Hackers can use sniffing attacks to suck up the sensitive data that travels across your network. But before we can explain what sniffing attacks are and how to defend against them, we need to cover some background. This will give you a solid understanding of how these attacks can affect you, and why you need to adopt certain defensive measures.
What is network traffic?
The traffic in a city is composed of the vehicles moving out at any given time, and network traffic is much the same. Network traffic is simply the data moving in and out of a network of computers. It’s also called data traffic, or even just traffic.
The data moving in and out of the network is broken down into small parcels known as network packets, data packets, or packets. A packet is comprised of two things:
- The payload — This is the actual data that is being sent.
- The header — This contains information about the data, where it is coming from, where it is supposed to be delivered, and other technical information.
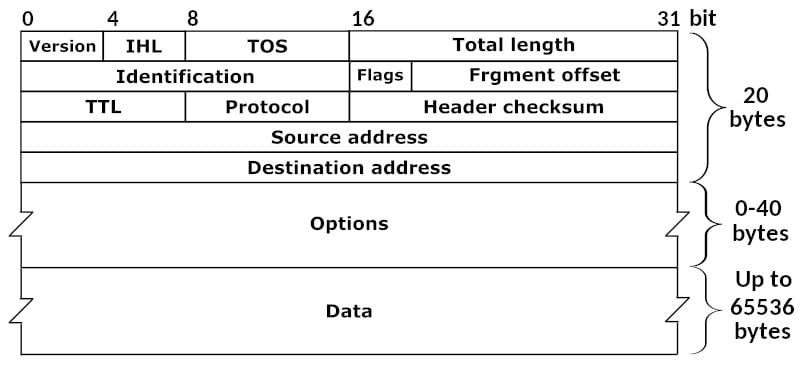
A diagram of an IPv4 packet. The header is all of the information from Version to Options. The payload is represented by the box marked Data. Note that the diagram is not drawn to scale, and that the Data can be up to 65,536 bytes. Data packet of IPv4 by Michel Rakni licensed under CC BY-SA 4.0.
Let’s use an email as an analogy to explain the difference between the two. The message body (Hey, how are you? Can you please… Yours sincerely…) is the payload. The header consists of information like the sender, the recipient, the subject, the time and date, as well as some technical information that helps make sure that the email gets delivered to where it needs to go in a readable format. While we don’t place too much importance on this header information, it’s essential for getting the message body to the recipient.
Network packets are much the same. While we may only really care about the data in the payload, the information in the headers is critical for getting it to where it needs to be.
Network packets are sent and received in a variety of different formats known as protocols. These are standardized forms of communication that each serve different purposes. As examples, HTTPS secures communication over a network, while SMTP is used for sending and receiving emails.
These differing protocols allow computers to send and receive various types of information in a mutually understandable way.
The traffic of a given network includes all of these different types of packets that are going in and out of the network at any one time. If you are at work and send an email, the data packets that comprise the email will be part of the network’s outgoing traffic.
If you Google something, you will be sending packets out of the network in the form of a request. The search results will be delivered to you in the form of incoming data packets.
Thankfully, our web browsers, email clients and other programs do all of this under the hood, so we generally don’t have to think about packets in our day-to-day use of the internet. But deep down, this is the form that all of our information takes when it travels in and out of our computer networks.
What is a packet sniffer?
A packet sniffer is a piece of software that can capture and log the packets that travel over a network. They are also known as network analyzers, protocol analyzers or packet analyzers.
These tools help to give network administrators insight into what is happening across their network, allow them to diagnose problems, and much more. While they have a range of legitimate uses, these programs can also be abused in the form of sniffing attacks.
Examples of packet sniffing software include:
- Wireshark — Wireshark is a free network protocol analyzer that helps you identify what is happening over your network. It’s open source, and can be used to inspect the data of hundreds of different protocols.
- TCPDUMP — This is a command line packet sniffer that doesn’t have a graphical user interface. It is compatible with most Unix-like operating systems, including Linux, macOS and FreeBSD. There is a port for TCPDUMP for Windows, known as WinDump.
