Cloud Access Security Brokers (CASBs) are an essential part of the modern cybersecurity landscape, particularly as businesses increasingly adopt cloud-based services. A CASB acts as a gatekeeper, providing visibility and control over user activity across cloud applications and services.
As organizations migrate more of their operations to the cloud, they face new security challenges, such as managing and securing data, ensuring compliance with regulations, and preventing unauthorized access to sensitive information. CASBs bridge the gap between on-premise security measures and the cloud, offering the tools needed to safeguard cloud environments.
This guide explores this critical technology, explaining its role in cloud security, the benefits it provides, and how organizations can leverage it to protect their cloud-based assets. As businesses adopt multiple cloud platforms, including SaaS, PaaS, and IaaS, a CASB helps ensure that these services are secure, compliant, and properly monitored.
Our investigation explores the core features of CASBs, including data security, threat protection, compliance monitoring, and visibility into cloud usage. With a CASB in place, organizations can gain insight into cloud app usage, enforce policies regarding data storage and sharing, and protect against data breaches, malware, and other risks. CASBs also enable organizations to manage cloud security policies across multiple providers, ensuring that consistent protection is applied wherever data resides.
We will cover the different types of CASBs, including forward proxy, reverse proxy, and API-based solutions, each with unique benefits suited to different organizational needs. As more organizations embrace cloud computing, understanding the role of CASBs in enhancing cloud security is crucial to reducing risks and maintaining a secure environment.
Overall, this guide provides valuable insights for organizations seeking to understand CASBs and integrate them into their cloud security strategy. By implementing a CASB, businesses can improve their cloud security posture, reduce vulnerabilities, and ensure they meet compliance requirements.
What is a CASB?
The acronym CASB – pronounced “kas-bee” or “kaz-bee” – stands for “cloud access security broker“. It can be a software or hardware solution tasked with protecting data and identity, preventing threats, and offering insights into the risks involved in a network’s connection to other cloud apps and devices. A CASB can be deployed locally, on-premises, or remotely to run as a cloud SaaS.
Trivia: Gartner was the first to define CASB in 2012 as “on-premises, or cloud-based security policy enforcement points, placed between cloud service consumers and cloud service providers to combine and interject enterprise security policies as the cloud-based resources are accessed.”
Typically, a CASB is used to analyze data flows and scan cloud documents to detect any malicious files or tools hidden within them. It is also used to gain insight into and granular control of cloud data usage information.
What are the four standard features of a CASB?
A CASB must have at least four basic features for it to be called an intelligent solution. These features are:
- Data Security – it should monitor data access and share under presiding loss-prevention policies that are in place. This security can be further enhanced with data labeling and encryption to ensure privacy and integrity.
- Threat Protection should act as a line of defense against internal and external threats arising from malicious user activity, malware, and risky or prohibited cloud services. It should also:
- Track and identify anomalies in data access and usage
- Log audit trails for later inspection and reporting
- Help in defining new adaptive access policies or even suggest corrective actions to be taken in strengthening existing ones
- Visibility – apart from immediately identifying current and any new cloud services being accessed, a CASB should assess the risks involved in accessing and using them. It should also keep an eye out for shadow IT
- Compliance – a CASB can be a helpful tool when trying to achieve compliance to internal security policies or external industry-standard requirements, like HIPAA or SOX. Apart from assessing the current security configurations, it should also be able to make additional input for enhancing any security oversights, thus contributing to maintaining compliance.
What are other features of a good CASB?
Apart from the four core ones we have just seen, there are some more features, ranging from “nice to have” to “very helpful if offered,” that would contribute to making a good CASB solution.
Some of these features include:
- Monitoring and auditing of traffic to gauge overall risk exposure across applications used or accessed within the architecture.
- Ranking each discovered application according to the risk it could pose; would help determine the cumulative risk level across the whole architecture. The analysis can also be used as a springboard for further threat-mitigation actions.
- Rapid data scanning capabilities, with AI-backed or machine learning technology, prevent data loss while also providing deep insights into the data used. This should be backed with real-time reporting on malicious activity or unauthorized access (and sharing) of sensitive data via emails, chat, file sharing, forums, screenshots, or other methods.
- Efficient round-the-clock enforcement of security policies to stop threats and prevent data loss without affecting the network’s performance or causing any deterioration of user experience (UX) on endpoints.
