Intrusion Prevention Systems (IPS) are a critical component of modern cybersecurity strategies, designed to proactively protect networks and systems from unauthorized access, malware, and other security threats. While traditional firewalls and antivirus software can block known threats, an IPS actively monitors network traffic in real-time and takes immediate action to prevent potential intrusions before they can cause harm.
IPS tools are essential for organizations looking to safeguard sensitive data and maintain a secure network environment. As the threat landscape continues to evolve, organizations need effective solutions to identify and mitigate a wide range of security risks. IPS tools go beyond simple detection. They offer automated responses like blocking malicious IP addresses, terminating harmful connections, and alerting security teams to suspicious activity.
By examining network packets and analyzing their contents, an IPS can identify abnormal patterns that indicate potential security breaches. Examples of such malicious activity include distributed denial-of-service (DDoS) attacks, buffer overflows, or SQL injections.
This article explores the best IPS tools and software available today, providing detailed insights into their features, strengths, and how they integrate into broader network security strategies. We highlight both enterprise-grade solutions and more affordable options for small to medium-sized businesses, ensuring that organizations of all sizes can find a solution that fits their needs.
Whether you are looking for a simple, out-of-the-box tool or an advanced solution with deep customization options, this guide will help you navigate the world of IPS technology. By implementing the right IPS tool, businesses can ensure continuous monitoring and real-time protection against emerging threats, reducing the risk of data breaches and enhancing overall network security.
Here is our list of the best IPS tools:
- ThreatLocker (GET DEMO) This security system makes it impossible for unauthorized access to data through fencing and by blocking any software from running without valid user credentials. Access the demo.
- ManageEngine Endpoint DLP Plus (FREE TRIAL) This software package blocks off the options for outright intruders and then focuses on detecting account takeover and insider threats. Runs on Windows Server. Start a 30-day free trial.
- CrowdStrike Falcon XDR This security package offers threat detection and automated responses. This is a cloud-based system with device-based agents.
- Datadog Real-time Threat Monitoring A combination of cloud-based network monitoring and a SIEM system that work together to watch over network performance while also spotting anomalous behavior that could indicate an insider threat or an intruder.
- Splunk Widely-used network analysis tools that has intrusion prevention features. Available for Windows, Linux, and in the Cloud.
- SolarWinds Security Event Manager This powerful security tool uses both network-based and host-based intrusion detection methods and takes preventative action. Pre-installed presets will get you up and running in no time. Installs on Windows Server or via cloud.
- Sagan Free intrusion prevention system that mines log files for event data. Installs on Unix, Linux, and Mac OS, but can gather log messages from Windows systems.
- OSSEC The Open Source HIDS Security is highly respected and free to use. Runs on Windows, Linux, Mac OS, and Unix, but doesn’t include a user interface.
- Trellix XDR Platform This cloud-based system includes endpoint protection and network scanning that quickly identifies and blocks both manual and automated attacks.
- OpenWIPS-ng Open-source command-line utility for Linux that detects intrusion on wireless networks.
- Fail2Ban Free lightweight IPS that runs on the command line and is available for Linux, Unix, and Mac OS.
- Zeek Network-based intrusion detection system that operates on live traffic data. This tool installs on Linux, Unix, and Mac OS and is free to use.
Security weaknesses
Any system is only as strong as its weakest link. In most IT security strategies, the weakness lies with the human element of the system. You can enforce user authentication with strong passwords, but if users write passwords down and keep the note close to a device that has network access, you might as well not bother enforcing user authentication.
There are many ways that hackers can target employees of a company and trick them into disclosing their login details.
Phishing
Phishing has become common. Everyone has learned to become wary of warning emails from banks or trading platforms such as eBay, PayPal, or Amazon. A phishing campaign involves a fake Web page from an online service. The hacker sends out emails en masse to all emails on a list bought on the internet. It doesn’t matter whether all of those email addresses belong to customers of the mimicked service. As long as some of the people being reached have accounts with the tricked website, then the hacker stands a chance.
In phishing attempts, the victim is presented with a link within an email that leads to a fake login page that looks like the usual entry screen of the mimicked service. When the victim tries to log in, that username and password go into the hacker’s database and the account is compromised without the user realizing what has happened.
Spearphishing
Hackers target company employees with phishing scams. They also practice spear phishing, which is a little more sophisticated than phishing. With spear phishing, the fake email and login page will be specifically designed to be like the site of the company being hacked and the emails will be directed specifically at the employees of the company. Spear phishing attempts are often used as phase one of a break-in attempt. The initial pass of a hack is to learn details about some of the employees of a company.
Doxxing
The information gathered in the spear phishing phase can be blended together with research into individuals by examining their social media pages, or combing through their career details. This targeted research is called doxxing. With the information gleaned, a targeted hacker can build up profiles of key players in a business and map the relationships of those people to other company personnel.
The doxxer will aim to get enough information in order to successfully mimic one employee. With this identity, he can gain the trust of others in the targeted company. By these tricks, the hacker can get to know the movements of the company’s accounting staff, its executives, and its IT support staff.
Whaling
Once the hacker has earned the trust of various staff members, he can trick login details out of anyone in the business. With a lot of confidence and the knowledge of the way people work together in a business, a con artist can even steal large amounts of money from a company without even having to log into the system; orders for bogus transfers can be given over the phone. This targeting of key personnel in a business is called whaling.
Attack strategies
Hackers have learned to use phishing, spear phishing, doxxing, and whaling to get around firewalls and antivirus software. If a hacker has the admin password, he can install software, set up user accounts, and remove security processes and get access to the entire network, its equipment, servers, databases, and applications unhindered.
These new attack strategies have become so common that company network security administrators need to plan defenses that assume that the systems boundary security measures have been compromised.
