Report was sponsored by Anzenna – Understand employee risk using a real-time score. Prioritize and remediate to prevent breaches.
We can take all the precautions and preventive measures possible to minimize the risk of cybercrime impacting ourselves or our businesses. But at the end of the day, all it takes is simple human error to put everything in jeopardy. Whether it’s a link click, download, missed update, or misconfiguration, everyday mistakes can lead to big problems.
Individuals and businesses alike have suffered huge losses due to cybersecurity incidents including data breaches, ransomware attacks, system disruption, and more. And a surprisingly large number of these incidents could have been avoided had it not been for human error.
In this post, we examine the impact that people’s mistakes have on cybersecurity. We also provide some handy tips for trying to minimize the impact of human error on your individual cybersecurity as well as businesses’ bottom line.
Human error in cybersecurity
We’ve compiled the most interesting statistics, facts, and trends from recent studies to paint a picture of how human error is impacting the world of cybersecurity.
1. Almost half of US workers trust public wifi hotspots
Public wifi hotspots are notoriously unsecure. Hackers prey on unsuspecting users to steal information such as passwords, financial details, and other personal information. Really, no one should be connecting to a public network without connecting to a suitable VPN for public wifi first (to encrypt your internet traffic and keep it hidden from snoopers).
Even so, according to the Proofpoint 2020 User Risk Report, 45 percent of workers in the US believe that public wifi is safe when they are in a trusted location. Globally, we’re a bit more savvy, with 26 users worldwide trusting public hotspots.
2. 14 percent of workers in the UK don’t lock their smartphones
The Proofpoint report also found that more than one in 10 UK workers never lock their smartphones. This is in spite of the fact that 41 percent of workers admit to using their smartphone for both work and personal activities.
Globally, 42 percent of respondents use a biometric lock (for example, a fingerprint scan) and 24 percent use a four-digit PIN to unlock their device, but 10 percent have no lock on their device at all.
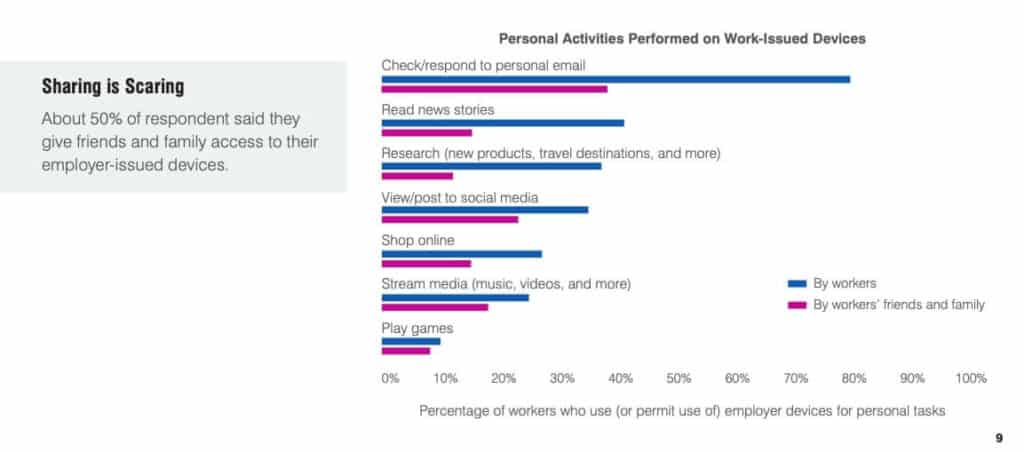
3. Half of workers share access to an employee-issued device with family and friends.
Proofpoint worryingly found that 50 percent of respondents admitted to allowing family or friends to use their work-issued device. While the motives behind this may be harmless (the most common reason is to check email), you just never know what someone might mistakenly click on.
4. Human error is a major cause of data breaches
What do Equifax, Capital One, and New Zealand’s gun buyback scheme have in common? They were all impacted by data breaches caused primarily by human error. According to testimony, the Equifax breach could have been avoided had an employee heeded security warnings and implemented the necessary software fixes.
But these are not anomalous cases. Egress’ Insider Data Breach Survey 2021 revealed that 94 percent of organizations have experienced insider data breaches in the last year, with human error being the top cause of serious incidents, according to 84 percent of IT leaders surveyed. Despite causing the most incidents, just over one-fifth (21 percent) of respondents said human error was their biggest concern.
