The cutting edge of internet privacy and anonymity today is Tor, The Onion Router. Developed at the U.S. Naval Research Laboratory in the mid-1990s as The Onion Routing program, Tor came about as a next-generation implementation of the original project.
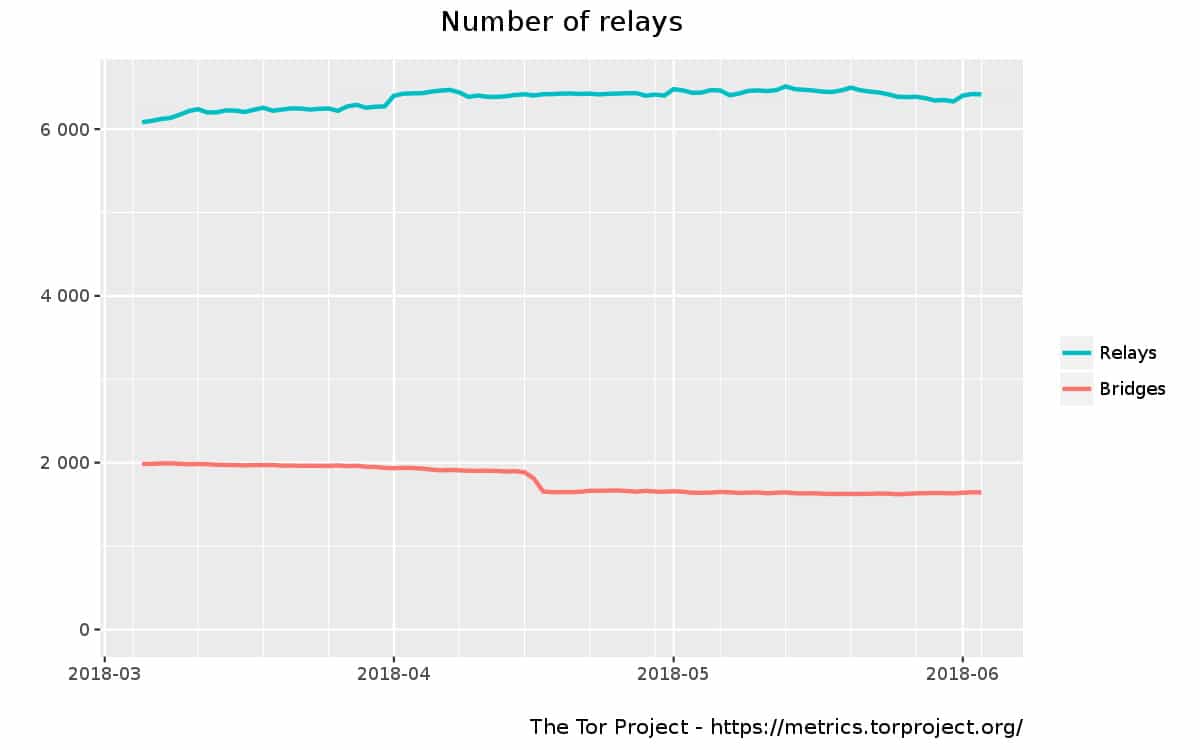
Tor is the most widely used software in the world for anonymously accessing the internet. Tor is made up of close to 7,000 relays and close to 3,000 bridges at the time of writing, all of which are operated by volunteers.
When properly connected to Tor, your web history, online posts, instant messages, and other communication forms cannot be traced back to you.
How does Tor work?
