In a digital world where every user needs to be carefully vouched for, constantly monitored, and efficiently managed, it becomes essential for network and server administrators to stay on top of everyone accessing their resources
And in cases where businesses have many user accounts, it makes sense to leverage one of the best user provisioning tools.
Here is our list of the best user provisioning tools:
- ManageEngine ADManager Plus EDITOR’S CHOICE A tool created for the Windows environment that is easy to use, cost-effective, and completely web-based; this is a comprehensive tool that integrates well and allows for delegation of administrative tasks. Access the 30-day free trial.
- Oracle Identity Management A highly flexible tool that can work equally efficiently in any architecture; it is a suite of tools that ensure the security of accounts from all angles.
- Okta A workforce and customer identity management solution offering frictionless logins and API integrations; other features include workflow integration with many systems and password-less access capabilities.
- PingIdentity PingOne A cloud-based user provisioning tool that is mobile-friendly and offers authentication services to many third-party solutions; it is a simple but powerful tool that administrators will love using.
- SolarWinds Access Rights Manager A lightweight AD user provisioning tool from one of the leading server and network monitoring tool makers; it is ideal for larger businesses.
- SailPoint Identity Platform Another cloud-based user provisioning tool that leverages the latest technology, making it an advanced solution fit for securing any architecture; it is flexible and keeps adapting as the user accounts scale or transform.
- OneLogin An all-encompassing user provisioning tool that caters to internal and external accounts and all assets in a digital environment; it brings unique technologies to the table without negatively affecting endpoint performances.
What is user provisioning?
User provisioning is the process of creating, managing, and maintaining user accounts and access rights within an organization’s IT systems. It ensures that employees, contractors, or third-party users are granted appropriate access to resources and applications based on their roles while ensuring security and compliance.
The provisioning process typically begins when a user joins an organization or assumes a new role. It involves creating a new account, assigning roles or group memberships, and granting access to required applications, databases, or systems. This access is often determined by the user’s position, department, and specific job responsibilities. User provisioning also includes configuring email accounts, setting permissions, and ensuring the necessary hardware or software tools are available.
One critical aspect of user provisioning is its automation. Modern provisioning solutions integrate with identity and access management (IAM) systems to streamline and automate the process. Automation reduces manual errors, ensures consistent access policies, and improves efficiency by enabling rapid onboarding and offboarding of users.
Effective user provisioning also includes deprovisioning, which ensures that access is revoked when a user leaves the organization or changes roles. This reduces the risk of unauthorized access and strengthens security. Regular auditing of user accounts and permissions is a key component of the process to prevent privilege creep. This term describes when users accumulate unnecessary access over time.
In addition to improving operational efficiency, user provisioning plays a vital role in maintaining compliance with data protection regulations such as GDPR or HIPAA. It ensures access control policies are implemented consistently and that sensitive information is only accessible to authorized individuals.
In summary, user provisioning is a fundamental process for managing access in any organization, balancing the need for efficient operations with robust security and compliance.
The primary role of user provisioning tools in businesses
Managing user accounts for every employee – especially in a large enterprise – can quickly become a tedious, error-prone job. This becomes glaringly evident in companies where employee turnover and transfers are high.
As the number of accounts that need to be handled increases, it can affect the line. Users that needed to be on-boarded can find themselves idle for hours, if not days, while their accounts are created, assigned the correct roles, tested, and finally handed over to them. This leads to wasted man-hours.
Installing a user provisioning tool is the best solution.
Features of an exemplary user provisioning tool
Our methodology for selecting a good user provisioning tool
- It should have the ability to provide business partners with layers of single sign-on (SSO), and Multi-factor Authentication (MFA) access to apps through a portal functionally – similar to the ones available to their internal users.
- A user provisioning tool should handle both workforce and customer accounts with equal efficiency.
- It should allow customers who already have established their identities on social media or other popular platforms (Facebook and Google are good examples) to register by using one of these accounts and then access resources they have been authorized to.
- It should be able to cover the whole enterprise and cater to all users of all applications and software solutions on a network under the control of directory services like Microsoft AD and Novell eDirectory.
- It should be easy to install, configure, use, and administer; the administration team shouldn’t find it challenging to create and assign roles and privileges.