Previous research backs up these findings. Kaspersky’s IT security economics in 2019 report tells us that “inappropriate IT resource use by employees” is the most common cause of a data breach, with 50 percent of SMBs reporting these types of incidents.
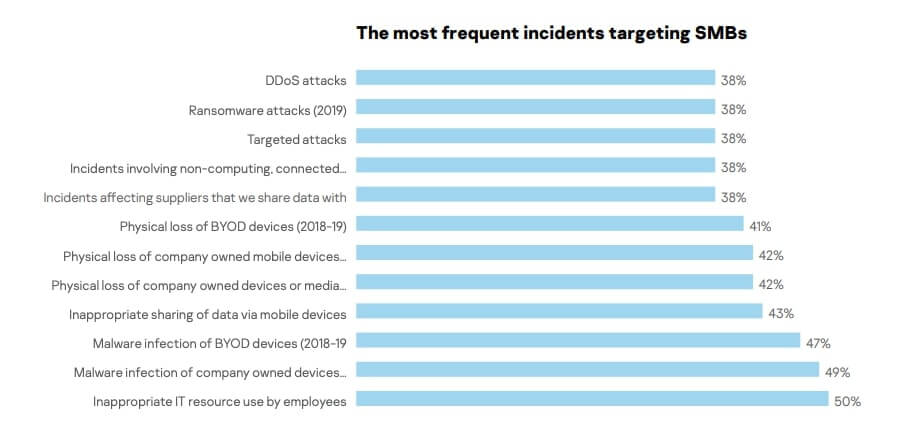
Other factors related to human error played a significant role too, including the loss of company-owned devices or media (42 percent), loss of company-owned mobile devices (42 percent), and loss of BYOD devices (41 percent).
5. Misdelivery and misconfiguration are among the top causes of data breaches
Verizon’s 2020 Data Breach Investigations Report further sheds light on the matter and analyzes the causes of data breaches in a slightly different manner. It found that phishing is the top threat action variety in breaches, playing a role in more than 20 percent of cases. Other human errors (misdelivery and misconfiguration) were in the fourth and fifth spots respectively, each representing the top threat action in around 10 percent of breaches.
In addition, the report found that some of the top malware vectors in data breaches are human error related. Email links, download by malware, and email attachments held the first, third, and fourth spots respectively.
When it comes to the high-level actions that cause data breaches, error is the only one that continues to increase in frequency.
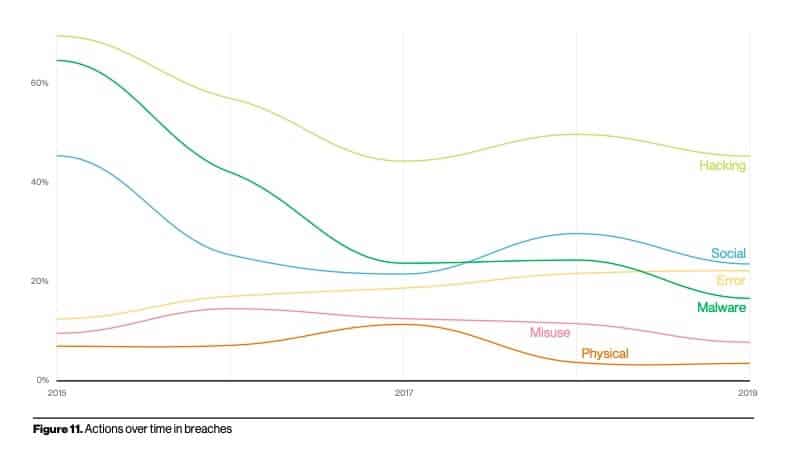
The top error varieties are misconfiguration, misdelivery, and publishing errors.
As Verizon points out:
…there is no getting away from the fact that people can, and frequently do, make mistakes and many of them probably work for you.
6. 58% of organizations report that employees ignore cybersecurity guidelines
One of the most alarming (but perhaps not all that surprising) findings of Netwrix 2020 Cyber Threats Report was that more than half of respondents said that employees ignored policies and guidelines surrounding cybersecurity.
It appears employees are simply modeling their executives though, as 85 percent of CISOs admitted to loosening cybersecurity measures so that employees could work remotely.
