Network services seem to suffer from continuous growth in demand. As soon as you expand the bandwidth available to the users, those limits get hit again by ever-expanding applications. In fact, network bandwidth is one area of your network where money spent on software will create more capacity than money spent on hardware. When you have an endless budget, the immediate answer to demand for better network performance is to simply upgrade the cabling and buy in more switches.
Accurate bandwidth monitoring and network management systems enable you to automatically reallocate resources or shape traffic. They can save you a lot of money while still improving the network availability.
Here is our list of the best network bandwidth maximization tools:
- SolarWinds Network Bandwidth Analyzer Pack (FREE TRIAL) A bundles offered by SolarWinds that combines some of their most successful monitoring software. These tools integrate to create cross-modular utilities and all run on Windows Server. Download a 30-day free trial.
- SolarWinds Engineer’s Toolset (FREE TRIAL) A pack of more than 60 tools to monitor and analyze all aspects of network performance. Download the 14-day free trial.
- Site24x7 Network Bandwidth Monitoring (FREE TRIAL) This SaaS service monitors network traffic through the use of flow protocols.This is a cloud-based system. Start a 30-day free trial.
- Paessler PRTG (FREE TRIAL) Three-in-one network, server, and application management system with traffic analysis features. Runs on Windows Server. Start a 30-day free trial.
- ManageEngine OpManager with Network Traffic Analysis and OpUtils A combination of ManageEngine tools that will enhance your traffic analysis efforts. Runs on Windows Server and Linux.
- ManageEngine OpManager Plus A bundle of ManageEngine network monitoring, management, and analysis tools. Runs on Windows Server and Linux.
- Progress WhatsUp Gold with Network Traffic Analysis and IP Address Manager A network monitor that can be enhanced by add-ons. Installs on Windows Server.
Most network administrators find that certain applications will keep expanding traffic while there is spare capacity. In those cases, unless that software is exceptionally unique, the most cost-effective solution is the simplest one. To improve the network for everyone it is better to just replace that bandwidth hogger with a more efficient rival program.
How to improve network performance maximization in 10 steps
You can optimize your network bandwidth in many ways, and these are worth trying out before you reach for the catalog and buy more hardware.
Here are some of the ways to maximize your network’s performance:
- Establish a view of the network topology
- Optimize tracking and network traffic flow
- WAN optimizations with trunking and data compression
- Deploy network traffic-shaping techniques
- Present network data into management-friendly reports
- Schedule admin tasks to low traffic times
- Examine the use of cloud services
- Minimize personal use of network bandwidth
- Implement bandwidth-friendly email policies
- Implement load balancing
1. Establish a view of the network topology
The first stage in bandwidth optimization is to get a detailed picture of network traffic. No two networks are exactly the same, so you won’t get off-the-shelf advice on the best way to get better performance out of your system. As a network administrator, you already know more about the priorities of the company you work for and its core business, but you may not know what secondary traffic is clogging up the network.
So, a view of the topology of your network is important, as is an audit of the applications and protocols that use the system most. You need to track how much traffic is internal, how much communications with the outside world originate from within the network, and how much incoming traffic travels across your cables.
What are those external endpoints? Are they actually important for the business, or are company resources being consumed by personal use?
Once you get a view of the network and the busy sections that create bottlenecks, you can investigate better network topologies and tools to serve the users. When you can see exactly how and why the staff of the company uses the network, you can build a basis for efficiency recommendations and introduce traffic-shaping policies.
2. Optimize tracking and network traffic flow
With a combination of traffic views and endpoint and application activity tracking, you can see what groups of users access specific devices.
Look where most of the traffic flow occurs and then reorganize addressing scopes and network topology. The aim should be to reorganize nodes so that most traffic is contained within segments of the network, rather than forcing communication to travel all around the system.
For example, the HR department probably generates a lot of email traffic and frequently accesses the local printer. The sales, purchasing, and accounts department will routinely access the ERP and customer support needs constant access to the CRM system. These are three types of business activity that periodically intercommunicate, but the bulk of the traffic will be internal to each group. In these cases, group the resources accessed by each department within one subnetwork.
Don’t enforce a standard subnet size in each segment. You can adjust the number of available nodes in each subnetwork to suit the size of that department and allocate physical equipment to load more bandwidth in the high-traffic subnetworks. You will find that a small number of nodes generate most of your network traffic. Allocate most of the infrastructure to those endpoints and your bandwidth will be available wherever it is needed.
3. WAN optimizations with trunking and data compression
Poor connections across the internet that integrate remote sites and Cloud servers in a corporate network can impair your application delivery performance. There are steps that you can take in order to improve link reliability and speed. The quality of your internet service is a major influence on your inter-site link performance. You could consider upgrading your plan to get better performance out of your WAN.
WAN optimization could be implemented by trunking services to carry traffic to faraway sites. However, fundholders within the company may be reluctant to allow you to enter into more expensive transport contracts. The ability to gather performance data on your WAN and demonstrate that this is the performance bottleneck is an important requirement of your network monitoring tool.
There are other WAN optimization measures that you can take. Data compression is a viable solution if your WAN connection problems are related to speed rather than connection quality. The benefits of data compression increase exponentially with distance, so this solution is suitable for transmissions between sites across the internet.
The application of data compression can actually slow down network performance on LANs. This is because the processing time to compress and restore data is an overhead that can only be compensated by transfer time saving over long distances.
4. Deploy network traffic shaping techniques
Your network analysis should show some applications that use way more bandwidth than the others. You need to investigate who uses those applications, why they need them, and whether alternative applications can be used without taxing the network so much.
The policy of traffic shaping won’t make you popular because it limits the performance of the applications that a few people in the business really love using. In the interests of keeping costs down and improving the service to the rest of the organization, you will need to throttle those bandwidth hoggers.
Don’t make a personal issue out of high-traffic applications. Instead, present the board with options. They can spend X amount to expand the network just for this application, or they could authorize the bandwidth-hogging department to switch to a lighter application. If they don’t like those options, suggest a limit on the bandwidth available to that application in order to make the rest of the network run perfectly without expending any money at all.
Offer to help the bandwidth hoggers overcome the restrictions with changes in working practices. For example, if one application requires a lot of processing to compile data, and that in turn generates a flood of requests over the network, that app probably doesn’t provide live data. If the users of that hogging app are slowed down, they will be more inclined to run the compilation of data overnight, when network resources are less congested.
5. Present network data into management-friendly reports
Presentation quality is important to persuade executives to make effective decisions. Although you can get a good picture of what’s going on by reading the onscreen output of command line utilities, laymen don’t respond well to screens of unformatted data. So, getting a network monitoring system that automatically generates attractive reports and graphics will help you to communicate with non-technical decision makers.
Systems administrators often use security as a cover to lock out supervision that might expose errors. Keeping system information to yourself is also a way to enhance your status. If no one else knows what’s going on, they can’t afford to fire you. But information hoarding often backfires. If executives don’t know what’s going on the IT department, they won’t make it a priority.
Excluding executives from system information excludes system administrators. When new projects are launched, the network administrator is rarely consulted. Even if a new project could be served by existing network resources, if the network administrator is just given a series of services requests, rather than the big picture, those new demands could be served in a sub-optimal manner.
