LogRhythm is one of the world’s most innovative SIEM solutions with the option to install it on-premises or access it as a cloud service. SIEM software is very complicated and also very powerful. However, the designers of the package have put a lot of thought into making the system easy to use by including the Deployment Center, which deploys wizards to guide the user through data investigation tasks.
All about SIEM
SIEM is a form of Intrusion Detection System (IDS). The acronym stands for Security Information and Event Management. The term indicates a blended strategy made up of two data investigation approaches.
Security Information Management (SIM) is the practice of looking through log files for indications of malicious activity. This is what is termed a Host-based Intrusion Detection System (HIDS).
Security Event Management (SEM) involves looking through passing traffic for unauthorized activity. This is similar to the Deep Packet Inspection (DPI) carried out by advanced firewalls. SEM is a Network-based Intrusion Detection System (NIDS) that operates on the header data of passing packets to extract information about the activities of users.
The advantage of SEM is that it is very quick. If suspicious activity is spotted, that activity can be acted on right away. However, this is not very effective at combatting stealth hacker activities, such as Advanced Persistent Threats (APTs). In an APT, a hacker group gains access to the system and is able to search through files and even use system resources for its own ends without being detected. The hacker evades detection by operating through regular user accounts.
SIM can identify unauthorized actions performed by legitimate users. This not only spots APTs but also blocks insider threats. A modern data loss event can only be identified by looking at a series of actions that each individually seems harmless, but when examined together indicate an attack. The big problem with SIM is that it can take time to build up a full picture of activities. By the time a suspicious pattern of activity becomes visible, the company’s data has probably already been stolen.
By combining SIM and SEM, SIEM systems can improve the speed of threat identification while also being able to see attacks that evade detection by traditional cybersecurity measures. SIEM is not meant to replace firewalls and other boundary defenses; it aims to identify and spot the types of attacks that firewalls can’t block.
About LogRhythm
LogRhythm, founded in 2003 by Chris Petersen and Phillip Villella, was a U.S.-based company that specialized in security information and event management (SIEM) solutions. Established in Boulder, Colorado, LogRhythm’s initial goal was to provide businesses with effective and efficient ways to detect and respond to cyber threats through log data analysis.
Over time, the company expanded its offerings to include network traffic analysis, endpoint monitoring, and advanced threat detection, helping organizations strengthen their overall security posture. Through the years, LogRhythm earned a reputation for delivering reliable, scalable solutions used by various sectors, including finance, healthcare, and government.
As the cybersecurity landscape continued to evolve, LogRhythm integrated advanced technologies like machine learning and behavioral analytics into its platform to improve threat detection and response capabilities. This innovation helped the company build a strong customer base globally.
In 2021, LogRhythm merged with Exabeam, another leading player in the SIEM space. This merger combined Exabeam’s strengths in user and entity behavior analytics (UEBA) with LogRhythm’s acclaimed SIEM platform. The goal was to create an integrated solution that would provide enhanced threat detection, quicker response times, and more efficient investigation capabilities for organizations.
The merger aimed to deliver a more comprehensive security offering by blending both companies’ strengths in data collection, threat detection, and automation. The CEO of LogRhythm, Christopher O’Malley took the helm of the new company, which continued the Exabeam name. With its corporate identity gone, the LogRhythm name lives on in the name of LogRhythm SIEM, which is now a core component of the Exabeam Security Operations Platform.
With the Exabeam merger, LogRhythm aimed to leverage improved cloud-native technologies, providing clients with more advanced analytics and a deeper understanding of security events. The merger also positioned LogRhythm and Exabeam as a formidable competitor in the cybersecurity industry, offering a powerful suite of tools to help organizations combat increasingly sophisticated cyber threats.
LogRhythm SIEM overview
The full title of LogRhythm SIEM is the LogRhythm NextGen SIEM Platform. The service is composed of five essential elements plus two optional modules. These are:
- NetMon – A live network monitor that extracts important packet information for analysis.
- SysMon – A distributed data collection agent and endpoint monitor.
- AnalytiX – A log manager.
- DetectX – The threat hunting module.
- RespondX – A Security Orchestration and Response (SOAR) system.
- NetworkXDR – An optional module that provides enhanced network monitoring.
- UserXDR – An optional module that is a user and entity behavior analytics (UEBA) solution.