7. The pandemic appears to have had an impact on human error concerns
An interesting comparison in the Netwrix 2020 report shows figures for how critical threats were considered pre- and mid-pandemic. A huge increase was observed in “accidental and improper sharing of data by employees.” Pre-pandemic, 58 percent of organizations considered this a critical threat, but now that figure is 92 percent.
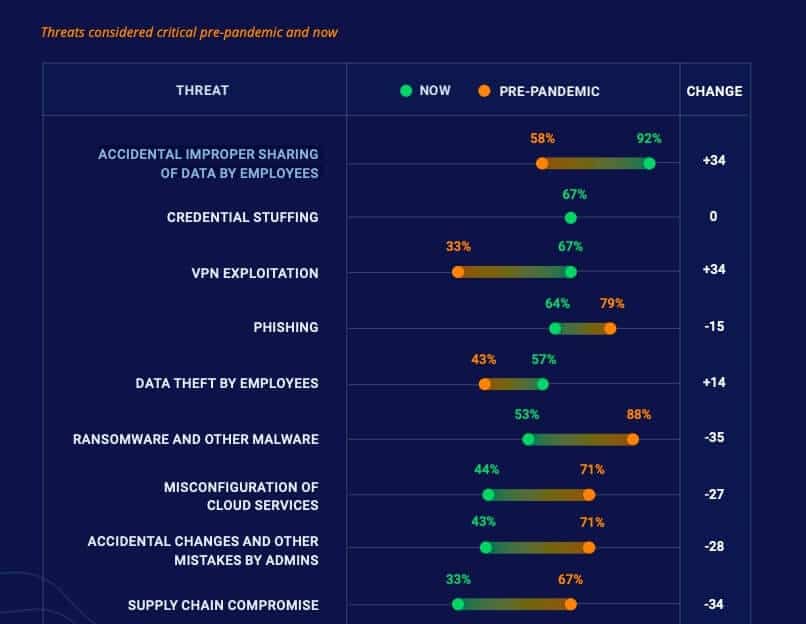
At the same time, other human error concerns have been alleviated to some extent. For example, critical concerns around “misconfiguration of cloud services” dropped from 71 percent to 44 percent, and “accidental changes and other mistakes by admins” saw a similar decline.
8. A worrying amount of people are guilty of using weak passwords
A 2021 report from NordPass, covering 50 countries, found that “123456” remains the most popular password for the second year running, with more than 103 million people using it for log-in purposes. This password would take less than a single second to crack. Other frequently used passwords include “123456789” (used by 46 million individuals), “qwerty” (22.3 million people), and “password” (20.9 million people).
This is particularly concerning given that in its 2020 Data Breach Investigations Report, Verizon found that of 868 hacking-related breaches, 80 percent involved passwords. Hackers either used lost or stolen credentials or brute force attacks (to guess passwords).
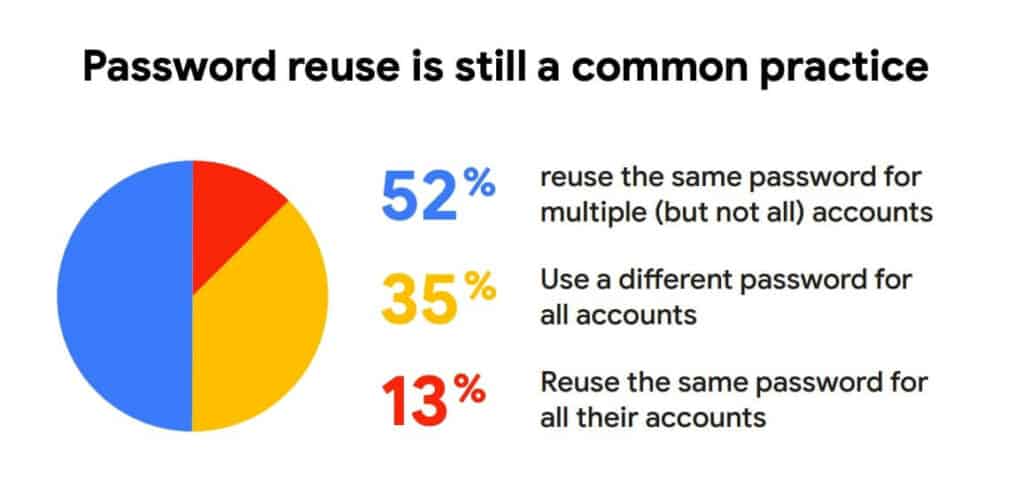
9. Password reuse is extremely common
With so many online accounts to deal with (HYPR says many of us manage more than 30 each), remembering all these passwords can be tough. As such, it’s no surprise that people tend to reuse passwords on multiple accounts. However, this can be a risky practice. If a set of credentials is compromised, for example, in a data breach, cybercriminals can use a tactic called credential stuffing to use that username and password combination to hack into other accounts.