A series of new service demands results in a misshapen network. All of that can be avoided if the decision-makers are more informed about the network and its demands. Network monitoring systems that offer customized dashboards and on-demand reporting tools enable you to give informational views on the system to non-technical executives and allow them to inform themselves. This inclusion will help you gain access to decision-making and ease budget requests to expand the network bandwidth.
6. Schedule admin tasks to low traffic times
Similar to the overnight processing of heavy network traffic apps, you could lighten the load on the network by running admin tasks overnight. Backups are particularly data-intensive, and if daily backups are acceptable, then schedule them to run overnight. Of course, that policy won’t work for critical data in certain industries where live-duplication of data is necessary to ensure continuous service and prevent the loss of customer data. However, even in such situations, some backups can be performed overnight.
The end of the month is usually a very intensive time for accounting departments. The accounts staff will work late on the last few days of each month and the first day of the next month to close off the accounts. This task involves a lot of intensive calculations as they try to balance the books, and it will pull in information from a lot of databases.
The IT department has a lot of monthly tasks to perform, such as system sweeps, data cleaning, monthly cost reports, and SLA delivery reports. If you can shift your department’s processing needs to a few days before the month-end, you will be able to provide the accountants with your department’s data quicker, thus reducing data transfer loads a little. You will also clear out bandwidth demand to give the accounts department the full capacity.
You probably already have enough bandwidth for the company’s needs if you can just manage the timing of demand.
See also: Network capacity planning tutorial
7. Examine the use of cloud services
The suitability of cloud services will depend heavily on your company’s working practices. Your business might collaborate with a lot of outside companies, either for bought-in services or as a service provider. In these instances, placing all of the business’s supporting apps on the web will aid communications and remove needless traffic from your network.
A cloud configuration is very suitable for companies that employ a lot of home-based staff or use freelancers. If your staff is all based on-site, then many functions can be outsourced. Call centers don’t need to have all of their incoming calls routed over your network. Even office PABX systems can now be provided from the cloud. Keep your data backups offsite if possible. Feed gateways to the internet directly into the users or servers.
Many cloud-based services are metered and extensible. That charging model is great for any size of business because it avoids upfront infrastructure costs. When you set your own network or expand it, you will always have a period of overprovision as you account for expansion. When those capacity levels are approached, you may be reluctant to expand the equipment base of your network until all spare capacity has gone. At the point of expansion, you will be oversupplying the service demand again. A typical infrastructure lifecycle will encounter points of overcapacity and undersupply. A metered cloud service avoids these peaks in expense and troughs in network service quality.
8. Minimize personal use of network bandwidth
In the early days of broadband internet access, companies were lax about controlling the activities of each user. Office staff checked their private email on the office computer, for example. Personal use can get out of hand very quickly. Before you know it, workers install their own apps to get live stock-price updates or stream sports games while they work. You might even catch users downloading with torrents or watching porn in the office.
Cracking down on personal use of company resources will make you unpopular. This is another example of a networking decision in which executives should be involved.
Legal problems can arise from some user activity. The board must take every possible action to prevent offensive material being downloaded onto their services or supporting illegal activities, such as digital piracy. Personal use of the company network impacts productivity, so this is not a matter that just concerns the network administrator.
Infected websites are a major point of entry for malware. You need to control web access allowed to company employees. This can be implemented either by whitelisting — allowing access only to approved sites or blacklisting — blocking access to a list of sites or sites that include specific text.
Knocking out personal use of the network will free up a lot of bandwidth, especially if workers have become accustomed to streaming or downloading entertainment.
9. Implement bandwidth-friendly email policies
Attachments to emails generate a heavy load on the network. Your company needs to know why so much information is being sent. Email attachments and file transfers are obvious channels for data leakage. The data protection requirements placed upon companies require you to pay more attention to information being sent out.
Modern file management systems track copies of documents distributed from central storage. In collaborative environments, several people may contribute to the same document, or information needs to be distributed to hasten decision-making. However, preventing data distribution helps security and needn’t restrict collaboration.
Distributing copies of documents around the office uses up a lot of bandwidth. Document distribution systems send out updates to each person on a mail list every time a change is made to a central document. This is a very wasteful policy and results in a duplication of documents stored all over the network. In this scenario, your users gobble up your network bandwidth, needlessly filling up storage space and making data leaks harder to trace.
You can switch to a centralized document storage with multi-user access and file permission groups. The next phase is to ban the use of email as a medium to distribute documents. If outside parties need to be delivered information, then a link to cloud storage is a more secure method of passing limited data outside of the business. A central store can be controlled easier and if that store is in the cloud, outsiders won’t access your network and use up bandwidth to view documents.
Block incoming attachments wherever possible. Email attachments are a traditional route for malware. Blocking incoming emails with attachments will improve your network security and lower your bandwidth demands. Of course, there will always be genuine business cases where users have to receive documents electronically.
In these cases, create offsite storage space to receive documents. It can be quarantined and have intensive checks performed on files before they can be accessed through the network. Create a policy where documents from external sources are held remotely and only viewed through a browser from within the network. This will improve network security, reduce the need for file server storage space, and lower bandwidth demands.
10. Implement load balancing
If your business requires essential services to be constantly available, you likely have a lot of spare capacity in your system and already use load balancers. A load balancer can be used as an extra resource when another server overloads.
A typical example of this is with web servers. If server A’s queue is full, then divert new traffic to server B. However, that spare server doesn’t have to be there just for overflows. You could keep all of your servers active and distribute demand sequentially. Such a policy avoids all traffic being focused on one link and then suddenly switching to another link. With sequential distribution, all channels get a lowered and equal load. You reduce the bandwidth allocated to each link. When you don’t need to allocate peak load capacity to each server connection, you save money on your bandwidth provision or redistribute saved bandwidth to other areas of the company network.
If your network has a lot of traffic, then caching at the load balancers and network gateways can also free up a lot of bandwidth.
More network bandwidth troubleshooting tips
If you are still having issues and need to further troubleshoot your network bandwidth you can take a broad look at the following issues which can guide you on where to do a deep-dive:
- Encountering bandwidth issues
- Uncovering bandwidth problems
- Balancing bandwidth demand
- Dealing with bandwidth costs
Encountering bandwidth issues
Small networks are less likely to encounter problems with bandwidth utilization. This is because a smaller system with few nodes covering a limited area is easy to literally keep an eye on. Throughput issues tend to arise when networks grow in an unplanned manner.
Predicting bandwidth requirements is relatively straightforward, but response performance issues at throughput levels might be way below your bandwidth capacity. Often what seems to be a capacity limit issue is really caused by some other factor. This might be an overloaded cable serving too many endpoints, resulting in long wait times for media access. Device failure in one part of the network can also create conditions that appear as though they are caused by bandwidth limits. DNS errors and IP address duplication can result in hanging processes that clog up the network.
Uncovering bandwidth problems
When you make a serious effort to get the most out of your network’s bandwidth, you also need to address issues caused by other network problems. When your network grows beyond the distance that you can actually see, you need to employ networking tools to restore the network’s visibility.
With monitoring tools that show all the metrics of your network’s performance, you can ensure the health of network devices and rule out equipment failure as a source of traffic problems.
