Network segmentation is a strategic approach in network architecture that involves dividing a large computer network into smaller, more manageable segments or subnetworks. Each segment functions as an individual, isolated unit, and administrators can implement specific policies and controls for each one. This division allows for better management of network resources, more efficient traffic flow, and, crucially, enhanced security.
Here is our list of the best network Segmentation tools:
- Cisco Secure Workload EDITOR’S CHOICE This application access control system comes from the masters of network segmentation. Offered as a SaaS platform or delivered on a network appliance.
- VMware NSX Implement network virtualization with this package from one of the leading hypervisor producers. This is a cloud-based service.
- Illumio This cloud platform provides Zero Trust Segmentation, which is an application-level fencing mechanism that is particularly strong at protecting cloud services.
- Faddom This IT asset documentation system provides a network discovery service that will detail each piece of hardware in an inventory and automatically draws up a network map.
- AlgoSec This platform offers a number of access control methods, which include ZTA for applications and network segmentation. This is a cloud-based service.
- Tufin This cloud-based system allows you to merge your network security with cloud services protection over a virtual hybrid network.
- Akamai Guardicore Centra This segmentation solution can be accessed as a SaaS package or on a network appliance and it interprets your security policies into network device configurations.
- Fidelis Halo This cloud system provides cloud security posture management strategies.
The primary benefit of network segmentation lies in its ability to restrict and control the movement of data across the network. By segmenting the network, organizations can limit access to sensitive data by placing it in isolated sections that are accessible only to authorized users or devices. This helps to minimize the risk of unauthorized access, whether from external hackers or potentially malicious insiders.
Segmentation builds virtual walls. For instance, segments containing critical business information, such as financial records, proprietary data, or customers’ personal details, can be shielded from other areas of the network. Thus, the exposure of sensitive data to potential threats is reduced.
Network segmentation also plays a key role in improving network performance and reducing the impact of security breaches. By isolating different parts of the network, an attack or failure in one segment can be contained, preventing it from spreading throughout the entire network.
This technique makes it more difficult for attackers to move laterally and access other parts of the network once they have infiltrated one segment. Additionally, segmentation enables the application of tailored security policies for different segments, ensuring that sensitive data and critical systems are given higher levels of protection.
Ultimately, network segmentation is an effective strategy for enhancing both network security and efficiency, helping organizations prevent data breaches, reduce vulnerabilities, and improve overall control over their IT infrastructure.
The primary goal of network segmentation is to enhance security by limiting the spread of threats and minimizing the impact of security breaches. By isolating sensitive data and critical resources in a separate segment of the network, organizations can prevent unauthorized access to these assets, thus reducing the risk of data breaches, cyber-attacks, and other security threats.
Segmentation can be accomplished using a variety of technologies, such as virtual LANs (VLANs), network firewalls, access control lists (ACLs), and software-defined networking (SDN). In some instances, automated tools and software can be used to help manage and enforce segmentation policies. In this article, we’re going to review the seven best network segmentation tools. Hopefully, this will guide you in the process of choosing the right one for your organization.
The Best Network Segmentation Tools
Our methodology for selecting a network segmentation tool
We reviewed the market for network segmentation systems and tested tools based on the following criteria:
- A system that can extract hardware status data from network equipment and computers
- Preparation for security zoning
- Methods for implementing microsegmentation
- Methods to implement segmentation with access control lists (ACLs)
- Nice to have security policy assurance and consistent implementation
- A free trial or demo to enable a full assessment before paying
- Value for money from a comprehensive and reliable tool that is offered at a fair price
1. Cisco Secure Workload
Cisco Secure Workload is a cloud-native workload protection solution designed to provide visibility, compliance, and threat protection for multi-cloud workloads. While it is primarily a security tool, it can also be used as a zero trust-based network segmentation tool to help organizations improve their network security posture.
Key Features:
- Zero trust access
- Microsegmentation
- European Data Residency enforcement
- SaaS option
- Network appliance option
Why do we recommend it?