There are lots of numbers floating around about the prevalence of password reuse, but the fact of the matter is that it’s far more common than it should be. Here is some data that shines a light on this issue which affects both personal and work accounts:
- Microsoft found that 44 million users were reusing passwords across accounts.
- Another Google survey discovered 13 percent of users utilized the same password for every account and an additional 52 percent used the same password on multiple accounts.
- 72 percent of respondents to the HYPR survey admitted to reusing passwords.
- LastPass discovered employees were happily reusing passwords on 13 different accounts.
- According to the Ponemon Institute’s The 2020 State of Password and Authentication Security Behaviors Report, IT professionals are the worst offenders, with 50 percent reusing passwords compared to 39 percent of other employees.
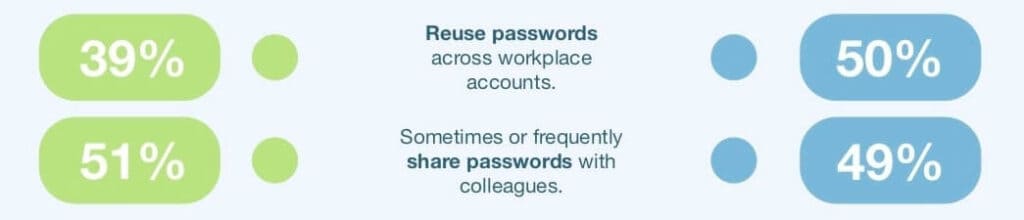
10. Password sharing is common too
A 2021 survey from The Zebra highlights that 79% of Americans share passwords but only 13% are worried about identity theft.
The Ponemon report adds more intrigue to these results as it splits up data from IT specialists and other individuals. It found that 49 percent of IT professionals admitted to sharing passwords with their colleagues. This is almost the same figure as for other employees (51 percent).
11. Only 45 percent would change their password after a breach
You would think that after being notified of a data breach, it’s common sense to change your password on any account that uses that set of credentials. But not so. Google found that only 45 percent said they would change their password after being notified of a data breach.
A concerning statistic in the Ponemon Institute survey was that only 65 percent of IT specialists would change their account protection methods after an account takeover. While this represents a majority, you would hope that the percentage would be greater. Indeed, the number for other individuals was quite a bit higher at 75 percent.
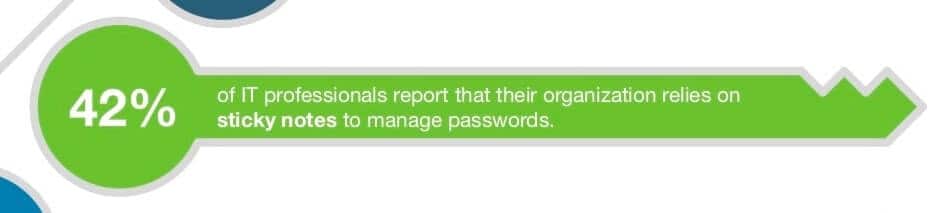
12. Almost half of organizations use sticky notes to help manage passwords
Ever walked into an office and observed a computer monitor surrounded by sticky notes bearing various passwords? It’s not an uncommon sight. Indeed, according to the Ponemon Institute, 42 percent of organizations rely on this practice to ensure employees can log into various accounts.
Related: 25+ Password statistics (that may change your password habits)
13. Human intelligence is the best weapon against phishing attacks
Some would argue that phishing attacks don’t fall under the category of human error, but the fact remains that phishing relies on user action (prompted by social engineering).
In its 2019 Annual Phishing Report (PDF), Cofense underscored the vital role of awareness training in preventing successful phishing attacks.