Collecting traffic data for every link in a network and keeping that monitor running over time will reveal where bottlenecks lie. If your bandwidth should be enough on paper but proves to be insufficient in practice, then uneven demand over time or a point of congestion is creating a bottleneck.
Balancing bandwidth demand
Switching the hours that bandwidth-consuming asks operate may be enough to maximize your bandwidth performance. If demand peaks periodically, then schedule traffic-heavy tasks for different periods of the day or, ideally, out-of-office hours. This should solve load spikes on your network.
Upon discovering one or two overloaded links, just solve that problem by moving some nodes onto a subnetwork common to them so their communications with each other do not flood the entire network and avoid the overloaded link.
If certain applications or protocols swamp the network’s bottleneck, consider switching the provision of those applications to the cloud to reduce traffic on the overloaded link.
Dealing with bandwidth costs
Removing surges in demand eliminates the traffic that pushes your bandwidth to the limits. Once you have stabilized the network and lowered peak demand below bandwidth capacity, you can start a second phase of bandwidth maximization: distribute the load across the system to reduce the current bandwidth provision.
Load balances, caches, and better-organized subnetworks drastically reduce traffic levels across your network. You probably have links and equipment currently under almost no load while other sections of your infrastructure are overloaded. Balancing out traffic flow so that all equipment is used will reduce peak throughput levels on any particular link or switch. This reduces overall bandwidth requirements and saves money.
Network bandwidth maximization tools
As you can see from the tasks outlined above, your starting point for maximizing your bandwidth is to get information on how your network performs in the moment. You need to find out where the demand for bandwidth lies, both physically and in terms of traffic types.
See also: The Best Network Traffic Monitors
A bandwidth monitoring system fulfills these needs. The complexity of the monitor that you choose depends on the size of your network and the typical traffic volumes that it carries. The list below ranges from bandwidth monitors with extensive analytical capabilities for large networks through to simpler systems that would work well for small enterprises.
The best network bandwidth maximization tools
The top end of the network management software market is dominated by a couple of providers that produce suites of network tools. To get a full picture of your network and implement solutions to maximize bandwidth, you will need a combination of these tools. Fortunately, these software houses understand the complexities of managing large networks and provide modules that fit together to create tailored solutions.
Our methodology for selecting bandwidth monitoring and network management systems
We’ve broken down our analysis for you based on these key criteria:
- Comprehensive Monitoring: Ensuring the tool provides end-to-end monitoring of network devices, traffic, and performance.
- Scalability: Assessing the ability of the tool to handle networks of varying sizes and complexities, from small businesses to large enterprises.
- Ease of Use: Evaluating the user interface and ease of setup to ensure the tool is accessible to both technical and non-technical users.
- Integration Capabilities: Checking how well the tool integrates with other systems and devices, including compatibility with multiple flow protocols and virtual environments.
- Alerting and Reporting: Reviewing the effectiveness of the alerting system and the quality of the reports generated for proactive network management and troubleshooting.
1. SolarWinds Network Bandwidth Analyzer Pack (with FREE TRIALS)
The key network traffic analysis tool of SolarWinds is its NetFlow Traffic Analyzer. However, to get the complete picture of your network’s performance, you also need the Network Performance Monitor. These two tools can be purchased together in a combination bundle, called the Network Bandwidth Analyzer Pack.
Key Features:
- NetFlow Traffic Analyzer: Analyzes network traffic to provide detailed insights into bandwidth usage.
- Network Performance Monitor: Monitors network performance and device status in real-time.
- Device Discovery and Mapping: Automatically discovers devices and maps the network topology.
Why do we recommend it?
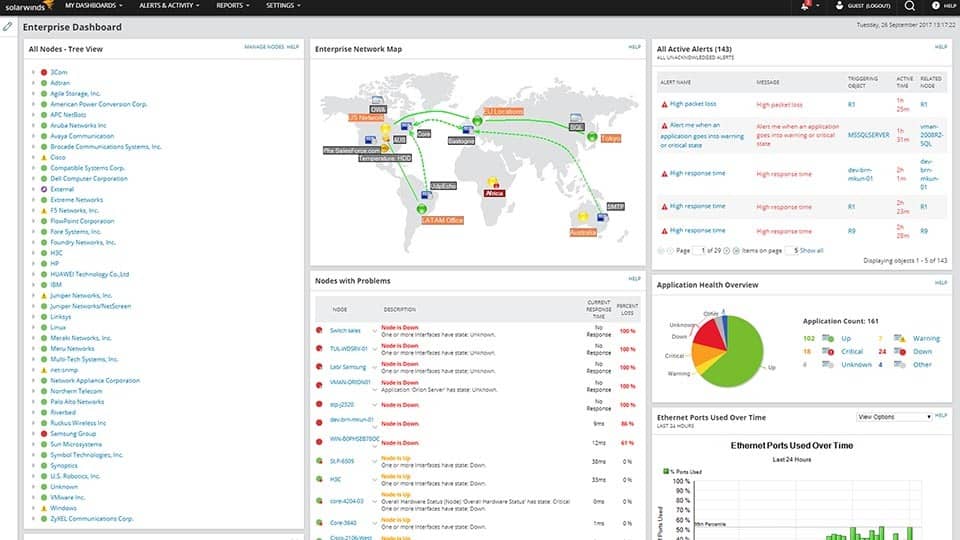
SolarWinds bundles allow network managers to cover all aspects of network monitoring and management with a series of interlocking modules. By selecting the combination of the Network Performance Monitor and the NetFlow Traffic Analyzer, you get device discovery and network topology mapping along with live device status reports and traffic volume records.
The free Flow Tool Bundle is worth adding on to any SolarWinds combo pack. This set of utilities works with NetFlow v5 and includes an interface so you can configure your Cisco routers to send NetFlow data to your collector. The other tools in the bundle are traffic simulators to help you test your network resources.
