When it comes to securing cloud environments and managing security data, organizations often turn to Security Information and Event Management (SIEM) tools to provide real-time monitoring, threat detection, and incident response. With a growing number of businesses shifting to the cloud, selecting the right SIEM solution is critical to ensuring comprehensive security across diverse infrastructures.
Datadog Cloud SIEM and Trellix Enterprise Security Manager are two leading solutions in the SIEM market, each offering unique strengths and capabilities. In this comparison, we look into the features, benefits, and potential drawbacks of each platform to help businesses make an informed decision based on their specific security needs.
Datadog Cloud SIEM is known for its cloud-native architecture, which integrates seamlessly with cloud services and provides advanced threat detection powered by machine learning. Its ability to monitor and correlate security events from cloud infrastructure, applications, and services makes it a powerful tool for organizations with a significant cloud presence. The platform’s intuitive dashboards and real-time alerting capabilities make it easier for security teams to respond to incidents swiftly.
On the other hand, the Trellix SIEM has a long-standing reputation in the enterprise security space, offering comprehensive on-premises and cloud security monitoring. Trellix’s SIEM solution excels at log management, compliance reporting, and in-depth analysis across hybrid environments. It is especially well-suited for organizations with a mix of on-premise and cloud systems, providing the flexibility to secure both worlds with one tool.
This guide compares both solutions in terms of features, scalability, ease of use, and deployment options, helping organizations determine which SIEM tool aligns best with their security infrastructure and operational requirements.
Overview of Datadog Cloud SIEM
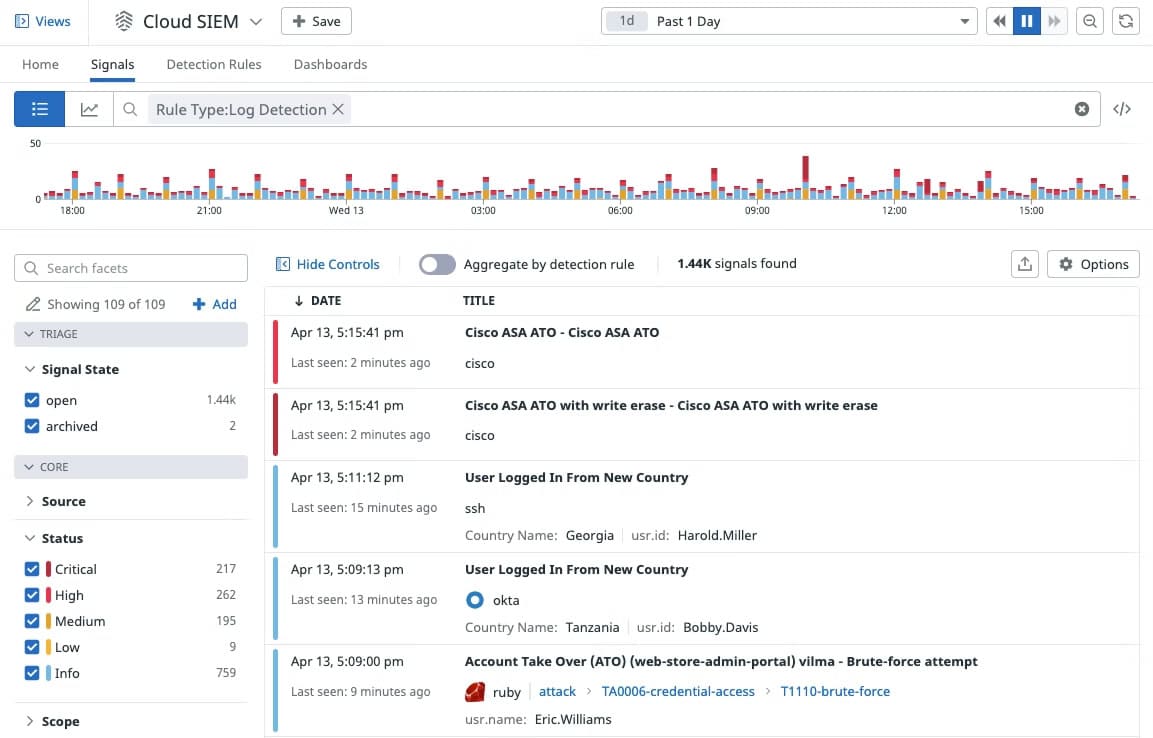
Datadog entered the SIEM application market with the launch of Datadog Cloud SIEM in 2020. Datadog Cloud SIEM (Security Information and Event Management) is a SaaS-based solution that provides end-to-end security coverage of dynamic, distributed systems. It is part of the Datadog Cloud Security Platform and is designed to provide a single centralized platform for the collection, monitoring, and management of security-related events and log data from across the enterprise. This enables security teams to identify and respond to suspicious behavior patterns more effectively than possible by looking at data from individual systems.