Cisco Secure Workload provides a method to plan and implement segmentation, with its main method being access control lists (ACLs). Cisco has been the industry leader in the development of ACLs and they form a major section in the CCNA course, so it is nice to get the technique delivered by such an authoritative source.
Cisco Secure Workload can be used for network segmentation by creating security zones within the environment. Security zones are logical groupings of workloads based on their security requirements, such as compliance regulations or sensitivity of the data they handle. By grouping workloads with similar security requirements, organizations can apply consistent security policies and controls across each security zone. For example, a security zone may require all workloads to have the same level of access control policies or encryption requirements.
Cisco Secure Workload uses security zones to implement network segmentation in an environment. Workloads with similar security requirements are grouped into a security zone, and security policies are applied to each zone. The security policies may include access control policies, encryption requirements, and other measures to protect the workloads within the zone.
Cisco Secure Workload also provides visibility into the traffic flowing between security zones, allowing administrators to monitor and control traffic to prevent unauthorized access or data leakage. The security policies are enforced by Cisco Secure Workload’s security controls, which may include firewalls, intrusion prevention systems, and other security measures. Administrators can manage and monitor the security policies across all security zones from a centralized management console, allowing them to quickly identify and address any security risks within their environment.
Who is it recommended for?
This system is suitable for any business that has sensitive data to protect and needs different levels of security within the network. The package helps you set up zones of trust and then monitor all activity to ensure that you got the boundaries right.
Pros:
- Deployment options between a SaaS package or the software on a network appliance
- A guided way to implement segmentation with ACLs
- Continuous monitoring to confirm security measures
- Alerts for security failures
- Security review mechanism
Cons:
- No price list
The pricing and licensing plan for Cisco Secure Workload varies depending on the deployment model and the features you require.
EDITOR'S CHOICE
Cisco Secure Workload is our top pick for a network segmentation tool because it is provided by Cisco Systems, the authority on access control lists, which are the key mechanisms for creating effective segmentation. This package can be used to create zones of trust and allow different access across the network to resources according to the origin of the traffic. The system helps you set up DMZs and allows the management of both employee and customer traffic on a single, but segmented, network.
OS: Cloud-based
2. VMware NSX
VMware NSX is a software-defined networking (SDN) and security platform designed to virtualize networking and security for data center, cloud, and enterprise environments. NSX decouples network and security services from underlying physical infrastructure, providing a virtual networking layer that can be abstracted from the physical network.
Key Features:
- Software define network
- Addressing overlay
- Central management of traffic routes
- Merges networks and internet links
Why do we recommend it?
VMware NSX provides an innovative solution to the complexities of segmentation that gets even more convoluted for hybrid networks and multi-tenanted systems. The virtualization of the network makes the separation of sections of the network possible to virtualize in the console and then the VMware software sorts out that aspiration into actual real-world implementation.
VMware NSX can be an effective tool for network segmentation, providing enhanced network security and control within virtualized environments. It provides a range of network security features such as distributed firewalls, network isolation, and micro-segmentation that enable the creation of logical network segments within a virtualized infrastructure. This helps to improve network security by reducing the attack surface and limiting the spread of threats within the network.
NSX uses software-defined networking (SDN) to abstract network functionality from hardware and create a virtualized network overlay. This enables network administrators to create multiple virtual networks that are logically separated from each other, even if they share the same physical infrastructure. Each virtual network can have its own set of security policies and controls, which can be enforced at the virtual machine level, providing granular security and control.
NSX also provides micro-segmentation, which allows administrators to define security policies at the individual workload level, rather than just at the network level. This means that each workload can be isolated and protected, even within the same virtual network segment. This can be particularly useful in protecting sensitive workloads and preventing lateral movement within the network.
Who is it recommended for?
This system is beneficial for any company that runs a network and wants to implement zones of trust through segmentation. The system gets more necessary with more complicated networks. It is particularly useful for making sense of hybrid networks, WANs, and networks that carry different types of traffic over the same infrastructure.