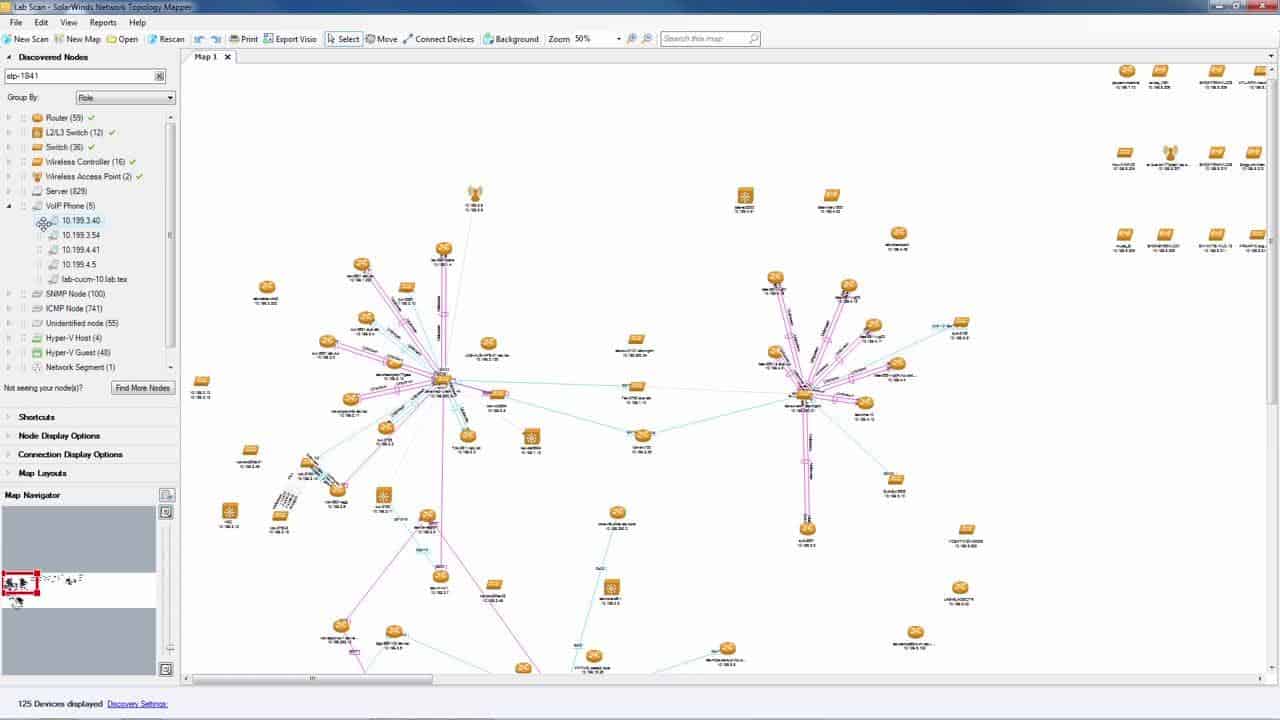
Finally, add on the Network Topology Mapper to see the physical layout of your system.
The Network Performance Monitor is the core product of SolarWinds and is necessary for your day-to-day network management tasks.
This system includes an autodiscovery capability that will trace all of the devices connected to your network and highlight the network equipment. Autodiscovery creates a starting point for bandwidth maximization.
The Network Topology Mapper will be your next port of call. This tool does exactly what it say on the tin and gives you the layout of your network. With the assistance of the mapper you can identify traffic that serves virtual environments and wifi services as well as your wired network.
Within the Network Performance Monitor is a module called NetPath. This displays a visual path of links that carry specific connections. Those links trace through to cloud services. If your network includes wireless systems, you will benefit from the Heat Maps in the Network Performance Monitor. This gives you a visual display of the signal footprints of all of your wifi routers. With this information, you can see the low signal areas and deadzones that reduce the bandwidth available to your users.
Switching between the Network Performance Monitor and the Network Topology Mapper is not a difficult task because SolarWinds built all of the tools recommended in this combination on the same platform, called Orion. When you buy several of these products, they integrate together. Enhance that integration further with an overview module, which is called the Enterprise Operations Console. It consolidates all of the data coming from multiple SolarWinds servers.
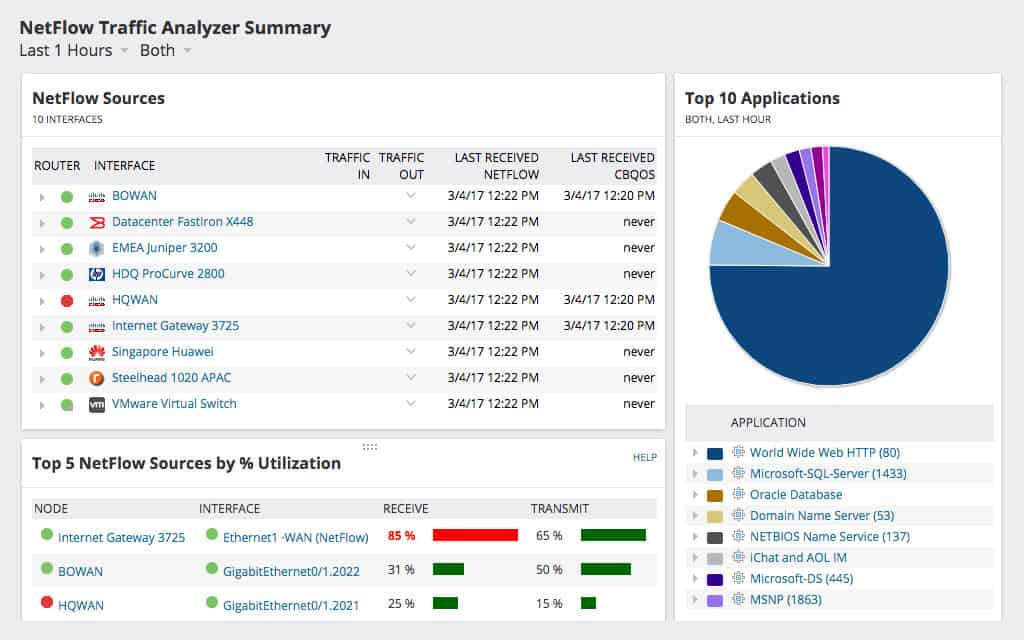
The NetFlow Traffic Analyzer element of our recommended SolarWinds combination is probably mis-titled. NetFlow is a specific messaging language used by Cisco Systems for its network equipment. This communication standard enables a monitor to pick up traffic flow information. The SolarWinds traffic Analyzer does collect NetFlow data. However, it doesn’t only communicate with NetFlow devices, which is why you should perhaps overlook the “NetFlow” in the name of this tool.
Most network administrators operate a multi-vendor policy, so you may be put off by a network tool that only works with NetFlow. However, SolarWinds also collects J-Flow data generated by Juniper Networks equipment and it works with the NetStream messaging system that Huawei equipment uses. The network analyzer also interprets the sFlow and IPFIX messaging systems, which are vendor-neutral reporting languages for networking equipment.
Those network equipment reporting languages supply key data that the NetFlow Traffic Analyzer uses to monitor bandwidth usage. This is the key module to monitor the results of maximizing bandwidth. Combine this information with the NetPath data and the Network Topology Mapper to see the points of strain on your network where you most need to apply mitigating solutions in order to improve bandwidth availability.
The NetFlow Traffic Analyzer is able to monitor the performance of internet links between sites and out to Cloud servers. This information will help you decide on improvement strategies for WAN optimization.
Part of your solution to bandwidth over-utilization may be a QoS approach. This is the reverse of throttling because it enables you to tag certain types of traffic and prioritizes its flow through network equipment. Effectively, this tactic throttles all of the other applications that haven’t been prioritized. The NetFlow Traffic Analyzer has a tracking module, that monitors the flow of prioritized protocols. You can access “before” and “after” network traffic graphs to gauge the effect of the QoS strategy.
Who is it recommended for?
These packages provide different combinations of SolarWinds tools. Each module is quite expensive so buying multiple services in combination is a big investment. This means that the main market for the combination packages from SolarWinds lies with large organizations. These packages also implement automated monitoring with alerts, which provides the only way to monitor large networks.
Pros:
- Comprehensive Monitoring: Combines performance monitoring with traffic analysis for a complete network overview.
- Real-Time Insights: Provides live status reports and traffic volume records to optimize network performance.