In recent years, the advanced persistent threat (APT) has become a common strategy for hackers. In this scenario, a hacker can spend years with access to a company network, accessing data at will, using company resources to run covering VPNs through the company’s gateway. The hacker can even use the company’s servers for intensive activities such as cryptocurrency mining.
or laterAPTs go undetected because the hacker is in the system as an authorized user and he also makes sure to delete any log records that show his malicious activity. These measures mean that even when the intrusion is detected, it can still be impossible to trace and prosecute the intruder.
Intrusion detection systems
An essential element of intrusion prevention systems is the Intrusion Detection System (IDS). An IDS is designed to look for unusual activity. Some detection methodologies mimic the strategies employed by firewalls and antivirus software. These are called signature-based detection methods. They look for patterns in data to spot known indicators of intruder activity.
A second IDS method is called anomaly-based detection. In this strategy, the monitoring software looks for unusual activities that either don’t fit the logical pattern of user or software behavior or that don’t make sense when examined in the context of the expected duties of a particular user. For example, you wouldn’t expect to see a user in the Personnel Department logged in as altering the configuration of a network device.
An intruder does not necessarily need to be an outsider. You can get intrusion into areas of your network by employees exploring beyond the facilities to which they are expected to need access. Another problem lies with employees who exploit their authorized access to data and facilities in order to destroy or steal them.
Intrusion prevention
Intrusion prevention systems work to the maxim “better late than never.” Ideally, you wouldn’t want any outsiders getting unauthorized access to your system. However, as explained above, this is not a perfect world and there are many cons that hackers can pull to trick authorized users into giving away their credentials.
Specifically, intrusion prevention systems are extensions to intrusion detection systems. IPSs act once suspicious activity has been identified. So, there may already have been some damage done to the integrity of your system by the time the intrusion has been spotted.
The IPS is able to perform actions to shut down the threat. These actions include:
- Restoring log files from storage
- Suspending user accounts
- Blocking IP addresses
- Killing processes
- Shutting down systems
- Starting up processes
- Updating firewall settings
- Alerting, recording, and reporting suspicious activities
The responsibility of admin tasks that make many of these actions possible is not always clear. For example, the protection of log files with encryption and the backing up of log files so that they can be restored after tampering are two threat protection activities that are usually defined as intrusion detection system tasks.
Limitations of Intrusion Prevention Systems
There are many potential points of weakness in any IT system, but an IPS, although very effective at blocking intruders, is not designed to close down all potential threats. For example, a typical IPS does not include software patch management or configuration control for network devices. The IPS won’t manage user access policies or prevent employees from copying corporate documents.
IDSs and IPSs offer threat remediation only once an intruder has already begun activities on a network. However, these systems should be installed to provide an element in a series of network security measures to protect information and resources.
The best Intrusion Prevention Systems
There is a remarkably large number of IPS tools available at the moment. Many of these are free. However, it would take you a long time to study and try every single IPS on the market. This is why we have put together this guide to intrusion prevention systems.
Our methodology for selecting an IPS tool
We reviewed the IPS market and analyzed tools based on the following criteria:
- Procedures to detect email-bound cons, such as phishing
- Automated attack mitigation steps
- The ability to interface with other IT security systems
- Settings to let the user allow automated response
- Data storage for historical analysis plus analytical tools in the dashboard
- Attack protection for the IPS’s own processes and logs
- A free, demo, trial, or money-back guarantee
- Value for money
1. ThreatLocker (GET DEMO)
ThreatLocker is a data protection package rather than an intrusion prevention system. The service disables all applications by default and blocks access to data files.
Key Features:
- Blocks Untrusted Software: The tool will deny all the apps, software, and scripts that look malicious, including ransomware.
- Dynamic Controlling: It includes a host-based firewall, which uses automatic ACL to provide dynamic controls and access to users.
- Ring-Fencing Apps: The tool prevents the installation of unauthorized tools and other exploitation of services.
- Guaranteed 24/7 Support: It provides the best support in the industry within 60 seconds, by an expert team to resolve the issue instantly.
Threat Locker prevents the damage that intruders can implement by completely disabling every piece of software on all endpoints by default. This blocks ransomware and the utilities that intruders like to use. The system administrator then approves selected applications – paying attention to only allow those that have access controls.
The system administrator implements whitelisting. This means that listed applications are allowed to run. The ThreatLocker tactic means that it doesn’t matter if users install unauthorized software or if hackers sneak malware onto endpoints. Those programs will never run. They are just dead files of code.
The system administrator needs to limit authorized applications to those that have access controls. The whitelisted system can be given access to data files. In short, the ThreatLocker system ensures that there is no other way for anyone to get access to data.
Who is it recommended for?
Threat Locker provides an alternative philosophy to defense against intruders and malware – it doesn’t matter who or what gets onto your endpoints because they will be blocked from doing anything. If you follow this strategy you need to pay close attention to access rights management for approved software.
Pros:
- Application Control: You can control and decide which software is allowed to run on your computer to reduce the risk of malicious programs causing harm.
- Privileged Access Management: It allows limiting access to sensitive data to prevent chances of unauthorized changes and data breaches.
- Storage Access Control: The tool allows you to manage storage access so you can be sure only authorized users access your specific files or folders.
- Prevents Software Installation and Malware: It allows users to stop the installation of maliciously installing harmful software.
Cons:
- May Consume More Resources: Many users find that running ThreatLocker alongside other software causes an increase in CPU or memory usage and slows down the system.
ThreatLocker is a SaaS package. There isn’t a free trial for this package but you can get a demo.
2. ManageEngine Endpoint DLP Plus (FREE TRIAL)
ManageEngine Endpoint DLP Plus detects sensitive data and then blocks access to the files that contain it.
Key Features:
- Granular Settings: With granular settings, users can set custom protocols for who can access data and transfer.
- Report Scheduling: Users can schedule reports to receive instant prompts for false positives.
- Robust Data Classification: It has DLP software, which checks and categorizes sensitive data separately.
