At some point in time, if you’ve used a computer or a piece of software long enough, you’ve probably seen several messages pop up asking you to install security updates. Far too often, many consumers ignore these critical security updates pushed out either by application developers or operating system companies like Microsoft or Apple. Finding information on security updates, including how to properly install them, can also be time-consuming. To help readers save time, we’ve gathered information on how to manage updates on all major computer and mobile operating system, as well as a handful of important, integrated applications.
It’s understandable why you might try to ignore these updates, especially for your operating system. On occasion, they require you to stop what you’re doing on your computer and can cause significant work disruptions as your computer is unusable for fifteen, twenty, or even thirty minutes at a time (or more, depending on how many updates you’ve ignored). For enterprises, especially, this kind of work disruption on a large scale is extremely expensive, even when the update is free.
However, those security updates that software companies push out to you are not inconsequential. What’s happening is that these companies, through one means or another, are locating security flaws in their software that could allow hackers to compromise the software or even your entire computer system using malware or other means. Ultimately, they may steal your data, destroy your data, or completely shut down the affected program or operating system. Security updates may feel like a hassle, but they’re usually here to help keep your computer more secure.
How to install security updates and software updates for operating systems
Unfortunately, there’s no “one way” to perform security updates. How a software developer chooses to make updates available will change, depending on which developer or company made the software. However, there are some ways to help cover a larger number of applications and operating systems quickly, including allowing many applications to automatically install those updates for you.
Windows Security and Software Updates
Service Packs
Microsoft rolls out updates to their operating systems using a few methods. One known method the company uses is through what they call Service Packs. The company explains that a Service Pack “is a Windows update, often combining previously released updates, that helps make Windows more reliable.”
The “reliability” Microsoft mentions here is quite often the patching of security flaws, although a Service Pack will contain a large number of different fixes for issues beyond just security problems.
You can download Service Packs for Windows manually or automatically through your operating system settings. The process for this will be slightly different, depending on which version of the Windows operating system you’re using.
Keep in mind that Service Packs are not delivered on a regular basis, and many of Microsoft’s operating systems only receive one or two Service Packs during their support cycle. Do not rely on Service Packs to receive regular security updates.
To manually install Microsoft Service Packs, do the following:
- Go to the Microsoft Download Center
- Type in “Windows [insert OS number] service packs” (for example, Windows 7)
- Locate the newest Service Pack for your operating system
- Click to download the Service Pack for your specific operating system.
To automatically install Microsoft Service Packs and other updates, do the following:
Windows 10: All Windows Updates in Windows 10 are automatic. They cannot be turned off.
However, Microsoft now allows you to ignore them or delay them if you wish, but you can’t completely shut them off. Once you restart your computer, you’ll be forced to install the update. You can also check for new updates manually before they go active on the schedule by using this method:
- Click on the Windows button on the left and open Settings
- Click on Update and Security
- Go to Windows Update
- Click on Check for Updates
Windows 8.1: You can turn automatic updates on in Windows 8.1 by doing the following:
- Point your mouse to the lower-left corner of your screen and move it upward to open the Settings menu
- Select Change PC Settings
- Click on Update and Recovery
- Click on Windows Update. You can check for updates manually here by clicking on Check Now
- Click on Choose How Updates Get Installed
- Under the Important Updates section, enable Install Updates Automatically
- Under Recommended Updates, select the box for Give Me Recommended Updates The Same Way I Receive Important Updates
- Under Microsoft Update, select the box for Give Me Updates for Other Microsoft Products When I Update Windows and then select Apply.