- Autodiscovery Feature: Automatically traces all devices on the network for efficient management.
- Versatile Utilities: Includes a free Flow Tool Bundle for configuring routers and simulating network traffic.
Cons:
- Advanced Setup: The combination of multiple tools might require a steep learning curve for initial setup.
The NetFlow Traffic Analyzer includes a section for wireless traffic analysis. This works in combination with the Network Performance Monitor WiFi features to help you maximize the availability of wireless bandwidth to your user community.
EDITOR'S CHOICE
SolarWinds Network Bandwidth Analyzer Pack is our top network monitor because it combines the powerful NetFlow Traffic Analyzer and Network Performance Monitor into one comprehensive bundle. This integration ensures that network managers can efficiently monitor traffic and device performance for a complete view of their network’s health.
By leveraging these tools, users can benefit from device discovery, network topology mapping, and real-time device status reports. This bundle also includes a free Flow Tool Bundle, which aids in configuring Cisco routers and simulating traffic for better resource management. Adding the Network Topology Mapper further enhances the system by providing a visual layout of the network.
SolarWinds Network Performance Monitor is essential for daily network management tasks, offering an autodiscovery feature that automatically traces all connected devices, ensuring that network bandwidth is optimized from the start. This holistic approach makes SolarWinds Network Bandwidth Analyzer Pack a reliable and effective solution for comprehensive network monitoring and management.
Download: Download 30-Day Free Trial
Official Site: https://www.solarwinds.com/hybrid-cloud-observability
OS: Windows Server
2. SolarWinds Engineer’s Toolset (FREE TRIAL)
The above solution is the top-of-the-line combination of network tools to help you manage your bandwidth. However, SolarWinds provides an alternative pack of utilities if you find the combo above a little pricey. The Engineer’s Toolset is a cheaper alternative to those Orion-based systems listed in the previous section. SolarWinds points out that this package can also interact with the Network Performance Monitor. The Engineer’s Toolset includes a total of sixty utilities.
Key Features:
- Response Time Monitor: Displays real-time throughput and performance of network devices.
- Switch Port Mapper: Maps and documents switch ports and connected devices.
- TraceRoute Utility: Analyzes network paths and identifies routing issues.
Why do we recommend it?
The SolarWinds Engineer’s Toolset is a bundle of more than 60 network management and troubleshooting tools. The utilities in this package allow network managers to make investigations into network issues. Examples of services within this package include investigation tools for addressing issues and network response time testers.
This enormous set of tools includes functions that shadow the capabilities of the main SolarWinds products. Picking through the list of tools in the bag, you can put together a useful suite to help you maximize network bandwidth. Start with tools that log all of your network equipment and check on their health like the Port Scanner, Switch Port Mapper, SNMP sweep, IP Network Browser, MAC Address Discovery utility, and Ping Sweep tool.
The Switch Port Mapper facility produces a report page for each switch in your network and lists its connected ports. You can see the MAC address and the allocated IP address of each device connected to each port. The Port Scanner checks the addressing ports on your routers and endpoint devices, showing which ports are open and vulnerable to hacker exploitation. Once you have all of your equipment documented, you can start maximizing your network’s bandwidth.
Real-time network performance monitors examine bandwidth performance, like the Response Time Monitor and the TraceRoute utility. The Response Time Monitor displays the throughput of selected network devices. This live report shows which parts of your infrastructure are unavailable for routing and which are performing poorly. These points of failure could explain why your users experience slowness or an inaccessible network.
The TraceRoute tool is an implementation of a standard network administration utility that you probably already know. It uses ICMP to check on the links that make up the route to a specific destination. This information is presented in a searchable GUI table, saving you from manually diagnosing paths in the command line. These tools are also very useful when analyzing connections across the internet. This ability will prove useful when you are gathering evidence for WAN optimization.
The role of IP address management is covered by the DNS Analyzer, a DNS Audit tool, the DNS Structure Analyzer, the DHCP Scope Monitor, a Subnet Calculator, and an IP address monitor. This collection is not as well integrated as the IP Address Manager in the previous section. Switching between screens to get a full IPAM service means manual steps and note-taking are needed to manage your IP address space when you opt for the Engineer’s Toolset.
Who is it recommended for?
This package is a good choice for network administrators who need more than an automated monitoring service. The theme for these tools is that they allow you to make investigations into performance issues. So, while other systems flag a problem, you would switch to this package to find out how to solve it.
Pros:
- Comprehensive Toolset: Offers a suite of over 60 tools for network management and troubleshooting.
- Device Discovery: Includes tools for discovering and documenting network devices and their statuses.
- Performance Analysis: Provides real-time performance monitoring and diagnostic tools for network issues.
- Versatile Utilities: Supports DNS and DHCP functionality verification, aiding in comprehensive network management.
Cons:
- Limited Trial Period: The trial period could be longer to allow for a more thorough evaluation.
- Manual Integration: Requires manual steps for IP address management compared to more integrated solutions.
You can string together enough information with the Engineer’s Toolset to successfully identify points of network congestion and work out where to reduce bandwidth in order to improve performance in under-supplied parts of the network. This tool runs on the Windows Server environment. Although the Engineer’s Toolset is cheaper than the Network Performance Monitor and a lot cheaper than the whole combination of tools explained in the previous section, it is not as easy to use. You can check it out yourself on a 14-day free trial.
3. Site24x7 Network Bandwidth Monitoring (FREE TRIAL)
The cloud-based Site24x7 Network Bandwidth Monitoring service is part of a SaaS platform of system monitoring and management tools. The bandwidth monitoring facility is bundled together with network device monitoring and also server, could, application, and website monitoring utilities. The Site24x7 platform installs an agent on an enrolled network to gather and upload activity data for analysis in the cloud.
Key Features:
- Cloud-Based Monitoring: Utilizes a cloud-based platform for seamless system monitoring and management.
- Multi-Protocol Support: Communicates using various flow protocols like NetFlow, IPFIX, sFlow, and more.
- Performance Alerts: Triggers alerts based on predefined performance thresholds for proactive issue resolution.
Why do we recommend it?
The Site24x7 Network Bandwidth Monitoring module extracts data from switches, noting the capacity of each interface and then tracking the demand that traffic flows place on the device. The system will raise an alert if throughput approaches full capacity. This means that technicians don’t need to watch the monitoring console all the time in order to catch evolving problems.
This monitor exploits flow protocols to extract activity data from switches. Network device manufacturers don’t all use the same flow reporting protocols and so, in order to be relevant to clients with every brand of network device, the Network Bandwidth Monitoring service is loaded with the ability to communicate in all of them. These are NetFlow, IPFIX, sFlow, J-Flow, cFlow, NetStream, and AppFlow. The tool can communicate in multiple protocols with different switches simultaneously.
The package includes a series of performance expectation thresholds that can trigger if transfer speeds drop, if packet loss or jitter increases, or if the demand on switch interfaces approaches full capacity. As well as appearing in the system dashboard, alerts are forwarded as notifications by email, SMS, voice message, or Slack post.
The Network Bandwidth Monitoring package also includes path analysis features, particularly a Ping option. This can be run on demand to text traffic statistics on a connection through the network. The results of tests can be stored for reporting and all of the metrics that the monitor gathers are stored in the cloud for historical analysis. The analytical functions of the dashboard enable technicians to implement capacity planning and design traffic shaping requirements.