- Optimal Cloud Upload Protection: It protects file transfers and uploads while monitoring browsers and third-party services across the network.
ManageEngine Endpoint DLP Plus is a package of data protection measures that also provides insider threat detection and intruder prevention. The package identifies sensitive data and categorizes it. The tool then controls how those data sources are handled, particularly for movements through USB sticks, printers, or email systems.
If any intruder wants to steal data on a system that is protected by Endpoint DLP Plus, the only option is to hijack a user account. This is because the only way to access data is through a designated trusted application, which is guarded by access rights credentials. Suspicious access attempts through these applications trigger deeper scrutiny of that user account’s activities. This could be to track an insider threat or identify a stolen account.
The tool also controls file movements to USB devices, print queues, email systems, and cloud upload facilities.
Who is it recommended for?
This tool is important for businesses that need to provide reporting for compliance with data protection standards. It is available in a free edition, which is limited to monitoring 25 endpoints, larger businesses will need to go for the paid package. The software runs on Windows Server and it can manage data on multiple sites.
Pros:
- User-Friendly Reports and Alerts: It creates intuitive reports and actionable insights to update the admin instantly regarding cyber health.
- Future-Proof DLP Policies: These include future-proof DLP policies that prevent data loss when the network is changed.
- Robust Device Controlling: Users can restrict USB and other external devices from copying and transferring data.
- Safe Email Collaboration: It monitors and controls sensitive email attachments and makes sure the data is sent via trusted domains only.
Cons:
- Difficult to Understand Editions: Some users faced difficulty in understanding different editions; hence, it caused confusion in using specific features.
Endpoint DLP Plus is a software package for Windows Server. There is a Free Edition to manage data on up to 25 computers. The paid version is called the Professional Edition and you can get it on a 30-day free trial. If you decide not to buy at the end of the trial, the package switches over to the Free Edition.
3. CrowdStrike Falcon XDR
CrowdStrike Falcon XDR is an endpoint detection and response system with added interaction with third-party security tools. The system uses security orchestration, automation, and response (SOAR) to improve both threat hunting and threat mitigation.
Key Features:
- Full Spectrum Visibility: Users can see all the data from complex threats and cross-domain data with integrated XDR.
- Rapid Responsive: It monitors complex and repetitive tasks and has a real time response feature to respond instantly from a remote location.
- Industry Leading Threat Intel: This tool comes with inbuilt world-class threat intelligence to understand the threat and goal behind it.
- AI-powered Protection: It has integrated AI-machine learning to stop users of particular skill levels from data breaching.
CrowdStrike Falcon XDR is a hybrid solution that focuses on endpoint protection. This strategy identifies both human and software-based malicious activity. Each endpoint has a next-gen AV unit installed on it, which also uploads reports to a cloud-based coordinator. The cloud system receives a threat intelligence field and collates reports from all endpoints, looking for threats.
CrowdStrike Falcon is a cloud platform of security modules and the XDR builds on a couple of other products on the SaaS system. The first of these is an endpoint protection system called CrowdStrike Falcon Prevent – a next-generation anti-virus. The Prevent tool installs on each endpoint. There are versions of this system for Windows, macOS, and Linux. This system is able to continue protecting endpoints even when the network is down.
The next layer up in the XDR solution is Falcon Insight. This is an endpoint detection and response (EDR) system that coordinates the activity of each Falcon Prevent installation in the enterprise. This gives a system-wide view and creates a private threat intelligence network. The cloud module of Falcon Insight receives activity data from each Falcon Prevent instance, pools these feeds, and scans through for indicators of compromise (IoCs). If a threat is detected, Insight sends back remediation instructions to the Prevent units.
Who is it recommended for?
This XDR system creates a private threat intelligence network. The central system can communicate with endpoint units to implement remediation for discovered threats. An attack on one endpoint triggered hardening advice to all other devices on the networks. The endpoint unit can continue to protect the device if it is isolated from the network.
Pros:
- Next-Gen Antivirus Protection: It offers robust defense against wide categories of malware threats, including viruses, ransomware, and Trojans.
- Greater Visibility with USB Device Control: It gives a comprehensive view and insight into USB devices connected to your system.
- Simplified Host Firewall Management: This makes it easier to configure and manage host firewalls across your network.
- Automated Threat Intelligence: This tool utilizes advanced algorithms and real-time threat intelligence to identify cyber threats efficiently.
Cons:
- Complexity for Non-Technical Users: Advanced features and configurations may require a certain level of technical expertise to understand and implement effectively.
Falcon XDR adds on SOAR, which means that it can collect event data from third-party tools and unprotected devices, such as switches and routers that don’t have a Falcon Prevent service available. The system is also able to send instructions to non-Falcon products, such as firewalls. Start a 15-day free trial.
4. Datadog Real-time Threat Monitoring
Datadog’s Real-time Threat Monitoring is part of its network monitoring system which includes a built-in threat detection platform. Datadog is a cloud-based service that is delivered in modules to cover network and device monitoring, applications monitoring, and web performance monitoring.
Key Features:
- End-to-End Visibility: It checks for all layers in your cloud environment to detect suspicious and intrusion.
- Threat and Misconfiguration Detections: It detects anomalies, threats, and any misconfigurations done by unauthorized persons.
- Up to 900 Plus Detection Rules and 700 Integrations: You can get deep insights as this tool supports up to 700 plus vendor integrations.
- Low Maintenance: You can easily detect threats by easily filtering signals based on their severity.
Why do we recommend it?
Datadog Real-time Threat Monitoring is provided by a Cloud SIEM module on the Datadog platform. This tool can receive logs from all devices on your network and search through them for signs of intrusion. You can set up rules that provide responses to block traffic from specific sources or suspend suspicious user accounts.
