Adobe Flash has been around since the dawn of the commercial internet. The first version of the world wide web was built on a very unimpressive version of the Hyper Text Markup Language (HTML) which was not able to do anything in the way of animation or scripting. Adobe developed Shockwave Flash, which became simply Flash later in life, and that gave developers a way to bring rich content to the static web. Flash was used to play movies, create online video games, and display annoying advertisements. By the mid-2000’s Flash was installed on millions of desktop computers world-wide. That massive deployment caught the attention of hackers who liked the idea of being able to infect so many systems with one piece of malware. Flash has been targeted by malware authors for years culminating with hundreds of vulnerabilities in the last two years alone.
Security and privacy advocates world-wide recommend disabling or uninstalling Flash as a standard step in securing a computer. The vulnerabilities come too fast for Adobe to keep up, which means it is almost certain that there are zero day (unknown) vulnerabilities in the plugin at any given time. Thankfully, HTML has become more capable in the past few years and the need for Flash is dropping off, which makes the internet a safer place.
Large number of vulnerabilities
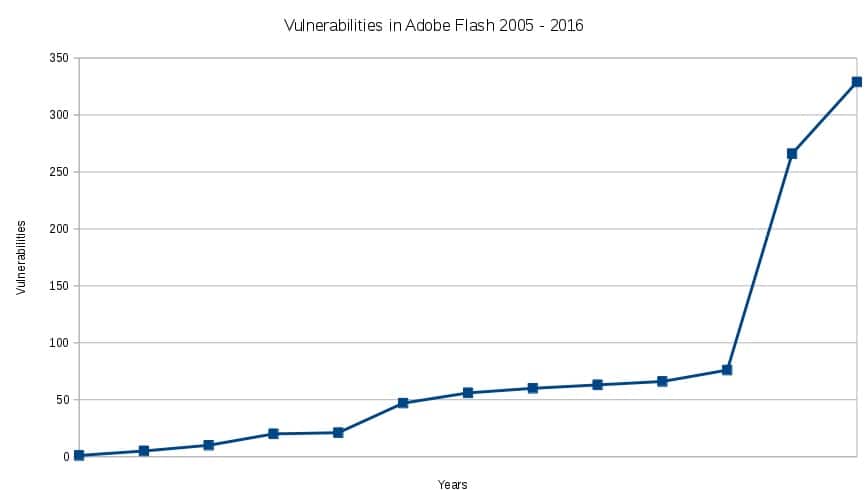
In a review of the vulnerabilities reported against Flash in the past 12 years, the site CVE Details reveals a whopping 1020 vulnerabilities were discovered since December 2005. While that may seem like a long time, the problem is getting exponentially worse. In 2005, there was a single vulnerability reported. By 2014 there were 76, and an astounding 595 vulnerabilities have been reported in the last two years alone.
Severity of vulnerabilities
Not all vulnerabilities are equally bad. There are many vulnerabilities reported against products that are not a high priority to fix. For example, an exploit that requires a large number of antecedent events to fall into place before it can be perpetrated is less critical than an exploit that can be used in a wider variety of situations. Another example is that an exploit which requires an attacker to be physically present in front of the computer is less critical than an exploit which can be used remotely over the internet. In an effort to bring some standardization to vulnerability assessment, the Common Vulnerability Scoring System (CVSS) version 3 was created. It scores vulnerabilities on a number of criteria to assess their level of severity. The score ranges are:
- Low: 0.1 – 3.9
- Medium: 4.0 – 6.9
- High: 7.0 – 8.9
- Critical: 9.0 – 10.0
The highest scoring, meaning worst, exploit is one where an attacker can execute code of their choice (called arbitrary code execution) remotely; usually over the internet. Of the 1020 vulnerabilities reported by CVE Details, 808 have a description which indicates the vulnerability can be used to execute arbitrary code remotely. That’s not terribly surprising since Flash is a plugin used on the internet, but it highlights how dangerous it is to have Flash available on your system.
