engineering, and others.
The NIST CF was created in collaboration with various government authorities and industry groups. It was designed to complement existing organizational cybersecurity procedures. As a result, it is easy to integrate into any business’ current risk management procedures. It is also beneficial as security teams can assess risk levels, set up risk tolerance objectives, improve security priorities, and even plan on their cybersecurity risk management budgets.
What is Bow Tie Analysis?
Bow Tie Analysis, the second tool, is more of a method than a tool. It is a simple process for identifying where new or enhanced risk controls may be most efficient. The technique is a core part of risk treatment planning, especially where there is a high level of risks or where control effectiveness of the risks is considered to be low.
Any cybersecurity risk assessment tool that is worth its salt will have this analysis method incorporated into it.
The Bow Tie Analysis method is a risk evaluation method that can analyze and demonstrate causal relationships in high-risk scenarios. The technique takes its name from the shape of the diagram that needs to be created and which looks like a bow tie.
The bow tie diagram helps with two things:
- It gives a visual summary of all plausible accident scenarios that could exist around a certain hazard.
- By identifying control measures, the bow tie displays what a business does – or needs to do – to control those scenarios.
Any decent cybersecurity risk management solution will include this analysis method. It helps draw a clear picture of the cause and effects in a risk-prone architecture, creating and making it easy to be proactive in mitigating issues before they occur.
Risk assessment software
Methodology for selecting risk management tools
We reviewed the market for cybersecurity risk management systems and analyzed the options based on the following criteria:
- A service that can identify IT susceptibility to attack
- A database of potential threats
- A method to assess the likelihood of an attack occurring
- Systems to provide mitigation strategies to prevent an attack or recover from one
- A service that can quantify the cost of a risk, the measures needed to reduce it, and the damage that it could cause
- A free trial or a demo package to allow a pre-purchase assessment
- Value for money from a cybersecurity risk assessment tool that can identify costs savings
Here are three excellent cybersecurity risk management software solutions:
1. Riskonnect Active Risk Manager
Active Risk Manager is a risk assessment system for projects that can aggregate all current activity within an organization. As long as all risk assessments within a business are entered into the Active Risk Manager, company executives and managers can see summaries of risk per project, per team, per department, and business-wide.
More features include:
- Centralized risk registers eliminate the need for disparate spreadsheets and other databases of risk information.
- Control libraries, templates, and testing to ensure that current risk management processes and controls are adequate, including Bow Tie Analysis.
- Standard Reports, which can be customized, make it easy to communicate risk across the organization and fit any business’ objectives – audits, security, and compliance.
- Risk forecasting – perform Monte Carlo Analysis as a quantitative risk assessment to predict project costs, timelines, and variability.
- Generates heat maps that present a visual representation of assessed risks to prioritize actions intelligently.
Why do we recommend it?
The Riskonnect Active Risk Manager package is suitable for use in a range of business expansion exercises. That activity might be a development, an acquisition, or even asset disposal to refocus investment. This risk assessment can be turned to the business’s priorities, such as data protection standards compliance or ESG goals.
Who is it recommended for?
This package is comprehensive and is aimed at companies that need to dot the i’s and cross the t’s. Corporations can get dragged down by paperwork and expansion projects, in particular, can be mired by documentation tasks. So, the Riskonnect system can make cautious corporations more agile by automating checklists.
Pros:
- Simple interface – easy to use with little configuration
- Offers flexible controls for risk management
- Includes both high-level and granular reporting
- Job Safety Analysis to track risks and hazards on job sites to prevent injuries and loss of life.
- Schedule and Cost Impact Analysis analyze the impact of risks on project schedules and budgets.
Cons:
- Better suited for enterprise environments
Book a demo of Riskonnect Active Risk Manager for free.
EDITOR'S CHOICE
Riskonnect Active Risk Manager is our top pick for a cybersecurity risk management tool because it offers a comprehensive, integrated approach to identifying, assessing, and mitigating cybersecurity risks. Threat landscapes are becoming increasingly complex and organizations need a platform that provides real-time visibility and proactive risk management capabilities. Riskonnect excels in this area by allowing businesses to centralize risk data, consolidate reporting, and ensure compliance with industry standards and regulations. Active Risk Manager supports a wide range of risk management activities, from threat detection and vulnerability management to incident response and mitigation. This allows organizations to tailor the platform to their specific needs, ensuring it aligns with their unique cybersecurity strategies and risk profiles. Riskonnect also provides powerful analytics and reporting tools, enabling security teams to evaluate and prioritize risks more effectively. The platform includes a range of the most important analytical techniques related to risk. These include Monte Carlo Analysis, Job Safety Analysis, and Bow Tie Analysis. The tool will generate Risk Heat Maps that identify all risks by priority. These utilities ease the task of identifying potential vulnerabilities and trends. The platform also integrates with other cybersecurity tools and systems, ensuring that all aspects of an organization’s security posture are considered in the risk management process. Riskonnect promotes collaboration across departments by enabling stakeholders to access and share risk data. This improves decision-making, accelerates the response to threats, and ensures that all parties are aligned on risk priorities.
