Address Resolution Protocol (ARP) poisoning is an attack that involves sending spoofed ARP messages over a local area network. It’s also known as ARP spoofing, ARP poison routing and ARP cache poisoning.
These attacks attempt to divert traffic from its originally intended host to an attacker instead. ARP poisoning does this by associating the attacker’s Media Access Control (MAC) address with the IP address of the target. It only works against networks that use ARP.
ARP poisoning is a type of man-in-the-middle attack that can be used to stop network traffic, change it, or intercept it. The technique is often used to initiate further offensives, such as session hijacking or denial-of-service.
Before you can understand what ARP poisoning is, it’s important to have a solid background on the ARP protocol. Before we can talk about the ARP protocol, we need to back up just a little bit further and talk about the Internet protocol suite.
The Internet protocol suite
When you open up the web browser on your phone, the memes and cat pictures are delivered to you almost instantaneously and with little effort, making the process seem simple.
It can seem as if your phone and the server that hosts the cat pictures are connected like two cups on a string, and that like two children playing telephone, the cat picture just travels along some wires and appears on your phone like the sound of a voice over the string. Given the prevalence of wifi and data these days, it may even seem like the cat picture somehow travels across the ether.
Of course, this isn’t the case. The cat picture’s journey is actually pretty complex, traveling across a multi-layered system that is best approximated with the Internet protocol suite model:
- The application layer – At the application layer, neither you, your web browser or the server software are really aware of how the cat picture got delivered to you. You don’t know how many routers the data for the cat picture went through, or whether it traveled over wireless connections. All you know is that you clicked a link and that the cat picture came to you.
- The transport layer – With the transport layer, we get under the hood a little bit. The transport layer is responsible for establishing a connection between the client (your phone) and the server that hosts the website. The transport layer keeps an eye on the connection and looks for errors, but it doesn’t care about how the data is moved between the client and the server.
- The internet layer – Internet layer software is responsible for moving data between the networks. It doesn’t care about the cat picture’s data and treats it the same as it would treat data for an ebook about chemistry. Once the internet layer software brings the cat picture data to your local network, it hands it off to the link layer software.
- The link layer – Link layer software moves both ingoing and outgoing data within your local network. It takes the data for the cat picture from the internet layer software and delivers them to your device.
Each of the above layers can have a bunch of different protocols running through them to complete their jobs. This mess of a system somehow works cohesively to bring the cat picture from the server to your phone’s screen.
What is the Address Resolution Protocol (ARP)?
The address resolution protocol (ARP) is simply one of these protocols. It’s used to discover which link layer address, such as a MAC address, corresponds with a given internet layer address for a physical machine. These are generally IPv4 addresses, which consist of a 32-bit binary number typically represented in decimal format.
IPV4 addresses provide a way to identify each device connected to a computer network that uses the Internet Protocol (IP) for communication. Unfortunately, the availability of four-byte IPv4 addresses is dwindling. In their place, IPv6 is being rolled out. These contain 128 bits – 16 bytes — each, and use hexadecimal digits for even greater variety.
However, since IPv4 is still the most commonly used internet protocol, ARP generally bridges the gap between 32-bit IPv4 addresses and 48-bit MAC addresses. It works in both directions.