Who is it recommended for?
This system is suitable for use by any size of business and it is provided in plans that include many other monitoring features. The packages are sized and priced for small businesses and larger companies are expected to add on capacity supplements to suit their system sizes. The service is hosted on cloud servers, which removes the need to maintain the software.
Pros:
- Multi-Vendor Compatibility: Supports multiple flow protocols to gather data from diverse network devices.
- Proactive Alerts: Sends notifications via email, SMS, voice message, or Slack when network stress is detected.
- Comprehensive Monitoring: Includes troubleshooting tools and capacity planning utilities for robust network management.
Cons:
- Bundled Package: Only available as part of a larger monitoring suite, not as a standalone product.
The Network Bandwidth Monitoring service is part of all of the many plans offered on the Site24x7 platform. You can examine any of those plans with a 30-day free trial.
4. Paessler PRTG Network Monitor (FREE TRIAL)
Paessler PRTG Network Monitor is a three-in-one infrastructure monitor. It covers networks, servers, and applications. The network monitoring component of the tool has two elements: a network performance manager, which checks on the health of network devices, and a network traffic analyzer. It is these network monitoring functions of PRTG that will help you to optimize your bandwidth utilization.
Key Features:
- Network Performance Manager: Monitors the health and performance of network devices.
- Network Traffic Analyzer: Analyzes network traffic using protocols like NetFlow, IPFIX, sFlow, and J-Flow.
- Customizable Sensors: Allows for the creation of custom monitoring solutions with sensor templates.
Why do we recommend it?
Paessler PRTG Network Monitor is a bundle of system monitoring tools. Paessler is clear that the aim of all the tools in the PRTG package is to monitor systems – it doesn’t include network management services. This system includes network bandwidth statistics gathering protocols, such as NetFlow, IPFIX, sFlow, and J-Flow.
The PRTG collector gathers real-time reports on network traffic using a range of network device messaging systems. These include NetFlow, sFlow, IPFIX, and jFlow. The data from these messages gets plotted in the dashboard in the form of charts. A network map compiled from SNMP data also shows color-coded statuses derived from the network traffic analyzer data gathering. The traffic data can be filtered by IP address, software, or protocol source so that you can see the origins of most of your traffic. The traffic data also gets stored to provide source material for capacity planning.
If you implement virtualization, PRTG can track which resources contribute to which VMs. You will be able to analyze the demand on each host and decide whether you need to redistribute virtual resources or add on more infrastructure to cater for upcoming increases in demand.
If you don’t have the budget for more equipment, the information provided by the network traffic monitor will enable you to prioritize traffic or limit bandwidth allocations to certain applications in order to prevent them overwhelming the network and crowding out other services.
Who is it recommended for?
This is a very flexible package because you choose how many of the units in the bundle to activate. Thus, every buyer is able to customize the package and pay only for those parts that get turned on. Small businesses that only activate 100 sensors get the system for free.
Pros:
- Comprehensive Monitoring: Ideal for businesses needing to monitor networks, applications, and servers simultaneously.
- Customizable Solutions: Highly flexible with customizable sensors and templates for popular applications and devices.
- Autodiscovery Feature: Automatically maps the network and gathers performance metrics immediately.
- Cost-Effective: Free for small businesses with up to 100 sensors activated.
Cons:
- Complex Platform: Requires time and effort to fully explore and utilize all features.
You can choose to subscribe to PRTG as an online service or you can install the software on your server. The system incorporates a series of sensors. A “sensor” is a system condition or hardware attribute. You can get Paessler PRTG for free, but that version is limited to 100 sensors. You have to pay for larger implementations, but Paessler offer a 30-day free trial to check out the system.
5. ManageEngine Tools
ManageEngine is probably the main rival to SolarWinds in the network monitoring field. Its main network management system is called OpManager. The company produces a range of other network utilities, many of which are available as add-ons for OpManager as well as standalone tools.
Key Features:
- NetFlow Analyzer: Monitors network traffic and helps optimize bandwidth usage.
- OpManager: Provides ongoing monitoring of network devices with real-time data and alerts.
- OpUtils: Combines IP Address Management with Switch Port Mapping for comprehensive network management.
Why do we recommend it?
ManageEngine tools provide an alternative to the SolarWinds stable. While SolarWinds produces just about all of its tools for Windows Server, most of ManageEngine’s systems will also run on Linux, AWS, and Azure. The menu of systems from ManageEngine includes the NetFlow Analyzer, which helps you record and improve network bandwidth performance.
The second principle tool created by ManageEngine is OpUtils. This combines the functions of an IP Address Manager with that of a Switch Port Mapper. Together with the Network Traffic Analysis add-on for OpManager, they give just enough functionality to maximize network bandwidth.
The well-planned layout lets you absorb information on a lot of different aspects of network performance at a glance. The main dashboard has a top band across it that shows miniature, color-coded charts. Each of these small graphics displays live data and acts as a link through to more detailed information.
The main purpose of OpManager is ongoing monitoring of network devices. This is not exactly the tool you need for bandwidth maximization, but it shows live data and provides alerts on important status changes. That service will help you to avert sudden bandwidth impairment that could be caused by faulty equipment.
The OpManager’s autodiscovery function will build a map of your network. OpManager represents network structures in a series of in-depth views. The basic mapping function generates a layout of the network’s topology. For WANs, that topology is overlaid on a real world map. The network’s physical layout isn’t the only map on offer. You also get an L2 map, which shows all of the network devices and all of the links that radiate to neighboring equipment.
A couple of other views available are probably better suited to non-technical staff. The first of these shows a 3D representation of the building with the network layout on each floor. The second shows a server cabinet with each of your servers positioned at the correct shelf in the rack, along with their make and model. These visualizations probably won’t solve your network bandwidth problems, but they are great presentational aids.
The OpManager network monitoring module works with virtual environments. Specifically, OpManager has special capabilities for identifying and managing VMWare, Hyper-V, and Citrix systems.
The NetFlow Analyzer improves bandwidth availability to the entire network. This reach extends across the internet to remote sites, so you can use the Analyzer for WAN optimization. With this tool, you can see any links or segments of the network that frequently hit their capacity limits. The capacity on all of the other links on the network can also be seen, identifying overprovision that could be shifted to relieve the bottlenecks.
The analyzer picks up network messages from equipment. Despite the name, it doesn’t just collect Cisco NetFlow messages. It can also detect and interpret J-Flow, NetStream, sFlow, IPFIX, cflow, FNF, and Appstream messages.
The tool can distinguish between data, voice, and video streams. If you really want to free up some bandwidth, those video streams are the ones to go for. The dashboard includes traffic shaping capabilities to implement QoS prioritization and throttling once you have identified the traffic that you want to squeeze some space out of.
NetFlow Analyzer’s capacity planning module compiles a traffic trend report based on historical data, and it can show projections of where traffic growth seems to be heading.