OS: Cloud based
2. Fusion Risk Management
From Fusion Risk Management, we get an Information Technology and Security Risk Management solution that is powerful and offers numerous features. It allows for the management of cybersecurity risks and their resilience – aka root cause analysis – from one platform.
More features include:
- Integrated action plans for disaster recovery – administrators can create dynamic intends to rise to meet new risks, threats, or any similar challenges with an agile response and return all systems into operation mode within the shortest possible time.
- Staying one step ahead of new risks with the help of Emerging Technologies Risk – to quickly predict and have insights into emerging technologies surface risk; this tool helps administrators create policies and controls to protect the network.
- Having a clear risk landscape to see where current security levels lie – whether for compliance, auditing, or securing the architecture, administrators will always know where things stand.
Why do we recommend it?
The Fusion Risk Management platform provides a list of modules for risk management, which includes business continuity planning, data protection issues, and third-party risk assessments. The platform’s Emerging Technologies Risk is particularly impressive because it pushes a business to keep ahead of developments to secure the business.
Who is it recommended for?
This is a large platform that caters to large businesses. The tool is designed to interconnect with the large ERP and CRM systems that big businesses use to run their operations, such as SAP, Salesforce, and Oracle. All of the functions of this system would be too much for a small business.
Pros:
- Excellent admin console and visual reporting
- Combines risk management and root cause analysis to streamline remediation
- Offers disaster recovery features and audits
- Scalable controls to simplify risk management across the enterprise
Cons:
- Better suited for enterprise environments
Book a Fusion Risk Management demo for FREE.
3. SAI360 IT Risk & Cybersecurity
Finally, last but not least, we have an IT Risk & Cybersecurity solution from SAI360. This cybersecurity risk management tool allows for a 360-degree defense perimeter – just like the name suggests. In addition, it has requirements that are pre-mapped frameworks and controls for the rollout of efficient security campaigns. Add easily exportable and customizable policies that are monitored using workflows – which ensure they haven’t expired – and we get an ideal tool for easily battening down the hatches.
But, there are even more features:
- Automated and centralized vulnerability management of cybersecurity risks; this tool comes with a repository for external data feeds, risk assessment, and scanning tools.
- Automation is everywhere – workflows for everything from asset inventory, strategic resource deployment, and compliance assessments.
- Administrators can create insightful and interactive dashboards and aesthetic reports that are easily understood for a quicker, more informed response.
Why do we recommend it?
SAI360 IT Risk and Cybersecurity focuses on systemic problems and how to prevent, detect, document, and reduce them. The service includes a vulnerability manager and a third-party risk assessor. All of the services of the platform can be tuned to data risk or ESG compliance requirements.
Who is it recommended for?
As with the other tools on this list, the SAI360 system is aimed at large corporations. The tool’s risk assessments can be tuned to a range of regulatory requirements or sector standards and it can even track compliance to multiple standards and different standards according to branch locations.
Pros:
- Highly focused on automated risk assessments and management
- Designed with enterprises in mind – great for global operations
- Excellent dashboards and reporting capabilities
Cons:
- Can take time to fully explore all features and tools
Book a SAI360 IT Risk & Cybersecurity demo for FREE.
Why is cybersecurity risk management critical in a business?
Let’s have a quick look at why you, as a business, need a cybersecurity risk management solution installed:
- Keeping data safe – obviously, this is the first thought that comes to mind.
- Building client trust is created when a business takes clients’ data protection to the heart and invests time, money, and technology to keep it safe.
- You are adhering to HIPAA, GDPR, compliance requirements, etc. – to show that your business is more than capable of protecting the data.
- Increasing competency in the market – you can appear to be more secure than the competition with lax security policies and, therefore, poses a higher risk.
Administrators and business owners alike will sleep soundly knowing that they have put in place the right solution to tackle any issues before they have even occurred.
Implement a cybersecurity risk management solution
As we end this post on the definition and uses of cybersecurity risk management – and some tools to help with the implementation – we would like to part with a few words of advice.
Every day a business stays online is one more day for malicious users and hackers to try and breach its security. As a result, implementing a cybersecurity risk management solution has become a must. We, therefore, recommend that you implement one today.
Please, let us know what you think – will you opt for a cybersecurity risk management tool? Leave us a comment below.
Cybersecurity Risk Management FAQs
Is cybersecurity part of risk management?
Cybersecurity is a process that requires an assessment of threats and the risk that they might occur, so risk management is central to cybersecurity and the likelihood of a cyber attack is an essential calculation that any business should make, so cybersecurity is also central to risk management. This close relationship between cybersecurity and risk management is recognized by the NIST Framework for Improving Critical Infrastructure Cybersecurity and the FISMA Risk Management Framework.
What are the four cybersecurity risk treatment mitigation methods?
There are four typical mitigation strategies when dealing with any type of risk and these are:
- Avoidance
- Reduction
- Transference
- Acceptance
When addressing cybersecurity risk, it is more common to identify three risk mitigation methods. These are:
- Prevention
- Detection
- Remediation
What are the 5 C's of cyber security?
The driving purpose behind cybersecurity covers risk assessment, prevention, and mitigation. The key factors of these considerations can be boiled down to five Cs:
- Change
- Compliance
- Cost
- Continuity
- Coverage






