Elastic SIEM has very strong foundations, supplied by the Elastic Stack products. Elastic NV is particularly well-known for its log file management products. As log messages are one of the key sources of SIEM methodology, Elastic SIEM has a good chance of being one of the leaders in the field. However, log management is just one part of the full SIEM strategy.
How does SIEM work?
SIEM stands for Security Event and Information Management. It is a combination of two previous security monitoring techniques: SIM and SEM. SIM is Security Information Management and it examines log file records. This is a Host-based Intrusion Detection System (HIDS). SEM is Security Event Management and it deals with real-time data. This is a Network-based Intrusion Detection System (NIDS).
Network-based security monitoring systems have the advantage of speed because they work in real-time. However, this strategy has weaknesses because hackers can sneak into the system without detection by combining a series of actions to make any malicious activity seem to be legitimate individual transactions.
Host-based security systems are able to unify different log message formats to gather data from many points in the system and look for signs of attack. The problem with SIM is that it isn’t instant. It takes time to accumulate enough information to feed into the analysis.
SIEM systems are not designed to block entry to the network – that is the job of a firewall. The purpose of SIEM is to catch intruders who have managed to sneak through the perimeter defenses of the network. By combining SIM and SEM, SIEM can direct network traffic investigations to specific users and endpoints that have been identified by SIM. So, SIEM gives more accurate warnings than a standard network security monitor.
About Elastic NV
Elastic NV was originally called Elasticsearch BV. The company was started by developers who created Elasticsearch, which was a hit.
After forming a company to manage the Elasticsearch software, the team continued development creating more products, namely Kibana, Beats, and Logstash. Each of these packages can operate as standalone tools, but they also fit together into a suite, called Elastic Stack.
- Logstash is a log server and consolidator
- Elasticsearch is a search tool that is ideal for analyzing log files
- Beats is a data transfer agent with a specialist variant for log data
- Kibana is a data viewer and analysis tool, used as a front end for Elastic Stack and able to take data input from other data collection tools
Logstash, Beats, and Kibana are all open source free to use. Only Elasticsearch has a charge. Each unit in the Elastic Stack can be used in combination with other tools produced by third parties. The free tools are widely recommended by the producers of other free data analysis tools and intrusion detection systems. Kibana is particularly widely used.
The Elastic Stack package is free to use as on-premises software with higher-paid plans that include professional support. The Elastic SIEM system is an add-on to Kibana. All Elastic NV products are available as cloud-based SaaS solutions for which there is no free version. There is however a free trial available.
Elastic SIEM overview
Elastic Stack is an SEM system because the combination of all of those tools creates a log message gathering, consolidation, searching, and analysis system. So, all Elastic NV needed to do in order to create a full SIEM system was to pre-write data searches for security issues. It then added a live network monitor that could feed through real-time data into the Logstash and Elasticsearch file handling system.
The new network monitoring element is an extra capability added to Kibana. The Kibana system provides data representation tools for any data source. Its live network monitoring facility uses the Cisco Systems traffic reporting standard, NetFlow as its source.
Another new service in the Elastic collection is the Elastic Agent, which acts as endpoint security and is also marketed under the name Elastic Security. It is still under beta testing and so is offered for free. Elastic plans to release a paid version once it has perfected the software. This tool feeds data on endpoint activity into Kibana as another source of information for the SIEM solution.
Elastic SIEM features
Elastic SIEM is flexible because it allows the user to decide which information sources should be used as input into the activity detection monitoring system. The tool itself is just a data interpreter and isn’t of much use without activated data sources set up.
Threat Intelligence
The most important requirement of a SIEM that Elastic NV doesn’t supply is threat intelligence. This is sourced from a third-party in the form of MITRE ATT&CK® Matrix. Elastic also supplies detection rules for free. However, these are not automatically updated and don’t fully compete with the sophisticated research department that feeds chain of attack and threat intelligence updates to rival SIEM systems.
User monitoring
Elastic SIEM implements user and entity behavior analysis (UEBA). This has become a standard element of a SIEM system. It tracks normal behavior by each user or user group and adjusts alert levels accordingly. This process uses AI-based machine learning techniques and helps to reduce false-positive reporting. Before UEBA was introduced SIEM systems tended to be oversensitive and flagged a range of legitimate activity as suspicious.
