Sumo Logic and Splunk are two of the most widely recognized tools for log management and data analytics. Both systems offer efficient features for collecting, analyzing, and visualizing machine data from applications, systems, and network devices, helping businesses gain valuable insights into their IT infrastructure. Both packages are suitable for troubleshooting, security monitoring, or performance optimization. These platforms are designed to enhance operational efficiency and security posture.
Sumo Logic is a cloud-native log management and analytics service. It offers real-time log collection, advanced analytics, and machine learning to provide actionable insights from data. Sumo Logic is highly valued for its ease of use, especially for businesses that require rapid deployment and don’t want to deal with complex infrastructure management. The platform’s pay-as-you-go model ensures that companies only pay for the services they use, making it an attractive option for smaller businesses or those with fluctuating needs.
Splunk, on the other hand, is a more established log management tool. Known for its powerful capabilities in handling large volumes of data, Splunk is used by enterprises across various industries for performance and security monitoring. Splunk offers detailed search and analytics, alerting, and reporting, and its ability to integrate with other enterprise systems. While Splunk’s pricing can be a consideration for smaller organizations, its flexibility and depth of functionality make it a preferred solution for complex environments.
This comparison will explore the features, benefits, and potential drawbacks of both Sumo Logic and Splunk to help businesses determine which platform is the best fit for their needs.
Similarities: Sumo Logic vs Splunk
Both Sumo Logic and Splunk act as continuous security monitors for your organization that can detect and remediate threats that firewalls and antivirus endpoints often miss. As a SIEM tool, both products can be configured to detect insider threats, external intrusions, and track APTs (Advanced Persistent Threats) across a network.
Both companies boast an impressive host of international and enterprise clients. Sumo Logic has served giants such as Samsung, Whole Foods, and Pitney Bowes. Splunk on the other hand has worked with industry leaders such as Intel, Comcast, and Coca-Cola. Both Splunk and Sumo Logic have served clients in the Fortune 500 and are built well for enterprise environments.
From a dashboard perspective, both products present incoming data and new information through an intuitive interface. Views can be fully customized depending on your needs through drag-and-drop style templates.
Sumo Logic
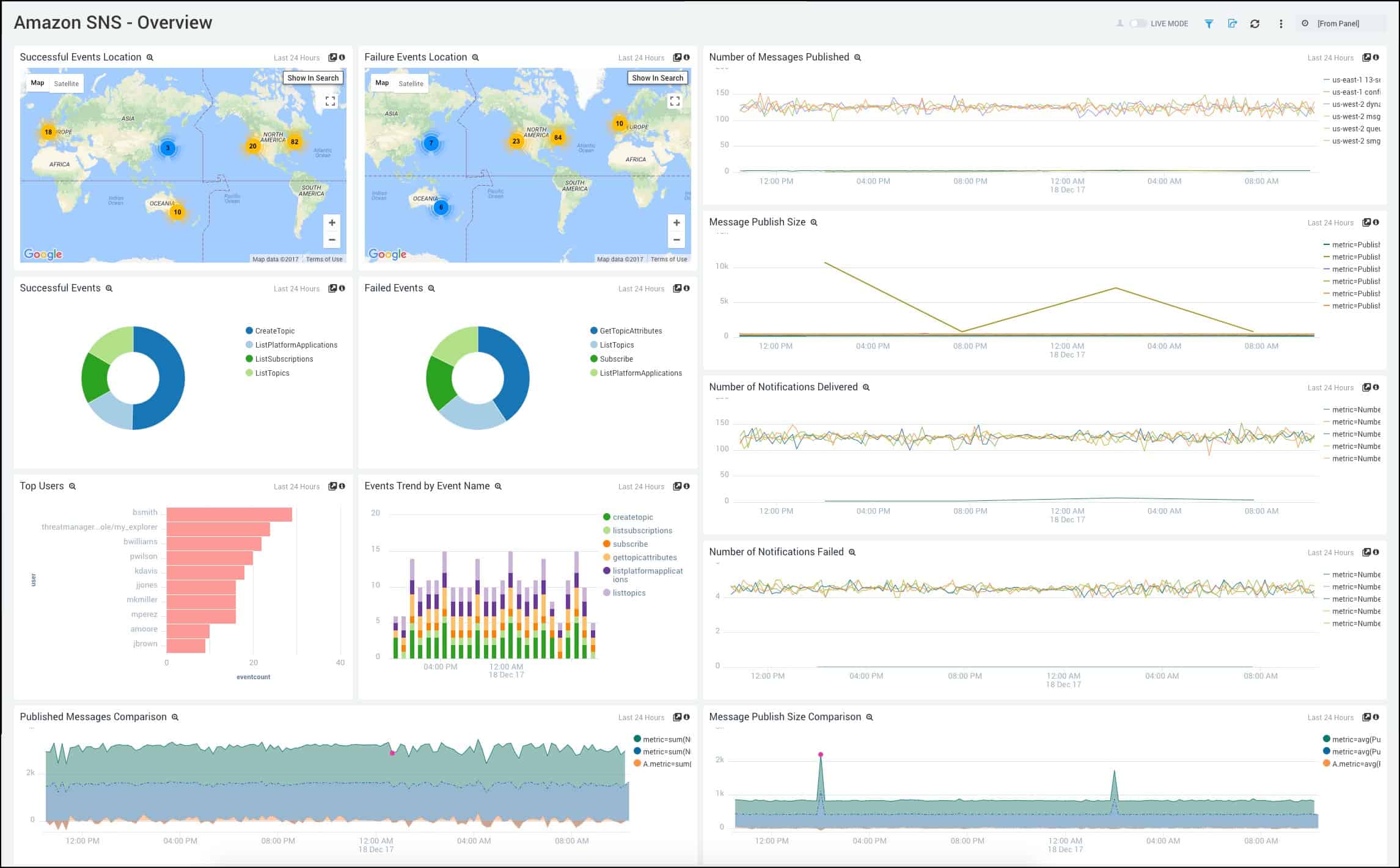
Sumo Logic brings security, business, and operations intelligence into a single manageable platform from both structured and unstructured data streams. A key difference between Sumo Logic and Spunk is that Sumo Logic is currently only available for cloud setup, meaning the data you gather across your devices and networks will be stored in a private cloud. For most companies, this won’t be a problem, but for organizations that are strictly looking for an on-premises solution, this may present a problem.
Key Features:
- Flexible data collection tool
- Prewritten search tools called apps
- Query builder
- Alert definition function
- Free version