- SolarWinds Network Packet Sniffer — This is a paid tool that offers a range of high-level features. It is packaged alongside comprehensive monitoring software.
- Paessler PRTG Network Monitor — Paessler PRTG Network Monitor is another paid offering that also includes other analysis tools and a full-featured dashboard.
- Pktmon – Windows 10 and 11 have an often overlooked built-in network monitoring tool called Packet Monitor (Pktmon). Microsoft says that “it can be used for packet capture, packet drop detection, packet filtering and counting.”
There are also hardware packet sniffers, which network administrators may plug directly into their networks to collect certain information.
The legitimate uses of packet sniffing
Networks are complicated, with large numbers of many different types of packets zipping in, out and through the connected network of computers. This complexity can easily lead to things going wrong.
A lot of the time, it’s something innocent, like a compatibility issue, a software bug or a hardware failure. However, hackers can also work their way into networks, infecting them with malware, stealing data and causing other havoc.
Packet sniffing software gives network administrators real-time insight into what is happening in their networks. These tools help them monitor the traffic traveling across their networks, let them see if everything is running smoothly, pinpoint bottlenecks, and can help to give them the information they need to diagnose any problems or determine whether the systems are under attack.
Not only do packet sniffers give admins real-time insight, but their logging abilities allow them to inspect the network history and determine changes over time.
Packet sniffers can capture all of the packets that they come across in unfiltered mode. These can then be logged and analyzed later if necessary. Another option is filtered mode, which enables the network administrator to specifically capture packets with certain attributes, such as only the HTTPS packets. This can be handy for zeroing in on certain issues, because it allows admins to look at the relevant packets, while discarding all of the noise.
While packet sniffers are excellent for giving insight into the activities happening on a network, they cannot discern the contents of encrypted traffic unless the administrator has the key to decrypt the data. If a weak security mechanism like WEP is protecting the data, they may be able to recover the key with ease.
What is a sniffing attack?
We’ve discussed how packet sniffing tools can be used by administrators to gain an understanding of their networks, diagnose issues, and detect threats. But what happens when an attacker secretly connects to an organization’s network and does their own packet sniffing on the network’s traffic?
Packet sniffers can intercept and log many of the packets that travel over a network. This is a dangerous power when it falls into the wrong hands, especially if sensitive data travels over the network in an unencrypted format.
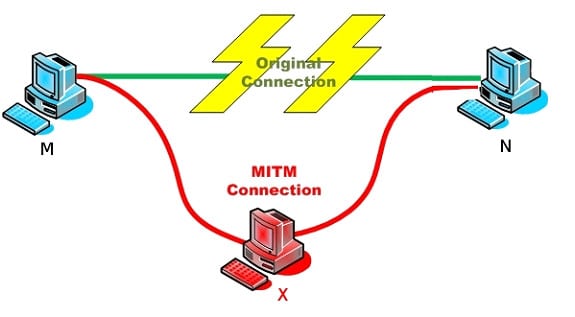
Wiretapping is the most common analogy used to help people understand sniffing attacks. In the old days, the police would get a technician to reroute the physical circuit so that they could listen in on the calls of a suspected criminal and record them. By inserting themselves into the connection, they would know everything that the criminal discusses over the phone line, and they could use this information to build a case.
Sniffing attacks follow very similar concepts, except with updated technology. Basically, an attacker can insert themselves into the network, and then record all of the packets passing through it. This can give them access to information that an organization or the users of its network want to keep private.
Attackers may be able to use a packet sniffer to intercept data packets that contain things like usernames, passwords and other valuable data. They could use what they learn from the sniffing attack to take over accounts, escalate their privileges, and further penetrate into the targeted network. This could lead to all kinds of havoc for the victims.
Attackers could also attempt to directly intercept data packets that contain valuable information like credit card numbers and electronic protected health information. Then they could take this information and abuse it themselves, or sell it on darknet marketplaces.