Each of these modules is explained further below.
NetMon
NetMon is the main source of live network traffic data for the SIEM analysis engine. It uses Deep Packet Inspection (DPI) to read the metadata in packet headers. This enables the service to log traffic per application, per user, and per endpoint. This information is formatted according to the SmartFlow protocol for analysis when uploaded to the central analytical engine. This system gathers network stack perspectives all the way from Layer 2 to Layer 7.
The NetMon module doesn’t just gather data for analysis; it also acts. It can reconstruct email attachments as they travel in a series of packets, spotting malicious content and deleting them if there is time or updating their status at their destination to indicate a problem.
NetMon has its own network monitoring screens in the LogRhythm dashboard that include status alerts and adjustable thresholds. The data screens are customizable and network traffic data can also be fed to other applications through an API. Traffic data includes the source and destination of external connections, identified communication with botnet controllers, and an updateable list of banned IP addresses.
SysMon
SysMon is the main data collection system, of LogRhythm. It has components on each monitored endpoint and it also has a central controller. The Sysmon controller receives data from each agent and sends back instructions for responses.
The SySMon agents install on endpoints and servers to collect log data and generate proprietary LogRhythm stats and then send them to the central controller.
Tasks include file integrity monitoring to make sure that local files are not tampered with. The central SysMon performs the same duty with gathered data. The agents also monitor processes on each machine, performing local safety checks including registry protection, attached device monitoring, and blocking malicious user access locally.
The SysMon agents also contribute to live network traffic monitoring by logging each connection made or accepted by the monitored device. All activities on the devices are logged against the user account that was active at the time.
AnalytiX
AnalytiX is the log manager of LogRhythm. It receives all of the log data channeled by SysMon and puts those records into a common format before sending them to the Dashboard for display and filing them.
While reformatting records, AnalytiX flags suspicious actions, and links events. The log files are stored in meaningful directories and a search engine component supplied by Elasticsearch makes these raw logs accessible for direct access by the user and any other interested party, such as a standards compliance auditor.
DetectX
DetectX is the threat hunter of LogRhythm. It takes the structured files created by AnalytiX and applies the services detection rules to them. This component is adaptable to the requirements of data security standards. The rules for detection are constantly updated by a live threat intelligence feed.
The DetectX process identifies malicious activities and launches appropriate workflows to shut them down. Those actions will be implemented by RespondX.
RespondX
RespondX is the Security Orchestration, Automation, and Response (SOAR) unit of LogRhythm. It links to other system services such as firewalls and access rights managers to gather extra data and also implement response workflows.
The RespondX mitigation methodology is called SmartResponse Automation. It alters firewall rules to block suspicious IP addresses and interfaces with user access systems to suspend accounts.
NetworkXDR
NetworkXDR is an optional module that enhances the detection capabilities of NetMon. It is able to spot activity on several points of the network that indicate a lateral attack. It uses machine learning to establish a baseline for regular network activity rather than imposing a threshold level that could be too tight.
UserXDR
UserXDR is an optional module that enhances the user behavior monitoring of SysMon. This is a User and Entity Behavior Analytics (UEBA) service that applies AI machine learning to establish a pattern of normal behavior by each user and user group.
The UserXDR system looks for abandoned accounts, which are security weaknesses. It is also able to manage the permissions given to users who connect with their own devices.
LogRhythm SIEM dashboard
The dashboard for LogRhythm SIEM is web-based and can be accessed from any of the following web browsers:
- Google Chrome
- Microsoft Internet Explorer
- Microsoft Edge
- Mozilla Firefox
The console of the SIEM is tabbed with the Dashboard being one element of the layout. Other tabs access utilities such as alert lists and reports. Two further tabs at the bottom of the screen give access to a task list and direct access to logs for searches.
