A Honeypot is an information system resource whose value lies in unauthorized or illicit use of that resource. – Lance Spitzner
As you might have guessed, the traffic which is attracted – and then diverted away or studied more closely, depending on the purpose – is of the malicious sort; that which comes from hackers, malware, and viruses.
Why do you need a honeypot on your network?
A honeypot is a security mechanism designed to detect, deflect, or study unauthorized access attempts on a network. It acts as a decoy, luring attackers away from critical systems and collecting valuable information about their techniques and objectives.
Key Benefits of Using a Honeypot:
- Early Detection of Threats: Identify malicious activities before they reach critical systems.
- Enhanced Network Security: Divert attackers from actual systems to the honeypot, reducing the risk of compromise.
- Threat Intelligence: Gather data on new attack methods, malware, and strategies.
- Cost-Effective Monitoring: Minimal resources are required to operate a honeypot compared to other security tools.
- Training and Research: Security teams can study real-world attack scenarios in a controlled environment.
Types of Honeypots
Honeypots can vary based on their purpose and deployment complexity:
- Production Honeypots:
- Deployed within a live network to improve security by distracting attackers.
- Provides real-time threat analysis.
- Research Honeypots:
- Used by researchers to collect data on the behavior of attackers and study emerging threats.
- Often more complex and detailed.
- Low-Interaction Honeypots:
- Simulates limited services and responses.
- Easier to deploy but provides less detailed information.
- Ideal for detecting automated attacks or basic reconnaissance.
- High-Interaction Honeypots:
- Simulates real systems with fully functional services.
- Engages attackers more deeply, offering richer data on tactics and tools.
- Requires more resources and careful management to prevent exploitation.
- Client Honeypots:
- Actively seek out malicious servers by imitating vulnerable clients.
- Useful for detecting attacks targeting end-user devices.
Types of Data That Honeypots Record
Honeypots collect a wide range of data to enhance threat detection and analysis:
- Attack Signatures and Patterns: Identify specific behaviors or sequences used by attackers.
- IP Addresses and Geolocation: Log the source of the attack, providing insight into potential origins.
- Exploited Vulnerabilities: Capture details about the specific weaknesses attackers attempt to exploit.
- Malware Samples: Record and isolate malicious software for analysis and defense improvements.
- Command and Control (C2) Communications: Monitor how attackers communicate with their systems, revealing infrastructure.
- Tactics, Techniques, and Procedures (TTPs): Understand how attackers operate, from reconnaissance to exploitation.
- Time and Duration of Attacks: Track when attacks occur and how long they persist, offering insights into attacker persistence and strategy.
By deploying a honeypot, organizations can gain deeper insights into their threat landscape, enhance their defensive strategies, and stay one step ahead of potential attackers.
Pros & Cons of Honeypots
Pros:
- Early Detection of Threats: Detect unauthorized access or suspicious activity before attackers target critical assets.
- Improved Threat Intelligence: Valuable information about attackers’ techniques, tools, and objectives.
- Cost-Effective Monitoring: Compared to comprehensive security solutions, honeypots are relatively low-cost.
- Diversion of Attackers: Honeypots reduce the likelihood of actual data breaches or system damage.
- Isolation of Malicious Activity: Security teams can study malware and attack strategies without risking the broader network.
Cons:
- Limited Scope: Honeypots only detect threats that interact directly with them.
- Potential for Exploitation: If improperly configured, attackers might use the honeypot to their advantage.
- Resource Intensive (High-Interaction Honeypots): High-interaction honeypots require significant resources to operate effectively.
- False Sense of Security: Organizations may overestimate the protection offered by honeypots.
- Skilled Attackers May Avoid Them: Advanced attackers can recognize honeypots and avoid them entirely.
Where to find honeypot installation instructions
In this article, we will focus on the strategy needed to successfully implement a honeypot on your network rather than the actual step-by-step installation of the software solutions themselves. But, for those who do need to see the honeypot solutions being installed, there are some great sites and videos out there. Our recommendations would be:
Windows – for most of the world, this is the operating system (OS) of choice. And at Analytical Security, you get to set up a honeypot for this operating system and incorporate the cloud (Amazon AWS) in your network.
Linux – if you are the hands-on, Linux type of person who loves to go under the roof and tinker under the hood, here is a good site that shows how a honeypot is installed in that OS environment: Hacking Blogs.
Of course, in today’s world of YouTube tutorials, channels, and online digital communities like GitHub, it really isn’t that difficult to install a honeypot. It is the strategy and management that is truly the challenging part.
What are the best honeypot software solutions out there?
For anyone that is searching, there is a myriad of software solutions to choose from when it comes to honeypot solutions. Below, we have three of the more popular ones for you to choose from:
KFSensor
A Windows-based honeypot that starts monitoring your network as soon as it has been set up. It is a full-fledged toolkit that was designed to mimic a honeypot – among many other useful features. But, the endearing character of this host-based Intrusion Detection System (IDS) is that it is highly configurable which makes it easier for administrators to defend their individual networks.