When data is sent via unencrypted protocols, it is vulnerable to sniffing attacks. These insecure protocols include:
- HTTP
- POP
- SMTP
- IMAP
- TELNET
- FTP
- DNS
How do attackers launch packet sniffing attacks
There are many different ways that an attacker can sniff packets. These vary based on the attacker’s goals, as well as the setup of the targeted network, such as whether it is wired or wireless, and which security mechanisms are protecting it.
Packet sniffing on wi-fi networks
The ease of sniffing wi-fi packets will depend on a variety of factors. First of all, an attacker must have access to the router so that they can actually intercept the data packets.
If the attacker is across town or in another country and cannot directly access the wi-fi signal of their target, they will need to figure out a way to load malware onto one of the systems within the network.
In the rare case that a wi-fi network is unsecured, an attacker can sniff the data packets by being within range, turning their wireless network interface controller to either promiscuous or monitor mode, and running a program like Wireshark.
Monitor mode and promiscuous mode
Let’s break this down a little. Wireless network interface controllers are the components of computers that allow them to pick up wi-fi signals and connect to networks.
They have two modes that are useful in this scenario. Monitor mode allows them to monitor all of the wi-fi traffic, without having to associate with an access point. However, attackers using monitor mode still won’t be able to access encrypted data, unless it uses a weak form of protection. Networks that are only protected by the outdated WEP protocol are a good example of this, but we will discuss them more thoroughly in a moment.
Promiscuous mode allows either a wired network interface controller or a wireless network interface controller to hand all of the packets it receives over to the CPU. This means that promiscuous mode can pick up all of the packets sent over the wired or wireless network that the device is connected to, rather than just the packets that are addressed to the device.
Note that the main differences between monitor mode and promiscuous mode is that monitor mode is wi-fi only, while promiscuous mode is both wi-fi and wired. Monitoring mode does not require the device to be connected to the network, while promiscuous mode does.
Other protection mechanisms
In the above scenario, an attacker will be able to intercept the packets, but this does not necessarily mean that they will be able to access all of the data. While having the wi-fi password may allow them to circumvent the encryption at that level, traffic is often encrypted by other means.
These days, the overwhelming majority of popular websites use HTTPS, which encrypts the connection between the browser and the web server.
When HTTPS is in place, it prevents hackers from being able to access sensitive data like usernames, passwords and credit card details via packet sniffing. If the target is using a VPN, this also encrypts the packets and prevents a hacker from being able to access the data.
These varying security mechanisms mean that packet sniffing isn’t as fruitful as it once was. In many of the situations we will discuss in this article, packet sniffing may not actually help an attacker find much useful data in practice. In cases where it does, it often needs to be combined with a range of other attack techniques.
WPA, WPA2 and WPA3 protected networks
These days, most wi-fi networks are secured by some form of Wi-Fi Protected Access (WPA), which means that the packets are encrypted and an attacker can’t just show up unannounced and listen in. They need to do a little prep-work first.
One option they have is to just be given the password. In this case, they could be a formally trusted user of the network who has simply turned rogue. Another scenario is if the password is weak and can be cracked by an attacker.
Attackers may also be able to target security vulnerabilities, especially in cases where the outdated first version of the protocol is securing a network. There are numerous ways to do both of these things, but covering them all would take us off on too much of a tangent.
Even if an attacker can come up with the password, they still face additional barriers. Each WPA connection is encrypted with its own pairwise transient key, which is dynamic. This means that each device that connects to the access point has a different key, and the attacker’s key will be different to the key of their target.
Because of this, an attacker needs to find a way to steal the target’s key if they want to access their network data. To do this, they need to be able to capture the handshake between the access point and the client they are targeting.
The handshake is the mechanism through which the two parties establish a secure connection. Listening in on this connection can give the attacker all of the information they need to figure out the target’s key.
Once the attacker has the key in hand, they can use it to decrypt all of the packets and inspect the data that is traveling between the target and the access point. This How to decrypt WPA traffic in Wireshark guide does a great job of explaining the whole process.
WEP-protected networks
There may still be some legacy systems that are only protected by Wired Equivalent Privacy (WEP), which is an old security system. It is trivial for hackers to crack because it uses the outdated RC4 algorithm for encryption.