The security features of the network traffic monitor are based on Threat Detection Rules. These are supplied, but it is possible to create new rules. They establish a pattern of traffic that the system looks out for and if one of the combinations of events that a rule describes gets spotted, the service triggers an alert. The service also includes Security Rules, which are similar to Threat Detection Rules but they specify searches in several different data sources.
Who is it recommended for?
The Datadog system is priced per GB of processed data and it is a cloud platform, which doesn’t take up on-site resources, so it is suitable for businesses of any size. All businesses need to implement intrusion detection and so this cloud service is a necessary purchase for small businesses just as much as for large organizations.
Pros:
- Detailed Observability: You can analyze and observe workload, app logs, infrastructure, and various other data metrics.
- Proactive Scanning: The tool continuously scans various cloud accounts, hosts, and other containers of the organization to maintain security.
- Gives Third-Party Alerts: The tool instantly notifies you of third-party integrations or other access.
- Easy and Safe Collaboration: Users can easily collaborate with multiple teams with the help of remediation tools and easy integration.
Cons:
- Complex Log Ingestion: Some users find the log analytics process more difficult as they were able to send logs but difficulty in analyzing.
The Security Monitoring service is an add-on to the standard Infrastructure Monitoring or Network Performance Monitoring modules of Datadog and it is priced per GB of analyzed data. Datadog offers a 14-day free trial of the Security Monitoring service.
5. Splunk
Splunk is a network traffic analyzer that has intrusion detection and IPS capabilities.
Key Features:
- IT Modernization: Splunk helps businesses modernize their IT operations by providing real-time insights into their IT infrastructure.
- AI Threat Detection: Users can analyze huge amounts of data in real-time and identify potential security threats, anomalies, and suspicious activities across IT environments.
- Solve Cloud-Native Problems: Users can monitor across cloud-native applications, microservices, containers, and orchestration platforms.
- Cloud Visibility: It allows collecting and analyzing data from various cloud platforms, including AWS, Azure, and Google Cloud.
Why do we recommend it?
Splunk is a data processor that can be put to any data analysis role but it is particularly useful for log analysis. You can create your own intrusion detection system with this tool or buy the pre-written Splunk Enterprise Security to do the job for you. This system is able to shut down detected threats automatically.
There are two editions of Splunk:
Splunk Enterprise runs on Windows and Linux while Splunk Cloud is a Software-as-a-Service (SaaS) package. Both versions of Splunk can provide IPS functions.The detection system operates both on network traffic and on log files. The detection method searches for anomalies, which are patterns of unexpected behavior.
Who is it recommended for?
Splunk is a flexible tool but small businesses might not be able to get the full potential of this system. The ideal buyer of this system is a large business that has expert network and security specialists on the payroll. The free versions of this tool are no longer available.
Pros:
- Find and Fix Threats: It is the perfect tool for big businesses that can’t compromise on server downtime.
- High-Automation: The automation techniques help users to get quick information to work on the issues instantly.
- Get Maximum Insights: It gives maximum insights and data by analyzing use cases and every cloud platform.
- Easy Restoration Service: You can easily restore critical services after threat detection and get back to work for maximum productivity.
Cons:
- Long Implementation Process: Many users faced trouble in configuration and integration of tools while using it, especially from non-technical backgrounds.
A higher level of security can be gained by opting for the Splunk Enterprise Security add-on. This is available on a seven-day free trial. This module enhances the anomaly detection rules with AI and includes more executable actions for intrusion remediation.
6. SolarWinds Security Event Manager
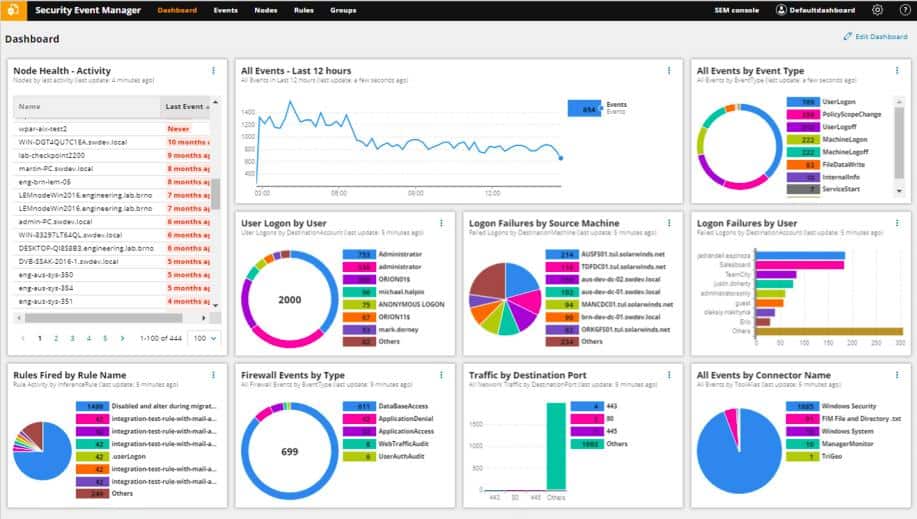
The SolarWinds Security Event Manager controls access to log files, as the name suggests. However, the tool also has network monitoring capabilities. The software package doesn’t include a network monitoring facility, but you can add this capability by using the free tool, Snort for network data gathering. This setup gives you two perspectives on intrusion. There are two categories of detection strategies used by IDSs: network-based and host-based.
Key Features:
- User Activity Monitoring: This tool tracks user activity to detect malicious activities like secret login and log off and much more.
- File Integrity: It is involved with file protection to prevent file loss, theft, and other malware issues like file corruption due to viruses.
- USB Security Analyzer: The tool also protects business data by installing a USB defender to protect USB devices as well.
- Firewall Log Analysis: You can make custom rules for your firewall management to track and protect network, application, database, and firewall events.