Access rights supervision
Elastic SIEM identifies log messages from access rights management systems, such as Active Directory to discover hacker attempts to break in through techniques that include brute force attacks.
The collection of event data from around the system enables the network manager to spot patterns of activity that show hackers attempting to find an easy route into the network.
Anomaly detection
The threat intelligence rules provided by Elastic NV trigger alerts that attract the attention of network support staff to the SIEM console for further information. Analysis features support manual threat hunting efforts.
Elastic SIEM configuration options
Both Elastic SIEM and Elastic security are new products and offered for free as part of Kibana functionality. The SIEM service requires the implementation of the entire Elastic Stack. Elastic Stack is available for free for on-premises installation and that includes Elastic SIEM. Paid plans offer the same functionality but include access to a professional support team.
The on-premises version of Elastic Stack and Elastic SIEM installs on EHEL, CentOS, SLES, OpenSuSE, Debian, and Ubuntu Linux. It will also install on macOS and Windows. There are four plans for the software and the base package is free to use.
Elastic SIEM and Elastic Stack are also available as a cloud-based service. There are four plan levels for this SaaS version of Elastic Stack, which is called Elastic Cloud, and none of them are free. However, it is possible to get a 14-day free trial of the service.
Elastic SIEM dashboard
Elastic SIEM is implemented as extra screens for Kibana. The SIEM dashboard includes an overview screen, a network screen, and detail views that show conversations and activities per source or destination of connections.
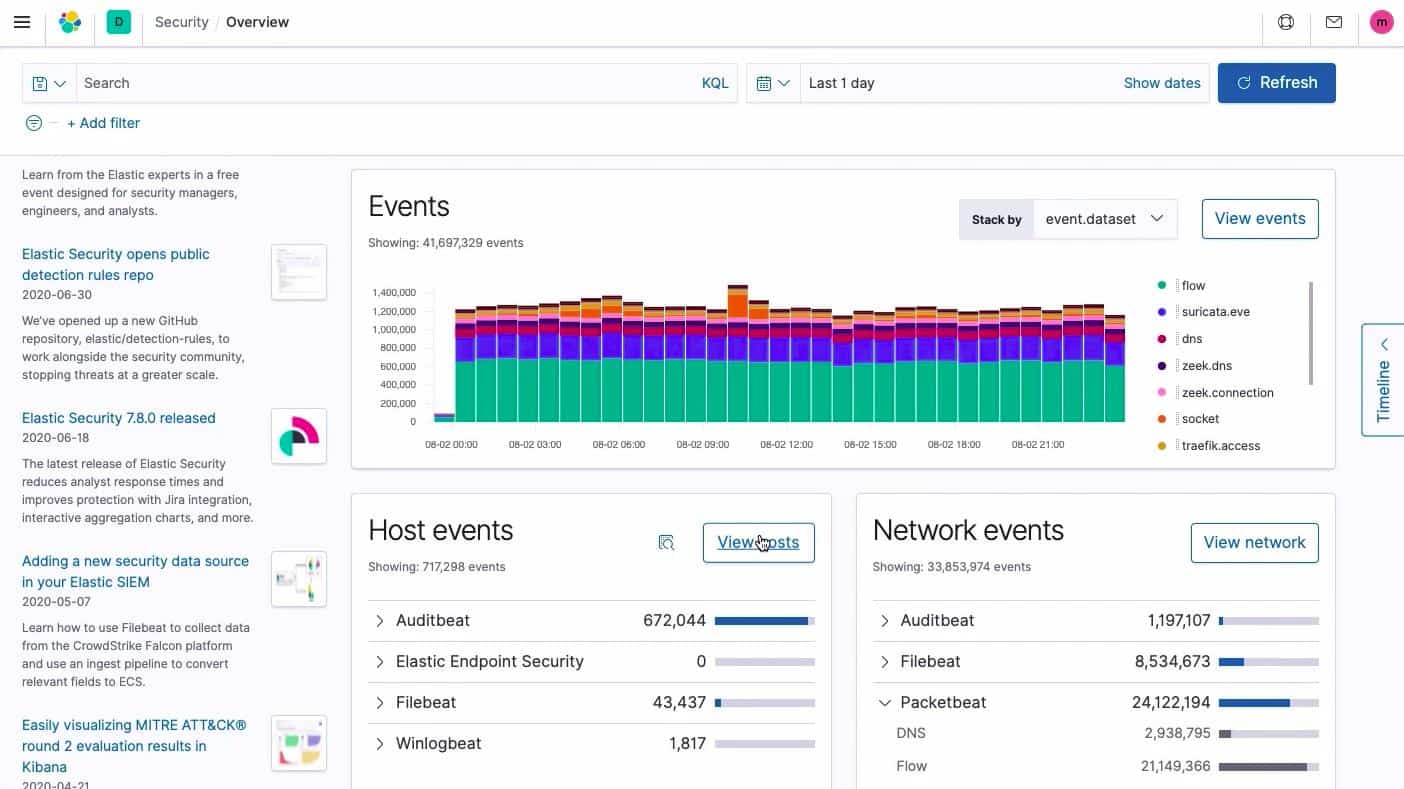
The Overview screen displays event information in a tabulated format.