In these cases, the attacker can easily figure out the password if they don’t already know it. All they have to do is monitor the WEP-protected device for a few minutes. This allows hackers to capture the random initialization vectors that are transmitted as plaintext, and they can then use this information to figure out the key that protects the network.
When data is only secured by WEP, it doesn’t have the additional protections that are provided by the various versions of WPA. This means that there aren’t individual keys for each connection to the access point. Therefore, once an attacker has the password, they can decrypt their target’s traffic and inspect the data.
Packet sniffing on wired networks
Things have come a long way over the past decade or two, and now only the most incompetently administered networks will lack security mechanisms. This means that in most cases, an attacker won’t be able to easily plug into an organization’s ethernet cable and siphon up data. Despite this, there are still a number of attacks which may be viable in rare cases.
Passive and active sniffing attacks
Sniffing attacks were traditionally broken down into both passive and active attacks. To understand the difference between the two, we need to cover some of the networking hardware basics.
Hubs and passive sniffing
A hub is a piece of hardware that connects multiple computers into a shared network segment. It relays the data it receives to all of the computers that connect to it. Data that comes in one of its ports then gets pushed out to all of the other ports, meaning that all of the connected computers receive the data traffic, even network packets that are not specifically for them.
Hubs can be passively sniffed. which means that attackers can use the MAC addresses to quietly listen in to the network traffic. Because the data is repeated to all ports, an attacker can often suck up the data while evading detection for a long time. However, hubs are outdated technology that are rarely used these days, so opportunities for this type of passive sniffing are extremely uncommon.
Switches and active sniffing
Switches are more advanced pieces of hardware. They transmit data to the specific MAC addresses of computers on a network, rather than using the inefficient approach that hubs use and repeating data to all ports, even where it isn’t needed.
Sending the data only to where it is needed makes the attacker’s job more difficult, because the attacker can’t just listen in to the data being unnecessarily repeated out of the ports. Instead, attackers must use other tactics.
MAC flooding
One option is to overwhelm the switch with a large number of fake requests, which fills up the content-addressable memory (CAM) table. In this case, the CAM table contains the MAC addresses, which the switch uses to send data to the correct computers.
Filling up the CAM table causes the switch to lose the MAC addresses for the specific computers where it is supposed to send traffic. This is known as MAC flooding, and it forces the switch to act like a hub. Once the switch has been flooded, the switch starts sending data to all ports rather than only to where the data is needed, just like a hub would. This enables the attacker to listen in and inspect the packets.
The downside of this approach is that it is far more obvious. While it is more practical on most modern networks, an active sniffing attack against a switch is unlikely to go undetected for as long as the passive sniffing attacks of yesteryear.
Sniffing vs spoofing attacks
In essence, sniffing attacks involve the unauthorized listening in on network traffic. When they are used against secure modern networks, they often require a few tricks from the hacker, but ultimately, the focus is to just capture the data. The hackers can then use the data they intercept for a range of other purposes, including selling it or using it to gain further privileges in the network.
An example of an attacker using spoofing to impersonate another party. This allows them to launch a man-in-the-middle attack. ARP Spoofing by Saeed azadi licensed under CC BY-SA 4.0.
Spoofing, on the other hand, involves the attacker impersonating another party. Hackers trick their victims into sending them data that is meant for someone else. Often, the two attacks can be used to achieve relatively similar aims—to access valuable data. There are a wide variety of spoofing attacks, including DNS spoofing, MAC spoofing and ARP spoofing.
Examples of sniffing attacks
We have collected some examples of how packet sniffing attacks play out in the real world to give you an idea of how they are actually used. As you will see, sniffing is usually just a small portion of the attack, and there are usually a large number of other techniques involved, including tricking the target into downloading malware.
EMOTET banking malware
A good example of a sniffing attack was found in the EMOTET banking malware. Trend Micro first published a report on the malware in 2014. The examples of EMOTET first described by Trend Micro began with spam emails.
Many of these were with shipping invoices or messages concerning bank transfers, which are the kinds of messages that people often feel pressured to click on, simply because they seem so important.