- Ability to look within the network (ala antivirus, etc.) to spot malicious activity, compromised accounts, or unauthorized access attempts made by privileged account holders as they work with internal and external data or applications.
- Being capable of easily integrating with the existing security infrastructure and all third-party security applications and tools on it for an optimized and unified security perimeter. It should also be future-proof as well as highly scalable.
- Capable of covering the network from end-to-end and monitoring whole stacks regardless of connection method – be it in a cloud, on-premises, or hybrid architecture.
Of course, all these features need to be accessed and monitored from a single dashboard that is comprehensive, insightful, interactive, shareable (for collaboration), and easy to use.
Uses of a CASB in real-life scenarios
After looking at the features that make an excellent CASB, we can now go on to see how they can be applied on a network:
- A CASB can discover the services running in a cloud platform and assess individual risks at an application level; it can then block connections to suspicious or prohibited applications instead of completely denying access to the platform.
- A CASB can serve as a data protection barrier for an organization’s websites and cloud services – it can handle the security and enforcement of SaaS, IaaS, and PaaS access and usage. Then, depending on the requirements, administrators can create one overriding policy or as many procedures as necessary to ensure compliance.
- The administrators can also prevent sensitive data from being transferred from or to unmanaged cloud applications, stop accessing specific compromised services, and avoid downloading or uploading confidential They can, for example, block employees from sending company emails containing sensitive data to their personal (external) email addresses or prevent copying data from a sanctioned cloud platform to an unsanctioned one.
- Organizations can stay on top of their industry’s compliance requirements and standards by using a CASB to keep track of their data security levels, access controls, and encryption of data in motion and at rest – and also get pre-defined customizable reports to be consumed by both local stakeholders as well as external auditors.
A CASB in the network infrastructure
Let’s now delve a little deeper and have a look at the CASB itself.
Location
There are a couple of ways and places a CASB can be run or placed in a network. First, it needs to sit between end-users and the cloud.
But, physically, it can be located in the cloud (if it is a SaaS itself, for example) or installed on-premises in a corporate data center by hosting it on a physical or virtual server.
Configuration
There are three ways of configuring a CASB. First, it can be set up as:
- A forward proxy – this CASB sits between the users and the cloud services and monitors the data passing through the proxy. If there is a drawback to this otherwise simple configuration, it would be the need for self-signed certificates to be installed on every device that uses the proxy. This can be a pain in cases where there are many remote devices, a hybrid network configuration, or a large number of BYOD.
- A reverse proxy – here too, a proxy is used; but it monitors traffic trying to access servers. Although this is a highly accessible option and requires no special certificates or configurations, it could pose a problem when client-server communication is required by apps that have their hostnames hard-coded into them.
- API-based – this is arguably the better (and modern) solution as the CASB runs as an out-of-band tool that integrates directly with cloud services and doesn’t follow the same network path as the data accessed from the cloud service providers. It is ideal because no performance degradation occurs as users go about seamlessly accessing their data.
Of course, it is also possible to configure them to run in mixed mode – as both forward and reverse proxies – and in a multi-modal configuration where it serves as both a proxy and an API-based security technology.