Windows 7: You can turn on automatic updates in Windows 7 by doing the following:
- Click on the Start button
- When you see the search box, type in Update. You will receive a list of results, from which you should select Windows Update
- On the left, click on Change Settings. Under Important Updates, select Install updates automatically
- Finally, under Recommended Updates, select Give Me Recommended Updates the Same Way I Receive Important Updates and click OK
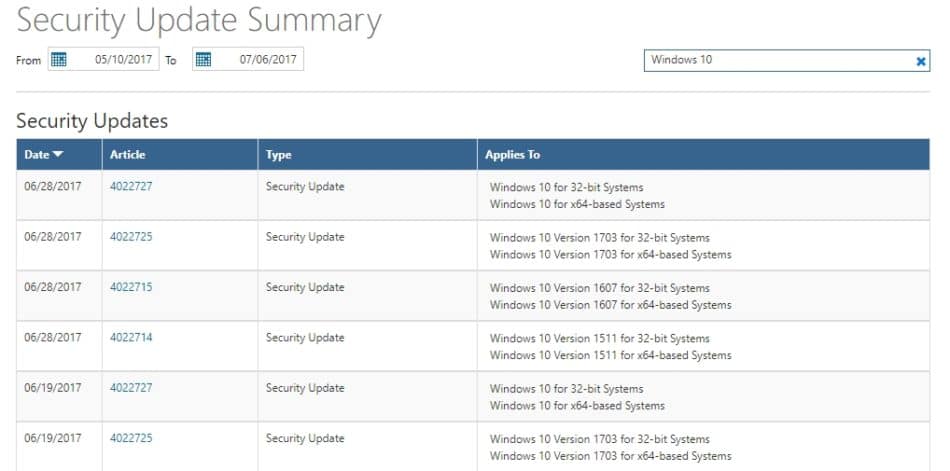
Manual security-specific updates
To manually install Windows security-specific updates, click here to go to Microsoft’s Security TechCenter. You’ll find a list of recent security updates Microsoft has pushed out, organized by date. You can search for security updates for your specific system by clicking on the right-hand search box and typing in the appropriate operating system.
Automatic updates for Windows Store apps
Windows 10 and 8.1 users can choose to have apps automatically update if they were installed through the Windows Store.
For Windows 10, do the following:
- From your Start screen, click on the Store icon to open the Windows Store
- Click on the Account Menu (usually your personal Windows icon or picture beside the search box) and click on Settings
- Look under App Updates and enable the Update Apps Automatically option
For Windows 8.1, do the following:
- Locate and click on the Store icon from the Start screen to open up the Windows Store
- Swipe right from the right edge of the screen and tap Settings, or if using a mouse, point to the lower-right corner of the screen and move the pointer upward
- Select App Updates
- Make sure Automatically Update My Apps is set to Yes
Install the latest version of Windows
If you’re currently using an older version of Windows, it may be wise to update to the latest version. Microsoft offered a free upgrade from Windows 7 or 8 to Windows 10 up to July 29, 2016. Those looking to upgrade now will not get the free upgrade option.
You can purchase and download the either the full version of Microsoft Windows 10 or by purchasing a device that has Windows 10 already installed.
If you have Windows 8, an easy method to upgrade to Windows 10 is by going to the Windows Store and typing in Windows 10 to get an upgrade option. Windows 7 may be able to install this upgrade through the Microsoft update notifications.
Note: ZDNet suggests that you may still be able to receive a free Windows 10 upgrade. Click here to read more.
Mac OS and app security and software updates
As with Windows, Mac users can adjust some of their security and software update settings. Apple makes this process a bit simpler than Windows, however. You can set your Mac to automatically install updates to your operating system and any applications you downloaded through the App Store, or simply go app by app and download those updates yourself. If you don’t have the App Store installed on your Mac, you can still check for OS security updates from your system settings.
You can only update any apps on your system using the Apple ID that was used to purchase the app.
To manually install updates on your Mac from your App Store, do the following:
- First, check your App Store icon. It will indicate a number on the side of the icon that represents the number of updates currently available for download
- Open your App Store
- Click on Updates
- Individually click on any apps you want to update, or click on Update All
When updating Mac OS X specifically, you can click the More link for the update and see if there are updates for specific Mac applications and components, such as Safari or iTunes.
However, Apple installs required security updates automatically. If you want to turn off automatic security updates, do the following:
- Click on the Apple menu and then go to System Preferences
- Click on App Store and then deselect the Install System Data Files and Security Updates option.
- You may also want to deselect the Automatically Check for Updates option and the Download Newly Available Updates in the Background option to completely disable all aspects of automatic updates
Please note, disabling automatic security updates is not recommended.