SolarWinds Security Event Manager is an on-premises log manager and SIEM system. This tool supplies automated searches for signs of intrusion and also provides opportunities for manual and custom-written repeated searches of log data. The logs are collected from all sources on your system including operating systems, applications, and network devices.
A host-based intrusion detection system examines the records contained in log files; the network-based system detects events in live data.
The instructions to detect signs of intrusion are included with the SolarWinds software package – these are called event correlation rules. You can choose to leave the system to just detect intrusion and block threats manually. You can also activate the IPS functions of the SolarWinds Security Event Manager to get threat remediation performed automatically.
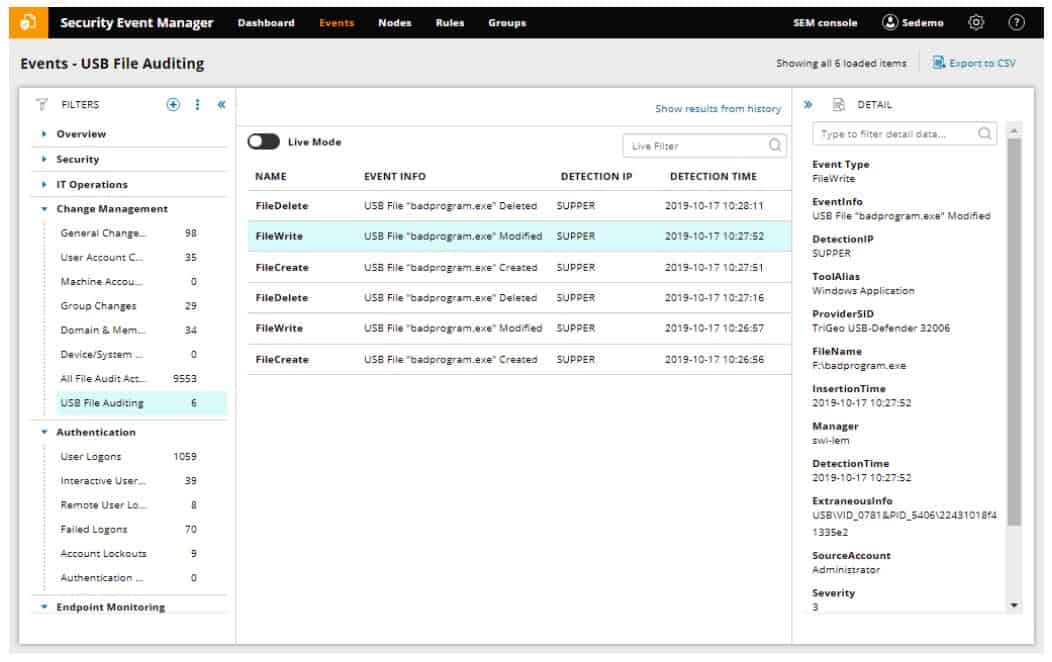
The IPS section of the SolarWinds Security Event Manager implements actions when threats are detected. These workflows are called Active Responses. A response can be linked to a specific alert. For example, the tool can write to firewall tables to block network access to an IP address that has been identified as performing suspicious acts on the network. You can also suspend user accounts, stop or start processes, and shut down hardware or the entire system.
The SolarWinds Security Event Manager can only be installed on Windows Server. However, its data sources are not limited to Windows logs – it can also gather threat information from Unix and Linux systems connected to host Windows systems over the network.
Who is it recommended for?
You need to have a Windows Server computer to host the software for SolarWinds Security Event Manager, so if all of your servers are running Linxc, you won’t be able to use this software. This tool has a high throughput capacity and so is designed for use by large businesses.
Pros:
- 24/7 Security Event Manager: The tool has a security event manager that keeps an eye on the events and responds to critical activities around the clock.
- Intuitive and Easy to Use: The tool gives out-of-the-box data with the use of a log that can be easily understood by a person with minimal experience.
- Alarm Notification for DDOS Attacks: It instantly gives alarm notifications for DDOS attacks for several window servers.
- Secures Sensitive USB Information: This tool sends an instant email to the admin in case someone breaks the custom rule or shares sensitive information via USB.
Cons:
- Behavior Analytics: Many users faced issues in behavior analysis of users when analyzing across multiple servers.
You can get a 30-day free trial of the SolarWinds Security Event Manager to test it for yourself.
7. Sagan
Sagan is a free intrusion detection software system that has script execution capabilities. The facility to connect actions to alerts makes this an IPS.
Key Features:
- Multi-Threaded Architecture: This tool is lightweight and has multi-threaded architecture; users can use CPUs for real-time log processing.
- Tracks Geographical Locations: Users can track data based on geographical locations to identify logins from suspicious locations and VPNs.
- Custom Blacklist: Users can create a custom blacklist to block certain websites, usernames, IP addresses, emails, and much more.
- Automated Responses: The tool sends automated responses to the admin when it detects any threat or flag events.
Why do we recommend it?
Sagan is a free, open-source project that provides a host-based intrusion detection system that has response automation features, making it an IPS. This package is highly respected and is one of the longest-running HIDS available today. The fact that it is a free tool means that it doesn’t come with professional support and its designers didn’t prioritize ease of use, so you need technical skills to use it.
The main detection methods of Sagan involve the monitoring of log files, which means that this is a host-based intrusion detection system. If you also install Snort and feed output from that packet sniffer into Sagan, you will also get network-based detection facilities from this tool. Alternatively, you can feed network data gathered with Zeek (formerly Bro) or Suricata into the tool. Sagan can also exchange data with other Snort-compatible tools, including Snorby, Squil, Anaval, and BASE.
Who is it recommended for?
This tool is a great solution for businesses of all sizes because it is free and it is also reliable. Large businesses will need to have a team of technical, and security specialists to get the best out of this tool. It can’t run on Windows but can collect data from that operating system across the network.
Pros:
- Free to Use: It is open-source software and suitable for business. It is also compatible with data collected through snort.