Examples of reasonable CASB solutions
OK, now it’s time to have a look at some tremendous CASB solutions that can genuinely help protect data and networks. They are:
1. Check Point’s SASE (Access FREE DEMO)
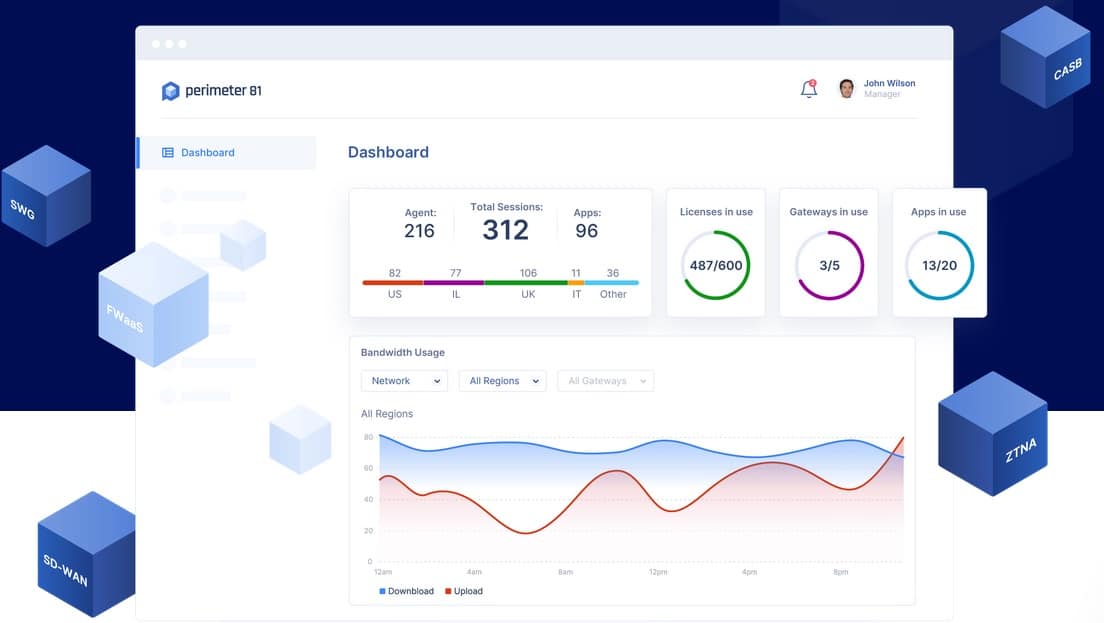
Check Point’s SASE, formerly Perimeter 81, offers plans that combine VPN connection protection with identity and access management (IAM) to provide application-level access rights for each of the users on the system. This package includes a secure Web gateway (SWG) and a CASB system to define data access permissions and cloud access rights.
Here are some of the features of the Check Point’s SASE package:
- A Network-as-a-Service platform that creates a protected private network over the internet to connect sites, SaaS servers, and remote users.
- A cloud-based console that enables the definition of individual user rights to access specific applications on the cloud and on-site.
- A Zero Trust Access manager requires each user to provide credentials for reach access action.
- An activity logging service that records all access attempts
- A secure Web gateway to control user access to the business’s SaaS services and other We assets
- A single sign-on service (SSO) removes the need for the user to log in again and again while going through a normal working day.
- A Firewall-as-a-Service that blocks DDoS attacks and other traffic-based malicious activity and also scans outbound traffic for data theft attempts.
The core of the Check Point’s SASE system is a cloud-based hub that directs traffic between sites and remote users and the services deployed by the business on-premises and in the cloud.
Pros:
- Flexible features and offers that cater to smaller networks as well as enterprises
- Multi-site management makes this viable for MSPs
- Wide variety of integrations (LDAP, SAML, etc)
- Flexible pricing – great for any size network
- Easy to use object-based configurations
Cons:
- Would like to see a trial as opposed to a demo
Access a demo to see Check Point’s SASE for yourself.
2. Netskope
With Netskope, we have one of the leading CASB solutions on the market today. The company is proud to advertise that they have been named a “2020 Magic Quadrant Leader for CASB” by Gartner – for the fourth consecutive year, no less.
Let’s look at features that have contributed towards this excellence:
- Netskope can manage the unauthorized movement of confidential data between cloud app instances while streamlining security workflows with similar intuitive policy controls – it can prevent personal data from being sent to external email addresses.

- This CASB solution helps administrators quickly identify and manage the use of their cloud applications regardless of whether they are managed or unmanaged solutions.
- It prevents data loss, due to threats from both inside and outside the network, by allowing administrators to set granular security policies and gain visibility into their organizations’ overall vulnerability levels.
- It is designed to secure standard cloud services like Microsoft 365, Google Workspace, Box, and AWS; it provides comprehensive security across these cloud services to protect against threats and malware.
- This CASB’s security is backed by 40 threat intelligence feeds that help identifies malicious sites, detect abnormal user behavior, and protect against cloud-based malware.
- Administrators can set their own customizable data loss protection policies that include role-based access controls (RBAC) that are enforceable across all cloud applications.
- Although Netskope can be deployed as a SaaS, the product is also available as an on-premises appliance and a hybrid tool.
Pros:
- Leverages big data to improve threat detection
- Offers a great deal of filtering and scanning customizations
- Can protect both managed and unmanaged cloud applications
- Supports BYOD environments
Cons:
- Best suited for enterprise environments
Request a Netskope demo for FREE.