- Of course, it should also provide full workflow automation – functions like user reviews, provisioning, or compliance should be event-driven as they move along the approval chain – with no manual intervention required.
- It should also leverage analytics and allow administrators to apply privileges based on informed context and not guesses. Therefore, the tool should discover, aggregate, correlate, and standardize unrelated identities, access levels, and security models for better insight.
- A good user provisioning tool should be able to identify risky behavior in real-time; it should also send alerts about suspicious activities or security threats to help stop malicious attacks.
- Zero Trust security – the act of eliminating network authentication as a primary access model to safeguard and apply access control, regardless of where users log in from – would be a sign of a great user provisioning tool; this is the “modern” way of securing a network and limiting the damage that malicious users can cause.
- And finally, the price should be worth the investment – there is no need to pay exorbitant subscription fees when a similar tool can perform a better job for a lower price… or even for free.
The best user provisioning tools
Well, let’s move on to the best user provisioning tools.
1. ManageEngine ADManager Plus (FREE TRIAL)
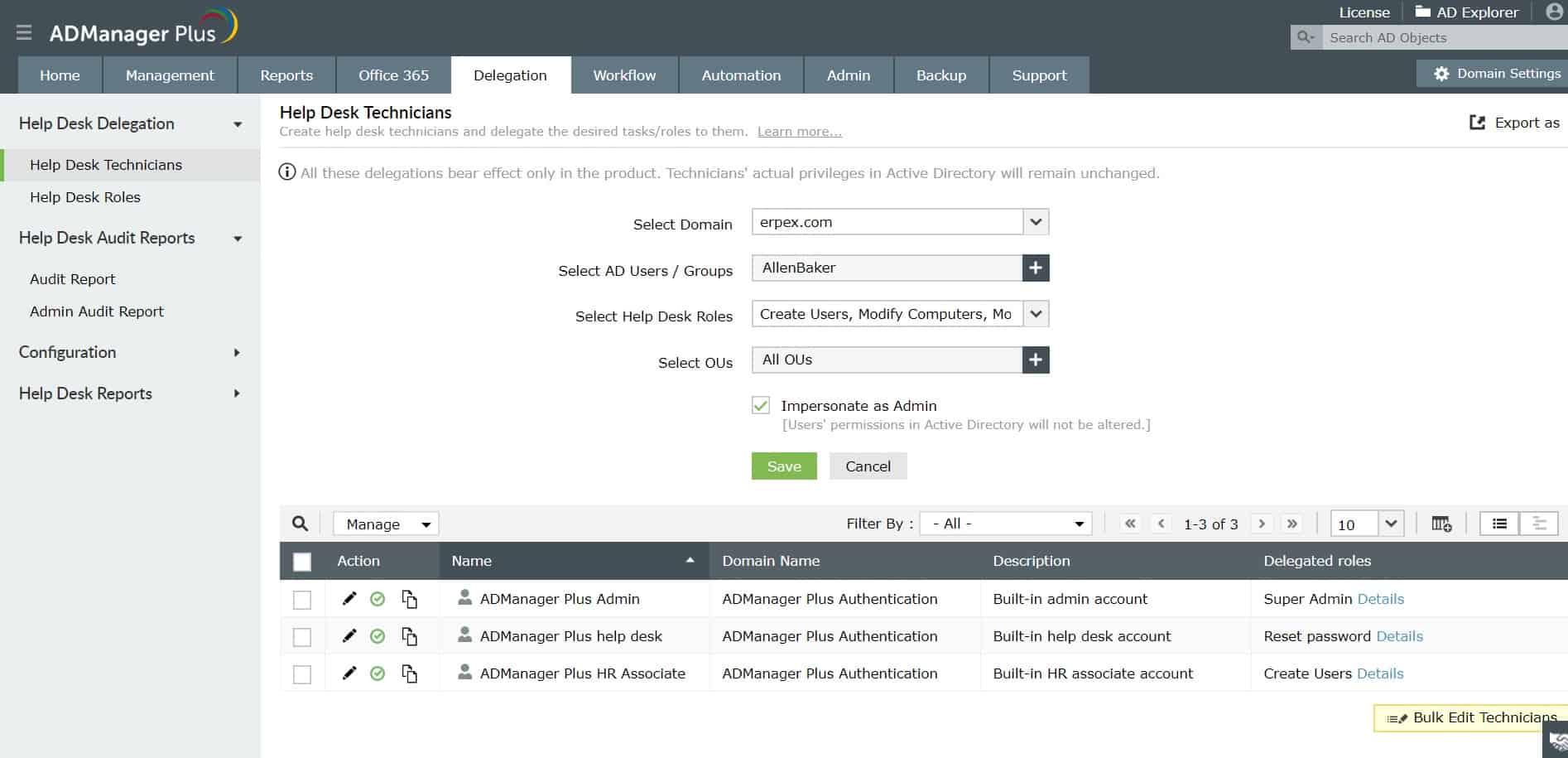
ManageEngine ADManager Plus makes delegation easyManageEngine ADManager Plus was explicitly built for the Microsoft ecosystem. It is an AD management and reporting solution for administrators and technicians who efficiently manage objects and generate instant, one-click reports.