When perimeter technology fails, people must step up. Given the right conditioning, they will. They’ll unite to become a “Human Intrusion Detection System,” a set of sensors intuiting threats your controls miss. It’s human intelligence, not the artificial variety.
One example cited was that of a phishing scheme that targeted a major healthcare organization. While the phishing campaign was extremely sophisticated and bypassed controls, thanks to swift employee reporting, the attack was stopped in under 20 minutes.
Related: Phishing statistics and facts for 2019–2020
14. Spending on cyber security awareness training is increasing dramatically
Although it may be underestimated, the issue of human error in cybersecurity has not gone unnoticed. Businesses across the globe are ramping up efforts to improve employee knowledge to help prevent mistakes. The global market for cybersecurity awareness training was worth $1 billion in 2014, but the Gartner analyst Perry Carpenter estimates it will be worth $10 billion by 2027.
Data from 2020 Netwrix IT Trends Report: Reshaped Reality supports these spending figures, finding that one of the most important IT projects across organizations involves raising employee cybersecurity awareness. It was named a priority by more than half (52 percent) of organizations. What’s more, the percentage of mid-size organizations planning to invest in security awareness more than double compared to last year, increasing from 33 percent to 67 percent.
15. Remote Work and Cybersecurity Breaches
The rise of remote work during the pandemic introduced new vulnerabilities in cybersecurity. A report from Malwarebytes revealed that 20% of organizations experienced a security breach due to remote workers. This statistic underscores the human factor as a significant vulnerability in remote work environments. The shift to working from home often means using personal devices for work and operating in less secure IT environments. These factors create opportunities for cybercriminals to exploit security gaps. Addressing these risks requires organizations to implement stronger cybersecurity measures. These measures include comprehensive employee training, secure systems for remote access, and robust endpoint protection strategies.
16. Ransomware and Malware Attack Trends
Ransomware attacks have become a critical threat to cybersecurity. The average ransom demand has surged, with the payout increasing from $812,380 in 2022 to $1,542,333 in 2023, according to SC Magazine. This significant increase indicates the growing severity and sophistication of ransomware attacks. Moreover, Varonis highlights that 94% of malware is delivered via email, emphasizing the need for heightened email security. To combat new ransomware tactics, organizations must adopt dynamic cybersecurity strategies. These include regular data backups, advanced threat detection systems, and extensive security training for employees to recognize and respond to potential threats.
What can be done to mitigate the risk of human error?
As we can see, human error is a huge liability. That said, there are measures you can take to minimize the impact that people’s mistakes have on your organization’s cybersecurity. Below are some avenues to consider. Note that while these focus on a business environment, many of these measures can be applied at home too.
1. Have more controls in place
There are a ton of ways to implement controls in your organization to help boost cybersecurity. For example, using the principle of least privilege, you can limit the data and functionality each employee can access. This lowers the chance that information will be lost or fall into the wrong hands.
Access control can also be used to mitigate the risks of errors such as misdelivery or misconfiguration. For instance, requiring an extra set of eyes on certain tasks means that more than one person would have to make the same error for it to go unnoticed.
2. Improved password practices
Password practices can be improved with controls, too. For example, you can force regular password changes and stipulate that passwords abide by a set of rules about length and composition. You may find our password strength checker and strong password generator tool helpful for this.
In a similar vein, you can mandate or encourage the use of a password manager for all work-related accounts. You can also set up platforms to require 2FA or 2SV. This means that even if weak passwords are being used or people are sharing passwords, another layer of protection is in place.
Another way to make life easier for employees is to implement a Single Sign-On (SSO) system where one password is used to access multiple accounts.
3. Utilize cybersecurity awareness training
As mentioned, phishing attacks require human action to be successful. But it’s also human action that can nip these attacks in the bud. A major deciding factor in which way things will go is simple: knowledge. Most cybersecurity awareness training programs focus on teaching employees how to spot, avoid, and report phishing attacks, so your organization can be ready when the inevitable attacks hit.
Training programs also help with other areas involving human error including password management, spotting malware, data handling, and physical security.
4. Filter incoming emails
Of course, it’s easier for employees to avoid phishing attacks if there are fewer opportunities for them to slip up. One simple way to limit the risk of phishing emails is to flag messages from outside the company. You can even remove links from external emails and sandbox attachments to confirm they are safe.