3. McAfee MVISION Cloud
McAfee MVISION Cloud is a CASB made by one of the leading anti-virus and computer security software makers. It is a cloud-native solution that protects data that resides in the cloud.
MVISION Cloud has some great features:
- It covers the entire stack offering insights into data, context, and user activity in all the apps and devices it has to cover.
- Being a cloud-native solution means MVISION can protect data in that realm with ease. Still, it can also cross over into the local on-premise network and keep sensitive data shielded without compromising performance there too.

- It can be configured to enforce data loss prevention (DLP) policies, prevent unauthorized data access, detect compromised accounts (or those showing suspicious characteristics and activities), and even point out policy violations.
- All these policies and configurations are managed and monitored from a single dashboard that offers deep insight into cloud applications, granular data protection policies and is highly customizable to cater to unique network configurations.
- It comes with the risk profile of over 30,000 cloud services, making it easy to stay safe even when accessing unfamiliar third-party apps and services.
- MVISION works as a forward proxy for better web security, offers data encryption, and helps prevent Shadow IT services.
- It can be configured to stop users from moving sensitive data to their personal or unmanaged devices and accessing prohibited cloud services; it keeps an eye out for operating systems being used, device management statuses, and location to enforce these policies.
- It can also be extended to spot any misconfigurations or vulnerabilities in popular cloud services like GCP, Azure, and AWS; even containers can be monitored in real-time.
Pros:
- Supports Windows, Linux, and Mac OS
- Offers roll-back points for infected endpoints
- Monitors network traffic to stop DDoS attacks, botnets, and rouge mail servers
- Allows sysadmins to orchestrate security policies across their environment
Cons:
- McAfee can use a lot of system resources while scanning (not ideal for older endpoints)
Schedule a McAfee MVISION Cloud demo for FREE.
4. Bitglass Cloud Access Security Broker
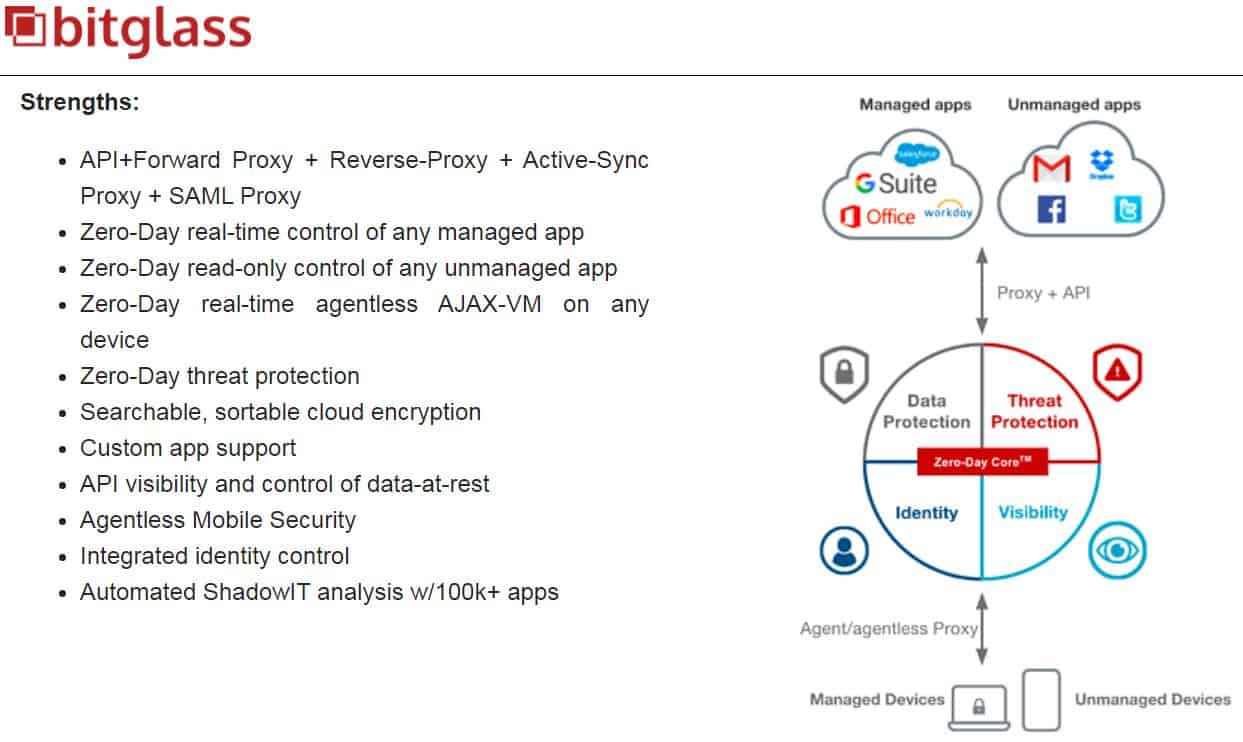
Bitglass is another major player in the CASB market. Their product, simply dubbed the “Bitglass Cloud Access Security Broker,” allows organizations to work with cloud applications and services without compromising their security. This tool can be configured to apply policies that protect any device that needs to access cloud data.
