In response to a ransomware attack that caused days of outages across the US healthcare system, United Healthcare’s Change Healthcare subsidiary reportedly chose to pay $22 million to hackers. But that’s not the end of the matter, according to claims made by a second hacker group.
Normally, when a ransom is paid, ransomware attackers agree to give the victim a decryption key to restore its systems, and attackers promise not to sell or release stolen data to other third parties.
Despite the ransom reportedly being paid, however, another ransomware group now claims to possess the stolen data. RansomHub, a relatively new hacker group, says it has access to 4TB of the data originally stolen by ALPHV/BlackCat.
The claim has yet to be verified. Comparitech contacted Change Healthcare for comment and will update this article if it responds.
ALPHV was running a ransomware-as-a-service business. Customers, called “affiliates”, could essentially hire ALPHV to launch ransomware attacks on their behalf. When a ransom is paid, the proceeds are distributed among ALPHV and the affiliates.
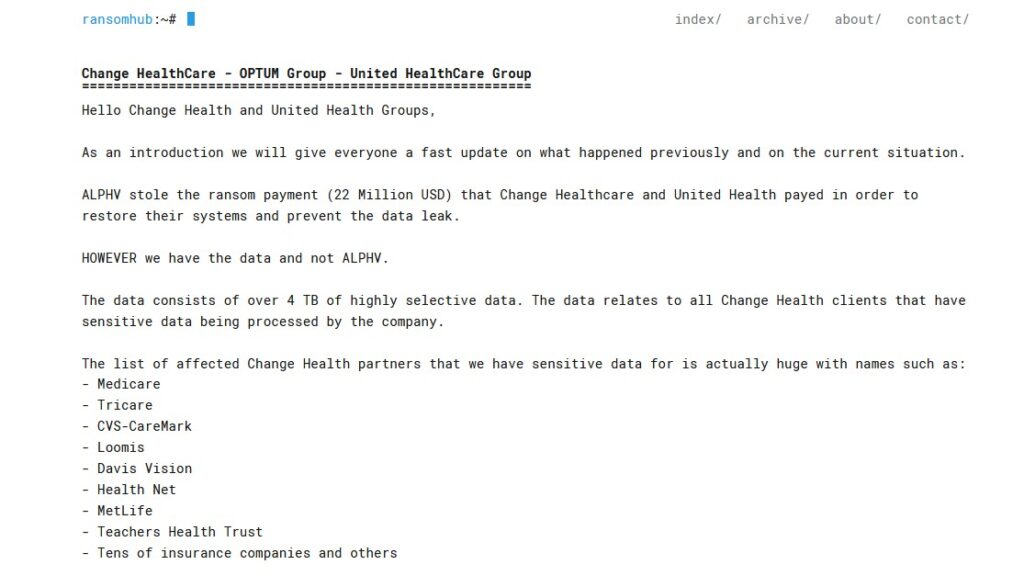
After the Change Healthcare attack, RansomHub claims, that didn’t happen. On April 8, RansomHub posted a message stating ALPHV stole the entire $22 million ransom payment, and never paid affiliates:
The note says, “ALPHV stole the ransom payment (22 Million USD) that Change Healthcare and United Health payed in order to restore their systems and prevent the data leak. HOWEVER we have the data and not ALPHV. [sic]”
RansomHub said it now holds “4 TB of highly selective data” affecting Change Healthcare partners, including Medicare, Tricare, CVS-CareMark, Loomis, Davis Vision, Health Net, MetLife, Teachers Health Trust, and more.
“The data relates to all Change Health clients that have sensitive data being processed by the company,” the note reads.
Possible ALPHV/BlackCat exit scam
We don’t know exactly what’s happening behind the scenes between ALPHV and RansomHub, but many observers say ALPHV pulled off an exit scam. An exit scam occurs when a business–in this case, ALPHV–absconds with funds contributed by or owed to the participants—ALPHA’s ransomware-as-a-service affiliates.
If true, this could be the end of ALPHV/BlackCat, one of the most prolific ransomware groups of the past few years. Shortly after the attack, ALPHV shut down its leak site and started selling its ransomware source code for $5 million.
RansomHub was likely one of ALPHV’s affiliates. Shortly after ALPHV failed to pay out, affiliates threatened to leak the data, which would in turn damage ALPHV’s reputation and cause it to lose future affiliates. But ALPHV’s reputation matters little if it no longer exists, hence the exit scam.
RansomHub could use the data to attempt to extort a second ransom out of Change Healthcare. Some observers speculate that RansomHub could have acquired ALPHV’s operations.
ALPHV/BlackCat has claimed more than 70 victims since it began, including some of the most high-profile ransomware attacks of the past few years. Most recently, it claimed responsibility for hacking Prudential Insurance and LoanDepot.