Pros:
- Creates a virtual network for presentation
- Interprets a virtual design to an implementation on the actual network
- Provides WAN management
- Integrates remote workers and cloud services into a corporate network
Cons:
- No price list
NSX Cloud is licensed on a per-virtual machine (VM) basis, and the price is based on the number of VMs that will be protected with NSX. In addition to the base licensing costs, there may be additional costs for support and maintenance. VMware offers various support plans, including Basic, Production, and Premier support, which provide different levels of technical support, software updates, and other benefits.
3. Illumio
Illumio is a network segmentation platform that provides comprehensive visibility and control over the network traffic flowing across an organization’s infrastructure. It works by creating a software-defined perimeter around each workload or application, enabling fine-grained segmentation and protection of network assets.
Key Features:
- Zero Trust
- Access control list
- Security monitoring
Why do we recommend it?
The Illumio platform provides a menu of network security services that includes Illumio Core for on-premises and cloud hybrid networks and Illumio CloudSecure, which focuses only on cloud systems. Both of these network-centred products implement Zero Trust Access through segmentation and creating zones of trust.
Illumio’s approach to security is based on separating it from the underlying network and hypervisor technology. By doing so, their technology can be applied to various computing environments, such as private data centers, private clouds, and public clouds. This enables them to implement a zero-trust micro-segmentation strategy that spans from endpoints to data centers to the cloud, which effectively prevents cyber-attacks and the proliferation of ransomware.
Illumio’s network segmentation technology is based on a Zero Trust model, which means that it assumes that no user or device can be trusted until it has been authenticated and authorized. This model allows Illumio to provide granular access controls to every workload, application, and user on the network, regardless of their location or device type.
One of the key benefits of using Illumio as a network segmentation tool is that it provides continuous monitoring and threat detection capabilities, helping organizations to detect and respond to network security incidents in real-time.
By leveraging machine learning and behavioral analytics, Illumio can identify and isolate malicious traffic or behavior, reducing the attack surface and minimizing the risk of data breaches and cyber-attacks. Illumio’s segmentation capabilities are highly customizable and can be tailored to meet the unique needs of any organization. The platform can be easily integrated into existing security infrastructure, enabling organizations to leverage their existing investments in firewalls, intrusion detection systems, and other security tools.
Who is it recommended for?
Illumio offers the same service as the Cisco product on this list because it operates through implementing access control lists to interpret a design formed in the cloud-based dashboard. Annoyingly, like most of the providers on this list, Illumio doesn’t publish its prices. However, the company’s products appeal to some large organizations, such as Oracle, Cathay Pacific, and Morgan Stanley.
Pros:
- Cloud security
- Manages hybrid systems
- Segmentation and microsegmentation
Cons:
- No price list
Illumio’s pricing and licensing plans are not publicly disclosed, as they are customized based on the specific needs and requirements of each organization. However, they do offer a free trial for organizations to test and evaluate the product before making a purchase decision. Illumio’s licensing model is based on the number of workloads or endpoints being protected, and they offer both perpetual and subscription-based licensing options. They also offer a range of support and professional services options, including technical support, training, and consulting services, which may be included as part of the licensing agreement or purchased separately.