Additionally, the following issues may be relevant to your update process:
- If you’re using a personal hotspot, large automatic downloads are disabled
- If you’re using a business or school network, you may not have access to Apple’s software update servers, in which case you may need to install the updates manually
Don’t see an update you expected? Try this:
- After installing any available updates, look to see if you still have any updates available. At times, some updates only appear after you’ve already installed other updates
- Click on the Search box and type in the app name you want to update to see if it was missed
- Select the Purchased option and check to see which apps you already purchased. There’s a chance you may be on the wrong Apple ID, or that you downloaded the app from a location other than the App Store
- OS X Snow Leopard and OS X Lion users can find updates to the operating system by going to Software Update from the Apple menu, and app updates from the Mac App Store
Android OS and app security and software updates
Android users can turn app updates on or off through the Google Play Store settings. However, you cannot set the operating system to automatically install software updates. Android will push out notifications when an update is ready for the operating system.
You can also check for updates manually. If your device is not receiving updates, it may be because the device maker has chosen not deliver updates to your device.
Although Google makes system updates available, some device makers, such as Samsung and LG, only provide the updates to newer devices. It is important to update Android when possible, as Android ranked at #1 on the CVE vulnerabilities list for 2016 and #6 for “All Time Leaders.”
To adjust automatic updates for apps, do the following:
- Open your Play Store app
- Tap on on the Menu icon (the three lines by the search bar)
- Tap on Settings
- Tap on Auto-update Apps
- Choose your desired update option, either Do Not Auto-Update Apps, Auto Update Apps at Any Time, or Auto-Update Apps Over Wi-Fi Only.
When apps are auto-updating, you’ll see a download notification appear on the top of your screen.
To install or check for operating system and security updates, do the following:
- Go to your device settings
- Locate and tap on About Phone
- Tap on Update Center
- Tap on System Updates
- Here, you will see the last time your Android device checked for updates. You can also click on Check for Update at the bottom
Note: Android operating systems will vary in how the UI and settings menus are set up. Your menu layout for this process may look different, depending on which mobile device you are using and which version of Android you have. However, this process should help guide you to the right location for most Android versions for most mobile devices.
Additionally, note that if you installed any Android apps from outside of Google Play, such as through a sideload or due to activating the Unknown Sources developer option, your apps will not automatically update. You will need to update those apps manually by downloading the latest version to overwrite the current version on your device.
You can also determine how recently your security was patched under Settings > General > About Phone > Software Info. Look at the date under Android Security Patch Level. If the date looks like it may be a bit old, check with your device maker to see if a patch is available. Google releases security bulletins monthly, and your device may or may not be among those receiving security updates.
How to install to latest Android version
Android is not an easy operating system to work with if you’re trying to upgrade to a new version. Unfortunately, upgrading to a newer version is at times not possible. Whether you can or cannot upgrade to a new version depends on whether your phone provider decides to roll out a new version for your phone model.
Outside of hoping your device maker and service provider offer a new version for your specific device, your only other option is to install a newer version after rooting your phone, which can be complex and may void your phone’s warranty, alongside causing compatibility issues for your mobile device.
Apple iOS and mobile apps security and software updates
Apple makes it simple to update your iOS apps and software easily, either using a wireless connection or through a wired connection on a computer.
To update your iOS software, do the following:
- Make sure your device is connected to Wi-Fi with a working internet connection
- Tap on Settings
- Select General
- Go to Software Update
- You will see Download and Install. You may see a message that iOS needs to temporarily delete apps. Either click Continue or Cancel. Your apps will be reinstalled after the installation process, so it may be a good idea to hit Continue if you’re unsure
- Tap Install to start the process.
- If you want to delay the installation, choose Install Tonight or Remind Me Later
To update your iOS apps, do the following:
- Go to your Settings
- Tap [your name]
- Tap the iTunes & App Store option
- Tap to turn on Updates if the option is off (grayed out bar)
To manually update any app, you can go to its page directly in the App Store to check for updates.
You can also check out the Apple Security Updates page to see if any of your devices have received recent updates.
How to install the latest iOS version
Installing the newest version of iOS follows the same process as with security updates.
To check for a new version on your iPhone or iPad, go to:=
- Settings
- General
- Software update
If you see a red number next to “Software update,” it means there is an update available for your device. If you do not see one, there is no update currently available. Click here to check on the current version of iOS.
Linux security and software updates

Linux is a bit more complicated, as updating the system depends on which distribution you’re using.