It is an easy-to-use, completely web-based, and cost-effective AD management tool.
Key Features:
- Delegation Capability: Simplifies the delegation of AD management tasks for enhanced efficiency.
- Comprehensive Integration: Supports Active Directory, Microsoft Exchange, Google Workspace, and more.
- Compliance Support: Aids in adhering to major regulations like PCI DSS, HIPAA, SOX, and GDPR.
Why do we recommend it?
ManageEngine ADManager Plus provides a front end for multiple Active Directory instances. As well as the general system accounts AD instance, the tool will organize Active Directory instances working or Microsoft tools and Google Workspace. The package’s functions include bulk actions on accounts and coordination between instances.
The tool offers a support team safe access to AD, so the team manager can safely allow subordinates to use the AD management system. The package simplifies and unifies the management of Active Directory for system resources and also Microsoft Exchange, Google Workspace, and Skype for Business Server.
The ADManager Plus system will help you to centralize access rights management and improve the precision of user account permissions. The service helps with compliance with PCI DSS, HIPAA, SOX, and GDPR. All records in the AD domain controller are locked down and changes to user accounts are all logged. You get compliance reporting services as well.
Who is it recommended for?
If you run several different instances for Active Directory, keeping them coordinated can be troublesome. The purpose of ADManager Plus is to provide a better dashboard for the ARM and enable bulk actions to be performed, such as upload and update functions. The system also makes propagation easier.
Pros:
- Unified Management: Offers a centralized console for managing multiple Active Directory environments.
- Bulk Operations: Enables mass actions on accounts, facilitating easier administration.
- Access Improvement: Strengthens access controls and streamlines compliance with automated reporting.
Cons:
- Limited Threat Detection: Does not offer an extensive insider threat detection system, focusing more on management and reporting.
The software for ADManager Plus runs on Windows and Windows Server. Try ManageEngine ADManager Plus FREE for 30 days.
EDITOR'S CHOICE
ManageEngine ADManager Plus is our top pick for a user provisioning tool because it simplifies and streamlines the process of creating, managing, and modifying user accounts across Active Directory (AD). Its intuitive interface and powerful automation capabilities support IT teams to efficiently handle user provisioning, reducing the time spent on manual tasks and minimizing the risk of human errors. An important feature of ADManager Plus is its role-based delegation, which ensures that only authorized personnel can create, modify, or delete user accounts, enhancing security. It also supports bulk user provisioning, enabling the creation of multiple user accounts at once, which is especially beneficial for large organizations. The tool provides reliable reporting features, allowing administrators to generate detailed reports on user accounts, group memberships, login activity, and more. This helps in maintaining compliance with organizational policies and regulatory requirements. ADManager Plus integrates easily with existing Active Directory environments, offering advanced automation for user provisioning tasks such as password resets, group management, and user deactivation.
Download: Get a 30-day FREE Trial
Official Site: https://www.manageengine.com/products/ad-manager/download.html
OS: Windows Server
2. Oracle Identity Management
Oracle Identity Management front menu – easy to navigateOracle Identity Management is a scalable user provisioning solution that allows organizations to manage the end-to-end lifecycle of user identities effectively. It integrates well with enterprise resources, both within and beyond the firewall and even in the cloud.
Key Features:
- Lifecycle Management: Manages the complete lifecycle of user identities across varied environments.
- Policy Integration: Seamlessly integrates with existing security frameworks for consistent enforcement.