4. Faddom
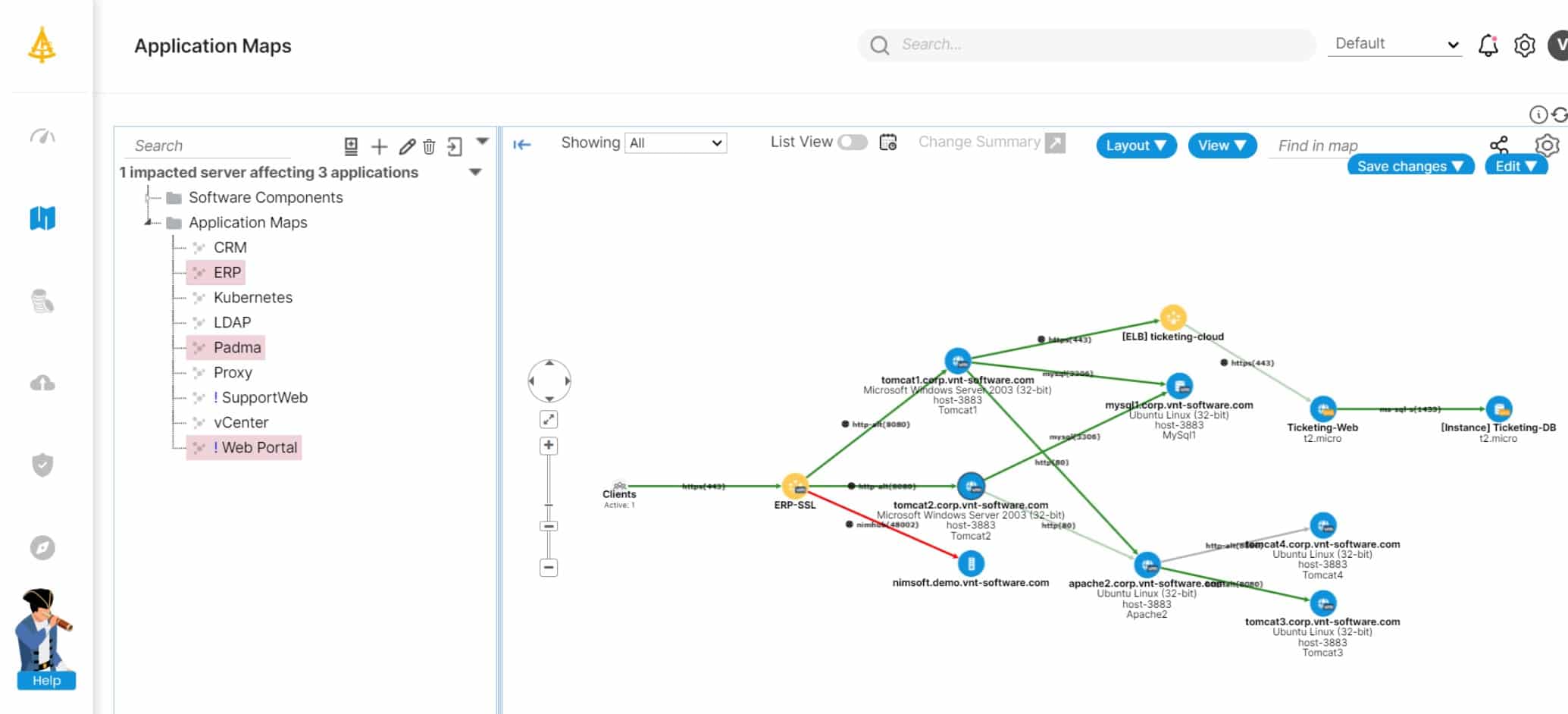
Faddom is a tool that you would use when planning your network segmentation strategy rather than a utility to implement segmentation. The fundamental mechanism for implementing segmentation lies with access controls that are implemented within your network devices. In order to plan out the access control entries (ACEs) that will implement your segmentation, you need to be able to visualize how traffic flows between the different areas of your network.
Key Features:
- Network discovery
- Network mapping
- Planning tool
Why do we recommend it?
Faddom won’t implement segmentation for you but it provides a network map that is an essential tool for implementing segmentation manually with access control lists. You need to plan your IP address applications in subnets and then you can apply all the allow and deny rules to groups of endpoints.
When writing out ACLs, you need to be able to see where the devices on your network are, what IP address ranges they have, and which devices the traffic has to pass through in order to move from one zone to another. This is where Faddom comes in.
This tool will scan your network and identify all of the devices on it. It details all of the attributes of each device and creates an asset inventory reentry for it. This information includes IP and MAC addresses. The service then creates a network map from the information that the tool reads from the definitions of each device interface.