With Datadog Cloud SIEM, you can analyze operational and security logs in real-time regardless of their volume. Developers, security, and operations teams can leverage detailed observability data to accelerate security investigations in a single, unified platform.
Key features and capabilities include:
- Observability and security See all of your security data in one place and correlate them with runtime events, application and service logs, and more. Development, security, and operations teams can access the same observability data and drive security investigations in a single, unified platform.
- Out-of-the-box dashboards The Security Overview dashboard allows you to have a high-level view of your security posture. The IP Investigation and User Investigation dashboards enable users to correlate specific IP addresses and users with security signals, events, and logs, so they can quickly hone in on malicious activity patterns.
- Out-of-the-box threat detection rules Datadog Cloud SIEM comes equipped with rules that don’t require a query language for widespread attacker techniques and misconfigurations that are mapped to the MITRE ATT&CK framework.
- Built-in vendor-backed security integrations Built-in security integrations with AWS CloudTrail, Okta, G Suite, and more enable users to ingest additional security data in minutes, which provides deeper context and helps accelerate investigations.
A free personalized demo and a free 14-day-trial with full access to all the features are available on request. After that, the software is generally sold through monthly subscription plans based on hosts, events, or logs.
Overview of Trellix Enterprise Security Manager
Trellix Enterprise Security Manager (ESM), previously known as McAfee Enterprise Security Manager (McAfee ESM), is a reliable SIEM solution designed to help organizations detect, investigate, and respond to security incidents in real time. The platform’s rebranding to Trellix marks a shift toward a more integrated, intelligence-driven approach to security, while maintaining its core capabilities.
Trellix ESM offers system monitoring, log management, event correlation, and threat detection to safeguard enterprise environments. It is able to manage very large amounts of security data and turn it into actionable insights. The system collects and analyzes security event data, enabling teams to detect anomalies, track security incidents, and ensure compliance with industry regulations. The solution integrates with existing IT infrastructures, offering both on-premises and cloud deployment options for flexibility in how it’s used.
Key modules in Trellix Enterprise Security Manager include:
- Event Receiver: Captures security events from a variety of data sources, including network devices, endpoints, and applications, to provide a central point for all event collection.
- Advanced Correlation Engine: Correlates security events in real time, enabling teams to detect sophisticated, multi-stage attacks and uncover hidden threats within large volumes of event data.
- Enterprise Log Manager: Manages the collection, storage, and indexing of log data across the organization, ensuring efficient log aggregation and compliance with regulatory standards.
- Enterprise Log Search: Provides fast, comprehensive search capabilities across logs, enabling security teams to quickly find relevant data for investigations and audits.
- Application Data Monitor: Monitors data flows between applications, ensuring the integrity and security of sensitive application data, and identifying any unusual or unauthorized access patterns.
- Direct Attached Storage (DAS): Ensures high-performance storage for log data by utilizing local, attached storage systems for more efficient data handling and faster access.