Unmanaged data is pulled from multiple sources from a Collector. This collector is a lightweight agent that can be installed manually or deployed via script. The setup process is fairly straightforward and supports multiple hosts such as Linux, Windows, macOS, or as a binary package. Once the Connector is deployed through the install wizard, you will see your connector active under the Manage Data > Collection > Collection section of your Sumo Logic dashboard.
Sumo Logic makes it easy to start extracting value from your information relatively quickly through its series of wizards, onboarding support, and intuitive interface. After your collectors are in place, you’ll specify a source for your data through another wizard. This adds context to the data the collector is now beginning to pull in.
When it comes to visualizing your data you can manually configure metrics from each source to display information through a chart or graph. This can be a bit time-consuming during the initial setup. Thankfully, Sumo Logic has an entire section called Apps that is dedicated to creating out-of-the-box insights you can apply to your data. Deploying an app to your data is as easy as choosing what app or insight you want for your data, and clicking Install.
Running manual queries against your log data is a simple process, especially if you’ve queried data from logs or other search engines before. Like Splunk, Sumo Logic automatically populates the search bar with parameters and data sources to help you save time on remembering search functions. If you’re new to working with search functions and queries Sumo Logic provides a series of helpful cheat sheets that contain all of the most common search functions to query your data.
In order to create meaningful alerts, you must first build a query off of to base that alert. Once that query has been written you can specify a condition to trigger that alert, as well as set a threshold. You can utilize an outlier operator to help position your thresholds to expand and contrast as your web traffic does. Creating alerts is simple to execute as long as you have your query written properly. Alerts can be emailed or sent through third-party integrations via webhook.
Pros:
- Supports multiple environments (Linux, Windows, and Mac OS)
- Simple installation – Uses wizards to streamline install and add-ons
- Has a host of templates and premade assets making the experience user friendly
Cons:
- Better suited for small to medium-sized businesses
Sumo Logic provides a smooth onboarding procedure with minimal setup needed to start garnering business intelligence. There is a free version of Sumo Logic that you can use to start collecting and analyzing data in a limited capacity. The current pricing model is broken down into four tiers based on data usage and uses a credit system for flexible billing. Small business logging and monitoring start at $2.50 per gigabyte with a 10GB per day data limit.
See also: Sumo Logic Review
Splunk
Splunk is a SIEM tool aimed at providing log management and security insights for enterprise-level clients. The Splunk platform offers a wide range of services and functionality including insider threat detection, forensic level auditing, and even fraud detection. While Splunk primarily advertises that it’s cloud-based, there is an option for an on-premises installation. This can be done via VMware infrastructure, however, compared to the cloud deployment you may find yourself using a considerable use of time ensuring requirements are met and that proper resources are being allocated.