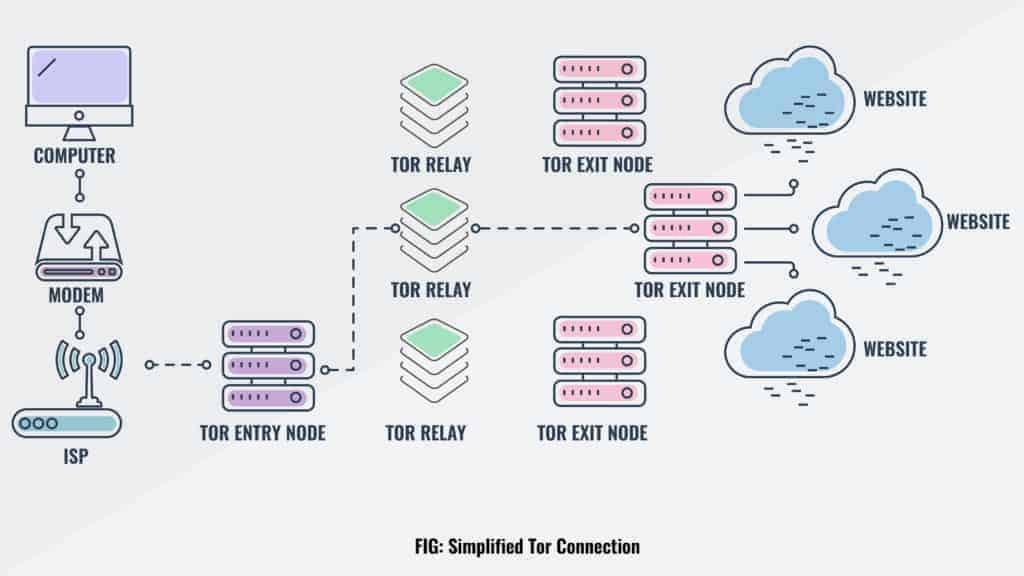
Tor is a network made up of thousands of volunteer nodes, also called relays. A relay is a computer inside Tor, listed in the main directory, that receives internet signals from another relay and passes that signal on to the next relay in the path. For each connection request (e.g. website visited) the path is randomly generated. None of the relays keep records of these connections, so there is no way for any relay to report on the traffic that it has handled.
The Tor network (or simply “Tor”) is made up of close to 7,000 relays and 3,000 bridges at the time of writing.
When you connect to the Tor network, say, through the Tor browser, all the data you send and receive goes through this network, passing through a random selection of nodes. Tor encrypts all that data several times before it leaves your device, including the IP address of the next node in the sequence. One layer of encryption is removed each time the data reaches another node until it reaches the final exit node, a process called onion routing. This means no one, not even the people running the nodes, can see the contents of the data nor where it’s headed.
A bridge is a hidden relay, meaning it is not listed in the main Tor directory of relays. These are provided for people who are unable to access Tor with the normal setup. This can be because the network they are using has a proxy (a sort of intermediary between the user’s computer and the internet gateway) that has been configured to block Tor traffic.
The last relay in the path is the exit node. The exit node is the only part of the network that actually connects to the server that the user is trying to access and is, therefore, the only bit that the server sees and it can only log the IP address of that relay.
Anyone who intercepts the data won’t be able to trace it back to an individual. At best, they can determine the entry or exit node, but never both. This makes it impossible to track the user’s activity and browsing history. All of the relays and bridges are run, believe it or not, by volunteers–people donating some of their bandwidth and computing power to expand Tor’s capabilities.
Tor is setup this way to allow an internet user to surf the web anonymously by hiding their internet address (IP address) from the website and search engines that they access via Tor and by hiding their internet traffic from anyone monitoring their end of the connection. An observer will only see that the user is connected to Tor, and not see any other websites or online resources being sent to the user’s computer.
Also, as another part of the overall network, Tor offers certain hidden services in the form of .onion sites and an instant messaging server. The .onion sites are websites hosted on Tor servers and hidden by randomly generating paths to them from “introductory points” in the network. This allows users to access the sites, but not pinpoint the location of the servers hosting them.
How do I get started with Tor?
The Tor browser is the easiest and most popular way to use Tor. It’s based on Firefox and works like a bare bones version of any other web browser. It’s pretty much plug-and-play; there’s no special tweaks or configuration to start browsing anonymously after the initial setup.
Tor is unique in that it provides anonymous access to both the clear net and the DarkNet. The clear net is what the vast majority of people are most familiar with. Anything on the World Wide Web that you can access with your non-Tor browser is considered the “clear net”. When you access websites on the clear net using the Tor browser, that website has no default way of identifying you because all of your internet traffic already went through Tor’s anonymity network, meaning the website can only see that you are visiting from a Tor exit node.
Accessing the DarkNet
Then there’s the DarkNet. Actually, there’s a few DarkNets, but the one accessible to Tor users is by far the most popular. The DarkNet is made up of hidden services, mostly websites that are not accessible in your day-to-day browser. These Tor hidden services can be identified by their .onion top-level domains appended to the end of their URLs.

Only people connected to the Tor network can access Tor hidden services, they do so anonymously, and they must also know where to look—Google and other search engines do not index .onion websites. Additionally, the Tor network also protects the identity of people who create Tor hidden services, so it’s nearly impossible to know who owns or operates a given .onion site.
Read more: How to access the Darknet and Deep Web safely
This is why the DarkNet is particularly well-suited to crime and has a reputation for being the seedy underbelly of the internet. Although Tor has many great legal and legitimate uses as discussed above, the DarkNet that it houses is also where you’ll find marketplaces for illicit goods and services as well as blogs and forums for extremist groups.