Whatever method you use to create your network segmentation, you will need a network map. Even if you use an automated system to generate your ACLs from written security policies, you should then go on to test the controls over traffic passing between zones and that testing will be greatly assisted by the map that Faddom provides.
Faddom gives you a definitive live map of your system. You can print it off, draw your zones on it, and then work out which devices and which interface you need to update in order to create your network segmentation.
Who is it recommended for?
If you don’t want automatically generated ACLs but you want to write them yourself, you are going to need to see the location of all of your endpoints relative to all of your switches so you know which interfaces you should write your ACLs on and how to filter traffic – you will probably need to sort out your IP address pools first.
Pros:
- Helps with planning for segmentation
- This is a research source for network security planning
- Also provides network monitoring
Cons:
- Doesn’t implement segmentation
Faddom doesn’t offer a price list and the full package is able to map applications and their dependencies. So, there is a lot that you will want to investigate about this package. The tool runs on one of your servers over a customized VM, which is included in the installation package.
5. AlgoSec
AlgoSec is a powerful network security management platform that provides several capabilities for network segmentation. One of the primary benefits of using AlgoSec for network segmentation is that it can automate and streamline the process, reducing the time and effort required to implement segmentation strategies. AlgoSec can help organizations identify and define network segments based on various factors, such as business units, security requirements, or compliance regulations. The platform provides automated discovery and mapping of the network, making it easier to identify the various devices and assets that need to be segmented.
Key Features:
- Microsegmentation
- Firewall rules
- Zero Trust
Why do we recommend it?
AlgoSec implements application access controls through microsegmentation. This is implemented by generating firewall rules rather than the ACL-based segmentation strategy. This package is able to defend applications on-premises and on the cloud. It implements a strategy that is known as a Cloud-native Application Protection Platform (CNAPP).
Once the network is mapped, AlgoSec can help organizations implement network segmentation strategies by generating firewall rules for each segment, ensuring that traffic is properly routed and isolated. The platform can also assess the risk associated with each segment, helping organizations prioritize their segmentation efforts. Another key benefit of using AlgoSec for network segmentation is that it can help organizations ensure compliance with industry regulations and best practices. The platform provides automated compliance checks and can generate reports that demonstrate compliance with regulations such as PCI DSS and NIST.
Who is it recommended for?
This package is aimed at businesses that use cloud-based services as well as or instead of on-premises software. The cloud-based platform protects other cloud systems and also activity on sites. The system merges hybrid systems by focusing on application access rather than network paths.
Pros:
- Operates like a cloud-based firewall
- Protects on-premises and cloud-based applications
- Security monitoring to confirm security policies
Cons:
- No price list
AlgoSec offers multiple deployment models, including on-premises, cloud, and hybrid deployment. AlgoSec offers both perpetual and subscription-based licensing plans for its network security management platform, depending on the deployment model. For on-premises deployment, AlgoSec offers a perpetual license with annual maintenance and support fees, while for cloud-based deployment, it offers a subscription-based licensing model. The pricing is based on the number of devices managed and the specific features and capabilities required. The choice of pricing and licensing plan depends on the organization’s specific needs and requirements. A free online demo is available on request.
6. Tufin
Tufin is a network security platform that provides a range of solutions for network segmentation. Tufin enables organizations to gain complete visibility and control over their network, automate security policy changes, and manage firewall rules. One of the primary benefits of using Tufin for network segmentation is that it simplifies and automates the process. Tufin offers a range of deployment options for its network security platform to meet the needs of different organizations. The platform can be deployed on-premises, in the cloud, or as a hybrid solution that combines on-premises and cloud components.
Key Features:
- Network security automation
- Options for manual intervention
- Server cloning
Why do we recommend it?
Tufin provides an automatic interpretation of security policies into firewall rules. Like AlgoSec, this system provides a hub through which all traffic should pass and it makes the most of that situation by controlling all packets to their destinations or blocking them. This package can be implemented on premises or taken as a SaaS system on the cloud.