Key Features:
- On-premises or cloud platform
- Data analysis platform
- Log management service
- SIEM option
- Alert creation mechanism
Like most SIEM products, Splunk utilizes its own agent referred to as an indexer to gather data. This indexer does require some configuration depending on what operating system environment it is installed on. Once the indexer is configured and installed you can configure Splunk to start receiving data by going to Settings > Forwarding and Receiving and entering the listening port for your agent.
The configuration process can be complex at times, involving forwarders and the installation of ‘apps’ which are intended to remove complexity from the onboarding process and avoid any misconfigurations from taking place. Depending on how complex your environment is, and how many domain controllers and servers you need to set policies for, your onboarding time may vary. Splunk’s support team does have a professional services division that can assist with onboarding as well as data migration and configuration.
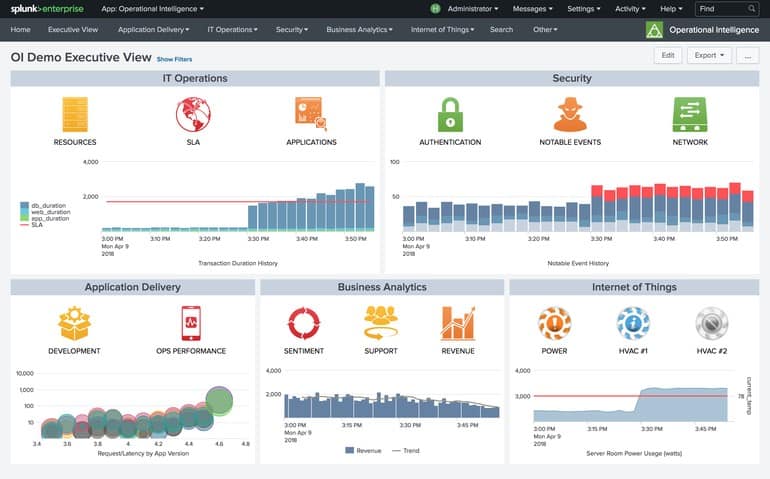
After the initial onboarding process, Splunk’s ease of use really begins to shine. Splunk has some of the most intuitive and flexible dashboards in the SIEM space, allowing for both drag and drop editing through the Visualization Editor, as well as XML configuration to make changes on the fly. Dashboard panels were built with teams in mind, and give you the ability to create specific views based on departments or groups. This helps ensure that no team is overwhelmed with information that isn’t relevant to their duties.
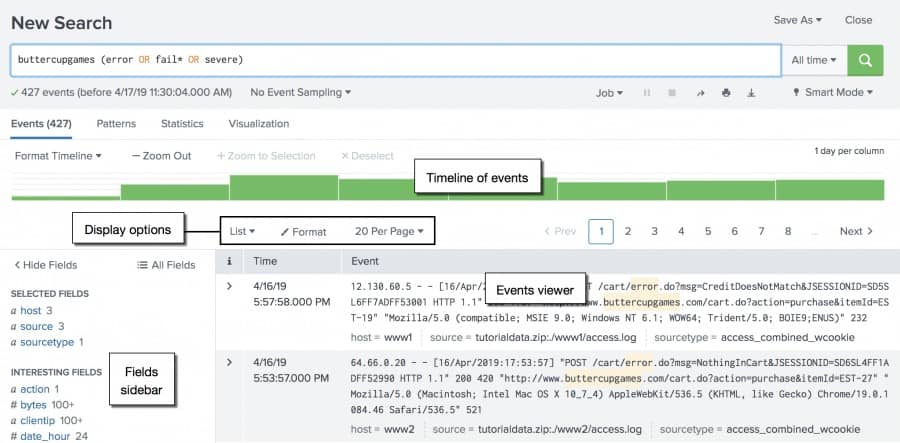
Searching within Splunk can be a complex, but rewarding endeavor. Splunk uses its own Search Processing Language (SPL) to filter and sort data. This SPL can have a steep learning curve at times but allows for intricate and complex queries to be generated. One of the more powerful features of Splunk’s SPL is the ability to visualize your search data in realtime. Whether this is a number value on a charted graph or a geolocation tag, this information can be displayed as you develop and refine your query.
You can create alerts in Splunk based on a query by simply entering that query as a search, and clicking on the Save As button, and choosing Alert. From here an alert workflow is created that allows you to choose the trigger conditions for alerting, as well as the permission level and schedule that the alert will operate in. Alerts can be received via email, log event, webhook, or set to execute a script. Once saved, all alerts automatically populate in your alert dashboard where you can see an overview of their current status, as well as how many times they have been triggered.