Tor limitations
Web surfing inside of the Tor browser is completely anonymous, but other activities on your computer are not. If you want to connect other applications and services to the Tor network, things start getting more complicated. You can find a list of other projects further down this article.
And although the Tor network will anonymize your connection to the internet, you’re still responsible for keeping yourself anonymous. A single misstep can put your anonymity in jeopardy. Check out our guide on achieving complete anonymity while online.
Keep in mind that because your information is being routed through a series of dedicated relays, the speed will not be what you are used to. It will be considerably lower than what you’re used to, actually. That is because the data is taking a much more circuitous path than normal and will be hampered by:
- The speed of the internet connections of the various relays along that path
- The amount of traffic on those relays
- The overall congestion of Tor at that particular time
- All the normal internet congestion that fluctuates throughout the day
The people at the Tor Project strongly urge their users to refrain from torrenting while using Tor. Torrent traffic, even through Tor, it is not anonymous and will only serve to (a) slow down the network for everyone and (b) completely obliterate any anonymity you may have enjoyed previously. (Torrenting is a way of sharing large chunks of data between peers using special software called a torrent client.) You’re better off using a secure VPN for torrenting, than Tor.
Your internet provider or the company where you work may block the use of Tor on their network. This is fairly easy to achieve as the network administrator just needs to blacklist Tor relays, which are publicly listed. In which case you will need to learn a bit about using bridges (hidden relays) or a VPN to gain access.
Tor’s main weakness is that it is susceptible to traffic analysis attacks, but this isn’t exactly news. The original design documents even outlined this type of vulnerability. That being said, Tor was never meant to stand up to a large scale attack of poisoned nodes.
Combining Tor with a VPN
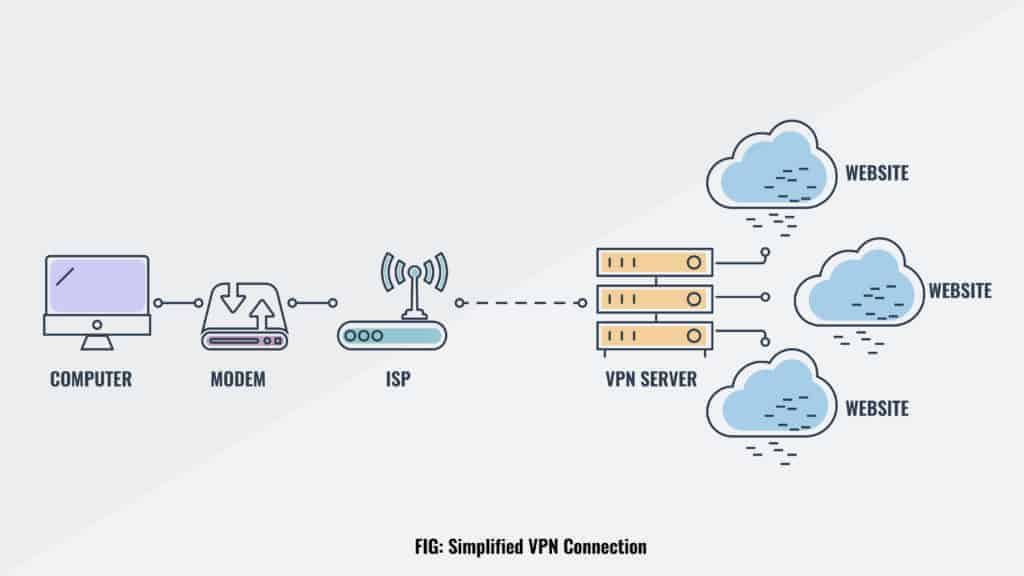
The best way to stay private is to use both Tor and a VPN together. A VPN, or Virtual Private Network, is an encrypted tunnel on the internet from your computer to a VPN server. Any web surfing you do over a VPN looks like it is coming from the VPN server, and not from your computer.
By way of example, a user in New York, NY can connect to a VPN server in Los Angeles and any websites that she accesses will see her as being a user in California, not New York. Her ISP in New York will not be able to see any of her web traffic. In fact, all that the ISP will see is that she has encrypted data going back and forth between her computer and the VPN server that she is connected to. Nothing else.
A VPN does not make the user anonymous (although most commercial VPN services add a layer of anonymity by having users share IP addresses). It only provides an encrypted tunnel between your computer and the VPN server that you are connected to. Whoever operates the VPN server can technically snoop on your online activity, though reputable VPN services claim not to do this in their privacy polices.