The NetFlow Analyzer is available as a standalone tool, so you could just install it without the others. But to really get a handle on your bandwidth usage, you need to cover a lot more factors than just bare traffic flows. To relieve bandwidth shortage, you need deeper insights to inform decisions. The Switch Port Management section of OpUtils breaks down traffic for each link and segment, tracing traffic origins to individual endpoints. This identifies specific users or devices that generate excessive traffic as well as any rogue devices or unusual activity indicating a compromised user account.
The final piece in the puzzle in the ManageEngine network bandwidth solution is the IP Address Manager. This tool is available as a standalone utility, or you can buy it as an add-on for OpManager. It is also integrated into OpUtils.
The IPAM will monitor DHCP and DNS servers and identify abandoned IP addresses on the network. This tool helps right-size each subnet and makes bandwidth available where needed. It monitors DNS entries and ensures all records include an actual live IP address. It will also look out for scope overlap between multiple DHCP servers and prevent IP address conflict. All of these issues can block up your network and make it seem as though you haven’t provided enough bandwidth. Getting your subnetworks right will reduce contention and make the most of your bandwidth by removing delays on network access per device.
All of these tools are written to the same platform, so they all integrate seamlessly. You can install ManageEngine tools on Windows Server or Linux environments. The interface can be allocated to different user groups, granting limited access to subsets of the data and controls of the dashboard to authorized users. That means you can give data access to non-technical executives and allow junior members of staff access to the monitoring system without risking damage. Each of the utilities listed in this section ship with pre-written standard reports, or you can generate your own custom reports.
You can also write custom alert conditions to notify you when bandwidth utilization thresholds are exceeded. This is useful if you want to observe the conditions that provoke excessive bandwidth usage. Alerts appear in the dashboard, color-coded by severity. You can have alerts sent by SMS or email to different members of the team according to device origin or alert type. Some actions can be configured to resolve alert conditions automatically. This helps you keep ahead of bandwidth exhaustion even when you are out of the office — you can even access the dashboard over the web from your mobile device.
The ManageEngine solution to network bandwidth maximization certainly gives you the views and controls necessary to keep on top of network availability and quality of service.
Who is it recommended for?
ManageEngine offers editions for its tools, such as the NetFlow Analyzer. That package is a standalone package and you don’t need to add it to the network performance unit, which is called OpManager. The Professional edition will monitor a single network and the Enterprise edition is for WANs.
Pros:
- Immediate Functionality: Designed to work out of the box with over 200 customizable widgets for unique dashboards and reports.
- Autodiscovery Feature: Automatically discovers, inventories, and maps new devices on the network.
- Intelligent Alerting: Uses advanced alerting to reduce false positives and prevent alert fatigue.
- Multiple Alert Channels: Supports various alerting methods including email, SMS, and webhooks.
- Seamless Integration: Integrates well with other ManageEngine products for a cohesive ecosystem.
Cons:
- Steep Learning Curve: Requires a significant time investment to fully understand and utilize all features.
You can get ManageEngine network management software on a 30-day free trial. That offer extends to all of the modules listed in this section. A free edition of OpManager lets you monitor 10 devices. The IP Address Manager can be used for free up to a maximum of 50 IP addresses. The NetFlow Analyzer can be used for free to monitor up to two interfaces.
6. ManageEngine OpManager Plus
The OpManager Plus package gives you all of the above ManageEngine modules fused together. Along with OpManager, OpUtils, and the Network Analysis Add-on, this bundle includes application and server monitoring modules, a network configuration manager, and a firewall log analyzer.
Key Features:
- Comprehensive Monitoring: Includes network, server, application, and storage monitoring.
- Network Configuration Manager: Enforces and tracks network device configurations to detect unauthorized changes.
- Firewall Log Analyzer: Analyzes firewall logs to identify issues affecting connection speeds.
Why do we recommend it?
ManageEngine OpManager Plus is one of the bundles available from ManageEngine. This package provides the OpManager unit to monitor networks and servers, plus the NetFlow Analyzer for bandwidth analysis. You also get an OIP address manager, a switch port mapper, a network configuration manager, a firewall manage,r a log analyzer, a storage monitor, and an application performance monitor.
The Network Configuration Manager feature spots sudden problems with network equipment. This module enforces the configurations of network equipment and keeps track of any changes to those setups. If an unauthorized change occurs on a network device, that alteration could quickly ripple and impair bandwidth availability. It could also indicate tampering by saboteurs, hackers, or malware.
The Applications Manager that comes bundled into the OpManager Plus package identifies specific applications on your network and how much bandwidth each uses. This visibility extends to cloud application servers, and you can identify VM environments.
The Server Manager module won’t directly sort out bandwidth problems. It identifies any server issues that may be slowing down response times, including non-bandwidth performance issues that may cloud your view of bandwidth availability. The Firewall Log Analyzer could serve a similar purpose because it can highlight drags on connection speeds that aren’t really bandwidth-related.
Who is it recommended for?
This is a big bundle and has an expectedly high price. That cost makes the bundle only affordable for large organizations. Smaller businesses will find that they might be able to get by with just a couple of the tools in this bumper package.
Pros:
- Holistic View: Monitors bandwidth consumption and alerts on configuration changes that could impact performance.
- Application-Level Insight: Tracks bandwidth and resource usage at the application level, identifying specific users consuming the most resources.
- Wide Range of Tools: Combines multiple ManageEngine modules for a comprehensive monitoring solution.
Cons:
- High Cost: The extensive features make it more suitable for large organizations with a higher budget.
- Complexity: Requires significant time to fully explore and utilize all available options and features.
The OpManager Plus system has the same front end and adaptability as the regular version of OpManager. This tool also runs on Windows Server and Linux. ManageEngine offers a 30-day free trial of OpManager Plus. As with the standard OpManager package, a free version of OpManager Plus covers up to 10 devices.
7. Progress WhatsUp Gold
Progress (formerly Ipswitch) is catching up with SolarWinds and ManageEngine. Its star product is WhatsUp Gold, a network monitor that can be expanded by integrating extra modules in the same way as the Network Performance Monitor and OpManager.
Key Features:
- Network Device Monitoring: Monitors the status and performance of network devices, both wired and wireless.
- Network Traffic Analysis: Provides insights into network traffic with support for multiple flow protocols.
- Virtual Environment Monitoring: Offers specialized monitoring for VMWare and Hyper-V virtual environments.
Why do we recommend it?
Progress WhatsUp Gold is a big rival to the SolarWinds Network Performance Monitor. This package runs on Windows Server and you get bandwidth monitoring as an add-on module. You can’t get the bandwidth monitoring unit by itself. That function relies on the device discovery features of the core module.
A suite of tools to improve network bandwidth utilization would include Network Traffic Analysis and Application Performance Monitoring modules.
WhatsUp Gold is a network performance manager that focuses on the statuses of network equipment. The system is capable of monitoring wireless networks as well as standard LANs. It can identify virtual environments that include both onsite and cloud-based configurations.
For bandwidth management, the first thing you need is a network map. The initial install of WhatsUp Gold finishes with a system sweep that discovers all of your network devices. The tool then produces a network map from this information. The network map shows how all of the devices connect together to form the entire network. Each node in the plan is a link through to a page of performance and status details about that device.
