LockBit adds 150+ victims in 5 days
LockBit added 152 victims to its data leak since Monday, May 6. We logged more than 100 unconfirmed ransomware attacks claimed by LockBit in the past 48 hours alone.
The leader of LockBit was unmasked and sanctioned this week.
Ohio Lottery
The Ohio Lottery now reports 538,595 people’s personal data was compromised in a December 2023 cyber attack. The data includeded full names, dates of birth, and Social Security numbers.
Ransomware group DragonForce claimed responsibility for the attack in January, saying it stole 1.5 million records, or 95 GB of data. The group claims those records account for 12 percent of Ohio’s population.
Pantana Accounting & Tax, Inc
Pantana sent notifications to 4,139 people regarding a data breach that took place in February 2024. Names and Social Security numbers were among the data.
Ransomware group Inc claimed responsibility for the attack in March. It posted a proof pack with a sample of the stolen data.
Lewis Brothers Bakery
Lewis Brothers Bakery issued notifications to 13,501 victims of a March 2024 data breach. Names and Social Security numbers were among the data.
Ransomware group Medusa added Lewis Brothers Bakery to its leak site last week, demanding a $1 million ransom in exchange for 116 GB of data.
American International College
American International College on May 8 notified 11,822 people of a November 2023 data breach that compromised their names and Social Security numbers.
Ransomware group nSafe claimed responsibility for the attack in January 2024, saying it stole 5,000 GB of data. American International College has not confirmed nSafe’s claim.
Electric Mirror
Lighted mirror manufacturer Electric Mirror LLC this week notified an undisclosed number of victims that their data was compromised in a March 2024 ransomware attack. The stolen data includes full names, Social Security numbers, dates of birth, passport numbers, military ID numbers, student ID numbers, financial account numbers, health insurance policy numbers, and electronic signatures.
Ransomware group Inc claimed responsibility for the attack.
Chemring Group (unconfirmed)
Ransomware group Medusa on May 7 added UK-based technology company Chemring Group PLC to its data leak site. It alleges it has stolen 186.78 GB of data and is demanding a $3.5 million ransom for its deletion. Medusa says it is in possession of “confidential documents, databases, and solidworks design files.”
Chemring Group says it has seen no indications of compromise, and it believes the attack was on a business previously owned by Chemring.
Kansas City Scout
Ransomware group Play on May 7 claimed a cyber attack that took down Kansas City’s traffic management system, KC Scout. The April 25 attack forced KC Scout to shut down its website, traffic cameras, and message boards.
In addition to disrupting service, Play claims it stole an undisclosed amount of data from KC Scout containing “private and personal confidential data, clients documents, payroll, accounting, contracts, taxes, IDs, finance information and etc. [sic]”
The Missouri Department of Transportation told Comparitech, “It is too early to provide an estimate, but it is expected to be months before restoration can be anticipated.”
Wichita, KS
The city of Wichita, Kansas was hit by a ransomware attack over the weekend that affected its airport, water service, and public transit. The attack, claimed by LockBit on May 7, forced the city to resort to cash transactions until systems are restored.
NRS Healthcare
Ransomware group RansomHub added NRS Healthcare to its data leak site on May 6. A cyber attack has been disrupting the UK-based healthcare company since the start of April, but NRS has not confirmed RansomHub’s claims.
RansomHub says it is in possession of over 600,000 private documents, including financial reports, contracts, and accounting documents.
Ashley Home Stores
The Dufresne Spencer Group, the company behind Ashley Home Stores, on May 8 notified an undisclosed number of people about a May 2023 data breach. The compromised data included names, dates of birth, driver’s license numbers, bank account info, and digital signatures.
Ransomware group ALPHV/BlackCat claimed responsibility for the attack in June 2023.
Aizer Health
Aizer Health notified 10,950 people of a data breach that took place in September 2023. The data included financial account numbers, credit card numbers, names, addresses, medical info, health insurance info, and Social Security numbers.
Aizer Health paid an undisclosed ransom, sources say. No one has claimed responsibility for the attack as of time of writing.
University System of Georgia
The University System of Georgia has now notified 800,000 people of a data breach that occurred in May 2023. The data included Social Security numbers, dates of birth, bank account numbers, and federal income tax documents.
An investigation concluded that ransomware group CL0P acquired the data through the MOVEit file transfer software vulnerability. That vulnerability led to dozens of high profile attacks in 2023.
J.B. Poindexter & Co
Truck body manufacturer J.B Poindexter & Co, Inc has notified (PDF) more than 300 former and current employees that their data was compromised in an April 2024 ransomware attack. The data included contact info, Social Security numbers, an dates of birth, and included data from employees’ dependents as well.