Tor is used to make your connection to any websites that you visit anonymous. Your computer connects to a Tor entry node, and all of your traffic then hops through an intermediary relay to an exit node before finally reaching the destination website. Your ISP can see that you are connecting to a Tor entry node, which is enough to raise eyebrows in many cases.
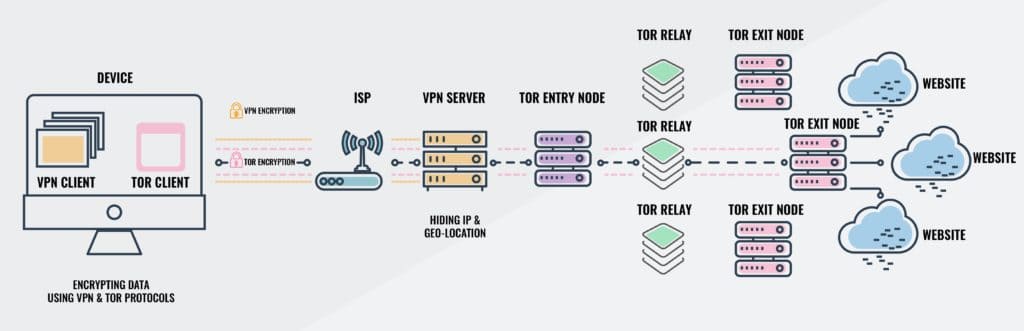
The solution seems simple enough. Connect to a VPN, then open the Tor browser and surf anonymously in private. Your ISP can’t see that you’re connected to Tor, and your VPN can’t read the contents of Tor traffic.
This solution appears to have created a bit of confusion, though, as people wonder if it is better to connect to the VPN first or Tor.
The easier option is to connect to your VPN and then launch the Tor browser. The more complicated option is to do it the other way round. This requires a remote secure shell connection to the VPN server or a VPN client that has this capability built in as a configuration option. You will most likely see something along the lines of using Tor as a “proxy” for the VPN client. That should initiate the secure connection through Tor.
Tor over VPN
In the first setup, Tor over VPN, your ISP sees that your computer is sending and receiving encrypted information with a specific server, and that is all. The VPN server only sees that it is connected to a Tor entry node and that all of your surfing is being handled through that network. All of the websites on the other end of Tor do not see any personally identifiable information. NordVPN operates servers with Tor over VPN pre-enabled so you don’t have to use Tor Browser, but bear in mind that Chrome and other common browsers might give websites other identifying information.
VPN over Tor
In the second setup, VPN over Tor, your ISP sees that your computer is communicating with a Tor entry node. The VPN server gets your login information from a Tor exit node, which can be considered personally identifiable information, thereby breaking Tor’s anonymity. The websites that you connect to only see the VPN server’s address. AirVPN and BolehVPN are just two VPN providers that allow users to connect using VPN over Tor.
If your VPN provider does keep logs of activity, any benefit you might have received from the Tor connection is lost.
Be part of the Tor network
If you find Tor useful and would like to support it, you can volunteer to create and maintain your own Tor node for others to use. Check our tutorial on how to build your own Tor relay, but be warned that doing so comes with a high probability that law enforcement and/or your internet service provider will take notice and approach you with questions. You’ll need a spare server or computer lying around to act as the node.
You can also set up your own Tor hidden service, which essentially means you create a website or service only available on the DarkNet. Again, this could draw undue attention from your ISP and law enforcement, but there’s nothing inherently illegal about it. Check out our guide on how to set up a Tor hidden service.
Note that operating a Tor relay or hidden service requires quite a bit more technical expertise than simply browsing the web with the Tor browser.
Is Tor legal?
Even though using Tor is completely legal, simply connecting to it is cause for suspicion in some areas of the world. No one has ever gone to prison or even been fined for using Tor. But there have been reports of people being questioned by their ISP and local law enforcement regarding their browsing habits simply because the ISP’s logs show that they are connecting to Tor.
Those who run a Tor relay are cautioned that they will eventually be contacted by either their ISP or local law enforcement, maybe both, regarding some illicit activity online that is linked to the IP address used by their relay. To date, in all instances, simply informing these entities that the IP address in question is assigned to a node of the Tor network and that no logs are kept on that server has been sufficient.
Who uses Tor?