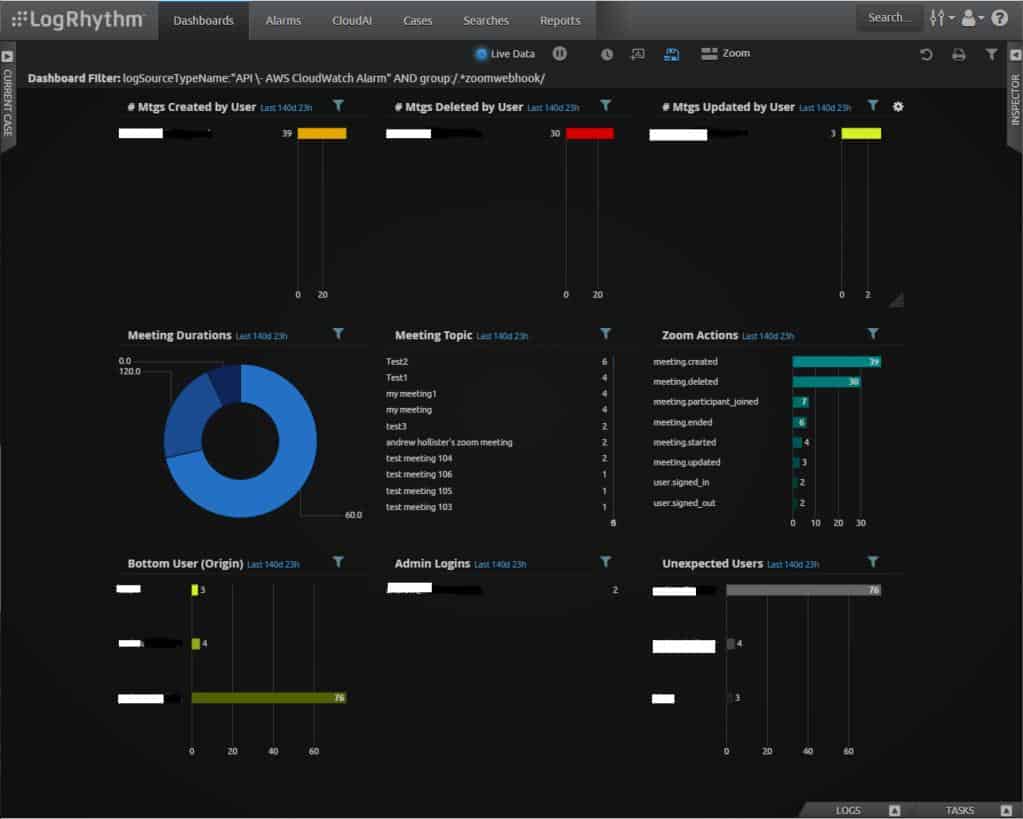
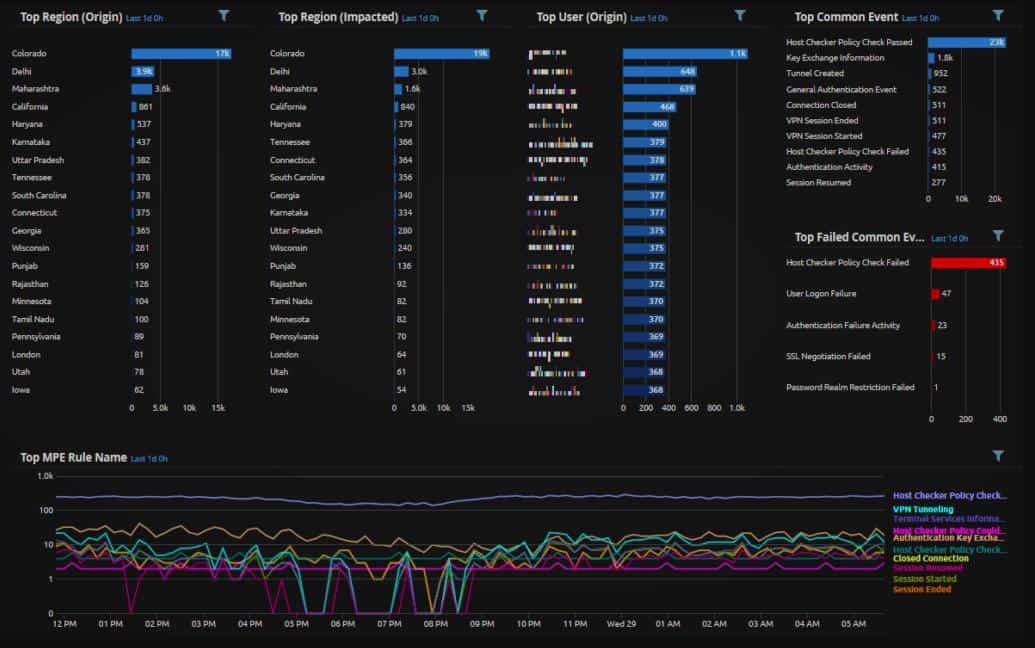
The background of the dashboard is black with lighter colors used for text and graphics. Each screen in the dashboard offers a mixture of graphs and text panels, as shown in the example of the Analyze dashboard below.