Tufin provides automated network discovery and mapping, making it easier to identify the various devices and assets that need to be segmented. This helps organizations gain a better understanding of their network and enables them to create more granular security policies that align with business requirements. Tufin also offers a range of features and capabilities for implementing network segmentation strategies. The platform provides policy-based automation and compliance checks, ensuring that firewall rules are configured correctly and that they comply with industry regulations and best practices. Tufin also enables organizations to define and enforce security policies based on business context, such as user groups or application requirements.
Another key benefit of using Tufin for network segmentation is that it provides a centralized platform for managing security policies and firewall rules across different devices and vendors. This enables organizations to ensure consistency and compliance across the entire network and simplifies the management of complex, multi-vendor environments.
Who is it recommended for?
Tufin provides a highly automated security policy creation and enforcement service. This is a good choice for businesses that don’t want to waste time on manually implementing segmentation or microsegmentation to interpret their security policies. The tool is able to monitor activity for segmentation fine-tuning.
Pros:
- Automatic interpretation of security policies
- Alerts for security policy compliance violations
- Firewall optimization
Cons:
- No price list
Tufin offers various pricing and licensing plans for its network security platform. The pricing for Tufin’s network security platform is based on the specific needs of the organization, and the platform can be tailored to meet the requirements of small, medium, and large businesses. The pricing depends on the deployment model, features, and the number of devices managed. For on-premises deployments, Tufin offers a perpetual license with annual maintenance and support fees. For cloud-based deployments, Tufin offers a subscription-based licensing model that is billed on a per-device or per-user basis. A free online demo is available on request.
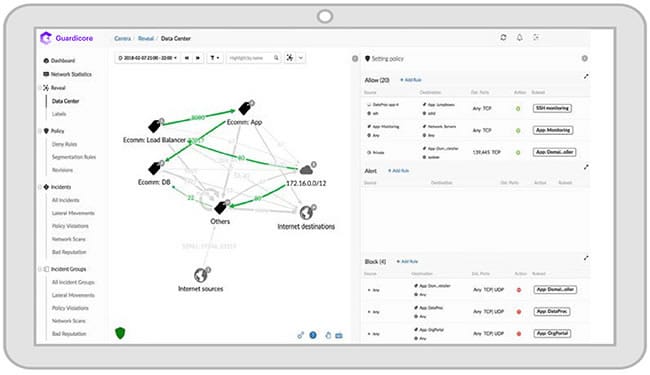
7. Akamai Guardicore Centra
Akamai Guardicore is a network segmentation platform that provides organizations with granular control over their network traffic, enabling them to detect and prevent cyber threats. The platform is designed to provide organizations with a powerful and flexible tool for securing their network and protecting critical assets and data from cyber threats. The platform uses a combination of software-defined networking (SDN) and micro-segmentation technologies to isolate and protect critical assets and applications within an organization’s network. This allows organizations to limit the impact of cyber-attacks and minimize the risk of data breaches.
Key Features:
- Zero Trust Security
- Delivered from the cloud
- Network segmentation
Why do we recommend it?
Akamai Guadicore Centra is one of the services offered on the Akamai cloud platform. The Akamai brand has a strong reputation in Web protection services, such as CDNs and DDoS protection. The Guardicore Centra product extends Akamai services to the protection of private networks.
Guardicore Centra utilizes a range of data collection methods, including agent-based sensors, network-based data collectors, and virtual private cloud (VPC) flow logs from cloud providers, to gather detailed information about an organization’s IT infrastructure. This information is then contextualized through a flexible and highly automated labeling process that can integrate with existing data sources like orchestration systems and configuration management databases.