5. Ensure devices are locked
Whether employees are using company-issued devices or you have a Bring Your Own Device (BYOD) policy, you can stipulate rules to abide by. For example, a simple measure is to require that all devices are locked with a PIN, passphrase, biometric lock, or similar.
6. Encourage the use of other security apps
You can also require the use of a VPN, in particular when connecting to public wifi hotspots. This will ensure that all internet traffic is encrypted and unreadable if intercepted. You may even want to mandate or encourage the use of apps that can help find lost or stolen devices (such as the Google Find My Device tool or Apple Find My app) and remotely wipe devices.
7. Use mobile device management platforms
You might want to go a step further and utilize Mobile Device Management (MDM) or Mobile Application Management (MAM) platforms. These tools can perform a variety of tasks, including forcing data encryption, running malware scans, wiping data, and tracking devices.
8. Create an environment that helps prevent human error
We all know how environmental factors can affect our concentration and focus. And it’s not a stretch to say that our surroundings can have an impact on the number of mistakes we make. Ensuring staff are working in an organized and relatively quiet environment that’s not too hot, cold, or humid could go a long way in helping reduce errors.
Other factors to consider include tiredness (perhaps due to long shifts), excess workload, privacy, and even posture.
9. Improve the culture around cybersecurity
It’s all too easy to have a lackadaisical attitude toward cybersecurity… until it’s too late. If your organization has a purely reactive approach to information security, there needs to be a culture shift. Taking some of the above steps can certainly help. In addition, you can implement initiatives to remind workers about security actions and policies, for example, via posters or emails.
You should also encourage discussion around cybersecurity and ensure that employees know where to direct any questions they may have. Bear in mind that culture changes often trickle down from the top, so higher-level employees, in particular those in the IT department, need to set a good example.
FAQs about the role of human error in cybersecurity
What are some common causes of human error in cybersecurity?
Cybersecurity mistakes happen to the best of us, and there are plenty of reasons why. Let’s take a look at some of the most common culprits:
- The clueless factor: Believe it or not, many people are still in the dark when it comes to online safety. They may not know the basics of cybersecurity or how to avoid common pitfalls.
- The oops factor: Sometimes, people just make silly mistakes. They might use a weak password, leave their computer unlocked, or click on a shady link by mistake.
- The phisherman: Phishing scams are like the chameleons of the online world. They can look like legitimate emails, websites, or messages, but they’re actually traps designed to steal your personal information.
- The software snafu: Even the best software can have vulnerabilities, and when employees fail to update their programs or keep them properly patched, they’re basically rolling out the red carpet for cyber attackers.
- The techno-tangle: Let’s face it, technology can be confusing. It’s easy to get lost in the labyrinth of programs, files, and settings. Sometimes, it’s just a matter of accidentally hitting the wrong button or deleting the wrong file.
- The burnout blues: When people are overworked or have too much on their plate, they may be more prone to making cybersecurity mistakes. Focusing on security protocols is hard when you’re drowning in a sea of emails and deadlines.
But don’t despair! You can do plenty of things to prevent human error in cybersecurity. This includes regular training, implementing strong security policies and procedures, and using tools like firewalls and antivirus software. Remember, when it comes to online safety, prevention is the best medicine.
How common is human error in cybersecurity?
Well, it’s no secret that we humans are far from perfect, especially when it comes to cybersecurity. In fact, it’s safe to say that we’re the weakest link in the chain. Don’t get us wrong – we’re amazing creatures with unparalleled problem-solving skills and creativity. But we tend to drop the ball when it comes to staying safe online.
The numbers don’t lie – over 90% of cyber attacks involve some kind of human error. That’s right. We’re talking about mistakes we make daily, like clicking on a bad link or using a weak password. It’s like leaving the front door of your house wide open and inviting burglars in for a cup of tea. Except in this case, the burglars are cybercriminals, and they’re not interested in tea.
But before you throw your hands up in despair, know that there are things you can do to reduce the risk of human error in cybersecurity. Education is key – teach yourself and your employees about the risks of online activity and how to avoid them. Use strong, unique passwords and enable two-factor authentication. Keep software up-to-date and use firewalls and antivirus software. And most importantly, use common sense – if something seems too good to be true or suspicious, it probably is.
So yes, human error is common in cybersecurity. But with the right tools and knowledge, you can be a cybersecurity superhero and protect yourself and your organization from cyber threats.