Each event entry in the overview represents a suspicious occurrence and the line representing the event can be expanded for more details. The overview screen also shows a map of the network and graphs of host activity.
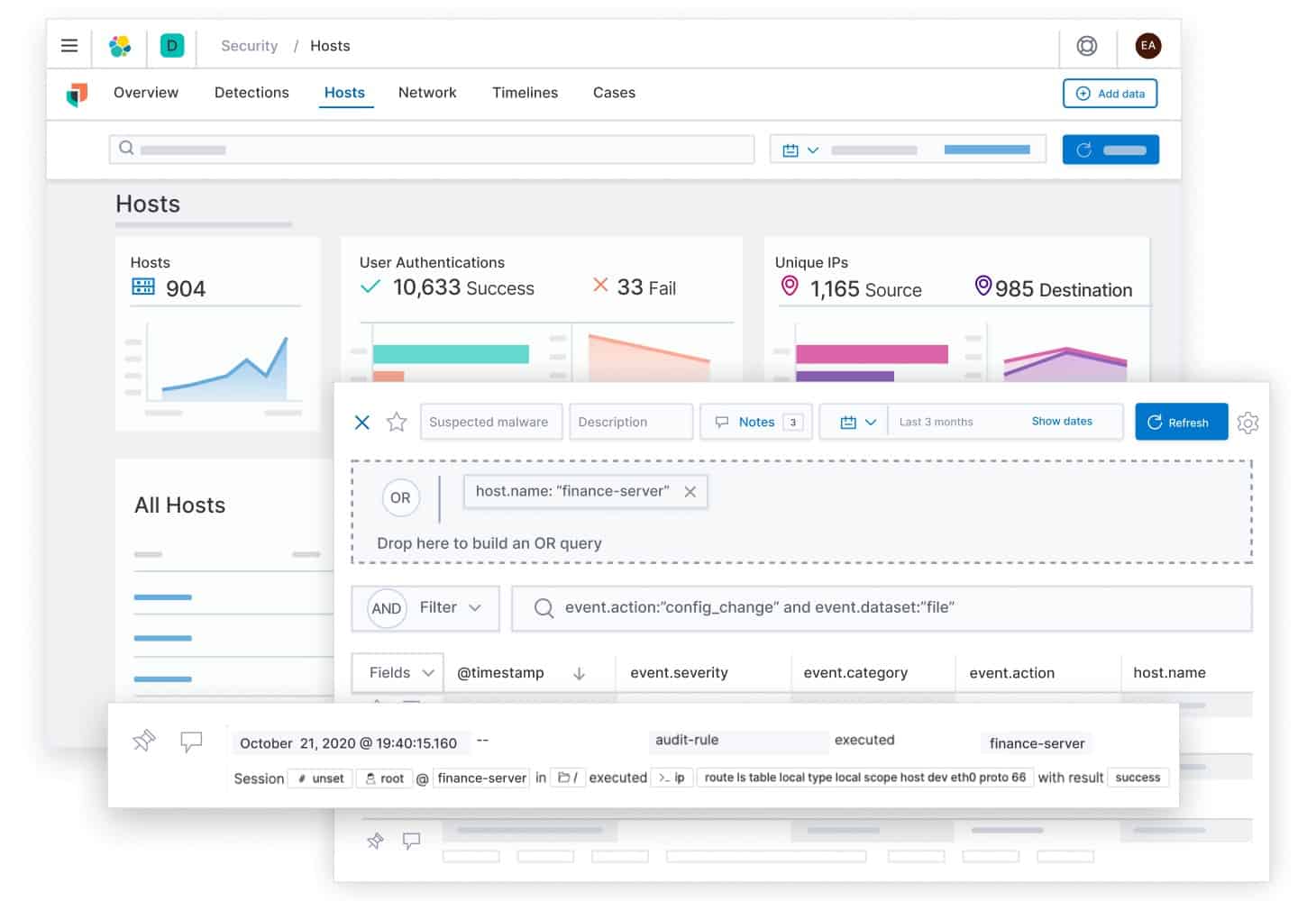
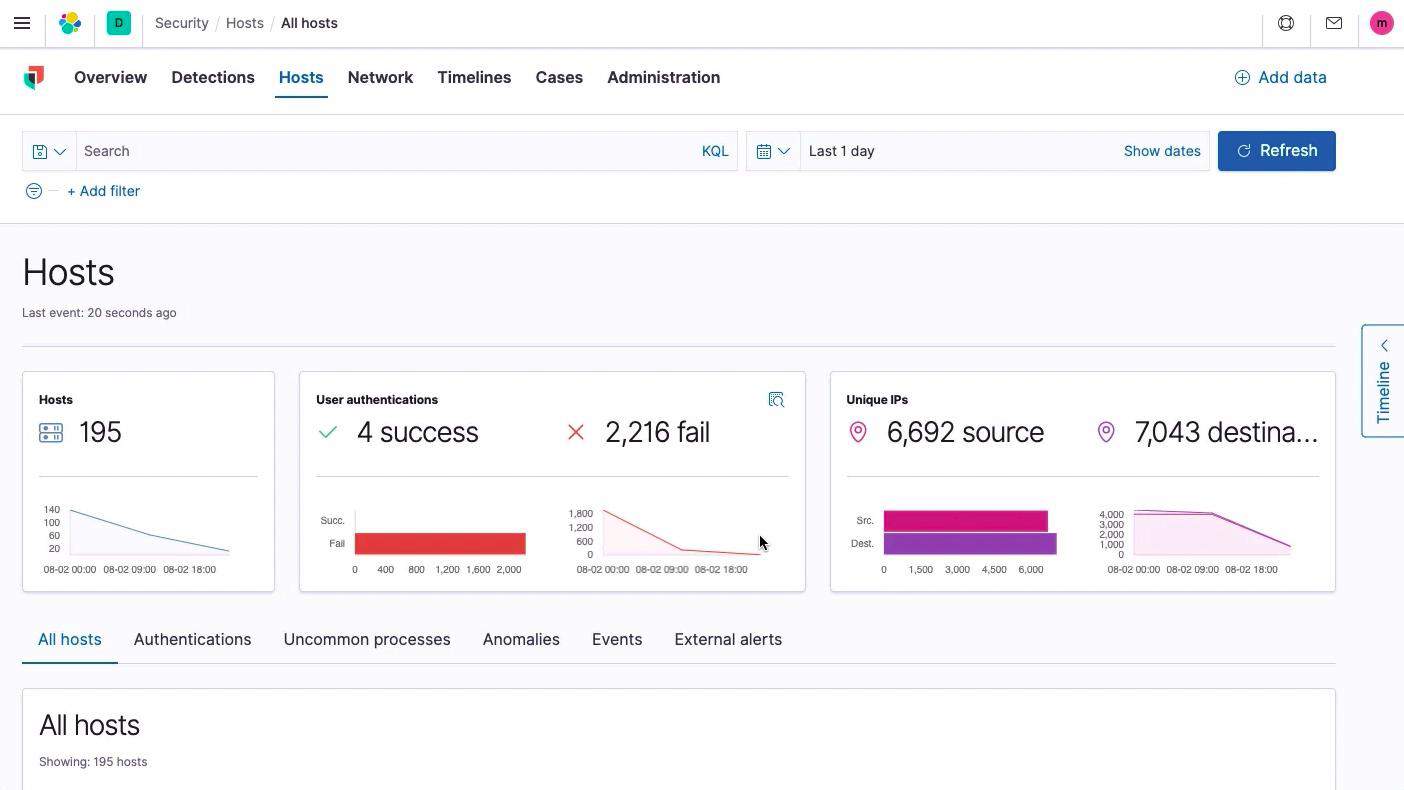
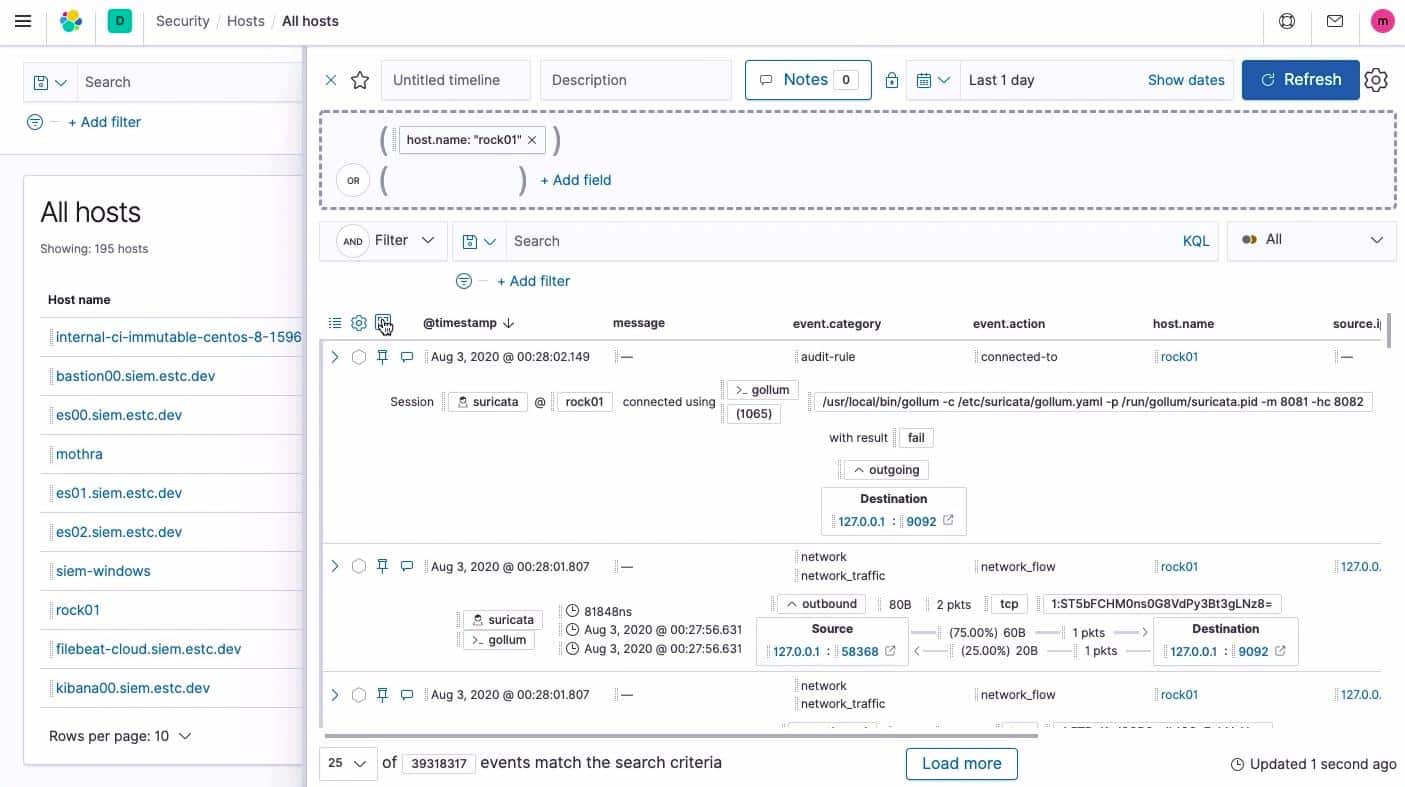
Detailed screens along with the menu focus on one part of the IT infrastructure, such as host performance or network activity.
Each record in a detailed screen, such as the Hosts screen, shown below, can be expanded to reveal further details.