When a target clicked on one of the links in the email text, it would ultimately end up downloading variants of EMOTET onto the system. Once EMOTET had a foothold, it would download its component files. These included a configuration file with information about banks that the group behind the malware were targeting. This configuration file did vary somewhat between infections, but in many cases, the lists focused heavily on German banks.
Another component was a .DLL file, which would then be injected into all processes to log outgoing network traffic. This is where the sniffing part of the attack came into play. The malicious .DLL file was injected into browsers, where it would compare websites accessed by the browser with those that were listed in the configuration file.
When the strings of a website matched with those that were targeted in the configuration file, the malware would steal any of the data it could from the connection. It intercepted this banking data by sniffing out the data by a process known as API hooking.
This is a more advanced form of sniffing than the examples we discussed earlier in the article, and it takes advantage of the way that different applications share data with each other to enhance functionality and make processes smoother. Discussing it in depth would take us off on too much of a tangent, so feel free to dive into the link above if you would like to find out more.
EMOTET monitors network traffic by hooking the following APIs:
- PR_OpenTcpSocket
- PR_Write
- PR_Close
- PR_GetNameForIndentity
- Closesocket
- Connect
- Send
- WsaSend
This setup led to an interesting situation. When Trend Micro’s researchers experimented with the malware and attempted to log in to a bank, they found that EMOTET was able to capture their login details.
Even though the login page was protected by TLS, the API hooking allowed the malware to steal the information before it was encrypted. This technique circumvented the security protections, posing a grave threat to valuable user data.
The attack’s use of sniffing was a relatively novel way of stealing information, because other attacks at the time often relied on phishing, inserting fake forms into a webpage, and other tactics to steal data, rather than monitoring network activity.
Sniffing the network traffic also made the attack harder to detect, because it didn’t involve any visible changes to the website, such as new input fields or a phishing page.
Another tactic that helped EMOTET avoid detection was its use of registry entries. Both the component files that EMOTET downloaded onto the system, as well as the stolen information, were stored in registry entries.
Most normal users rarely check their registry entries for suspicious activity, so this approach helped EMOTET to remain undetected in the system.
Over time, the EMOTET malware evolved and became more widespread. It was used to deliver dangerous payloads and in 2020 it was classified as one of the most widespread strains of malware in the world. However, in 2021, Europol conducted a string of arrests which disrupted much of the group’s infrastructure, limiting it’s abilities to continue its reign of cybercrime.
BIOPASS RAT sniffing attack
In the middle of 2021, Trend Micro discovered another attack that involved packet sniffing. They dubbed it BIOPASS RAT, and they noticed it was targeting Chinese gambling companies. It began with a watering hole attack, with a malware loader that was carefully disguised to look like Microsoft Silverlight, Adobe Flash Player and other common apps.
The loader would then either deliver the Cobalt Strike shellcode, or the newly discovered BIOPASS RAT backdoor, a remote access Trojan that was written in Python.
BIOPASS RAT included some of the malware basics, like remote desktop access, file system assessment, file exfiltration, and shell command execution. It even had the capability to steal data from instant messaging clients and web browsers, which enabled it to gather up personal information.
Trend Micro thought that BIOPASS RAT was still in active development, because it relied so heavily on Cobalt Strike. The company’s researcher’s also found version numbers in the code, which could be an indicator that the attackers were still working on its development.
One of BIOPASS RAT’s more interesting features is that it abused the framework of Open Broadcaster Software Studio to sniff packets. This is a video recording and live-streaming app.
BIOPASS RAT used the Real-Time Messaging Protocol (RTMP) to set up live streaming to a cloud service controlled by the attacker. It also abused Alibaba Cloud’s Object Storage Service, which the attackers used to host both the BIOPASS RAT scripts, as well as the data they stole from victims.
In the context of our article, one of the most important features was one of the two plugins that the attacker used. However, they aren’t implemented in the BIOPASS RAT malware themselves. The one we are interested in is written in Python and referred to as xss_spoof.