- Multiple OS Compatibility: This tool can be installed on Linux, Mac OS, and Unix.
- Firewall Protection: You can ban specific IPs with the help of a log analysis tool and IP locator to protect your organization’s firewall.
Cons:
- Complex Installation Process: You might require technical knowledge and other skills to set up and install this tool.
Sagan installs on Unix, Linux, and Mac OS. However, it is also able to pick up event messages from connected Windows systems. Extra features include IP address location tracing and distributed processing.
8. OSSEC
OSSEC is a very popular IPS system. Its detection methodologies are based on examining log files, which makes it a host-based intrusion detection system. The name of this tool stands for ‘Open Source HIDS Security’ (despite the lack of an ‘H’ there).
Key Features:
- Open Source HIDS: Users can configure and add custom rules and scripts according to their security needs.
- Active Response: Users can use multiple mechanisms like firewall policies, third-party integration, and much more to take quick actions on real-time attacks.
- File integrity monitoring: This tool keeps forensic copies of files. Users can maintain file integrity and detect changes.
- System Inventory: The tool collects and monitors system information like what software and hardware are installed and all other information.
Why do we recommend it?
OSSEC is an open-source HIDS that has been available for free since 2008. It is a little more user-friendly than Sagan and there is an improved version, called OSSEC+ available for free. The OSSEC+ system bases its threat detection on log file searches and it includes machine learning for more accurate anomaly detection.
The fact that this is an open-source project is great because it also means that the software is free to use. Despite being open-source, OSSEC is actually owned by a company: Trend Micro. The downside of using free software is that you don’t get support. The tool is widely used and the OSSEC user community is a great place to get tips and tricks on using the system. However, if you don’t want to risk relying on amateur advice for your company software, you can buy a professional support package from Trend Micro.
The detection rules of OSSEC are called ‘policies.’ You can write your own monitoring policies or get packs of them for free from the user community. It is also possible to specify actions that should be implemented automatically when specific warnings arise.
Who is it recommended for?
Small and mid-sized businesses will find OSSEC+ easy to use but large corporations that require professional support for all their software should look at the paid version, which is called Atomic OSSEC. All the OSSEC versions run on all of the major operating systems and can also be installed on cloud platforms.
Pros:
- Multi-Platform Compatibility: Due to its multi-compatibility, it can be easily used on any platform.
- Support from Active Community: It has a huge active community to help with configuration and other issues.
- Customizable with Detection Rule Language: Users can tailor OSSEC to their specific security needs by crafting detection rules that match their environment and threat landscape
Cons:
- Upgrade System: Most of the users find the upgrade system very difficult because of disappearing old rules.
OSSEC runs on Unix, Linux, Mac OS, and Windows. There is no front end for this tool, but you can interface it with Kibana or Graylog. Visit their downloads page.
See also: The Best HIDS Tools
9. Trellix XDR Platform
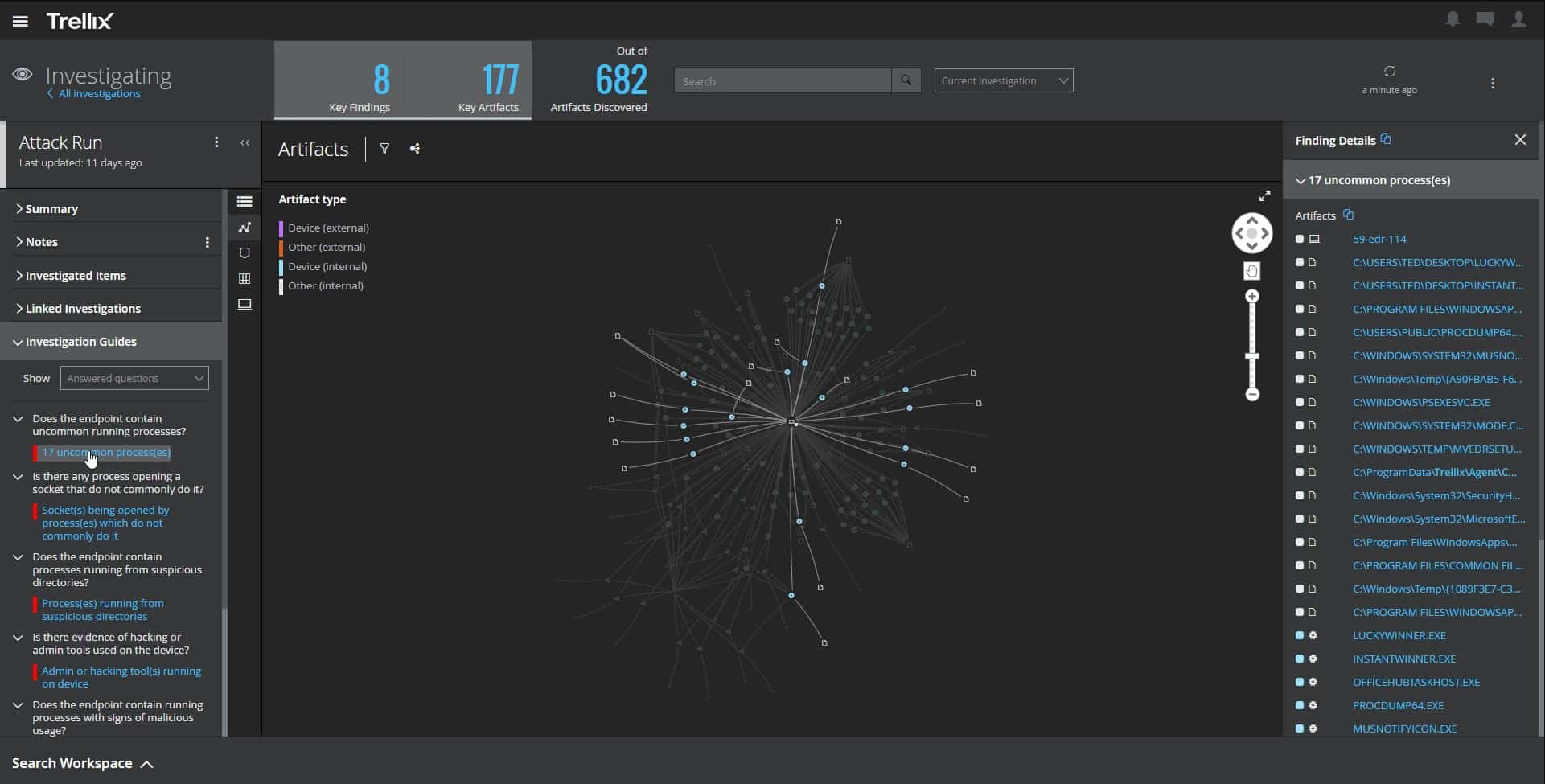
The Trellix XDR Platform detects and blocks intrusion. It also kills and removes malware. This is an AI-based service that actually improves its accuracy over its service life. This is because the exact nature of regular behavior is a little different in every organization and the AI system learns those characteristics as it works.