With regards to the CVSS scores, 92 percent of the vulnerabilities reported in Flash scored either High or Critical:
- Critical (9.0+): 863
- High (7.0 – 8.9): 77
Privacy implications
The problems with Flash are not all related to vulnerabilities. Flash will also report detailed information about your browser and your operating system to snooping sites. As the use of VPNs and privacy tools like Tor gain greater adoption, it’s becoming harder for adversaries to count on being able to identify a person by their IP address. One technology that is replacing that type of identification is browser fingerprinting.
Every browser has a fingerprint of some sort. A browser has to send some information to a web server in order to view the website, but browsers with Flash installed can supply a much richer data set. The more data your browser provides, the more unique its fingerprint. Observers can then track your progress throughout the internet by seeing the same browser fingerprint on multiple sites.
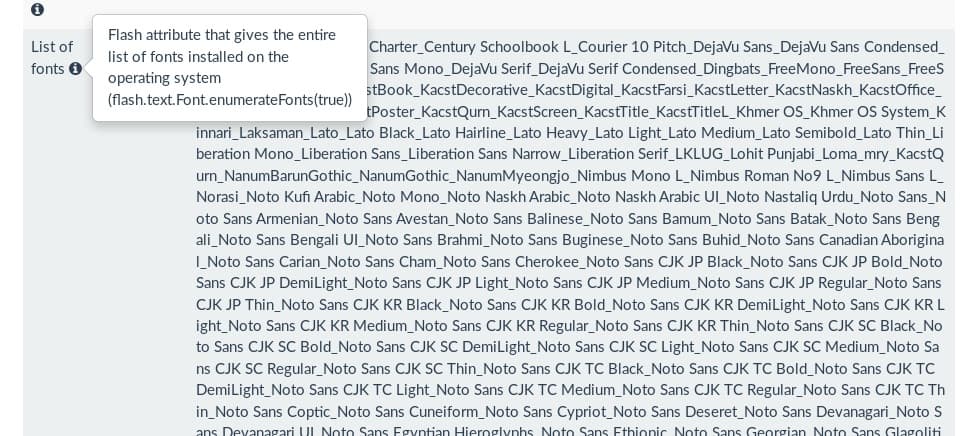
By way of example, the Am I Unique website shows that my Flash plugin gives up the following information about my system when queried:
- List of installed fonts
- Screen resolution
- System language
- Platform
Why is Flash targetted so heavily by bad guys? There are a few reasons.
Big target
Flash is cross-browser and therefore is present in millions of web browsers across the globe. The most efficient type of malware is a type that can be written once and then deployed over the largest possible number of victims. Those types of odds greatly increase hackers’ chance of success, so big targets like Flash are attractive. We can see from the stats at the beginning of this article, the uptick in Flash infections over time is striking.
Confusion
Flash has a long, twisted history, which is very hard to follow. In 2012, at least two different version numbers were in use. One for Windows and macOS, and one for Linux users. Up until around this time, Adobe had used the Netscape (NPAPI) interface but Google had just released a Pepper Plugin (PPAPI) version which had a little more separation from the system and was also updated more frequently with new features. That changed the version numbering system again. The Pepper Plugin is now the standard in partnership with Adobe. With all this confusion, it is hard for users to keep up with the current version which does not help keep the plugins in the wild up to date.
Outdated software is an excellent attack vector. Once a company issues a patch for a particular issue, the world can examine that patch and in many cases determine what was fixed. For bad guys, this means they have just learned of an exploit that they can use for a few days or weeks or maybe months against users who have not yet updated their system with the new patch. Confusing users with different version numbers makes it harder for people to know when they should update.
Alternatives
HTML5 is the latest and greatest version of the HTML language that makes up the web. Historically, plugins like Flash were needed to fill in functionality that HTML could not provide, such as playing videos or animated ads. HTML5 has that ability built-in and therefore the general dependence on Flash is dying off. Apple has never had Flash on its iOS devices, and Google dropped it out of Android several years ago. That leaves just desktop users who may stumble across a Flash site now and again.