(This guide assumes you are a regular Linux user).
To install security updates on Debian, you’ll need to use the following command:
$ sudo apt-get install unattended-upgrades
You can also use the following command to install security updates:
$ sudo unattended-upgrades
To receive logs of the update process, use the following command:
$ sudo unattended-upgrades -d
To install security and software updates on Ubuntu, we recommend checking out this detailed guide.
You can check for individual updates for Debian here.
You can check for individual updates for Ubuntu here.
How to install the latest Linux version (Debian and Ubuntu)
You can easily install a newer version of Linux directly on the distribution pages, or through the operating system.
Ubuntu users can update to the latest version using the Software Updater application. Click here for a how-to guide upgrading to the latest version of Ubuntu.
Considering Debian is a bit less user-friendly for newcomers, upgrading is a bit more difficult. Click here to access a how-to from Debian on keeping the OS updated.
Related post: Best Linux Patch Managers
Fake security updates and how to avoid them
Not all security update warnings you receive are going to be real. At times, you may see such messages and click on them, only to find nothing happens or that it opens a suspicious web page or tries to download a file blocked by your antivirus software or filters.
Given how common software security updates actually are, it’s not uncommon for fake update warnings to appear. Here are a few tips to avoid fake security updates:
- Turn on automatic updates. This is the simplest method to avoid getting notifications requesting you to manually update. In general, you’ll receive a message notifying you when the update has already occurred.
- Never accept a security update that comes from a web page popup. Security updates should come directly from the software or operating system you’re using.
- Check for spelling errors. While the occasional spelling or grammar mistake may slip through the cracks even for the best software companies, such mistakes are rare. In particular, look for misspellings in the software name, or unusual differences in the company or software logo.
- Research how your software actually provides updates. Some programs, such as Firefox, do not provide update notifications and instead provide those updates in the background. If you’ve been using an application for a long time and receive an update notification where one has never existed, be cautious and check for an update through that software’s official updating method or settings
Avoid unstable updates
At times, the software you’re using may offer you the opportunity to use pre-release versions of that software. For example, Microsoft offers an Insider Program for pro users and testers that allow users to install unreleased versions of the software.
By their nature, such releases, whether they are alphas, betas, nightlies, or previews, are going to have more flaws and more vulnerabilities to them.
No reputable software company or developer will automatically update your software to an unstable or pre-release version. These versions are only installed manually.
If you do decide to install a pre-release version of a program, you assume the risks inherent in using a program version that has not been widely used or tested en masse.
What if I have a choice between a newer beta and an older “stable” version?
If you’re offered either a newer beta version of an application or an older “stable” version, go for the stable version if you’re intending to use the program for general use purposes. Although it’s older and may have fewer features, it may also offer fewer vulnerabilities. Beta testing software can be fun but does come with some risks. If possible, use a separate machine for beta testing new software, and utilize the older, stable version on your general use machine.
Security and software updates for common software and other applications
Many popular applications do not receive automatic updates, leaving those programs highly vulnerable. In most cases, individual software programs that utilize an internet connection will provide push notifications when an update is available, but may not force the upgrade. It is often up to the user to check for and install these updates.
The following popular programs are known to have a large user base and are frequently targets for hackers due to their common use in most operating systems.
Adobe software (Flash, Shockwave, Acrobat, and more)

Adobe is an undisputed leader in dependency software applications. Programs such as Flash Player and Shockwave, for example, are a common target for hackers due to their significant integration for various forms of computer and web browser media.
Related: What makes Flash so insecure and what are the alternatives?
Hackers that take advantage of Adobe’s applications can easily steal valuable data or infect a computer with malware. Adobe’s programs rank highly on the CVE vulnerabilities list, at #4 (Flash Player), numbers 7-9 (Acrobat versions), and #12 (Reader) among other places.
To find the latest updates for Adobe software, do the following:
- Go to Adobe’s Security Bulletins and Advisories page
- Scroll down to the Bulletins and Advisories by Product section
- Locate the specific Adobe software you want to update and click on its name
- Check to see if any new updates have been posted. Install any new updates you find
You can also set many Adobe programs to install updates automatically.