Key Features:
- Multi-Vendor Detection: With the multi-vendor detection feature, you can identify threats and anomalies from various security vendors and sources.
- Open Integrations: Users can integrate with up to 1000 plus third-party sources and platforms to get better insights.
- Security Controls: Trellix provides a range of security controls designed to protect against cyber threats and enforce security policies.
- Insider Threat Protection: Trellix used advanced analytics and machine learning algorithms to detect potential insider threats.
Why do we recommend it?
The Trellix XDR Platform is a good choice for an IPS package because it is a flexible threat detection system that looks for unusual activity rather than relying on a database of characteristics. This system will catch all forms of malicious human activity and malware, blocking those attacks automatically.
Every action on a company system requires a user account – or at least it should. Therefore, no intruder is going to get in without stealing account credentials. Traditional cybersecurity systems ignore the actions of users but those accounts could easily be in use by an intruder. Thus, Trellix gives no one a pass and every account is subject to scrutiny.
The software records all the actions of each user and generates a baseline of regular behavior. If the activity of an account changes for the standard pattern, Trellix pays closer attention. Speedy confirmation of unusual activity raises an alert and automated remediation kicks in. This strategy takes care of malware as quickly as it shuts down intrusion. So, it is a universal protection system and it includes network scanning.
Who is it recommended for?
This package is ideal for mid-sized businesses and large organizations. The service is too expensive for small businesses. Any company that needs an IPS – which is just about every company – should draw up a shortlist of products such as Trellix XDR and give them a head-to-head comparison.
Pros:
- Adaptive Threat Protection: With adaptive threat protection, users can adjust their defenses based on evolving threats and attack patterns.
- Web Control Features: It has web control features that allow to restrict access to harmful and non-business related websites.
- Firewall: The firewall feature helps prevent unauthorized access to the network, filters incoming and outgoing traffic, and blocks malicious connections.
- High Severity Alerts: You can prioritize the critical threats and take immediate action based on the severity of the issues.
Cons:
- Unnecessary Notifications: Users find unnecessary notifications that take up their RAM storage in the system.
You can assess the Trellix XDR Platform by requesting a demo.
10. OpenWIPS-ng
If you specifically need an IPS for wireless systems, you should give OpenWIPS-ng a try. This is a free tool that will detect intrusion and allow you to set up automatic responses.
Key Features:
- Open Source: OpenWIPS-ng is one of the effective open source IPS software that works on sensors for delivering data protection.
- Scans Wireless Channels: Users can identify nearby access points, clients, and potential threats.
- Intrusion Detections: OpenWIPS-ng can detect unauthorized access attempts, rogue devices, and other suspicious activities on wireless networks.
Why do we recommend it?
OpenWIPS-ng is a unique tool because it is a free intrusion prevention system for wireless networks – WIPS stands for Wireless Intrusion Prevention System. The tool isn’t very easy to use because it doesn’t have a GUI front end. However, it is able to block malicious activity, which makes this system worth the effort to master.
OpenWIPS-ng is an open-source project. The software can only be run on Linux. The key element of the tool is a wireless packet sniffer. The sniffer element is a sensor module, which works both as a data gatherer and a transmitter of solutions to block intrusion. This is a very competent tool because it was designed by the same people that wrote Aircrack-NG, which is well-known as a hacker tool.
Who is it recommended for?
OpenWIPS-ng is only available for Linux, so if all of your endpoints run Windows, you won’t be able to use this tool. There is no technical support and the tool’s user manual is non-existent. However, you will reap the benefits of its protection if your business relies on wireless networks.
Pros:
- Logs and Alerts: It has a server that collects data from all sensors to analyze related to the attacks.
- Intuitive GUI: It has a user-friendly interface to manage and display information regarding threats on wireless networks.
- Detects Intruders: OpenWIPS-ng can identify unauthorized users or devices that are trying to connect to the network without proper authorization.
- Boot-Off Intruders: Admins can take specific action and respond to disconnect with unauthorized access or device.
Cons:
- Works only on Linux: This tool can only be used on Linux OS, and you need a proper command line system to operate it.
Other elements of the tool are a server program, which runs the detection rules, and an interface. You can see wifi network information and potential problems on the dashboard. You can also set actions to kick in automatically when an intrusion is detected.
11. Fail2Ban
Fail2Ban is a lightweight IPS option. This free tool detects intrusion by host-based methods, which means that it examines log files for signs of unauthorized activities.
Key Features:
- Log Monitoring and Parsing: It regularly checks system log files created by SSH, web servers, and mail servers to analyze and look for patterns that seem to be malicious activity.
- Dynamic Firewall Rules: In case of any suspicious behavior, you can modify your firewall rules to block specific IP addresses.