The features:
- This tool can be used to protect both managed and unmanaged devices and apps from data loss and malware threats; its multi-protocol proxy architecture and its Zero-Day Core platform make it the ideal cloud security solution.
- It also leverages another in-house technology, patent-pending, to ensure application resilience using AJAX-VM for agentless reverse proxy capabilities.
- It can be configured to work on firewall and proxy logs which can serve as input for decision making and action on any cloud application used in the organization – administrators can block or allow read-only access to them depending on their analysis results.
- The tool even identifies new applications and quickly learns any compromised behaviors or data leaks using machine learning; this analysis can be used for coaching, blocking, or zero-day control configurations.
- It has DLP and access control engines that can identify and control the context of the data being accessed as well as the applications that are doing the accessing; this contextual access control takes into consideration aspects like locations, user groups, access methods, times, and whether or not the devices are managed before deciding on the level of access to be granted.
- It can also give detailed insights into the users themselves as it collects authentication data, suspicious activity, and other related information to increase visibility and reduce risks.
- One central dashboard controls all analytics and feedback and offers insightful reporting for rapid response and actions; the tool also has a REST API that can integrate into some of the best SIEM tools or any other existing security tools’ workflows.
- The tool also has unique features like identity management, Microsoft AD integration, multi-factor authentication (MFA), and more; this eliminates the need for third-party identity and access management (IAM) tools.
- Bitglass has an index of over 100,000 applications – each of which is ranked by reputation and security risk – that is continuously being updated using machine learning technology.
Pros:
- Includes DLP modules
- Offers a wide variety of SIEM integrations
- Leverages intelligence networks to reduce the risk of zero-day attacks
- Includes detailed access controls for staff
Cons:
- Tailor for enterprises – not the best option for smaller businesses
Try Bitglass Cloud Access Security Broker for FREE.
5. Cisco Cloudlock
Cisco is a name that is synonymous with network security. It shouldn’t come as a surprise then that they also offer one of the best CASB tools out there: Cisco Cloudlock.
This CASB has it all: it is cloud-native and protects everything in the cloud – users, data, and applications.
Here are some of its features:
- It is a simple tool that is fine-tuned to prevent data breaches and achieve compliance by using APIs to monitor the access and usage of cloud application ecosystems.
- It has an advanced machine learning technology to detect anomalies using numerous input variables like locations, users, accounts, and even access speeds.
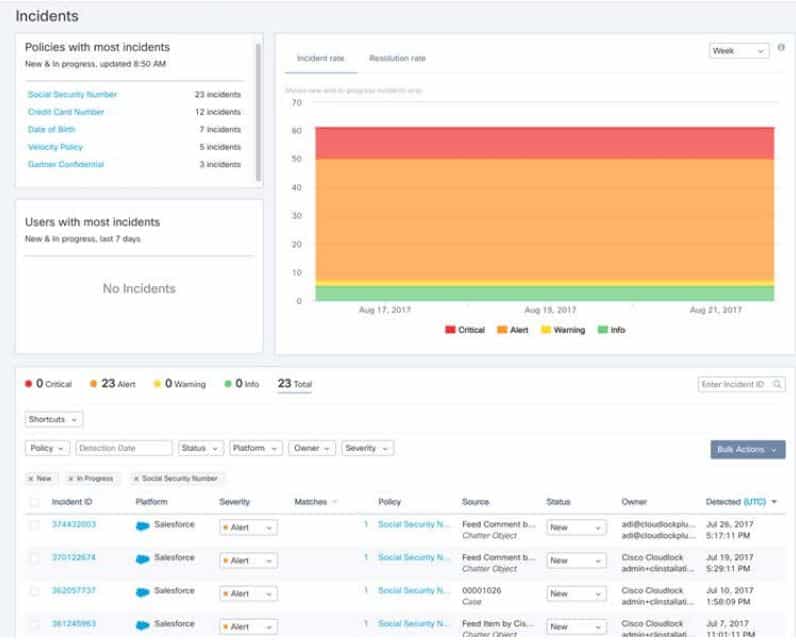
- It monitors the entire cloud environment as it works to stop data loss, tracks the movement of sensitive information, also helps develop a security policy strategy; in fact, Cloudlock comes with its ready-to-use policies that can also be customized to meet unique requirements.