Pros:
- Has an excellent interface for displaying data and monitoring live metrics
- Supports physical and virtual environments
- Caters to enterprises with excellent support and a wide range of integrations
Cons:
- Caters more to enterprise clients
Splunk has a proven track record serving enterprise clients and brings a truly comprehensive SIEM tool to the marketplace. Splunk’s dashboards and alerting features are built with ease of use and scalability in mind. Splunk has a unique pricing model that encompasses four different pricing options built around different ways your business wants to scale. You can expect pricing for Splunk Enterprise to start at $2000.00 per year at the 1GB/day data plan.
See also: Splunk Review
Key Differences Between Sumo Logic vs Splunk
When comparing Sumo Logic vs Splunk there were some key differences that you may desire to really dive deep into mastering a SIEM to consider before you make a decision to commit one tool.
Splunk has a larger community and more features. Splunk has taken its revenue and heavily reinvested it back into the Splunk platform. This has allowed the platform to achieve “hockey stick” growth while maintaining a competitive advantage over other SIEM tools.
Features such as augmented reality (Splunk AI) allow you to visualize data in real-time, and new developments to the Splunk mobile app give data newfound versatility over other platforms. Although Splunk is not open source, it still boasts a large community that helps other users answer questions, share best practices, and request new features.
Splunk has extensive documentation and more support options. While both Sumo Logic and Splunk have multiple forms of support, Splunk has extensive documentation and additional support programs for those who need a higher level of service. Splunk has five different levels of support models ranging from simple access to documentation all the way to premium 24/7 support with 30 minute minimum response times.
While not every company needs this level of granularity in its support contract, Splunk has taken the time to create these plans to best serve their clients.
Sumo Logic has less of a learning curve. If you don’t have the budget or desire to really dive deep into mastering a SIEM, Sumo Logic will be the simpler choice. Sumo Logic offers premium security and log management without the need to spend dozens of hours on training. Splunk’s SPL search engine may be powerful, but adds many layers of complexity to the mix that smaller businesses may not need to utilize at all.
Splunk has more third-party integrations. While both platforms have the ability to utilize webhooks and API integrations, Splunk has many more out of the box plugins and features. Currently, Splunk has upwards of 600 different types of applications and plugins that extend and enhance the usefulness of the platform. Splunk also has many other security and business intelligence tools that allow you to integrate into those new features with relative ease.
Which Tool Is Best For You?
In the case of Sumo Logic vs Splunk, the comparison was neck and neck. Both products provide flexible and competitive pricing while offering cutting-edge features and log management. In the end, if you’re a larger business or enterprise that’s looking to scale and leverage data for the long term, Splunk will likely be your best bet. While the learning curve may be higher, you’ll have more options to grow into down the road, and have fewer issues integrating those features moving forward.
For smaller businesses looking to implement security and log management for their environment, Sumo Logic is a great choice based on its ease of use and flexible pricing.
Alternatives To Sumo Logic and Splunk
Our methodology for selecting an alternative to Sumo Logic and Splunk
We reviewed the market for log management systems and analyzed tools based on the following criteria:
- Log collection and consolidation
- Creation and cycling of log files
- Meaningfully named log file directories in a logical structure
- Log data viewer
- Log data search tool
- A free trial or a demo option that creates a no-risk assessment opportunity
- Value for money, represented by a log management system that is offered at a good price or is free to use
With these selection criteria in mind, we have identified log management tools that compete well with Sumo Logic and Splunk.
Below is a shortlist of alternatives to both Sumo Logic and Splunk:
- Datadog Leverages real-time and historical data to provide actionable insights, automated remediation, and alerting across your cloud or on-premises environment.
- Sentry.io Provides logging solutions primarily focused on serving software development teams and the DevOps industry.
- ELK Popular open-source tool dedicated to free log management and incorporates tools such as Elasticsearch, Logstash, and Kibana for extended functionality.
- LogStash Developed by Elastic, LogStash makes data management attainable for small development teams and researchers.
If you’re still comparing SIEM products, be sure to check our best SIEM Tools post.
Sumo Logic vs Splunk FAQs
Is Sumo Logic like Splunk?
Sumo Logic is a SIEM tool, which processes log messages and searches them for signs of security breaches. Splunk is a data searching tool that can be used for a range of purposes and that includes security breach detection. So, Sumo Logic is very similar to Splunk Enterprise Security, a SIEM application that is an added package for Splunk.
What is the purpose of Sumo Logic?
Sumo Logic is a cloud-based service that uses an on-site agent to gather log messages from around an enterprise’s system. Once those messages are uploaded, they get converted into a common format, stored, and also searched for signs of security breaches. This is a SIEM system.