- Oracle Integration: Designed specifically to manage accounts within Oracle products effectively.
Why do we recommend it?
Oracle Cloud Infrastructure (OCI) offers a suite of identity and access management (IAM) systems. These are not just intended for use with systems hosted on the Oracle Cloud platform. They can manage access rights for resources on other cloud platforms and also on the servers of subscribing companies.
This tool also handles identity governance, access management, and directory services and allows businesses to leverage mobile access and social media platforms.
Oracle Identity Management is a member of the Oracle Fusion Middleware family of products. It is, in fact, a suite of tools that consists of Oracle Identity Manager, Oracle Identity Analytics, and Oracle Privileged Account Manager.
You manage user accounts with the Oracle Identity Manager and then password control for privileged accounts for servers and Oracle databases. These accounts with administrator rights are closely audited and changes, as well as usage, are logged.
Oracle Identity Management can be used to control accounts on-premises and on cloud platforms. There is a cloud-based version, called Oracle Identity Cloud Service.
Who is it recommended for?
There are four units in the OCI Identity and Access Management (IAM) platform. Each module addresses a different market. These units are Oracle Cloud Infrastructure Identity and Access Management, Oracle Access Governance, Oracle Access Management, Oracle Identity Management, and Oracle Identity Services. There are on-premises units as well as cloud-based systems.
Pros:
- Privileged Account Monitoring: Offers rigorous oversight for privileged accounts with comprehensive logging.
- Flexible Deployment: Available both on-premises and in the cloud, catering to diverse infrastructure needs.
- Oracle Ecosystem: Optimally manages user access within the Oracle suite of products.
Cons:
- AD Exclusion: Does not directly manage Active Directory, focusing instead on Oracle environments.
Download and try Oracle Identity Management for FREE (you may need to refer to dependencies before installation).
3. Okta
Okta integrates well with many office productivity solutionsWith Okta, we also get a platform that acts as a workforce and customer identity management solution.
But, in this case, Okta can be further extended to cater to these users by offering frictionless logins and smooth API integrations. These features enhance the users’ login experiences and create seamless business process integrations and improve security on the whole.
Key Features:
- Multi-Factor Authentication: Enhances security with robust multi-factor authentication options.
- Single Sign-On (SSO): Facilitates a seamless single sign-on environment across numerous services.
- Passwordless Entry: Utilizes email magic links among other methods for secure, passwordless access.
Why do we recommend it?
Okta is best known for its Single Sign-On product. This is written along the standards of the SAML 2.0 and OpenID Connect protocols. These capabilities give Okta identity management access to thousands of systems, particularly SaaS services, such as Microsoft 365, Google Workspace, and Slack. It can also implement passwordless access.
Okta provides a multi-factor authentication module, called Okta Verify, which is an authenticator app. The system can interface with a list of LDAP-based access rights managers, including Active Directory.
Administrators create an Okta portal for users that provides access to authorized applications, with credentials flowing through from the portal login screen.
System administration tools in the Okta package provide a central console for the management of diverse access rights managers. You import accounts into Okta and then leave behind your old access rights system. Within the Okta administrator console, you can create, update, and delete accounts, individually or in bulk.
Okta reporting provides analysis tools and compliance reporting assistance.
Who is it recommended for?
Okta is particularly useful for businesses that use a lot of SaaS packages and so would otherwise require their staff to repeatedly log in to many different systems. The platform also provides account management for customers. So, companies that run commercial websites should also look at the Okta system.
Pros:
- Wide Compatibility: Integrates with a vast array of SaaS applications, offering broad access management.
- Simplified User Experience: Provides a user-friendly portal for accessing all authorized applications.
- Centralized Administration: Enables efficient management of user accounts from a single console.
Cons:
- Hosting Limitation: Does not offer an option for self-hosting, requiring reliance on Okta’s cloud service.
Okta is a cloud platform, so there is nothing to install in order to get started. Try Okta for FREE.