No one has claimed responsibility for the attack as of time of writing.
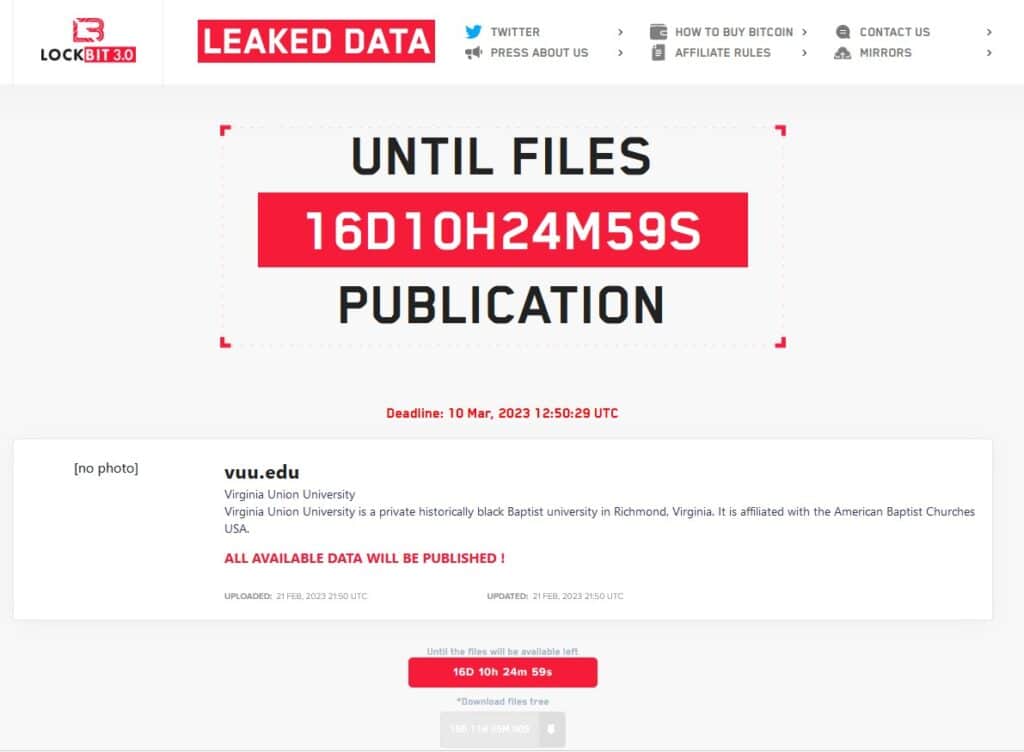
Virginia Union University
1,309 people in Texas and 459 in Massachusetts have been issued data breach notifications regarding a February 2023 cyber attack. The number of affected individuals currently stands at 1,768. The compromised data includes names, Social Security numbers, dates of birth, driver’s license numbers, and state ID numbers.
Ransomware gang LockBit claimed the attack at the time.
Numotion
Wheelchair maker Numotion has now notified 59,116 people in four states about a February data breach that compromised names, Social Security numbers, dates of birth, and employment info. That’s a sharp increase from the 4,190 people originally notified.
Ransomware group Black Basta claimed the attack.
Pensacola, FL
931 victims have been confirmed so far in the cyber attack on the city of Pensacola, according to breach notifications submitted in Maine and Texas.
The impacted data includes first and last names, Social Security numbers, ID card numbers (e.g. driver’s license), passport numbers, military ID numbers, and health insurance policy numbers. An investigation of the incident wrapped up on April 2, 2024.
The attack took down the city’s phone lines and several online services, including bill payment, and the FBI came in to investigate the incident. No cybercriminal groups has taken responsibility for the attack as of time of writing.
Church of Sweden
LockBit this week claimed responsibility for a November 2023 cyber attack on the Church of Sweden (Svenska kyrkan). The attack forced the church to shut down its systems, but said it won’t meet LockBit’s demands.
Boyden (unconfirmed)
Ransomware gang Medusa on May 6 claimed an attack against Boyden, an international headhunting firm. Medusa is demanding $2 million in ransom for what it says is 79.3 GB of stolen data, and is giving Boyden eight days to pay it.
Boyden has not confirmed an attack as of time of writing.
CoinMama.com (unconfirmed)
Ransomware group Flocker claimed responsibity for an attack on cryptocurrency exchange CoinMama.com. Focker says it stole 2 TB of data, containing 210,000 user records.
Flocker is a new group making big claims, but none of them have been confirmed by victims.
Consulting Radiologists (unconfirmed)
LockBit added Consulting Radiologists to its leak site on April 27 following a February 2024 ransomware attack. The Minnesota radiology practice has not confirmed an attack as of time of writing.