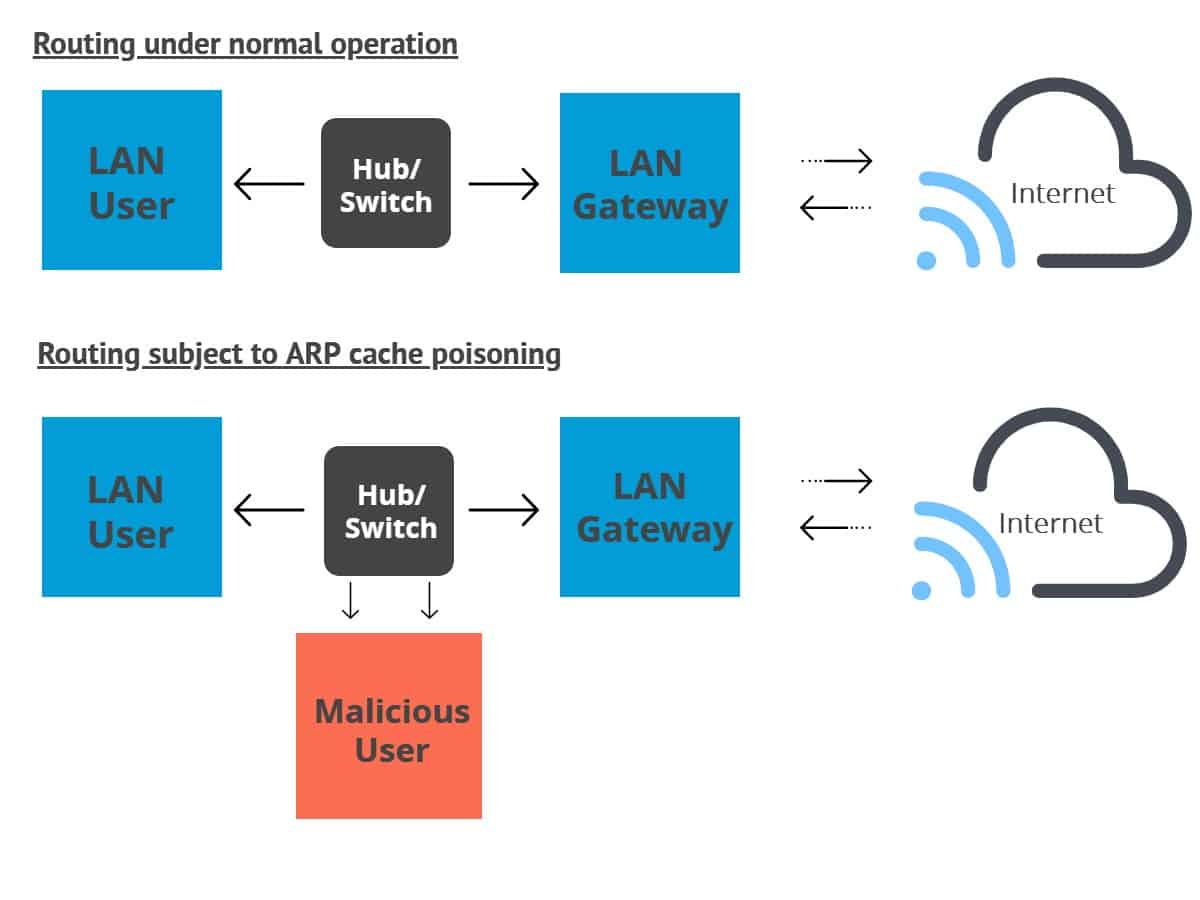
The relationship between a given MAC address and its IP address is kept in a table known as the ARP cache. When a packet heading towards a host on a LAN gets to the gateway, the gateway uses ARP to associate the MAC or physical host address with its correlating IP address.
The host then searches through its ARP cache. If it locates the corresponding address, the address is used to convert the format and packet length. Otherwise, if the right address isn’t found, ARP will send out a request packet that asks other machines on the local network if they know the correct address. When a machine replies with the address, the ARP cache is updated with it in case there are any future requests from the same source.
What is ARP poisoning?
Now that you understand more about the underlying protocol, we can cover ARP poisoning in more depth.
The ARP protocol — which was defined in 1982 — was developed to be efficient, which led to a serious lack of security in its design. This makes it relatively easy for someone to mount these attacks, as long as they can access the local network of their target.
Attackers can potentially gain unauthorized access to local networks through techniques such as phishing, malware, or social engineering.
Once they have network access, ARP poisoning can begin. This involves sending forged ARP reply packets to a gateway over the local network. Attackers typically use spoofing tools like Arpspoof or Arppoison to make the job easy. They set the IP address of the tool to match the address of their target. The tool then scans the target LAN for the IP and MAC addresses of its hosts.