4. PingIdentity PingOne
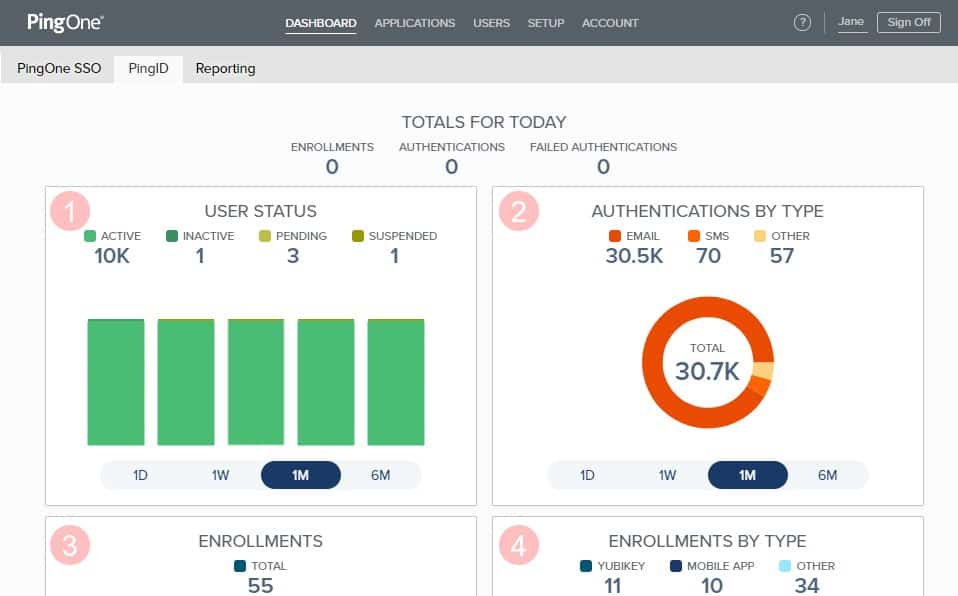
The PingIdentity PingOne is aesthetic and insightfulFrom PingIdentity, we get PingOne, a cloud platform from which administrators can cater to both their internal users and external customers and integrate well with a large number of security software solutions and the most common business and productivity applications in use today.
Key Features:
- Cloud Infrastructure: Delivers Identity-as-a-Service from a cloud-based platform for flexible access management.
- User-Friendly Interface: Boasts an attractive dashboard that simplifies navigation and task execution.
- Mobile Management: Offers a dedicated app for managing identity services on the go.
Why do we recommend it?
PingIdentity PingOne is a cloud-based Identity-as-a-Service (IDaaS) platform. You set up your user accounts in the cloud-based dashboard in PingOne and then link to the systems that those accounts apply to. You can manage user accounts for employees and also deliver a self-service account system for customers.
Administrators will love the PingOne Cloud Mobile Application, which allows them to offer the convenience of mobile SSO on the go from anywhere in the world using their Android or Apple devices.
PingOne is one of the leading user provisioning tools offered as Identity-as-a-Service (IDaaS) and provides authentication for AD, Google Apps, and other third-party directories. The system can interface to your existing IAM or replaces it. You can upload your existing user accounts into the cloud-based tool where you can analyze your permissions structure and improve it.
The system provides adaptive authentication, with options for location checking. It presents a full profile for each user, which establishes identity credibility and logically verifiable activity patterns.
The strength of the PingOne system lies with orchestration. This cuts out a lot of admin work and a list of integrations enables the creation of a SSO environment that users can access through a portal.
Who is it recommended for?
PingIdentity offers PingOne for Workforce and PingOne for Customers. The Workforce version is reasonably priced and subscriptions are calculated per employee per month. This is a scalable system at a reasonable price and is accessible for any size of business. The Customer version is very expensive and only suitable for large eCommerce businesses.
Pros:
- Versatile Management: Provides tools for both workforce and customer identity management, accommodating a wide range of business needs.
- Integration Ease: Seamlessly integrates with a variety of security software and business applications for comprehensive coverage.
- SSO Convenience: Enables single sign-on across multiple platforms, enhancing user experience and security.
Cons:
- Opaque Pricing: Lacks transparent pricing details, requiring potential customers to contact sales for information.
Try PingIdentity PingOne for FREE.
5. SolarWinds Access Rights Manager

SolarWinds Access Rights Manager (ARM) is a lightweight Microsoft AD and Azure AD user provisioning tool. It is made by one of the most popular server and network monitoring and administration tool makers. An ARM can streamline user onboarding and helps with account administration, and remains necessary right until a final user deletion request is sent.