Each element on a screen, such as the Analysis dashboard offers access to a details screen. Elements in a league table panel are active links to details screens. The screens in the Analysis dashboard all offer data filters so visualized data can be isolated down to a particular device or user.
LogRhythm SIEM configuration options
LogRhythm SIEM software runs on Windows Server 2012 and later. LogRhythm can also supply all of the software for the LogRhythm NextGen SIEM Platform pre-loaded onto an appliance. The system is also available as a cloud-based service, which includes processing power and storage space.
LogRhythm SIEM compliance reporting
The LogRhythm system can be adapted to focus on compliance with specific data security standards. These compliance requirements do not replace the standard procedures of the LogRhythm SIEM – any administrator still has access to all of the standard screens and services. The compliance adaptations come in the form of extra modules, which are called compliance automation modules.
Modules are available for the following standards:
- 201 CMR 17.00
- BSI-IT Grundschutz
- CIS Critical Security Controls
- DoDi 8500.2
- FISMA
- GDPR
- GLBA
- GPG 13
- HIPAA, HITECH & MU
- ISO 27001
- MAS-TRMG
- NEI 08-09 Rev 6
- NERC CIP
- NIST 800-53
- NIST Cybersecurity Framework
- NRC Regulatory Guide 57.1
- PCI DSS
- SOX
- UAE-NESA
As well as providing security monitoring controls adjustments to comply with the selected standard, a compliance automation module also adjusts auditing systems to fit with standards requirements. The module includes a library of report formats that are needed when generating compliance proof. LogRhythm distributes updates to these modules should any of the standards change.
Alternatives to LogRhythm SIEM
The LogRhythm SIEM is hard to beat. The system is comprehensive and includes automated response mechanisms, which can be great time savers. However, LogRhythm isn’t the only SIEM available on the market and anyone buying new security software will probably want to assess a number of alternatives.
To find out more about SIEM and the best systems that compete in the market, take a look at the Best SIEM Tools. If you don’t have time to read that guide, here is our list of the ten best alternatives to LogRhythm SIEM.
- ManageEngine EventLog Analyzer (FREE TRIAL) A log-based security analysis system that provides the SIM part of SIEM. This could be paired with OpManager to provide live network data and create a full SIEM. It installs on Windows and Linux. Access the 30-day free trial.
- Datadog Security Monitoring A cloud-based service that requires agent software to be installed on-site. This security system can be paired with a full network monitoring system.
- McAfee Enterprise Security Manager A well planned SIEM that includes log management and live traffic monitoring. This security system is enhanced by a high-quality threat intelligence feed. Installs on Windows and macOS.
- Fortinet FortiSIEM A cloud-based SIEM system that deploys agent software on monitored devices to provide continuity during network downtime. It includes a range of detection strategies, such as UEBA, and integrates automated defense responses.
- Rapid7 InsightIDR An impressive cloud-based security service that ensures continuity of service through on-site agent modules. It includes UEBA and automated threat response.
- OSSEC A free open-source host-based intrusion detection system that provides SIM functions. It will accept live network data as additional input but that needs to be supplied by a third-party tool. Installs on Windows, macOS, Linux, and Unix.
- Heimdal Threat Hunting and Action Center This cloud package is a coordinating threat detection and response service for Heimdal on-premises cybersecurity products. The tool unifies endpoint security and network detection systems among others. The platform also provides vulnerability scanning.
- SolarWinds Security Event Manager A tool that provides log management for security data analysis. It doesn’t include network monitoring but could be enhanced with a third-party feed. This software installs on Windows Server.
- IBM QRadar A security intelligence platform that includes a SIEM module. Elements of the SIEM include vulnerability scanning, a threat intelligence feed, live traffic analysis, and log management functions. It runs on Windows Server.
- AT&T Cybersecurity AlienVault Unified Security Management A well-regarded SIEM system that has the financial backing of a very large multinational. It runs on Windows and macOS.