The big video sites such as Netflix and YouTube dumped Flash years ago in favour of HTML5. Facebook has also stopped using Flash. Google Chrome and Firefox no longer ship with Flash installed.
But, what if you run across a Flash site that you just have to use? There are some old Flash alternatives which don’t generally work very well. I’ve found that I require Flash so rarely that I don’t even have it installed any more. As far as I can tell, the net drawback to my internet surfing has been that some ads don’t play which doesn’t really concern me. If I really needed Flash, like I did for this article, I would install it and remove it when I am done. It’s a very quick install so there’s no need to keep it lurking around on my system. The NoScript plugin for Firefox will block Flash as well as Javascript, so while I don’t recommend having Flash installed at all, if you simply must, then use that plugin to disable it by default and only enable it for the times you need it. For Google Chrome, the Flash Control plugin will block Flash.
I found some Flash alternatives still available, although most of them are abandonware now. It is not easy to tell whether these plugins would be more secure than Adobe Flash and my feeling is that they will not be. In some cases the code is very old so it does not look like anyone is maintaining or patching them.
Linux
Gnash
The GNU Flash Movie Player is a GNU project. The GNU project seeks to create open sourced versions of popular software in order to aid Linux adoption. The code for Gnash has not been updated since 2011 but it is still on GNU.org.
Lightspark
This also looks like abandonware. The last code commit was in 2013. However, the site wiki was updated in 2015 so there may be some lingering interest in it.
Swfdec
Swfdec is a Flash player for the Gnome desktop. It was last updated in 2008 and probably won’t work on modern browsers.
Honourable mentions
These don’t really count as Flash alternatives because, well…they’re not Flash. That means that users can’t decide to use these to view Flash in lieu of the Adobe Flash plugin. Rather, they’re competing technologies that deserve to be mentioned since they’ve made a mark on the animated web.
Unity Web Player
Unity web player is more of a game engine, but it can be used to display rich content on the web. It can’t play Flash directly, but it can handle many formats and it is not too difficult to convert Flash into many other formats.
Silverlight
Silverlight was Microsoft’s Flash replacement. It is no longer developed and will run into end-of-life in 2021, but the browser plugins are still available for the foreseeable future.
The future of Flash is certain; it is doomed, but not because of its security issues. HTML 5 is cleaner because it does not require users to install or maintain any plugins. It’s also more sustainable because it’s native HTML and therefore has a stable and certain future which companies and developers can count on. HTML 5 would have killed off Flash anyhow, but we’re especially happy to see it go because of all the security and privacy issues it brings to the table.

I brought my MacBook Pro back to Apple Store, the Senior Technician removed my Flash Player he said “It’s not Safe and Not Necessary”. I had to download some documents from work and it requires Flash Player, which Firefox installed the “Pepper Flash”. You’re right, my Chrome blocks all Flashes.
It frustrates me “That Certain Government (Canada) websites requires a Flash Plug-In” why don’t they upgrade their system?!! I used to pay for “DramaFever.com” to watch K-drama and it requires Flash or you can’t watch it. Annoying thing is ** Whether I use Safari/Firefox/Chrome to watch the Drama, this website requires me to Install Flash for all 3 Browsers!! In the end, I cancelled my Membership as there are other Paid websites that doesn’t require “Mandatory Flash” .
Thanks for this article!!
Hi,
It’s true, Flash is not totally dead yet. There are some companies that still use it and governments are almost always famously behind the times with everything. But, the trend is in the right direction with things like HTML 5 picking up most of what Flash is traditionally used for.
If you use Firefox, you can use the NoScript addon to control Flash. It lets you have it installed, but won’t allow any Flash to actually run unless you specifically say it is OK to do so. That, at least, will ensure that you’re only running Flash when you absolutely have to and can trust the source of it.