Key Features:
- Risk Assessment: Evaluates account vulnerabilities to mitigate insider threats effectively.
- AD Integration: Offers comprehensive monitoring and management for Active Directory changes.
- User Provisioning: Streamlines the process of account creation, modification, and deletion.
Why do we recommend it?
SolarWinds Access Rights Manager is a user activity tracking service that aims to spot insider threats and account takeovers. The package relies on Active Directory of Azure AD as the corporate ARM and enhances AD account security features. User access monitoring contributes to compliance with GDPR, PCI DSS, and HIPAA.
The number of accounts doesn’t matter as ARM standardizes user credentials using role-specific templates to manage accounts at scale securely. This makes it a good choice for any organization – big or small.
Administrators can create, delete or edit permissions from a single ARM console for multiple domain controllers. The SolarWinds system provides analysis, auditing, management, and monitoring support for AD and Group Policy configurations. The tool can work with Active Directory for Microsoft platforms like SharePoint, Exchange, and OneDrive.
Data owners can improve access control for folders and groups. The ARM package also provides a self-service permissions portal that supports the assignment of access rights. This removes a lot of the workload from administrators while empowering users.
The SolarWinds package includes a reporting module with pre-written report templates and the option to create custom report formats. Reports can be run on-demand or on a schedule and they include compliance reporting capabilities.
The Access Rights Manager includes a log management system that collects status messages from AD and tracks changes in programs, applications, and accounts, including mailboxes, calendars, or contacts. Gathered log messages can be forwarded to security information and event management (SIEM) solutions for a more detailed analysis of any suspicious activities.
Who is it recommended for?
This solution is ideal for large businesses that use Active Directory for access rights management. The AD system can be hosted on-site or as the Azure AD service. The software will only run on Windows Server but if you are running AD on-site, you will certainly have a server with that operating system.
Pros:
- Comprehensive Control: Centralizes domain controller management across various AD-supported applications.
- User Empowerment: Features a self-service portal, lightening the administrative load and enhancing data ownership.
- Automation Efficiency: Automates account setup processes, ensuring standardized and simplified user access.
Cons:
- No Cloud Option: Lacks a Software as a Service (SaaS) version, requiring installation on Windows Server.
The ARM package installs on Windows Server. Try SolarWinds Access Rights Manager with a fully functional 30-day free trial.
6. SailPoint Identity Platform
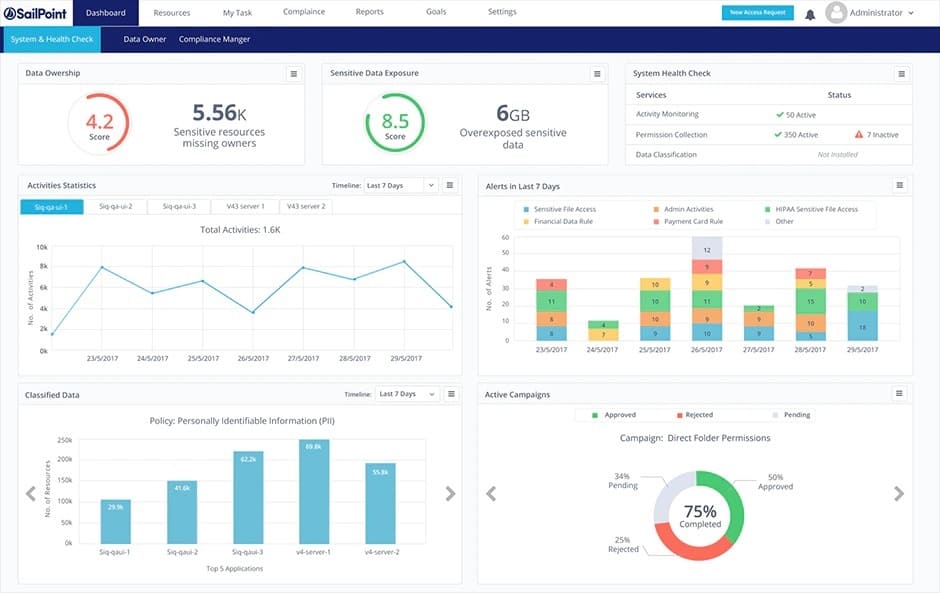
SailPoint Identity Platform dashboard – full of detailsSailPoint Identity Platform is a cloud-based user provisioning tool built on big data and machine learning (ML) technologies that allow for an AI-driven approach to identity governance.