Once the attacker has the addresses of the hosts, they start sending forged ARP packets over the local network to the hosts. The fraudulent messages tell the recipients that the attacker’s MAC address should be connected to the IP address of the machine they are targeting.
This results in the recipients updating their ARP cache with the attacker’s address. When the recipients communicate with the target in the future, their messages will actually be sent to the attacker instead.
At this point, the attacker is secretly in the middle of the communications and can leverage this position to read the traffic and steal data. The attacker can also alter messages before they get to the target, or even stop the communications completely.
Attackers can use this information to mount further attacks, like denial-of-service or session hijacking:
- Denial-of-service – These attacks can link a number of separate IP addresses to the MAC address of a target. If enough addresses are sending requests to the target, it can become overloaded by traffic, which disrupts its service and makes it unusable.
- Session Hijacking – ARP spoofing can be leveraged to steal session IDs, which hackers use to gain entry into systems and accounts. Once they have access, they can launch all kinds of havoc against their targets.
How to detect ARP poisoning
ARP poisoning can be detected in several different ways. You can use Windows’ Command Prompt, an open-source packet analyzer such as Wireshark, or proprietary options such as XArp.
Command prompt
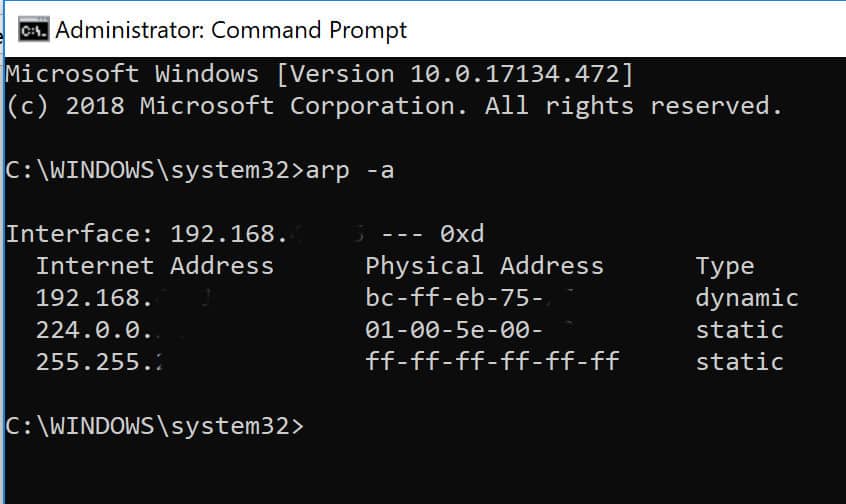
If you suspect you may be suffering from an ARP poisoning attack, you can check in Command Prompt. First, open Command Prompt as an administrator. The easiest way is to press the Windows key to open the start menu. Type in “cmd”, then press Crtl, Shift and Enter at the same time.
This will bring up Command Prompt, although you may have to click Yes to give the app permission to make changes. In the command line, enter:
arp -a
This will give you the ARP table:
*The addresses in the above image have been partially blacked out for privacy reasons.*
The table shows the IP addresses in the left column, and MAC addresses in the middle. If the table contains two different IP addresses that share the same MAC address, then you are probably undergoing an ARP poisoning attack.
As an example, let’s say that your ARP table contains a number of different addresses. When you scan through it, you may notice that two of the IP addresses have the same physical address. You might see something like this in your ARP table if you are actually being poisoned:
Internet Address Physical Address
192.168.0.1 00-17-31-dc-39-ab
192.168.0.105 40-d4-48-cr-29-b2
192.168.0.106 00-17-31-dc-39-ab
As you can see, both the first and the third MAC addresses match. This indicates that that the owner of the 192.168.0.106 IP address is most likely the attacker.
Other options
Wireshark can be used to detect ARP poisoning by analyzing the packets, although the steps are outside of the scope of this tutorial and probably best left to those who have experience with the program.
