Two-factor authentication (2FA) refers to a login process that requires more than just a password. If your password is compromised somehow, the second form of verification required by 2FA can prevent attackers gaining unauthorized access to your account.
Two-step verification (2SV) and multi-factor authentication (MFA) are terms often used interchangeably with two-factor authentication, though there are some differences that we’ll get into later. You may encounter 2FA when logging into a device or account. Examples include:
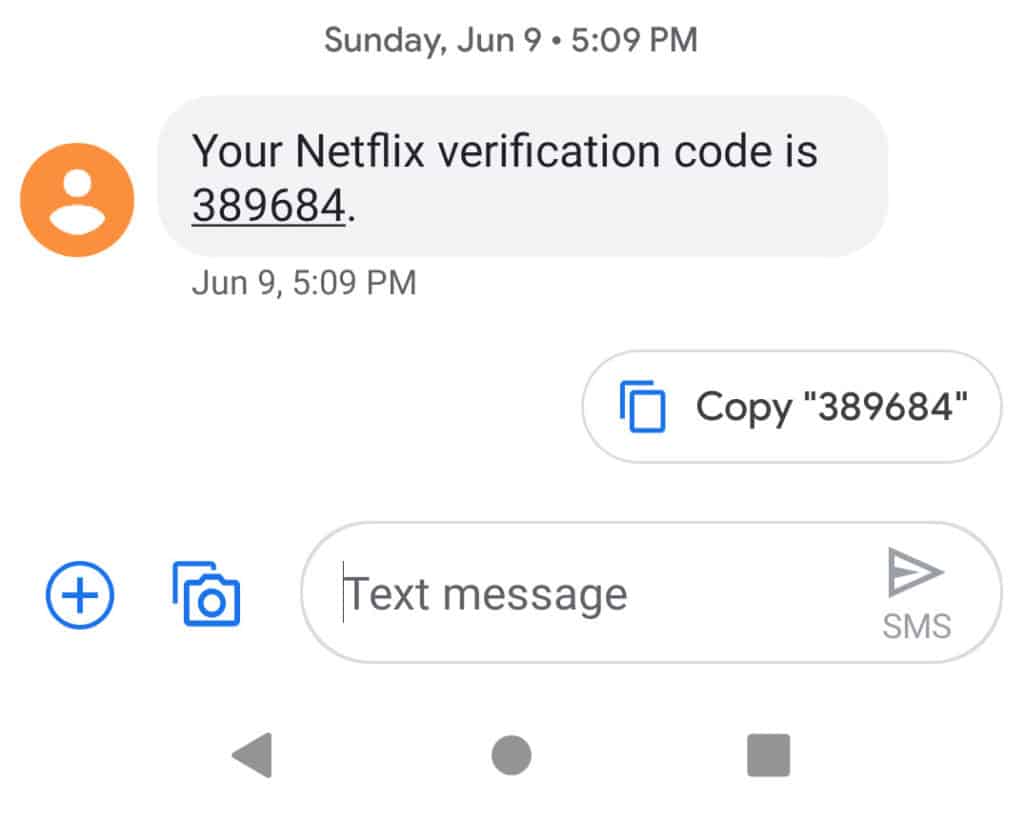
- A one-time PIN number sent via SMS, email, or an authentication app like Google Authenticator or Authy
- A hardware authentication device, such as a USB key, that must be inserted before logging in
- A biometric scan, such as a fingerprint or retina scan on a mobile device, in addition to a password
2FA can be set up for many online accounts, and we strongly recommend doing so. Typically, this involves entering a PIN number when logging in from a new device or location, or after your previous session has expired. It might seem like a burden, but the additional layer of security provided by 2FA goes a long way in protecting accounts from hackers.
How does two-factor authentication work in practice?
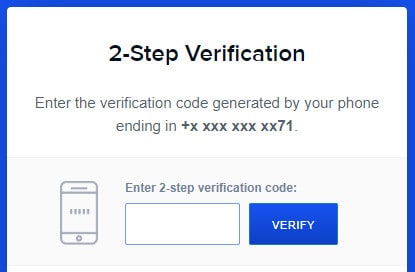
If 2FA is turned on for your account, you’re most likely to encounter it when logging in from a new device or from a different location. You’ll enter your username and password as usual, and then you’ll be required to prove your identity by entering a second form of verification that only you can provide.
Not all methods of verifying a user are equal. From most secure to least secure:
- A hardware authentication device such as a YubiKey or Titan Security Key. These are USB devices that you must plug in to your device in order to log in.