Glastop
Best thing about this honeypot is that it is an open-source software solution which means that, like all collaborative solutions, it is the brainwork of many experts that will also continue to evolve and improve over time.Glastopf is a Python web application virtual honeypot that is a low-interaction network emulator. An interesting feature of this tool is that it can even emulate applications that are vulnerable to SQL injection attacks.
Ghost USB
What makes this honeypot stand out is that it specifically focuses its attention on malware that spreads via USB storage devices. This is a big deal considering that USB drives used by employees and authorized users continue to cause serious concerns.
Once installed, Ghost USB emulates a USB storage device and broadcasts itself over the internal network, intending to trick any malware – that propagates using similar devices – into infecting it. Once detected, and secretly observed, it becomes easy for administrators to take the necessary steps and precautions.
Although these three honeypot solutions cover most network security needs, you can find a more exhaustive list of solutions for various networking and cybersecurity needs here.
Honeypot strategies
There are two types of honeypot implementation strategies you can adopt:
Low-interaction method
In this method you will be using fake data, folders, and databases as bait with the intent of monitoring attacks to see what would happen in a real-life data breaching scenario. Of course, they would have access to other peripheral information sets like IP addresses, usernames, and passwords – over which the administrators keep a keen eye. This is what you would want to do if you wanted to test some aspects of your internal network’s peripheral penetrability and the security of your authorization processes, for example.
High-interaction method
In this setup you would allow the attackers to interact with data, software (including OS), services, and hardware that appear to be as realistic as possible. The intent here is to gauge and capture the skills of the attackers. This setup is mostly used in research scenarios where the results of the studies are used to improve the defense capabilities of anti-viruses and anti-malware.
Take care!
Right, now let us look at some issues you will need to be aware of and careful about before you go about implementing your honeypot.
Legal issues
Whether it is to cover your behind in case you get sued by your clients for loss of their data or to make sure any charges you bring against intruders stick, you will need to have your legal wires untangled. While we are no legal entity we can still tell you that you will need to be aware of and careful with these three legal aspects:
Entrapment – the intruders can claim they didn’t know they weren’t supposed to access your internal network or the assets and data on it. They could counter-claim that you didn’t label it clearly enough and, taking it even farther, use the “entrapment” defense.
Privacy – implementing a honeypot needs to be done with extreme caution; this point cannot be stressed enough. One port left open by mistake or an administrator account that has been compromised could open the floodgates for attacks on your main network. This, in turn, could put the personal data of any of your clients in jeopardy. Should the attackers manage to share it with the world, you could find yourself the target of a lawsuit for breach of trust because the clients say they didn’t give you permission to share their data.
Liability – another way you could get yourself (or your network) in hot water is if the intruders decide to flip the crime right back at you by storing malicious content on your compromised servers and, even worse, guide legitimate traffic towards your IP addresses. Storing and distributing content like child pornography could make you see the inside of a courtroom real fast.
Word of advice: if you find any such incriminating content on your servers or being accessed via your network, the first thing you need to do is contact the authorities.
Being discovered – by the intruders
Setting up a honeypot environment requires anonymity for the real network that is behind it. Nothing would pose more of a risk to it than the intruders’ discovering that it is indeed a honeypot they are dealing with rather than the real deal.Because, with that realization, they could take it as a challenge to go on to find a way to breach the main internal network. And so, it becomes crucial that no telltale signs alert them to the fact that they are being monitored on a honeypot network. The common signs that usually give away the ploy – and should thus be avoided – are:
If the network is too easy to attack, or gain access to, it will make them suspicious or make them think it isn’t relevant enough to warrant their efforts.
If there are too many unnecessary services running, or one too many ports are open, it would be contrary to reality where normal Internet-facing devices are usually stripped of non-relevant services and only have the required ports open.
If the configurations of the running software solutions are still in their default settings, which almost never occurs in a live network.
If there is little-to-no traffic passing through the network indicating that there is nothing of interest on it and yet belongs to a major brand.
If too much effort has been put into making it look like they walked into a candy store with folders named “Passwords,” “Confidential,” or “Usernames.”
If the servers connected to the network appear to be empty or there is a lot of free diskspace it would show that they are of no value.
In short, your honeypot network and the devices on it should emulate a real-life connection, albeit with fake data and traffic. Put yourself in the attackers’ shoes and look at your network from their perspective.
Protect yourself well!
Don’t forget that you are stepping into the lion’s den when you opt for a honeypot setup. Therefore, here are a few points you need to always make sure are covered:
Never use real data – it doesn’t matter what sort it may be, create garbage data that looks real and use it as bait.
Never connect your honeypot to your main network – there should be no way that the attackers could hop on to your network via your honeypot; make sure it is isolated and keep it that way.
Use virtual machines – the safest hardware you can put on your honeypot is a virtual one; if you get hit, all you need to do is reboot and recreate it.
Firewalls and routers should be the only way to get to your honeypot – all incoming traffic should pass through them before they get on the fake network; configure ALL port numbers on them to point to the honeypot.
Usernames and roles should be unique to the honeypot – it would be insane to use the same ones that have access to your main network; create new credentials and use them for the honeypot only.
Always test, test, and test – never let a honeypot go live without throwing everything you have at it; in fact, invite experts to try to break through it and onto your main network before you let it face the Internet.