- Multi-Protocol Support: Users can protect SSH servers by using various protocols such as FTP, HTTP, and much more.
- Reporting and Notification: The admin can configure this tool to receive email notifications when any blocked IP or security threats are detected.
Why do we recommend it?
Fail2Ban is a free HIDS that is able to send blocking instructions to firewalls if it detects suspicious activity, which makes it an IPS. This system scans log files and identifies activity per IP address. This system focuses on external threats, so malicious actions by insiders represent a blind spot.
Among the automated responses that the tool can implement is an IP address ban. These bans usually only last a few minutes, but you can adjust the blocking period in the utility’s dashboard. The detection rules are called ‘filters’ and you can associate a remediation action with each of them. That combination of a filter and an action is called a ‘jail’.
Who is it recommended for?
Fail2ban isn’t very easy to use and it isn’t available for Windows, so it is a close competitor to Suricata. Both of those free HIDS tools are at a disadvantage when compared to OSSEC+, which has a better user interface and can run on Windows and cloud platforms.
Pros:
- Automation: It automatically analyzes logs and applies firewall rules according to threat and security concerns; hence, automation makes it time-saving.
- Flexible Jail Creation: Users can create customized jails by combining filters with actions to manage other security incidents.
- Fast Log Scanning: It detects suspicious activities such as repeated login failures or unauthorized access attempts by the fast scanning process.
Cons:
- Only for Linux: This tool doesn’t work with IPv6, and some users noticed a weak server authentication policy.
Fail2Ban can be installed on Unix, Linux, and Mac OS.
12. Zeek
Zeek (formerly known as Bro until 2019) is another great free IPS. This software installs on Linux, Unix, and Mac OS. Zeek uses network-based intrusion detection methods. While tracking the network for malicious activity, Zeek also gives you statistics on the performance of your network devices and traffic analysis.
Key Features:
- Traffic Inspection: Zeek analyzes data packets passing through a network, examining their contents to identify patterns, anomalies, and potential security threats.
- Attack Detection: It will prompt an alert in real-time when any malicious behavior is detected.
- Log Recording: The tool records detailed network activity, such as the attacker’s source and destination IP addresses, protocols, and data payloads.
- Distributed Analysis: Users can deploy this tool on distributed environments for more efficient analysis of network traffic across large and complex networks.
Why do we recommend it?
Zeek is a free open-source network-based intrusion detection system (NIDS) that has been running for 25. It used to be called Bro and it compliments OSSEC, Fail2Ban, and Sagan. The tool can be set up to implement automated responses when it detects suspicious traffic, so it is an IPS.
The detection rules of Zeek operate at the Application Layer, which means that it is able to detect signatures across network packets. Zeek also has a database of anomaly-related detection rules. The detection stage of Zeek’s work is conducted by the ‘event engine.’ This writes packets and suspicious events to file. Policy scripts search through the stored records for signs of intruder activity. You can write your own policy scripts, but they are also included with the Zeek software.
Who is it recommended for?
As it is free, Zeek will appeal to SMBs on tight budgets. Larger organizations with money to spend would probably be better off with the Datadog system on this list. The interface for the tool is a little dated but it is better than having to rely on the command line.
Pros:
- Gives Well-Structured Data: It has its own log parsing tool, and you can also integrate Zeek with Splunk and other relevant tools.
- Distributed Monitoring System: It is scalable up to 100 G networks and has load balancing tools to record the packet performance across high-volume networks.
- Vibrant Community: It has a well-formed community that often posts scripts to detect vulnerabilities to spread awareness.
- Respond Actively: You can ensure zero attack day as this tool uses traditional signature-based detection.
Cons:
- Lack of Built-in Threat Intelligence: You can’t use Snort and other rules for intelligent threat detection.
As well as looking at network traffic, Zeek will keep an eye on device configurations. Network anomalies and irregular behavior of network devices are tracked through the monitoring of SNMP traps. As well as regular network traffic, Zeek pays attention to HTTP, DNS, and FTP activity. The tool will also alert you if it detects port scanning, which is a hacker method used to gain unauthorized access to a network.
Choosing an Intrusion Prevention System Tool
When you read through the definitions of the IPS tools in our list, your first task will be to narrow down your selection according to the operating system of the server on which you intend to install your security software.
Remember, these solutions do not replace firewalls and antivirus software – they provide protection in areas these traditional system security methods cannot watch.
Your budget will be another deciding factor. Most of the tools on this list are free to use.
However, the risks of being sued if hackers get hold of the customer, supplier, and employee data stored on your company’s IT system, will lose your company a lot of money. In that context, the cost of paying for an intrusion prevention system is not that great.
Make an audit of the skills that you have onsite. If you don’t have any staff that could handle the technical task of setting up detection rules, then you would probably be better off selecting a tool that is professionally supported.
Do you currently run an intrusion prevention system? Which do you use? Are you thinking of switching to a different IPS? Leave a comment in the Comments section below to share your experience with the community.
IPS Software Tools FAQs
How is an IPS different from a firewall?
A firewall sits at the boundary of a system – either a network or an individual computer – while an IPS examines packets that travel on the network. One of the blocking strategies that an IPS can implement is to update the rules of a firewall to block access to a suspicious IP address.
Which is better, IDS or IPS?
An intrusion detection system seeks out anomalous behavior and notifies the network administrator when suspicious activity is detected. An intrusion prevention system automatically triggers remediation workflows to block suspicious activity. The decision over which is better depends on personal preference. Do you want to be given the choice to decide whether to take action or do you want that decision to be made for you?
Can an IPS prevent a DDoS attack?
IPS services aren’t suited to defense against DDoS attacks. This is because a DDoS strategy never makes it onto the network where IPSs operate. A DDoS attack sends a flood of malformed connection requests without any intention of ever making a connection. Edge services are a more appropriate mechanism for absorbing DDoS traffic.