- Click here to learn how to setup automatic updates for Acrobat and Reader
- Click here to learn how to setup automatic updates for Flash Player
- Click here to learn how to adjust Creative Cloud auto-updates
Google Chrome security and software updates
Google Chrome ranks #13 on the CVE vulnerabilities list. The web browser is regularly updated. To install updates in Chrome, you can click on menu button (three horizontal dots on the right side of the window) to check for updates. If there are new updates, the menu button dots will either be:
- Green, for 2-day-old updates
- Orange, for 4-day old updates
- Red, for updates that are 7 days old or older
To install any updates, click on Update Google Chrome. If you do not see this option after clicking on the menu dots button, you are currently on the latest version.
Firefox security and software updates
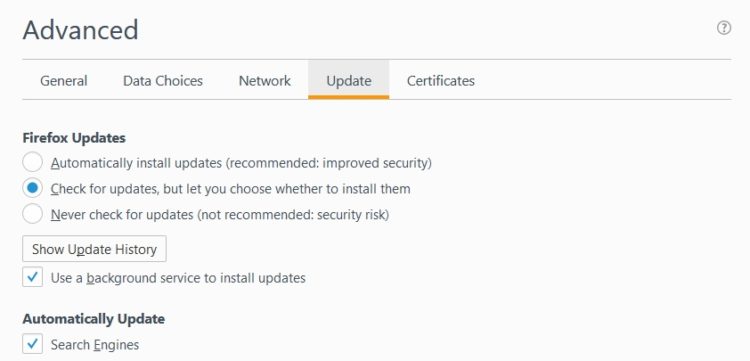
Firefox ranks at #21 on the CVE vulnerabilities list. You’ll find that Firefox is set to automatically install security updates. However, you can adjust these settings by doing the following:
- Click on the Menu (three lines on the top right) button
- Click on Options
- Click on Advanced
- Click on Update
- Select Automatically Install Updates if it is not already selected. If you do not want automatic updates, select either Check for Updates, But Let You Choose Whether to Install Them or Never Check for Updates (not recommended)
OpenSUSE security and software updates
OpenSUSE users should ensure they are installing updates as they come, as this application is often a target with many vulnerabilities. OpenSUSE ranks #6 on the CVE vulnerabilities list, making it one program users should update when those updates are available.
Click here to learn how to install updates for openSUSE, including how to use the GNOME Update Applet and setup automatic updates for new software patches.
PHP security updates
PHP ranks at #30 on the CVE vulnerabilities list. This application is a common factor for security threats but is not treated the same when it comes to security updates.
Click here to access the PHP website section on security to learn more about PHP security.
Data backup remains the best defense
There’s really no two ways about it here. Cyber security defense methods are advancing, but so too are the tools and methods cyber criminals are using to hack systems and steal or destroy data. With ransomware increasingly the most popular modus operandi for cyber criminal groups, both large businesses and individual users are increasingly likely to find themselves on the receiving end of a nasty piece of malware. The potential for losing valuable data is increasingly more than just a serious concern. It’s become a situation of “when” not “if.”
Related: What is disaster recovery and how do you plan for it?
Effective data backup has become an essential tool to ensure continuity for businesses as well as to ensure regular consumers don’t lose their valuable data and files. Both small businesses and average computer users, especially, need to consider the necessity of these options as well.
According to Small Business Trends, SMBs are a significant target for cyber criminals, accounting for 43% of all attacks against businesses. Additionally, SMB’s should note the following, additional cyber security-related stats:
- As many as 60% of small businesses are forced to close within six months of an attack (a stat some have, understandably, questioned)
- 48% of attacks are due to malicious intent
- Only 14% of SMBs are very confident in their ability to mitigate security risks
Related: Every business can plan to prevent ransomware, here’s how
Keep in mind that it wasn’t only SMBs that lost valuable data due to WannaCry and Petya. Many larger organizations, public service businesses, and individual consumers were heavily impacted, including important services such as hospitals and utilities. Data loss is extremely expensive and, once gone from your machine, it’s often gone for good.
Data backup ensures that your data can survive even after a ransomware attack or any other type of loss event. Whether it’s a fire or a virus more malicious than Peyta, data backup helps ensure that your business can be back up and running.
A simple data rule of thumb: Any data not backed up is data you’re willing to lose.