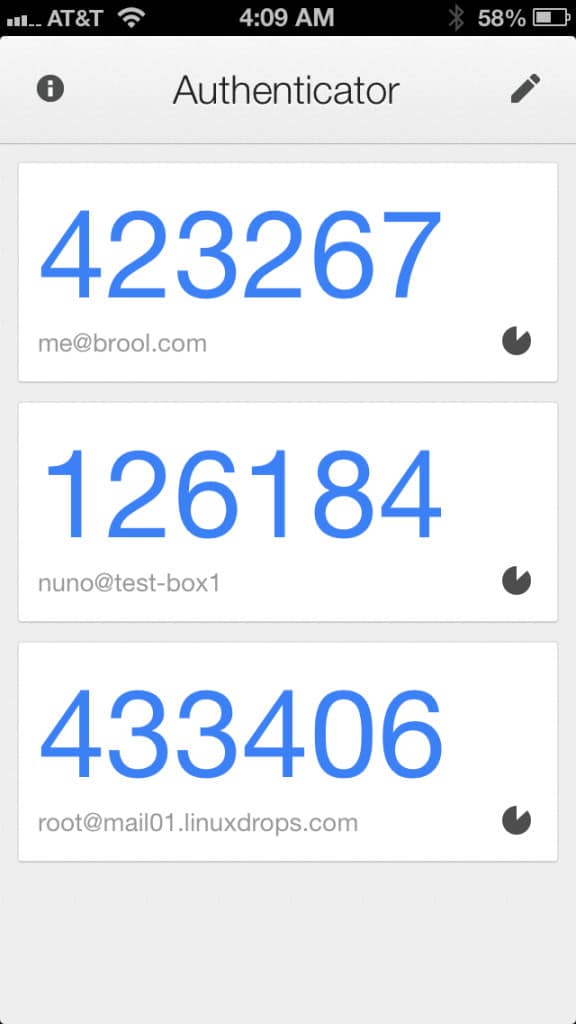
- An authentication app such as Google Authenticator or Authy. These apps generate temporary PIN numbers on your smartphone.
- A biometric scan such as a face, fingerprint, or retina scan. The security of biometric scans varies widely depending on the method used, the quality of the authentication software, and the hardware used for input.
- A PIN number sent via SMS to your phone. SMS is not encrypted and is vulnerable to SIM swap attacks, so this is considered less secure.
- A PIN number sent via email. This option is the least secure because email accounts can often be accessed from anywhere, as opposed to the other methods that require you to have a specific physical device present. Furthermore, email is not encrypted.
Even if your account supports 2FA, it might not be enabled by default. This is because there is an enrollment process required to set up 2FA for each site. Without that enrollment process, users would simply be locked out of their account. You’ll want to delve into the security or login settings of your account and hope to find 2FA settings.
SMS (text) message two-factor authentication
The advantages of using the SMS method is that it is nearly universal and is tied to your SIM card, not your phone. Almost all mobile phones accept text messages, even “dumb” phones that do not have apps installed on them. If you change phones, or your phone is damaged or lost, you can simply pop your SIM card into another phone and you’re good to go.
The main disadvantage is that in order for SMS messages to get through, you must be within cellular range. Also, global travellers can have problems with the SMS method if they change their SIM cards in different countries because each SIM card would have a different phone number.
A more advanced disadvantage to SMS 2FA is that it’s not terribly hard for bad guys to infiltrate the SMS system and intercept codes, or use social engineering to call your mobile provider and have your number assigned to their SIM card.
This type of nefariousness is usually reserved for people who are being deliberately targeted by an attacker rather than a normal run of the mill attack. There’s not much any security precaution can do for you if you’ve attracted the attention of sophisticated bad guys like that.
Two-factor authentication applications

There are a variety of 2FA apps on the market. The most popular is Google Authenticator, but competitors like Authy and LastPass also have 2FA apps. This type of product splintering does nothing to help the adoption of 2FA because companies have to spend time deciding which 2FA platform to use. Customers also have to be willing to install yet another 2FA app on their phones if a service uses a different 2FA platform than others.
The biggest pro to 2FA apps is that they do not need any type of internet or cellular connectivity to function. They simply display the necessary codes as needed. The down side to 2FA apps is that if you lose or damage your phone to the extent that you can’t get a code from it, you’re going to have a hard time getting in to your account.
Another small downside to 2FA apps is that each service needs to be set up individually. This normally means you just need to scan a QR barcode with the app but it can be more involved for some corporate implementations.
The best services offer both SMS and app 2FA, but those services are few and far between.
What is authentication, anyhow?
In order for you to gain access to something like your email, the email system has to be satisfied of two things. I’ve described them in more detail in the glossary at the end, but the high level view is this:
Authentication; sometimes abbreviated AuthN, means you are who you say you are.
Authorization; sometimes abbreviated AuthZ, means that you’re allowed to read your email.
What’s the difference between two-factor authentication and two-step verification?
Many computer science students and philosophers would debate this into the wee hours of the morning and while there is a subtle difference, in practice it’s not a very big one.
The main sticking point is that there is no concept of “verification” in authentication/authorization parlance. We have authentication and we have authorization. The introduction of the ambiguous term “verification” can lead to confusion over the difference between what someone knows and what someone has.