The number of people accessing the internet through Tor changes almost every day. Between August 2012 and July 2013 the Oxford Internet Institute and the University of Oxford calculated that “over 126,000 people access the Internet through Tor every day from the United States.” This translates to somewhere between .025% and .05% of internet users in the United States.
True to their claim, there are no stats available from the folks at TorProject concerning what their userbase is doing online or what sort of content they are accessing. It’s a safe bet that most of the users of Tor are legitimately just trying to maintain their anonymity for obvious reasons.
- Journalists who are protecting their sources,
- Whistleblowers trying to keep their jobs,
- Law enforcement officials trying to track down criminals and not blow their cover in the process,
- Corporate IT professionals conducting security testing on their own networks,
- And a bunch of other users that need the anonymity that Tor provides just to do their jobs.
For a more concise list of possible legitimate uses of anonymity, check out Tor’s description of their userbase.
Alternatives to Tor
One thing that is obvious is that Tor is not finished. In spite of that, some of you are already asking yourselves “Ok. What else is out there?” Well, you’re in luck. As it so happens there are other tools out there for those who wish to avoid being tracked. Here are a few of the most popular that are currently available.
I2P
 Similar to Tor, I2P, or the Invisible Internet Project, uses a distributed network database and peer selection for anonymous traffic. Also susceptible to traffic analysis attacks, I2P does have some benefits over Tor. The peers are selected through continuous profiling and ranking performance. It is also small enough that few, if any, active blocks are in place to prevent access.
Similar to Tor, I2P, or the Invisible Internet Project, uses a distributed network database and peer selection for anonymous traffic. Also susceptible to traffic analysis attacks, I2P does have some benefits over Tor. The peers are selected through continuous profiling and ranking performance. It is also small enough that few, if any, active blocks are in place to prevent access.
Freenet
![]() Unlike Tor, Freenet does not rely on dedicated entry and exit points. Instead, users connect to Freenet preferably through their friends’ computers. If you don’t have any friends on Freenet, you do have the option of connecting through strangers’ computers, but that is considered less secure than connecting to the computers of trusted friends. Freenet also is a file distribution service where encrypted files are stored on computer hard drives throughout the network. Due to the encryption, it is unlikely that a user would be able to determine what that file actually is.
Unlike Tor, Freenet does not rely on dedicated entry and exit points. Instead, users connect to Freenet preferably through their friends’ computers. If you don’t have any friends on Freenet, you do have the option of connecting through strangers’ computers, but that is considered less secure than connecting to the computers of trusted friends. Freenet also is a file distribution service where encrypted files are stored on computer hard drives throughout the network. Due to the encryption, it is unlikely that a user would be able to determine what that file actually is.
JonDoFox
 Another onion routing-type anonymizer for web surfing, JonDoFox is a profile for Mozilla Firefox or Firefox ESR. The user’s computer connects to a series of Mix operators that anonymize the user’s web traffic and wrap it in several layers of encryption. Just like Freenet, the network size is considerably smaller than Tor’s. This is primarily due to their certification process. In order for you to become a mix operator, you must go through their certification process. Theoretically, this could lower the chances of an attacker sneaking in modified servers, but such a claim would have to be tested in a simulated environment.
Another onion routing-type anonymizer for web surfing, JonDoFox is a profile for Mozilla Firefox or Firefox ESR. The user’s computer connects to a series of Mix operators that anonymize the user’s web traffic and wrap it in several layers of encryption. Just like Freenet, the network size is considerably smaller than Tor’s. This is primarily due to their certification process. In order for you to become a mix operator, you must go through their certification process. Theoretically, this could lower the chances of an attacker sneaking in modified servers, but such a claim would have to be tested in a simulated environment.
GNUnet
 GNUnet is a peer-to-peer file sharing tool that relies on large groups to obfuscate the identities of those that are attached to the group. An individual in the group is virtually indistinguishable from any other user by anyone but the initiator of the group.
GNUnet is a peer-to-peer file sharing tool that relies on large groups to obfuscate the identities of those that are attached to the group. An individual in the group is virtually indistinguishable from any other user by anyone but the initiator of the group.
Tor alternatives still in development
The following projects are still in development, but are working toward creating even stronger anonymity networks, but for more specific applications. Tor was created as a sort of generic, one size fits all solution for anonymous web use. These projects are more focused on specific applications of web use.
Aqua/Herd
Aqua is a file sharing network designed to be completely anonymous, while Herd is an anonymous Voice over IP network. The designers are working up a means of stripping the metadata from the network traffic, which is the primary way of tracing a client and the server that client is communicating with.