Attack mitigation
The incident response capabilities of Elastic SIEM is a weak point of the system. Elastic SIEM is still new and, although the sales pitch for the software explains that the Elastic Agent can be used for responses to attacks, it doesn’t detail how. Incident response is a manual workflow with Elastic SIEM
Compliance reporting
Elastic SIEM is suitable for businesses that need data management tools that comply with certain security standards. These include CSA STAR and HIPAA. The Elastic SIEM service isn’t fully integrated with SOX or PCI-DSS compliance.
Alternatives to Elastic SIEM
Elastic SIEM is a new tool and promises to develop into a very useful system security service. However, it isn’t fully developed and it lacks some of the important features that rival SIEM systems include.
Among the features that Elastic SIEM lacks is up-to-date threat intelligence data. Long-established cybersecurity operators have experts working in research labs and offering human analysis and penetration testing services. The expertise of these specialists is usually bundled into other SIM services. Elastic NV lacks a background in cybersecurity. It is the producer of system monitoring and management tools that has decided to move into cybersecurity.
What Elastic Stack is good at is log file analysis. This makes it a great contributor to a very high-quality SIM. The network monitoring features added to Kibana, using live NetFlow data make Kibana a great network monitoring tool. However, the requirements of a full SEM system to include constant updates on attack vectors are missing from the Elastic solution, making it a weak competitor in the SIEM market.
There are a number of fully developed SIEM systems that would offer any company a better security solution than the nascent Elastic SIEM. In a few years’ time, Elastic SIEM may have developed and could be worth another look.
More detailed information about SIEM and the major suppliers in that market is available in the guide The Best SIEM Tools. If instead you are looking to outsource the work and employ a team of SIEM experts instead, check out our The Best Managed SIEM Services post.
Here are the best alternatives to Elastic SIEM:
- ManageEngine EventLog Analyzer (FREE TRIAL) The ManageEngine SIEM solution is split into two modules: the EventLog Analyzer for SIM functions and Log360 for SEM services. It installs on Windows and Linux. Access the 30-day free trial.
- Datadog Security Monitoring An infrastructure monitoring system that is hosted in the cloud. Security features in the SaaS package include a SIEM-based security monitoring module.
- McAfee Enterprise Security Manager A SIEM tool from one of the oldest cybersecurity brands in the world. This software is backed by threat vector feeds for a research lab and includes strong rights management features based on Active Directory data. It installs on Windows and macOS.
- Fortinet FortiSIEM A well-planned platform of detection strategies paired with a feed of attack vector data from a specialist research lab. This is a cloud-based system that also involves on-premises device agents.
- Rapid7 InsightIDR A cloud-based SIEM cybersecurity service that deploys agent software on each device in the monitored system. It includes indicators of compromise feeds for a research lab and automated threat mitigation.
- Heimdal Threat Hunting and Action Center This cloud platform provides a SIEM service for threat detection and also automated responses. This unit interacts with on-premises Heimdal tools to gather data and block threats.
- SolarWinds Security Event Manager A SIEM tool from the world-leading producer of infrastructure monitoring and management systems. The software installs on Windows Server and includes real-time incident response and pre-configured standards compliance processes and reporting formats.
- OSSEC A free open-source IDS with a particular focus on log analysis. Often used with Kibana as a front end, this software installs on Windows, macOS, Linux, and Unix.
- LogRhythm NextGen SIEM Platform A network traffic and log message analysis implementation. It installs on Windows and Linux.
- AT&T Cybersecurity AlienVault Unified Security Management This cyber defense system includes a range of detection strategies that include SIEM techniques plus other methods. It runs on Windows and macOS.
Elastic SIEM FAQs
When was Elastic SIEM released?
Elastic SIEM was launched in June 2019 as a free service.
Is Elastic Stack a SIEM?
By itself, Elastic Stack is not a SIEM. This suite of free tools can be used to collect and search through log files and adding on the Elastic SIEM package get you a set of search terms that convert the data searching system into a full SIEM.
How much does Elastic SIEM cost?
Elastic SIEM is only available as part of Elastic Cloud, a hosted package. The service is available in four plans and all of them include Elastic SIEM. They are Standard for $16 per month, Gold for $19 per month, Platinum for $22 per month, and Enterprise for $30 per month.