A good strategy to adopt here is to make sure no one except an administrator can access the honeypot and even then, they should use a dedicated login account that has zero privileges on the real network. Or, better yet, one that doesn’t exist on it at all.
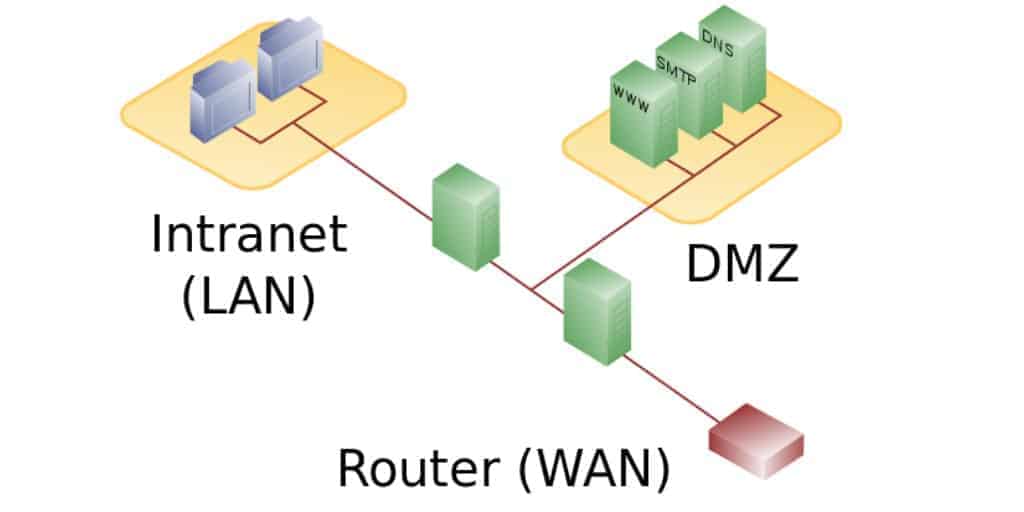
Placement of the honeypot
Arguably, the ideal place to create your honeypot is in the demilitarized zone (DMZ). This is the area that is out of your main network, but still behind a router which faces the Internet.
Image attribution: en:User:Pbroks13 [Public domain], via Wikimedia Commons
Then again, you should know that not all attacks come from the Internet. In fact, studies have shown that the statistics on “insider threats” – those that come from behind your firewalls, and by people who are authorized to use your network – is quite scary at over 30 percent.This means it makes sense to also install an internal honeypot. This way, network administrators will have an insight into the malicious attempts – or the simple human errors causing them.The following video will help explain the purposes, advantages, and drawbacks of placing a honeypot in the various locations on a network:
Honeytokens
A good way to observe the tactics of an intruder is to place a honeytoken on a control server or database. Honeytokens are files or data sets that would appear to be interesting to the attacker but are actually fake replicas of the real deal.
The honeytokens can also be embedded files or data sets in what would otherwise appear to be a legitimate physical server or database. It makes it easy for administrators to keep track of the data in case it is stolen – like whom it was stolen from and how it was stolen – as a different honeytoken is placed in each location.
Examples of this sort of honeytoken include email addresses and usernames or login IDs. If an attacker gains access to these pieces of information, it would be easy to know which database they have breached which would, in turn, help in figuring out how they managed to do it.
When used properly, and set up in a diverse number of ways, honeytokens and honeynets (two or more honeypots on the same network) can draw a pretty clear picture for the administrators.
Once the threats have occurred and then identified by the honeypot, alerts can be configured in response to attempts at access, modification, or deletion of the data or even when malicious packets and payloads have been discovered on the network.
Final thoughts on establishing a honeypot on your network
As we have seen, a simple honeypot will help you fight off attacks by drawing a clearer picture of your attackers and the methods they might use to attempt a breach. Placing it in the right position and configuring it well will help strengthen your network’s security, and any errors in doing so could lead to the demise of your main network.
And so,…
Always remember: a honeypot is, in itself, NOT a network security solution. It is in fact a tool that serves as a means to reach a secure network solution. Learn from it and tighten the screws using other network monitoring and protection solutions while making sure you have other live network security solutions as backups.
How to Set Up a Honeypot FAQs
Why are honeypots deployed outside of the firewall?
Placing honeypots outside the firewall avoids having to create firewall rules that direct traffic to them. The firewall will still provide effective protection for the network should a hacker break out of the honeypot.
Is a honeypot an IDS?
There are several types of honeypots. One located within the network, alongside production servers forms part of an IDS strategy.
Is honeypot a software or hardware?
Strictly speaking, a honeypot is an appliance. Software solutions are called virtual honeypots.
Our methodology for selecting honeypot management tools
We reviewed the market for deception technology software and analyzed the options based on the following criteria:
A system that combines constant anomalous network activity with deception strategies
An application emulator with settings that mimic different vulnerable systems
Coverage for all devices that are known targets of malicious activities
A service that guides honeypot deployment
Full activity logging for data protection standards compliance
A risk-free assessment period provided by a free trial or a money-back guarantee
Effective tools that are worth paying for and are reasonably priced