This contextualized data is used to create a dynamic visual map of the entire IT infrastructure, allowing security teams to view activity down to the individual process level, both in real-time and historically. These insights into application behavior enable teams to quickly create granular micro-segmentation policies using an intuitive visual interface. Centra’s micro-segmentation capabilities are further supported by a set of innovative breach detection and response capabilities, creating a powerful security solution for organizations looking to secure their IT infrastructure.
Guardicore’s platform offers a range of features, including policy-based segmentation, application dependency mapping, and visibility and analytics tools. The policy-based segmentation feature allows organizations to define and enforce granular access controls based on user identity, network location, and other factors, while the application dependency mapping feature helps to identify potential vulnerabilities and misconfigurations in the network.
Who is it recommended for?
Although this system is able to reach out to protect on-site systems, it will also defend cloud systems. So, this package will work best for businesses that operate a hybrid network with both on-premises and cloud-based resources. This is a very similar system to Tufin and AlgoSec.
Pros:
- A cloud-based security hub
- Guards cloud applications
- Segments the on-premises network to prevent lateral movement
Cons:
- No price list
Guardicore also offers integration with other security tools and platforms, such as firewalls and security information and event management (SIEM) solutions, to provide a comprehensive and cohesive security solution. Their pricing model is based on several factors, including the size and complexity of the organization’s network, the number of workloads or endpoints being protected, and the level of support and services required.
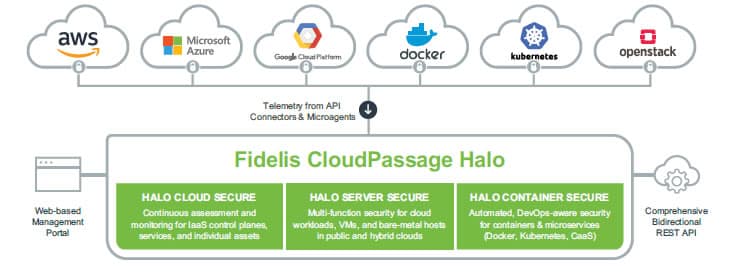
8. Fidelis Halo
Fidelis CloudPassage Halo is a comprehensive security platform designed for cloud environments. Halo is built on the cloud, for the cloud and it automates security controls and compliance procedures across various cloud models, including public, private, hybrid, or multi-cloud environments.
Key Features:
- A Cloud-native application protection platform
- Security monitoring
- Includes access rights management
Why do we recommend it?
Fidelis Halo is a CNAPP, which means that it protects applications and services that are hosted on the cloud. The package includes both preventative measures, which equate to vulnerability scanning, and live security monitoring. It also provides an access rights system, which is based on microsegmentation.
The Halo platform is particularly suitable for environments that are:
- Distributed Halo can securely manage application infrastructures across data centers and IaaS platforms and enable easy migration of workloads between cloud service providers without the need for reconfiguration or relicensing.
- Diverse Halo can secure an extensive range of asset types and workloads and leverage agentless connectors for IaaS and PaaS cloud security posture management.
- Dynamic Halo can accelerate security operations to keep up with rapidly changing application infrastructures and secure new resources as they are added, modified, or expanded.
Halo can be used as a network segmentation tool to enhance the security of cloud-based assets. CloudPassage network segmentation capabilities help organizations enhance the security of their cloud-based assets. Halo offers network segmentation capabilities through its micro-segmentation feature. This feature allows organizations to define granular security policies for each workload or application running in their cloud environment. It enables organizations to restrict network access based on the identity of the user, the type of workload, and the specific network segments to which they are allowed access.
Who is it recommended for?
This package focuses on servers and containers and the applications that they support. It doesn’t pay attention to network activity or permissible routes, so it doesn’t implement segmentation. The focus of this package is access control to applications. It also implements file integrity monitoring by blocking direct access to files.
Pros:
- File integrity monitoring, only apollo access through applications
- Application access controls
- Vulnerability scanning
Cons:
- Doesn’t implement segmentation
Fidelis CloudPassage Halo pricing and licensing depend on several factors, including the number of cloud assets to be secured, the level of security controls required, and the duration of the subscription.