Commercial ARP-poisoning detectors such as XArp make the process easier. They can give you alerts when ARP poisoning begins, which means that attacks are detected earlier and damage can be minimized.
OS-specific options include the following:
- Windows: Agnitum Outpost Firewall, AntiARP, Colasoft Capsa, elmoCut, Panda Security, Snort, Winarpwatch, anti-arpspoof, NetCutDefender
- Linux: Antidote, Arp_Antidote, Arpalert, ArpON, ArpStar, Arpwatch, ArpwatchNG, remarp, Snort, NetSec Framework
- Mac: ArpGuard
How to prevent ARP poisoning
You can use several methods to prevent ARP poisoning, each with its own positives and negatives. These include static ARP entries, encryption, VPNs and packet sniffing.
Static ARP entries
This solution involves a lot of administrative overhead and is only recommended for smaller networks. It involves adding an ARP entry for every machine on a network into each individual computer.
Mapping the machines with sets of static IP and MAC addresses helps to prevent spoofing attacks, because the machines can ignore ARP replies. Unfortunately, this solution can only protect you from simpler attacks.
Encryption
Protocols such as HTTPS and SSH can also help to reduce the chances of a successful ARP poisoning attack. When traffic is encrypted, the attacker would have to go to the additional step of tricking the target’s browser into accepting an illegitimate certificate. However, any data transmitted outside of these protocols will still be vulnerable.
VPNs
A VPN can be a reasonable defense for individuals, but they are generally not suitable for larger organizations. If it is just a single person making a potentially dangerous connection, such as using public wifi at an airport, then a VPN will encrypt all of the data that travels between the client and the exit server. This helps to keep them safe, because an attacker will only be able to see the ciphertext.
It’s a less-feasible solution at the organizational level, because VPN connections would need to be in place between each computer and each server. Not only would this be complex to set up and maintain, but encrypting and decrypting on that scale would also hinder the network’s performance.
Packet filters
These filters analyze each packet that gets sent across a network. They can filter out and block malicious packets, as well as those whose IP addresses are suspicious. Packet filters can also tell if a packet claims to come from an internal network when it actually originates externally, helping to reduce the chances of an attack being successful.
Protecting your network from ARP poisoning
If you want your network to be secure from the threat of ARP poisoning, the best plan is a combination of the above-mentioned prevention and detection tools. The prevention methods tend to have flaws in certain situations, so even the most secure environment may find itself under attack.
If active detection tools are in place as well, then you will know about ARP poisoning as soon as it begins. As long as your network administrator is quick to act once alerted, you can generally shut down these attacks before much damage is done.
ARP attacks will inevitably become less frequent as IPv6 becomes dominant. As of September 2023 the global adoption rate was approximately 40% — up from approximately 30% in 2020. In IPv6, the function of ARP is carried out by the Neighbor Discovery Protocol (NDP).
NDP helps nodes discover their neighbors, configure their addresses, and determine the presence of routers for forwarding packets. NDP is more feature-rich than ARP, and it addresses several limitations of ARP that made it less suitable for IPv6.
Related post: How to prevent spoofing attacks
Image credit: Image design based on ARP Spoofing by 0x55534C under CC3.0


Perhaps if you typed arp -a (as shown in the screenshot) you might do better B-)
Thanks for pointing out the typo, Martin. It’s been fixed now.
Under “Static ARP entries” you state “this solution can only protect you from simpler attacks”, can you provide some examples of “non simple” attacks which can defeat static ARP entries? Thanks.
Using static entries will protect your system in most ways. However, it will still be susceptible to MAC spoofing, as well as the complications that arise from trying to manage too many devices.
Thanks for the reply, I appreciate it. I’ve done some research and it seems that defending against MAC spoofing is difficult if even possible. 802.1X appears to be a solution. If you have insight to the following I’d appreciate a reply. Is MITM even possible with MAC spoofing since both systems receive all communications? If both systems respond won’t that create network confusion leading to discovery? Other than volume of traffic, is there an advantage of MAC spoofing over just using promiscuous mode?