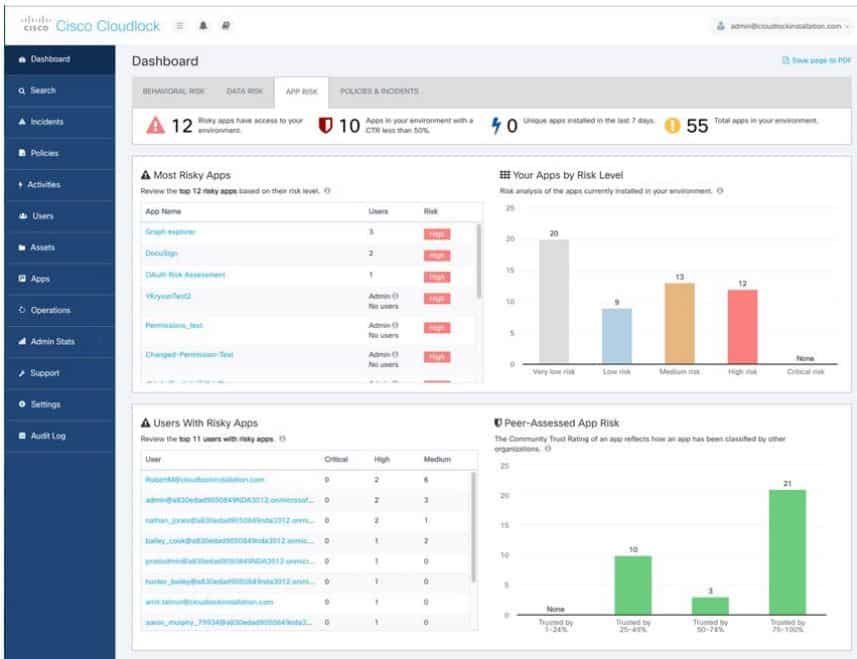
- The tool also comes with Cloudlock Apps Firewall – a firewall that discovers and monitors apps connected to the network and rates them according to the risk they may pose; they can then be blocked (or allowed) depending on their risk assessment analysis results.
- The organization can keep track of what cloud data their users are accessing, storing, or moving about as they go about their daily work schedules; and it’s not just to make sure users adhere to policies but to also train the machine learning system as it goes about detecting behavioral anomalies.
- Administrators will always have a clear insight into each application or software vendor. In addition, the tool continuously updates its risk assessment capabilities, ensuring that everyone is safe even when new apps are added.
- Finally, perhaps the best thing about using this tool may be that although it is a standalone solution, it has been designed to integrate seamlessly with Cisco’s wide range of security tools, especially Cisco Umbrella – their flagship web security platform. This ensures an end-to-end security coverage without the hassle of using third-party solutions to bridge gaps.
Pros:
- Simple interface – easy to learn and use
- Integrates well with other Cisco products
- Can proactively alert and prevent data theft or changes
- Stop new threats through behavioral profiling
Cons:
- Can take time to fully explore all features and supporting products
Request a Cisco Cloudlock demo for FREE.
A final consideration about when to use a CASB
Cloud computing is the future. The COVID 19 pandemic alone has learned that it is indeed an efficient way of working, although there are skeptics who still think the office is the best working environment.
Regardless, we will continue to access and use an ever-growing number of cloud productivity applications which means we will all eventually need the protection of a CASB. This is especially true for larger organizations.
Let us know when you think you would need a CASB? At what stage do you think it becomes a necessity? Leave us a comment below.