Vuvuzela/Alpenhorn
Alpenhorn is the second iteration of Vuvuzela, named after the horn normally used at soccer matches in Latin America and Africa. Alpenhorn is an anonymous, metadata free chat program that can be scaled to millions of users, in theory. Expect a public beta in the near future.
Dissent
If anonymity is more important to you than latency, then Dissent offers some of the strongest available anonymity. Due to the higher latency and low bandwidth, dissent is best used for blogging, micro-blogging or even IRC type communications. The way Dissent works is rather simple, but bandwidth heavy. When one client transmits anything, all the other clients transmit a package of the same size. Instead of using onion routing, Dissent is based on DC-nets, a dining cryptographers algorithm. Combine that with a verifiable shuffle algorithm and you end up with the most anonymous design being looked at by researchers today.
Riffle
Anonymous file sharing is becoming more and more sought after. Riffle is yet another attempt at providing an anonymous way for a user to share files of any size. However, it is not meant as a replacement for Tor, mainly because file sharing over Tor breaks anonymity. Riffle is meant to augment Tor by providing Tor users with a truly anonymous way to share files, without choking the Tor network. Inspired by Dissent, Riffle also uses a shuffle algorithm but drops the DC-net cryptographic algorithm.
Riposte
Riposte was inspired by Dissent, but focused on micro-blogging. Micro-blogging is currently the realm of Twitter, Pinterest and other such services where users update their “blog” with small snippets of information like quotes from famous people or requests for feedback or even requests to join networks. Riffle is designed to allow a user to micro-blog anonymously at the expense of internet speed. Following in the footsteps of Dissent, Riposte also uses the DC-net type setup for hiding the original transmission in a storm of transmissions of random data bits of the same size.
Tor projects
Finally, as an added bonus, here is a list of all the other projects in the works over at TorProject, all with an interest in maintaining internet privacy for any and all who wish to make use of their products. Some of these are rather obvious and user friendly, while others are more behind-the-scenes. A couple of different programming libraries are available for software developers to allow their products to communicate with The Onion Network.
The Tor browser
This is what most people use to access Tor. It’s very simple to acquire and use. The browser is actually a customized version of Mozilla Firefox, and therefore looks and feels like any other web browser. The customization is designed to leave no trace of your web surfing on the computer. Simply download the compressed file for your operating system, be it Windows, MacOS or Linux, extract it to its own folder, run the executable file inside that folder and surf to your heart’s content in complete anonymity. When you close the browser, all traces of your browsing are cleared from memory. Only your bookmarks and downloads are left behind.
.onion web sites
![]() These are websites that are only accessible within the Tor network, and by knowing where to go. There are special search engines like Onion.city and Onion.to, as well as a host of others. Keep in mind, though that there are hoaxes, scams, and honeypots strewn throughout the DarkNet. Be wary of what you click on. There are also some very disturbing images available in there. You have been warned.
These are websites that are only accessible within the Tor network, and by knowing where to go. There are special search engines like Onion.city and Onion.to, as well as a host of others. Keep in mind, though that there are hoaxes, scams, and honeypots strewn throughout the DarkNet. Be wary of what you click on. There are also some very disturbing images available in there. You have been warned.
Orbot
![]() You can access the Tor network on your Android device using Orbot. Orbot creates a Tor proxy on your device so that all internet traffic from your device goes through the Tor network. That means that all the apps on your phone or tablet will have their traffic routed through Tor as well. Of course, some apps are designed not to be anonymous and will break the anonymity provided by the Tor network. True anonymity requires just a few steps to make sure tattlers are disabled or, at the very least, not running while you’re tapping into Tor. Remember to disable auto-sync and shut down any apps that automatically log you into an account, like Gmail, Yahoo!, Facebook, Twitter and the like.
You can access the Tor network on your Android device using Orbot. Orbot creates a Tor proxy on your device so that all internet traffic from your device goes through the Tor network. That means that all the apps on your phone or tablet will have their traffic routed through Tor as well. Of course, some apps are designed not to be anonymous and will break the anonymity provided by the Tor network. True anonymity requires just a few steps to make sure tattlers are disabled or, at the very least, not running while you’re tapping into Tor. Remember to disable auto-sync and shut down any apps that automatically log you into an account, like Gmail, Yahoo!, Facebook, Twitter and the like.
OrFox
 To go along with Orbot, there is also a browser for Android devices that allows you to surf the net using Tor. However, this only applies to web surfing in a browser. All the other apps on your Android device will be communicating through normal lines of traffic without the benefit of anonymity provided by the onion router.