Read more: Data loss and disaster recovery statistics
Are security updates necessary?
The simple answer to this is “yes!” Two of the most recent and glaring examples we have of what can happen when users ignore security updates came with the WannaCry ransomware and the Petya virus attacks. The WannaCry ransomware attack, which ultimately infected over 400,000 machines and networks worldwide in the span of a few weeks, utilized a security flaw in the Microsoft Windows operating system. The Windows exploit was originally taken advantage of by the National Security Agency for their covert cyber warfare operations.
The Petya virus attack followed the WannaCry ransomware by about a month, utilized the same security flaw and stolen NSA tool, and infected even more computers along the way. Perhaps more disturbingly, the Peyta virus was not designed to grift money from infected computers. Security researchers soon found that, whether purposeful or because of poor design, the virus functioned by completely wiping a computer’s hard drive. Despite demanding $300 in a fashion similar to ransomware, it was discovered that the Petya virus lacked the function to unlock files or to even receive ransom payments.
In fact, one West Virginia hospital had to scrap all of their networked computers after getting infected by the Petya virus. This was after the hospital’s administrators attempted to not only recover files but also attempted to pay the ransom, finding that reports on the virus were correct: there was no way to pay the ransom, even if they wanted to.
When the NSA had their hacking tool stolen and then published online by a hacking group, the cyber criminals behind the WannaCry ransomware and those behind the Petya virus utilized the tool to their advantage. Other ransomware programs using the tool are also likely to crop up.
To be clear, Microsoft had already patched the vulnerability a month before the WannaCry virus was released into the wild. That security update was freely available; many users simply chose to ignore it. However, the difficulties in rolling out a such an update was also a potential headache for many large businesses and government organizations, which may also be why many chose to put off the update.
According to Kaspersky, the majority of the infected computers were running the outdated Microsoft Windows 7 operating system, which is currently the most common version of Windows. Windows 8 and 10 computers were not vulnerable to the attack, while most Microsoft Server operating systems were also not heavily impacted.
Petya equally targeted the same vulnerability, and therefore also impacted the same computers that were targeted by WannaCry.
The situation revealed several reasons why security updates are necessary.
Security updates are more important for users of outdated software
If you have failed to upgrade a software program to the latest available version, you should be taking any security updates you can get. One of the key benefits to upgrading to a newer software version, be it an application or an operating system, is the fact that the developers spend a lot of time fixing security flaws that existed in the previous version(s). The older the version you’re using, the more security flaws that likely exist.
Additionally, while some limited support will exist for older versions, the more versions behind you are from the newest version available, the less likely it is that version you’re using is still getting regular updates and security fixes.
Many users mistakenly assume that newer software versions are more vulnerable to security flaws. However, this is typically not the case. Newer software versions build on the previous version, fixing errors that existed in older versions. Developers also implement newer security tools into the newer versions of their programs and operating systems, making them less vulnerable to attacks. While older versions may still have developer support, older versions are often dropped, meaning any new flaws discovered may not get patched.
Additionally, there are times when software companies will stop support for older versions as a way to subtly force users to upgrade to newer versions. The reason your older operating system or software program may not be getting security patches is that the company wants you to upgrade. Dropping security support is a passive-aggressive way to force users to adopt a new version. Yes, that includes free software like Windows Internet Explorer. Software companies only have so many resources and developers on staff to keep patching old programs.
While it is true that newer versions of software will have as-yet-discovered vulnerabilities, it’s important to note that those vulnerabilities are often unknown to both the developers and hackers. After new software is released, there’s usually a flurry of activity from security professionals and hackers to discover those flaws, making it somewhat of a race to see who can find those exploits first. Once hackers discover and try to exploit those vulnerabilities, developers are often (but not always) quick to patch those flaws.
The older a software version is, the longer hackers have had to analyze it, break down its code, and find its flaws. Especially if that software is popular or important for a specific industry, hackers can and often do discover vulnerabilities that they can exploit. Newer versions of the software will likely have fixed those exploits, but older versions may still have them, making the older software increasingly dangerous to have around.