The xss_spoof plugin contained a number of Python scripts which were designed to use cross-site scripting (XSS) attacks to infect web servers. It used the WinDivert package, which is a Windows program similar to Wireshark that monitors network traffic. The plugin leveraged WinDivert to inject malicious scripts into the target’s web server response.
The xss spoof scripts accomplished this by capturing the HTTP GET requests that are delivered to port 80. Network traffic with file extensions other than JavaScript and HTML were filtered out with an ignore list that contains all of the types which the attackers weren’t looking for.
When the scripts came across JavaScript of HTML content, they would modify it before sending it to the unsuspecting visitors of a website that the attackers had already compromised.
When a victim came across the modified script, it scanned localhost to detect whether the device had already been infected by BIOPASS RAT. This step stopped the attack from targeting a victim that was already infected.
Taken as a whole, the BIOPASS RAT malware was capable of monitoring a stream of the victim’s desktop in real time, taking screenshots, stealing cookies, and more. It sent all of this data to the attacker’s cloud server. From this point, the attacker could safely sort through it and look for any directly valuable information. They could also seek out sensitive data which could eventually be used in other attacks
Flame sniffing attack
Our next example of a sniffing attack was labeled “…the most sophisticated malware we encountered during our practice; arguably, it is the most complex malware ever found” by a team of researchers that analyzed it. We are talking about Flame, which has been tied to the Equation Group, which in turn has been tied to the US Government’s premiere hackers, the NSA.
To be fair, it was labeled the most sophisticated malware back in 2012, and packet sniffing is just a small portion of what it can do, but it’s still worth talking about the incredible complexity of Flame.
The malware was discovered in May 2012, by Kaspersky Lab, the Russian antivirus company, after it was asked to conduct an investigation by the United Nations International Telecommunications Union. Both the Iranian National Oil Company and the Iranian Oil Ministry had been attacked by malware that was both stealing and deleting crucial information from their networks.
Researcher’s from the company searched through its own archives and discovered filenames and MD5 hashes of the malware that had only been deployed in the Middle East, with Iran being the primary target.
The same malware was also being independently analyzed by the Laboratory of Cryptography and System Security (CrySyS Lab) at the Budapest University of Technology and Economics. The malware is also known as Flamer, Skywiper, or, if you prefer strange capitalizations, sKyWIper.
Flame is far too broad for us to be able to discuss all of its modules and capacities, but we can zero down on the aspects that relate to packet sniffing. In addition to Flames’s many other ways of gathering data from victims, it also had a packet sniffer module.
When a machine was infected by Flame, this module could sniff all of the traffic on the local network that it was connected to. This allowed it to collect usernames and password hashes traveling throughout the network. The attackers could use this information to take over administrator accounts, giving them privileged access to other parts of the network.
In addition to this, Flame could capture screenshots, keyboard activity and even record audio. It could also turn infected devices into Bluetooth beacons, which tried to download contact information from devices within range.
Ultimately, the data was sent to command and control servers situated around the world, and Flame awaited further instructions from its operators. The complexity of the malware indicated that it was clearly developed by a nation-state actor, while the Middle Eastern targets and certain signatures led many to attribute it to either the US or Israel, or perhaps a collaboration between the two.
Kaspersky’s original estimates indicated that Flame had only infected around 1,000 machines, most of which were owned by government organizations, private companies, educational institutions and individuals.
However, after it was discovered, the operators sent a suicide code which removed it from infected machines. The command was sent out by the command and control server and it was capable of removing all of the Flame files on an infected computer. This helped the creators hide their tracks once they had been busted.
In 2019, security researchers discovered a new version of Flame, which they dubbed Flame 2.0. It was linked to the GOSSIPGIRL malware and likely operated from 2014 to 2016. It included new measures that were even more sophisticated to counter any meddling from researchers.
How to detect sniffing attacks
One way to detect packet sniffing on a network is to look for devices that are set to promiscuous mode. It’s easy to detect on Linux and Unix systems. A privileged user can simply run the ipconfig -a command, and then search for a string that says PROMISC.