To go along with Orbot, there is also a browser for Android devices that allows you to surf the net using Tor. However, this only applies to web surfing in a browser. All the other apps on your Android device will be communicating through normal lines of traffic without the benefit of anonymity provided by the onion router.
Tails
 This might be the ultimate usage of Tor. It is a “live operating system” that is run either from a CD or a USB thumb drive or memory stick. Put this in a computer right before you restart. If the computer’s BIO is setup correctly, it will load Tails instead of the OS that is loaded on the computer’s hard drive. Perfect for using a computer that does not belong to you for surfing the web anonymously and leaving no trace of your browsing anywhere on the computer. The computer’s internal hard drive is not touched while the computer is running Tails and the computer’s memory is erased with each reboot. Also, any cookies or temporary internet files that are loaded into Tails are not recorded to the CD or thumb drive while in use so those are also lost as soon as the computer is restarted.
This might be the ultimate usage of Tor. It is a “live operating system” that is run either from a CD or a USB thumb drive or memory stick. Put this in a computer right before you restart. If the computer’s BIO is setup correctly, it will load Tails instead of the OS that is loaded on the computer’s hard drive. Perfect for using a computer that does not belong to you for surfing the web anonymously and leaving no trace of your browsing anywhere on the computer. The computer’s internal hard drive is not touched while the computer is running Tails and the computer’s memory is erased with each reboot. Also, any cookies or temporary internet files that are loaded into Tails are not recorded to the CD or thumb drive while in use so those are also lost as soon as the computer is restarted.
Arm
![]() You were first introduced to Arm at the end of the “How to build your own Tor relay or node” article. Arm is a command line-based monitor for a Tor relay. It displays real-time information for a relay or bridge in the Tor network. This helps you keep an eye on your relay by providing statistics, metrics and health reports. You can learn how many Tor users have accessed Tor through your relay or how much of your available bandwidth is being used in support of Tor.
You were first introduced to Arm at the end of the “How to build your own Tor relay or node” article. Arm is a command line-based monitor for a Tor relay. It displays real-time information for a relay or bridge in the Tor network. This helps you keep an eye on your relay by providing statistics, metrics and health reports. You can learn how many Tor users have accessed Tor through your relay or how much of your available bandwidth is being used in support of Tor.
Atlas
![]() Atlas is a web application that provides information on the current status of the Tor network’s relays. Type the name of a relay into the search box at the top of the site and get a basic overview of its current status. Click on the relay’s nickname to get a much more detailed report along with an explanation of all the flags that apply to that particular node.
Atlas is a web application that provides information on the current status of the Tor network’s relays. Type the name of a relay into the search box at the top of the site and get a basic overview of its current status. Click on the relay’s nickname to get a much more detailed report along with an explanation of all the flags that apply to that particular node.
Pluggable Transports
![]() Used to change the way your data stream appears. This is yet another way of keeping you connected to Tor. Some entities have started blocking Tor traffic based on the traffic itself, not the IP address of the relay or bridge that is being used to connect to the network. Pluggable Transports change the look and feel of Tor traffic to appear to be normal, un-Tor-like traffic to escape detection.
Used to change the way your data stream appears. This is yet another way of keeping you connected to Tor. Some entities have started blocking Tor traffic based on the traffic itself, not the IP address of the relay or bridge that is being used to connect to the network. Pluggable Transports change the look and feel of Tor traffic to appear to be normal, un-Tor-like traffic to escape detection.
Stem
![]() This is the library that developers turn to for creating programs to interact with Tor. Arm is one example of such a program.
This is the library that developers turn to for creating programs to interact with Tor. Arm is one example of such a program.
OONI
![]() While Atlas is a site showing the status of the Tor network, OONI is the site showing the status of censorship in the world today. It does this by probing the internet using a known good result and comparing that result to an unprotected, unencrypted result. Any changes in the results are evidence of tampering or censorship.
While Atlas is a site showing the status of the Tor network, OONI is the site showing the status of censorship in the world today. It does this by probing the internet using a known good result and comparing that result to an unprotected, unencrypted result. Any changes in the results are evidence of tampering or censorship.
TorBirdy
![]() This is an extension for Mozilla Thunderbird that configures it to run on the Tor network. Consider it a Torbutton for Thunderbird.
This is an extension for Mozilla Thunderbird that configures it to run on the Tor network. Consider it a Torbutton for Thunderbird.
Onionoo
![]() Onionoo is a web-based protocol that gets information relating to the current status of The Onion Network. This information is not in a human readable format. It is meant to act as a service for other applications like Atlas or Tor2Web.