- Global Threat Intelligence: Integrates threat intelligence feeds to enhance detection and response, providing up-to-date, global insights into emerging threats and vulnerabilities that could impact the organization.
These modules work together to create a comprehensive security solution that enables businesses to respond swiftly to incidents, enhance visibility across their environment, and improve overall threat management. By integrating advanced analytics and machine learning, Trellix ESM offers an intelligent, proactive approach to defending against today’s complex cybersecurity threats.
Datadog Cloud SIEM vs Trellix Enterprise Security Manager: How They Compare
Deployment Model
Just as the name implies, Datadog Cloud SIEM is a cloud-based application for cloud-native environments; which means there are no on-premise system requirements and no installation hassles other than the usual sign-up process using an internet-connected device with a supported browser. However, you’ll be required to install local agents specific to the device or service you wish to monitor for the most part. This deployment makes it ideal for organizations that don’t want to burden themselves with any resource-intensive on-premise SIEM solution.
Tellix Enterprise Security Manager is also a cloud-based system that installs local agents on servers and cloud platforms. All of the log processing is performed on the cloud server and users access the console for an account through any standard Web browser.
Data Collection and Analytics
Datadog Cloud SIEM collects logs from many different sources into Datadog. All ingested logs are first parsed and normalized (reformatted) for consistency, easy correlation, and analysis. This helps to uncover malicious activities on the network, preventing bad actors from concealing their tracks. Once logs are collected, ingested, and processed, they are available in Log Explorer. Log Explorer is where you can search, enrich, and view alerts on your logs. This makes it easy to search and filter log data across your entire infrastructure for threat detection and investigation.
Similarly, the Trellix ESM uses what it calls “Event Receivers” as data collectors which can be distributed as needed throughout your network. Valuable data is collected from hundreds of third-party security devices and threat intelligence feeds. The Trellix Global Threat Intelligence (GTI) for example brings in data from more than 100 million Trellix Labs global sensors, offering a constantly updated feed of known malicious IP addresses. The Trellix Enterprise Log Manager also collects and stores logs from various sources which are then parsed and normalized for correlation and analyses to uncover incidents and possible threats and to meet compliance requirements.
Incident/Threat Detection and Mitigation
Datadog detects threats based on rules and creates a security signal. Datadog provides out-of-the-box rules for widespread attacker techniques, mapped to the MITRE ATT&CK framework. Detection rules take full advantage of Datadog’s “Logging without Limits”, which lets you customize what logs you want to index while still ingesting, processing, and archiving everything. Rules apply to the full stream of ingested, parsed, and enriched logs so that you can maximize detection coverage without any of the traditionally associated performance or cost concerns of indexing all of your log data.
On the other hand, Trellix’s SIEM solution detects incidents and threats using a variety of tools such as McAfee Advanced Correlation Engine, Trellix GTI, and others. The Trellix GTI enables organizations to quickly identify attack paths and past interactions with known bad actors and increase threat detection accuracy while reducing response time.
The capabilities of McAfee SIEM can be greatly enhanced by integrating it with McAfee Behavioral Analytics—a dedicated user and entity behavior analytics (UEBA) solution that distills billions of security events down to hundreds of anomalies to produce a handful of prioritized threat leads and allows analysts to discover unusual and high-risk security threats, often unidentifiable by other solutions. The McAfee ePolicy Orchestrator enables faster response. McAfee also works with independent SOAR solution providers such as D3 SOAR which delivers the automation capabilities you need to respond to incidents and cyber threats. The D3 SOAR platform is the first and only platform that combines automation and orchestration with MITRE ATT&CK Intelligence.
Notifications and Alerts
Datadog’s approach to alerts and notifications is based on machine learning (ML), which it calls Watchdog. Watchdog uses ML techniques to identify problems in your infrastructure, applications efficiency, and services, and flag anomalies. Alerts in Datadog are called Monitors. Users can receive alerts using Pagerduty, Slack, and email. These can be based on nearly any metric that Datadog can capture. As a result, every alert is specific, actionable, and contextual—even in large and temporary environments. This unique approach to alerts and notifications makes Datadog stand out and helps to minimize downtime and prevent alert fatigue.