If it appears in the search, then there are machines on the network that are on promiscuous mode. These could be set to promiscuous mode for valid reasons, so it isn’t a certain indicator that malicious packet sniffing is occurring on your network. However, at least it gives you some insight.
Microsoft offers the free tool Promqry on its website, allowing you to gain similar insight into Windows systems. However, Promqry cannot detect sniffers on operating systems other than Windows, nor can it detect them on standalone systems.
How to defend against sniffing attacks
If you want to keep your network safe from packet sniffers, you should follow the steps below:
Secure your network
Earlier in the article, we mentioned that legacy systems were vulnerable to sniffing. If your networking is using an outdated security mechanism like WEP, you are incredibly vulnerable to sniffing attacks. It’s best to use WPA2 or even WPA3.
We already discussed how hubs are incredibly easy for attackers to sniff. It’s best to update your equipment and use a network switch instead. On top of this, you should limit physical access to your systems to prevent attackers from being able to install packet sniffing hardware.
Encryption
Another good plan is to make sure that as much data as possible is encrypted. Sniffing operates at the packet level, but if the packets are encrypted, there isn’t much that the sniffer can detect, apart from a jumble of seemingly random characters.
This is why it is important to use security mechanisms like HTTPS, VPNs, secure messaging apps and other tools for encryption wherever possible. If the data is securely encrypted, it doesn’t really matter if a hacker intercepts it with a packet sniffer.
There is one caveat to this, particularly if your threat model includes nation-state attackers. Standard encryption algorithms like AES are safe for now, however, this is only true with current techniques and computing power.
Over time, computers will become more powerful — vastly more so in the case of quantum computers — and cryptographers will develop new techniques. This means that data which is safely encrypted today may no longer be secure in 10 or 20 years.
An adversary could potentially capture your encrypted packets and hold onto them until decrypting them becomes financially viable, eventually finding out all of your secrets. In most cases, this isn’t too much of a worry, because not that many adversaries are playing such a long game.
It’s also worth considering that data that is sensitive now may be useless in the future. If we were to capture the HTTPS packet that contained your encrypted Facebook password, we may be able to decrypt it in 20 years, and access all of your data. But, most people will have changed their passwords within that period, so the old password would no longer be useful.
Besides, if you have been using the same password for 20 years, you probably have bigger security worries than your Facebook account being hacked in a few decades.
Avoid public wi-fi
When you connect to public wi-fi, you don’t know who else may be listening in. The access point may even just be an elaborate ruse set up by an attacker in order to launch man-in-the-middle attacks against unwitting internet users.
If you must use public wi-fi, you should at least use a VPN. When you are connected through a VPN, all of the data is encrypted between the client on your device and the VPN server. The better VPN providers offer automatic public wi-fi protection.
You should absolutely never log in to a website over public wi-fi if you don’t see HTTPS in the left of the address bar. If it only says HTTP, this means that your data isn’t encrypted, and an attacker could easily see your login details. In fact, you should never log in to a website that only uses HTTP. Given that most browsers now block HTTP sites, this isn’t something you’re likely to encounter.
Antivirus
As you saw in the examples we listed, attackers often planted malware onto the target systems so that they could sniff the packets. This means that a good antivirus solution can help to defend your data against unauthorized packet sniffing. Tools like Windows Defender and Malwarebytes are good options to start with, because they are relatively effective and include minimal bloat.
Of course, it makes even more sense to limit your chances of encountering malware in the first place. This means that you need to be on the lookout for phishing attempts, and you should never click on any suspicious links or attachments.
You should also avoid the sketchier parts of the web, such as online gambling sites, and those that provide x-rated content. It’s also important to keep all of your software updated, because attackers often take advantage of the vulnerabilities left in unpatched software. This includes your operating system, web browser, plugins and other tools.
Packet sniffer: friend or foe?
Packet sniffers are tremendously useful for diagnosing network issues and giving you insight into the traffic traveling across your network. However, they also pose a threat if you aren’t taking the right security precautions. But as long as you follow the steps outlined above, such as encrypting as much of your data as possible and avoiding risky internet activity, you don’t have too much to fear from packet sniffers.