Onionoo is a web-based protocol that gets information relating to the current status of The Onion Network. This information is not in a human readable format. It is meant to act as a service for other applications like Atlas or Tor2Web.
Metrics Portal
![]() As the name implies, this is where you get metrics relating to the Tor network like available bandwidth and the estimated size of the current userbase. Any researcher that is interested in any specific, detailed statistics about the Tor network can find it here, or submit a request for the metric that they are looking for.
As the name implies, this is where you get metrics relating to the Tor network like available bandwidth and the estimated size of the current userbase. Any researcher that is interested in any specific, detailed statistics about the Tor network can find it here, or submit a request for the metric that they are looking for.
Shadow
![]() A simulation of a network using the real Tor browser. This is most useful in a lab type setup when you want to see how Tor can affect your network, without impacting your real network. Perfect for experimenting with Tor and various other programs before allowing or implementing them on your local area network.
A simulation of a network using the real Tor browser. This is most useful in a lab type setup when you want to see how Tor can affect your network, without impacting your real network. Perfect for experimenting with Tor and various other programs before allowing or implementing them on your local area network.
Tor2Web
 Grants non-Tor browser users access to websites running in Tor hidden services. The idea is to allow internet users the option of sacrificing their anonymity while still granting them access to information hidden inside the Tor network, while at the same time not sacrificing the anonymity of the websites that they are accessing.
Grants non-Tor browser users access to websites running in Tor hidden services. The idea is to allow internet users the option of sacrificing their anonymity while still granting them access to information hidden inside the Tor network, while at the same time not sacrificing the anonymity of the websites that they are accessing.
Tor Messenger
![]() An instant messenger client that uses the Tor network for all of its transmissions. Secure by default with cross platform capabilities, it is an ideal chat program for anyone wanting to stay secure and anonymous.
An instant messenger client that uses the Tor network for all of its transmissions. Secure by default with cross platform capabilities, it is an ideal chat program for anyone wanting to stay secure and anonymous.
txtorcon
![]() This is a programmers library for writing Python based applications that talks to or launches a Tor program. It contains all the utilities for accessing Tor’s circuits, streams, logging functions and hidden-services.
This is a programmers library for writing Python based applications that talks to or launches a Tor program. It contains all the utilities for accessing Tor’s circuits, streams, logging functions and hidden-services.
What is Tor FAQs
Is Tor free?
Tor is completely free and open source. As the Tor Project itself states, “any browser that forces you to pay and is claiming to be Tor Browser is fake”. Of course, there’s always the argument that if a product or service is free, that you yourself are the product. However, while this may be the case with other browsers such as Chrome (its main source of income is advertising), Tor is instead funded by a number of sponsors and donors.
What are the disadvantages of using the Tor browser?
The main disadvantage of using Tor Browser is the slow speeds. While onion routing ensures traffic is encrypted, the connection can be very slow as a result. This means it’s not suitable for more bandwidth-intensive activities such as streaming or online gaming. Furthermore, Tor only secures traffic traveling through the Tor browser and not that of external apps. This is why some people choose to use Tor in combination with a VPN. However, this can be particularly slow.






I read today….somewhere online, that Tor has a VPN so that ultimately a person could end up with the best of both worlds; is there a Tor VPN? And, how would the best VPN available together with Tor Browser affect streaming speeds? This may be a dumb question but, I truly am somewhat of a beginner who would like to set things up properly from the onset.
I have used a free VPN for a few months and do understand that, something is missing, when I am getting messages quoting my IP address, while denying access. Today, I was denied access to a site that I have been using for years without ever signing on. Afterwards I stopped my VPN and tried again, and sadly I no longer have access at all.
I learned a lot from Tor today and certainly don’t fault my VPN and do believe that, regardless of the security devices I constantly run, in ignorance, I had no awareness that my tracking and ad blocking apps etc., weren’t keeping me safe. My online behaviour has been consistent for years. I am hoping by gathering this new information and keeping informed via Tor, that I can get a fresh start.
Tor has such a long standing reputation, and certainly I will download a Tor Browser and, once I digest and comprehend all the VPN data above, hopefully autonomy will no longer be an issue..
Thank you so much to everyone at Tor, for your unbiased views and your obviously dedicated mission. Most appreciated. Doad
I truly appreciate this website; aside from interesting, it has been enlightening.
Tor doesn’t make a VPN as far as I know. There is a VPN called “TorGuard” but the “tor” in there refers to torrents, not The Onion Network.