WhatsUp Gold uses SNMP messaging to keep updated statuses on each device. Although this feature is not directly connected to improving bandwidth usage, an error status on a network device will contribute to network problems. You need to rule out health of network equipment before starting bandwidth usage analysis.
The core functions that you need in your quest to maximize network bandwidth lie in the Network Traffic Monitor add-on. This utility functions as a switch port mapper because, not only will it report on network traffic, it will segment data according to protocol and application. You will be able to see which links are overloaded and which protocols are channeling all of the traffic down a hop. The visibility of the WhatsUp Gold system extends to internet links to help you with WAN optimization.
The module interprets network traffic throughput details from captured messages circulating around the system. Cisco NetFlow, NetFlow-Lite and NSEL, Juniper J-Flow, sFlow and IPFIX generate the messages. The information gleaned from them is categorized by user, protocol and application. That user identification is a result of examining the switch port origin of each message.
With this data, you can establish a baseline for network bandwidth maximization. You next have to decide on a policy to deal with excessive traffic on certain network links. The Bandwidth Capacity Planner examines current and trend usage and flows around the network. You can simulate the effects of altering the configuration of the network, moving nodes from one switch to another, and increasing line capacity on a section of cable. With this information, you can evaluate whether the solution to your bandwidth problems lies with further investment in infrastructure.
Reports on application and protocol activity may highlight an obvious cause of your congestion problems. Examples of glaring traffic problems that visibility can highlight include the timing of data backups or the allocation of output devices, such as printers to separate subnets.
WhatsUp Gold supports an alternative strategy of QoS traffic prioritizing. With this method you can ensure that vital traffic always gets through congestion points first, holding up non-essential or bandwidth guzzling applications for the benefit of the wider user community. The capacity planner can replay historic data with priority traffic tags in place. With this simulation, you can test the effectiveness of QoS prioritization.
The Flow Monitor module produces insightful reports on network capacity and time-based usage. These are essential for communicating with executives when planning for a policy to deal with bottlenecks. This is where you might decide to shift certain applications to the cloud or block the use of bandwidth-hungry applications, such as video streaming, during hours of peak demand.
Alerts built into the WhatsUp Gold traffic monitoring system notify you when capacity thresholds are reached. This lets you watch the buildup of traffic during your investigation phase. Once you understand the problem, you will be able to put solutions into place, such as caches and load balancers.
The monitor integrates Cisco NBAR classifications. NBAR is the Network-based Application Recognition list that ranks applications by importance. This information acts as a guide to identify which application traffic to prioritize if you want to take the QoS route to solving bandwidth exhaustion.
The combination of WhatsUP Gold and its Network Traffic Monitor add-on will give you insights into virtual environments. However, if your network uses VM technology heavily, you might consider investing in the Virtual Environment Monitoring add-on. This tool gives deeper analysis of virtual environments.
The monitor covers VMWare and Hyper-V implementations and offers live data on the performance of VM systems. The sensor that will interest you most in your bandwidth maximization task is the interface utilization monitor. This will show if one VM is overloading the system, or if all of the virtual endpoints in the network are evenly distributed, using acceptable amounts of bandwidth. If you rely heavily on virtualization, you need to at least rule out this system as the source of bandwidth exhaustion.
The virtualization monitor integrates into the standard WhatsUp Gold dashboard. Its alerts, together with alerts raised by the other modules, can be sent by SMS or email as well as appearing in the console and log files.
Alerts can be sent to team members according to the source application or severity of the alert condition. The dashboard can also be customized and different views can be allocated to individual user accounts. This is a good way to deliver self-service information displays to executives and collaborate with decision-makers.
One shortfall of the WhatsUp Gold solution is the absence of an IP Address Manager module. Identifying overloaded links is an important part of bandwidth maximization. A tool that reorganizes your subnets can avert the need to invest in more infrastructure.
Who is it recommended for?
Progress WhatsUp Gold is suitable for businesses of all sizes. Although very small businesses with only a few computers won’t need all of its functions. You don’t need technical skills to use this package because it sets itself up and it has a simple interface. So, owner-managers will be able to use it.
Pros:
- User-Friendly Interface: Features an intuitive and easy-to-navigate interface.
- Comprehensive Monitoring: Supports a wide range of flow-enabled devices, including both virtual and physical hardware.
- Balanced Features: Strikes a good balance between user experience and advanced monitoring features.
- Customizable Alerts: Allows customization of alerts, which can be sent via SMS or email, based on source application or severity.
Cons:
- Windows Only: Available exclusively for Windows operating systems, limiting cross-platform use.
- Limited Free Version: The free version can monitor only up to five resources, which might be restrictive for larger needs.
The WhatsUp Gold package can be installed on Windows. You can get a free trial to check it out before you commit. The free version of WhatsUp Gold is called WhatsUp Gold Starter. This only allows you to monitor five devices, and in reality, if your network is that small, you won’t really need extensive automation procedures or complicated monitoring software.
Planning for Success
A few hasty additions to a network can cause bandwidth and performance headaches for years to come. If you can spare the time, design your network starting from scratch.
Going forward, make an effort to communicate network issues to executives and decision-makers in your organization. Show that you can work as part of an interdisciplinary team. When a new project begins, the execs will be more likely to ask your input on capacity requirements from day one. Planning expansion of the network avoids traffic flow errors that panicked additions create.
Do you have a favorite tool for bandwidth monitoring? Have you managed to isolate a bottleneck, resolve it, and reduce your network’s bandwidth requirements? Tell the community about your capacity planning experiences by leaving a message in the comments section below the FAQ section.
Network Bandwidth Performance FAQs
What affects network bandwidth?
Network bandwidth is the data capacity of your network infrastructure. Every piece of hardware that contributes to your network will influence bandwidth. These include the quality, capacity, and type of cable, the length of each cable stretch. The distance between network devices, such as repeaters, switches, and routers, plus the capacity of those devices.
How do I check my network bandwidth?
Your network bandwidth is its maximum capacity. To find out the maximum capacity of your network, you need to identify the lowest capacity of all of your network devices. You can check on the box of each of the devices you bought for that information or query the management console of each piece of equipment. A network bandwidth analyzer will perform all of those queries for you. It will present capacity data for all network devices in one screen so you can work out which is a bottleneck, governing the total capacity of your network.
Does increasing bandwidth increase Internet speed?
One reason for a slow Internet connection can be the capacity of your router/gateway. Another reason could be that you chose a cheaper plan with your Internet Service Provider that has a limited bandwidth. Whichever is lowest between the capacity of your plan and your router governs your Internet speed. If you buy a bigger router, you will get more capacity, thus more bandwidth. However, you need to check that your ISP plan will provide that greater bandwidth, too. If both your router and ISP plan have higher bandwidth you should get better Internet speed.
Does my router affect bandwidth?
Your router’s capacity will govern your bandwidth. All of the other equipment on your network has equal influence as does the delivery speed and bandwidth of your ISP. Your maximum bandwidth is governed by the lowest capacity of all of your network equipment. If you upgrade your router to have more capacity, and thus bandwidth, make sure that your cable and your Internet service plan have an equally high capacity, otherwise, you would have wasted your money on the router upgrade.
Image: Facebook Connections by Tim Walker via Flickr. Licensed under CC BY-SA 2.0