Both popular and essential software are targeted by hackers more frequently
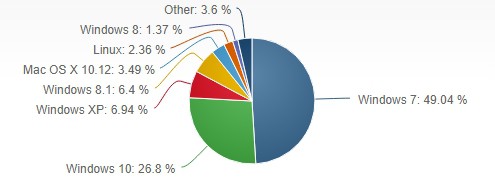
As The Verge reported, the majority of the WannaCry victims were running Windows 7. A key reason for this is because Windows 7 is still the most popular operating system on the market. According to NetMarketShare, the Windows 7 OS makes up nearly 50% of all computer operating systems. As hackers are opportunists who tend to cast a wide net, finding vulnerabilities and creating viruses and malware for Windows 7 is more likely to reap some kind of reward over other operating systems with a smaller market share, such as Linux. It certainly plays into their favor that businesses tend to lag when it comes to upgrading to newer operating system versions. For example, there are still more users on Windows XP (which is no longer supported) than on Windows 8, the Windows version that preceded the current Windows 10.
However, despite Windows 7 being the most popular and most commonly targeted computer operating system, it’s far from the most vulnerable software program or operating system around. The heavily-cited website CVEdetails.com (Common Vulnerabilities and Exposures), found that Google’s Android operating system had the most number of vulnerabilities in 2016 (unspecified version), while Adobe Flash Player was the most vulnerable software program. The site also shows that the “all-time” offenders appear to be Unix-based systems–Linux Kernel and Mac OS X–while Google’s Chrome and Mozilla’s Firefox web browsers appear to be among the most vulnerable of those types of programs.
Ignoring software updates can come with significant consequences
As is the case for those Windows 7 users who chose to ignore Microsoft’s security patch, failure to update software with such fixes can result in the exact situation the developers were hoping to prevent.
In 2016, security blog DarkReading published a post on The 10 Worst Vulnerabilities of the Last 10 Years. That list includes the following:
- OpenSSL Heartbleed Bug: affected website SSL/TLS security, patched through software updates.
- DNS Cache Poisoning Flaw: affected web browsers, patched through software updates.
- GNU Bash Remote Code Execution Vulnerability (Shellshock): affected web browsers and Linux systems, patched through software updates.
- Android Stagefright Vulnerability: affected Android operating systems, patched through software updates.
- SSL 3.0 Protocol Vulnerability / POODLE Attack: affected website and web browser security, mitigated (but not completely patched) by disabling SSL 3.0.
- Remote Code Execution Vulnerability in Microsoft Server Service (Buffer Overflow Vulnerability): affected Microsoft Server operating systems, patched through software updates. Read more on buffer overflow attacks and remote code execution attacks.
- Java Serialization Bug: affected Java software and middleware products using Java, mitigated (but not completely patched) through software updates.
- Glibc getaddrinfo Stack-based Buffer Overflow: affected Linux distributions, patched through software updates.
- Bad USBs: not a software program, but a known threat that’s difficult to mitigate.
In almost all of these cases, those who chose to ignore the patches were at a high risk for malicious activity on their machines. This was particularly true for the Heartbleed bug which affected over 600,000 websites, allowing hackers to steal a significant amount of private encryption keys.
Here’s a huge wrinkle in choosing to ignore a software security patch: they’re almost always free. So why do users ignore them?
A 2016 research paper in the Operations Research and the Management Sciences (INFORMS) Journal notes that up to 87% of computer users simply ignore security warnings. The study suggests that users have essentially become desensitized to the warnings, as they’re so used to messages popping up for many different reasons, many of which are inconsequential. Additionally, as security warnings appear when users are in the middle of performing tasks, many decide to ignore them.
The problem, of course, is that anyone sitting at a computer is likely doing something important or leisurely at the time a message appears, and is unlikely to want to put a hold on that activity to install an update. The paper also provided a ranked list of what type of activities individuals may be engaged in that leads them to ignore update messages and security warnings.
Topping the list of activities were “on the way to close window” (74% disregarded), “while typing” (78% disregarded), “during video” (79% disregarded), and “while transferring information” (87% disregarded).
Regardless of why users do not update their security systems, simply put, they’re ignoring the associated risks and choosing not to update.
If you fall into that category, you’re in good company. However, the last company you want to be in is amongst the many people who have knowingly or unknowingly refused security updates and faced the distinct consequences for that action.