Key Features:
- AI and ML Integration: Utilizes artificial intelligence and machine learning for advanced threat detection and identity governance.
- Risk Assessment: Offers sophisticated user account risk evaluation to identify and mitigate potential security threats.
- Cloud-Native: A fully cloud-based solution that ensures scalability and flexibility without hardware dependencies.
Why do we recommend it?
The SailPoint Identity Platform is concerned with account security rather than access rights management or password storage. It applies AI to examine account behavior. The tool helps businesses manage workforce accounts but it can also be used to manage customer accounts. The security features extend to data access controls.
This leveraging of advanced technology makes it a powerful user provisioning tool with features like autonomous risk detection and mitigation, innovative process orchestration, and low or no-code extensibility that can be applied on any cloud architecture without draining local resources.
SailPoint provides user account creation but its strong point is its security monitoring and activity tracking. It guards access to applications and also protects data by logging its usage by each user account.
As if the built-in automation capabilities for role creation and privilege assignment weren’t enough, SailPoint Identity Platform uses its machine learning capabilities to study the host organization’s identity needs and caters to it by adapting accordingly. Access controls continue beyond permissions. This is a Zero Trust system that performed a risk assessment on users and the devices that they use before granting access. There is also a governance and compliance unit in the SailPoint Identity Platform.
Who is it recommended for?
The SailPoint platform can be put to many different uses. For example, it provides user access management for Zero Trust Access models and there is also a Cloud Infrastructure Entitlement Management (CIEM) unit. You can manage accounts for your workforce to access cloud services or operate user accounts for your own SaaS platform.
Pros:
- Advanced Security: Employs AI-driven security measures for proactive threat detection and response.
- Zero Trust Framework: Implements Zero Trust Access control to continuously assess and authenticate user access.
- Compliance and Governance: Features robust data governance tools alongside compliance reporting capabilities.
Cons:
- Lack of Pricing Transparency: Similar to PingOne, SailPoint does not readily provide pricing information.
Try SailPoint Identity Platform by registering HERE.
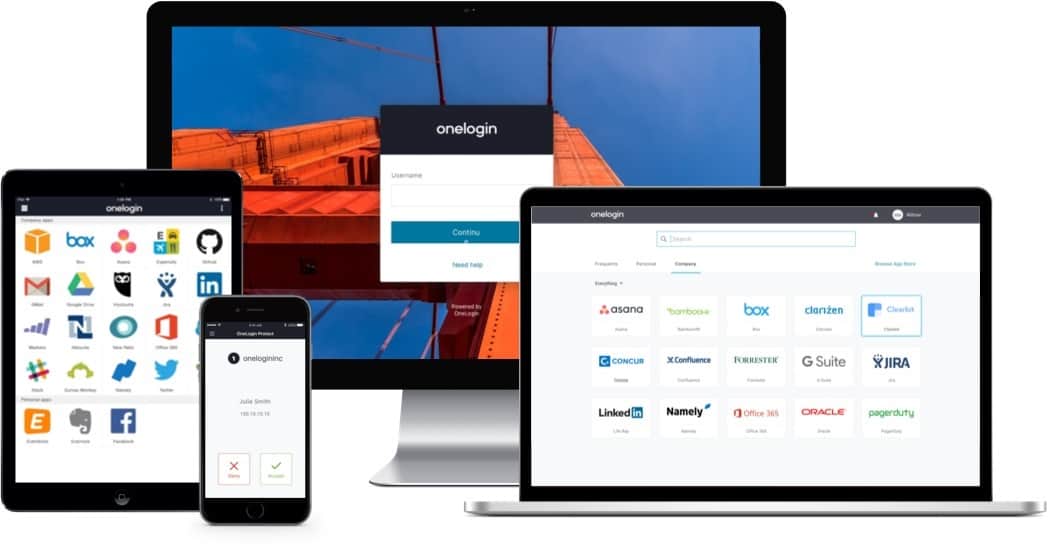
7. OneLogin
OneLogin – this is a device-agnostic solutionOneLogin is the user provisioning platform for secure, scalable, and intelligent experiences that covers the in-house users, customers connecting from beyond the network, and the developers helping create a smoother digital environment.