Trellix Enterprise Security Manager notifications and alerts are based on the concept of alarms. Alarms drive actions in response to specific threat events. Trellix ESM allows you to define conditions that trigger alarms and what happens when alarms trigger. Security admins can respond to triggered alarms from the dashboard. Yellow, orange, or red alerts can be generated to notify you of increasing threats against key systems and services. However, there is limited information about receiving alerts on external applications such as email, SMS, Slack, and others. This is where Datadog has an edge.
Compliance and Integration
Instead of generating the usual out-of-the-box reports that most network admins expect, Datadog’s approach to reporting aims to make metrics easily searchable, and it does excellently. Cloud SIEM is fully integrated with all of Datadog’s application and infrastructure monitoring products, which allows users to seamlessly pivot from a potential threat to associated monitoring data to quickly triage security alerts. Datadog’s 500+ integrations let you collect metrics, logs, and traces from your entire stack as well as from your security tools, giving you end-to-end visibility into your environment. Datadog integration with Slack and PagerDuty allows you to automatically loop in relevant teams when a high-severity rule detects a threat. You can also export security signals to collaboration tools like JIRA or ServiceNow.
Trellix SIEM comes with an in-built compliance framework that simplifies audits and governance. The Trellix Advanced Correlation Engine produces audit trails that support investigations and compliance reporting efforts. Trellix ESM offers integration with dozens of complementary incident management and analytics solutions, including Trellix Threat Intelligence Exchange based on endpoint monitoring and Trellix GTI which brings in data from more than 100 million Trellix Labs global sensors.
Licensing and Price Plans
Datadog Cloud SIEM pricing model is per GB of analyzed logs, per month billed annually or on-demand. An analyzed log is a text-based record of activity generated by an operating system, an application, or other sources analyzed to detect potential security threats. Datadog charges for analyzed logs based on the total number of gigabytes ingested and analyzed by the Datadog Cloud SIEM service.
TrelIix subscription licensing, which is ideal for customers who prefer renewable annual contracts
Choosing Between Datadog Cloud SIEM and McAfee SIEM
Although Datadog is a newcomer in the SIEM market, it has no doubt distinguished itself over the years in the observability space. It is therefore well positioned to meet the security needs of its existing customers and organizations that don’t have dedicated IT personnel to keep tabs on the infrastructure at a granular level. Datadog customers can leverage Datadog Cloud SIEM to aggregate and better analyze events inside their cloud-native applications without looking to third-party SIEM tools. This provides an advantage in terms of cost, implementation, and integration.
Datadog’s ability to support and integrate with more than 500 technologies makes it more versatile and adapted to many different functions, provides deeper context during investigations, and lets you cast a wider net to catch possible security issues. However, the lack of SOAR and UEBA capabilities makes it less effective in responding to modern security challenges.
Trellix is not a well-known brand in the IT security space. However, its products were inherited from McAfee. The Trellix system’s ability to leverage companion UEBA solution as well as SOAR capabilities from independent providers puts it in a better position to defend against modern security challenges. However, contrary to popular practice, the UEBA and SOAR capabilities are not an in-built feature in the SIEM package, but a separate module in the Trellix security portfolio or a third-party solution. Customers that want to use these powerful features will have to pay more, thereby increasing the total cost of ownership.
Notwithstanding, choosing between Datadog and McAfee shouldn’t be just about which is better. The focus should be on which SIEM solution best meets your business and security needs. Key factors to consider should include:
- Is the SIEM solution capable of meeting your organization’s security and compliance requirements?
- How much native support does the SIEM tool provide for relevant log sources?
- Does the SIEM solution possess the capabilities of next-generation SIEM functionalities such as SOAR and UEBA?
- What is the total cost of ownership, is vendor support available in your region, and to what extent?





