Update – June 2025 – 7,797 people are confirmed to have had their health data impacted in this attack.
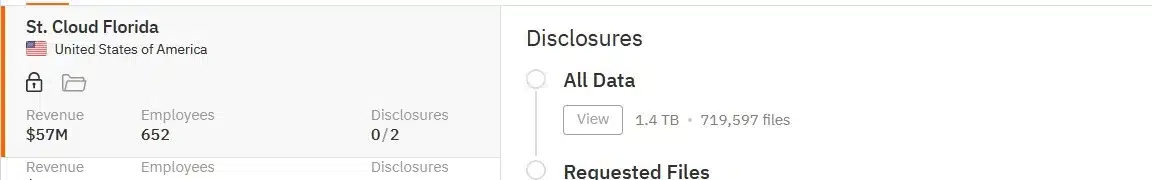
Ransomware gang, Hunters International, has just added the City of St. Cloud, Florida, to its data leak site. On its site, Hunters International claims to have stolen 1.4 TB of data, which includes 719,597 files.
On March 25, the City of St. Cloud confirmed it was dealing with a cyber attack and was working to resume normal operations “as quickly as possible.” The St. Cloud Police Department confirmed via social media that it was a ransomware attack, stating that 911 services were still operating as normal.
The latest update from the city was on April 4 to confirm opening times for Toho Water Authority’s customer service lobby at City Hall. At the time of writing, there have been no comments on whether data has been stolen from the systems. Comparitech has contacted the City requesting an update on this and will update the article with any comments.
Who is Hunters International?
Hunters International first appeared in October 2023 with some suggesting it was a spin-off of Hive. It has quickly become known for its double-extortion tactics whereby it seeks a ransom for decrypting systems and for deleting stolen data. One of its biggest confirmed attacks was on the Fred Hutchinson Cancer Center in November 2023. The attack saw 890,959 individual records affected with the group also contacting victims individually. It requested $50 in exchange for their data being deleted.
According to our data, Hunters International is also responsible for the confirmed attacks on two other US government organizations–St. Johns River Water Management District (Florida) in November 2023 and the Village of Skokie (Illinois) in December 2023.
Due to the fact this group is known for stealing data as well as disrupting systems, its recent posting of the City of St. Cloud suggests the same could have happened here. While we await updates from the City, employees and residents should be on high alert for any phishing emails, texts, or phone calls while monitoring accounts for any suspicious activity.
Ransomware attacks on government organizations
So far this year, we’ve tracked 19 ransomware attacks on US government organizations. The average ransom demand is nearly $940,000. In one case, a ransom was secured. Following an attack in January, Washington County approved $400,000 for recovery, suggesting it included a ransom payment (source). Bucks County, the City of Jacksonville Beach, Fulton County Government, and Tarrant Appraisal District all confirmed they hadn’t paid a ransom.
The City of Jacksonville Beach has recently issued a data breach notification to 48,949 following its attack which was carried out by LockBit.
Attacks on government organizations have the potential to cause significant disruptions to crucial services, such as 911 dispatch centers, sheriff’s offices, city councils, and utilities. Often, employees have to resort to pen and paper as systems become unavailable. In some instances, backups may help restore data, but, in many cases, organizations face a decision as to whether they meet the hackers demands fo a decryption key or they rebuild their systems from scratch.
In 2023, government entities lost 16.42 days to downtime on average.