Further, what does verification mean? Does it mean that the person has been identified (AuthN) or does it mean the person is allowed to access some resource (AuthZ)? We have adequate words for those concepts already.
A secondary point of confusion stems from the distinction between what a person has, and what a person knows. At face value it’s easy to think that something like a biometric second-factor that uses a fingerprint constitutes something the user has (they have their fingerprint).
But, the use of fingerprints as a phone unlock mechanism has been debated in the US court system. Some judges feel that a fingerprint is implicit testimony and testimony is something someone knows, not something they have.
Both these concepts fall under the umbrella of multi-factor authentication (MFA) and both require you to have something else other than a password. It doesn’t matter whether that something else is a fingerprint, a one-time numeric sequence, or a Yubikey.
Why do we need something other than passwords?
Usernames are generally pretty easy to discover; in many cases it’s just our well-publicized email address or, in the case of forums, it’s the display name everyone can see. That means the only real protection you have against someone logging in as you is the strength of your password.
There are three main ways that bad guys get your password. The first is to simply guess it. You may think that has a very unlikely chance of success but sadly many people use terribly weak passwords. I see a lot of passwords in my daily work life and there are far too many Chucks in the world with the password chuck123.
The second way is to utilize a dictionary attack. The bulk of the remaining passwords for the billions of accounts in the world are comprised of a few thousand words. Bad guys run dictionary attacks against sites knowing that most of the accounts on that site will be using one of those common passwords.
The third way is to steal the data. Data breaches often expose passwords stored on company servers.
Sites and systems that employ 2FA require a second factor in addition to your password to log in. At face value, that may seem silly. If passwords are so easily compromised, how much value can simply adding a second password bring to the table? It’s a good question that the two-factor authentication method addresses.
In most cases 2FA takes the form of a numeric code that changes every minute or can only be used once. Therefore, someone who manages to get your password won’t be able to log into your account unless they’ve also managed to obtain your current 2FA code.
In this way, 2FA removes that human frailty of creating weak passwords and reusing them across services. It also protects against account data being stolen because even if the bad guy manages to steal all the usernames and passwords for a site, he still will not be able to log in to any of those accounts without that essential 2FA code for each user.
Why do I want to use two-factor authentication?

Consider that most password hacks happen over the internet. A dated, but usable, analogy is a bank robbery. Before the internet, robbing a bank was very difficult. You had to get a crew, case the bank to find the best time to rob it, obtain some weapons and disguises, and then actually carry out the robbery without getting caught.
Today, the same bank robber can sit across the world and try to brute force your web banking account without you even being aware. If he can’t get into your account, he just moves on to the next. There’s virtually no risk of getting caught and it requires almost no planning.
With the introduction of 2FA, that bank robber has virtually no chance of succeeding. Even if he were to correctly guess your password, he would have to hop on a plane, track you down, and steal your 2FA device to get in. Once a physical impediment is introduced to a login sequence, it becomes orders of magnitude harder for the bad guy to succeed.
2FA requires you to provide two things: something you know and something you have. The something you know is your password. The something you have is the numeric code. Since the numeric code changes so frequently, anyone being able to provide the correct code at any moment is almost assuredly in possession of the code generating device.
2FA is proving to be very resilient to brute force password attacks, which is good news. The bad news is the relatively slow adoption rate. Each individual service has to decide to implement 2FA – it’s not something you can decide for yourself to use on every site. While an ever-growing number of sites support 2FA now, many more do not. Surprisingly, very critical sites like banking and government sites have been slow to adopt 2FA.
Two-factor authentication in enterprise
2FA has a better adoption rate in corporations than in public services. Many companies that have remote workers have strongly implemented 2FA. The most common and mature 2FA mechanism for corporations is the RSA SecurID. It has been around for years and can be installed as an app, or provided as a hardware dongle much like a USB stick with a screen showing the code.
Another strong contender these days is Okta. Okta began focusing on Single Sign On (SSO) meaning users only had to log in once and could then access many third-party services. Many corporations use SSO heavily and now that Okta offers 2FA, it is becoming more popular.
Glossary
Authentication (AuthN): You are who you say you are. This is where your username and password comes into play. Anyone who presents both of those things is deemed to be you. However, just being authenticated doesn’t mean you will be allowed to read your email.
Authorization (AuthZ): Once you’ve been authenticated (the system knows who you are), it can then determine what you’re allowed to access. In the case of logging in to your email, there’s really just one thing you’re there to do. But, consider an office scenario where you’re able to read some shared network drives, but not others. It’s the AuthZ layer that determines what you’re allowed to do but it can’t do that until you’re probably authenticated.
Using 2FA is a very good security measure and you should consider enabling it everywhere you can. The 2FA Directory attempts to list the companies that support 2FA and provides an easy way to publicly shame companies that do not.
If a service you currently use does not support 2FA, you may be able to find an alternate service that does.
See also: Password strength checker, a fun way to check how good your password is (disclaimers apply!).