Key Features:
- Zero Trust Security: Adopts a Zero Trust approach to access management, verifying every access request meticulously.
- Application Assignment: Allows for precise control over which users can access specific applications, enhancing security.
- SSO Capability: Facilitates a single sign-on environment, streamlining access to various applications.
Why do we recommend it?
OneLogin offers access rights management for workers and also provides a customer account management service for cloud platforms. The workforce management tools provide an access portal for users, which ripples through to approved applications, creating a single sign-on (SSO) environment. This is a Zero Trust Access model.
With the help of this user provisioning tool, administrators can securely connect all of their applications and take quick actions as soon as they identify potential threats.
As the name suggests, OneLogin is mainly about providing a single sign-on environment. To this end, the platform provides a range of user assessment tools, which include multi-factor authentication and a portal that assigns allowed applications to users. So, user A is allowed access to applications 1, 2, and 3 and just has no way to even see the access screens for applications 4, 5, and 6.
When setting up a new user account, the authentication tools in the platform automatically apply. The administrator just needs to add access to approved applications to the user.
The user logs into the portal and the OneLogin platform adds AI-based assessments to the action in addition to straightforward password matching. For example, if a user logs in from London, then New Delhi, and then Tokyo, within the space of a few hours, a flag is raised and the user is automatically blocked from accessing the system pending investigation.
Importantly, OneLogin is able to interface with Active Directory. It will also exchange authentication signals with Google G Suite, Workday, and LDAP.
Who is it recommended for?
You can use this tool to standardize application access for your workforce in the office and remote workers. It provides access controls for applications on your servers and on cloud systems. The customer account management option is a CIEM that enables the owners of cloud SaaS platforms to manage the accounts of users.
Pros:
- Comprehensive Risk Analysis: Each login attempt is scrutinized for potential security risks, ensuring a high level of protection.
- Efficient Onboarding: Simplifies the process of setting up new user accounts and assigning necessary application access.
- Active Directory Integration: Offers compatibility with Active Directory, Google G Suite, and more for seamless user management.
Cons:
- No Clear Pricing Details: Pricing information is not immediately available, necessitating inquiries to the sales team for more details.
Try OneLogin FREE for 30 days.
Why do we need user provisioning tools?
Ok, we have just seen the best user provisioning tools. So let us close by reviewing how these tools can help businesses in their day-to-day activities and overall security.
Here are some reasons:
AD is one of the most popular user administration platforms. HR departments will find that these tools make it easier to manage users’ logins, accounts, roles, and privileges quickly, accurately, and efficiently without relying on the IT department.
Automating any task – user management included – saves time and money. This is especially true when it can all be done centrally from one console.
The cost-saving also applies to software licenses where removing unnecessary accounts quickly means recuperation of subscription costs.
In this case, it also means saving money – indeterminable amounts – by not letting hackers (incredibly disgruntled former employees with still-active accounts) run amok on a network.
Enforcement of policies also becomes more accessible as actions can be taken based on reports and audits showing details like malicious attempts, inactivity, or privilege abuse.
Then there is the fact that businesses today need to meet various requirements and compliance standards, and user provisioning tools make it much more manageable.
It is apparent now, we hope, that businesses that choose to invest in any of the best user provisioning tools we have seen would be at an advantage when it comes to effectively and securely managing their user and customer accounts.
We would like to know what you think – are there any tools you have tried ad feel should also be on this list? Let us know; leave us a comment.
User provisioning FAQs
What is User Provisioning?
User provisioning is also known as account provisioning. The outline of the tasks is to just sgt up new user accounts on your business system. This can be for employees or for customers and other invited outsiders. On a more detailed level, the user provisioning task requires user account maintenance, which involves updating and deleting accounts. So, the discipline extends to full system access management.
What is user provisioning in SSO?
Implementing user provisioning for single sign-on environments requires a coordination process between the access rights manager of the business and the user authentication systems of the third-party applications that the business uses. This connection can’t be built manually by the administrator because it requires coordination with the internal processes of those third-party systems.
What does provisioning mean in IAM?
User provisioning is a function that Identity and Access Management (IAM) systems require of the administrator. This is the action of entering user details into the IAM to create an account. Those accounts also need to be maintained for relevance and that requires an amount of manual intervention.