This week was a big one in ransomware. Attacks struck law firms, schools, public services, and private companies, to name a few. Read on to catch up on all of the week’s ransomware news, big and small.
Houser LLP
Law firm Houser LLP increased the number of victims affected by a May 2023 attack from 326,386 to 370,001 people. Victims were first notified in February 2024.
Ransomware group BlackCat claimed the attack. Houser’s notification states, “in June 2023, the unauthorized actor informed us that they deleted copies of any stolen data and would not distribute any stolen files.” We can infer from that statement that the ransom was most likely paid.
The data included financial account numbers, credit card numbers, Social Security numbers, driver’s license numbers, tax ID numbers, and medical information.
This was the second biggest breach on a US law firm in 2023 (Orrick, Herrington & Sutcliffe affected 637,620).
Kisco Senior Living
Kisco Senior Living, LLC sent out data breach notifications to 26,663 people following a cyber attack over 10 months ago in June 2023. Ransomware group, BlackByte, claimed an attack on the organization at the time.
According to the notification, names and Social Security Numbers are among the data affected.
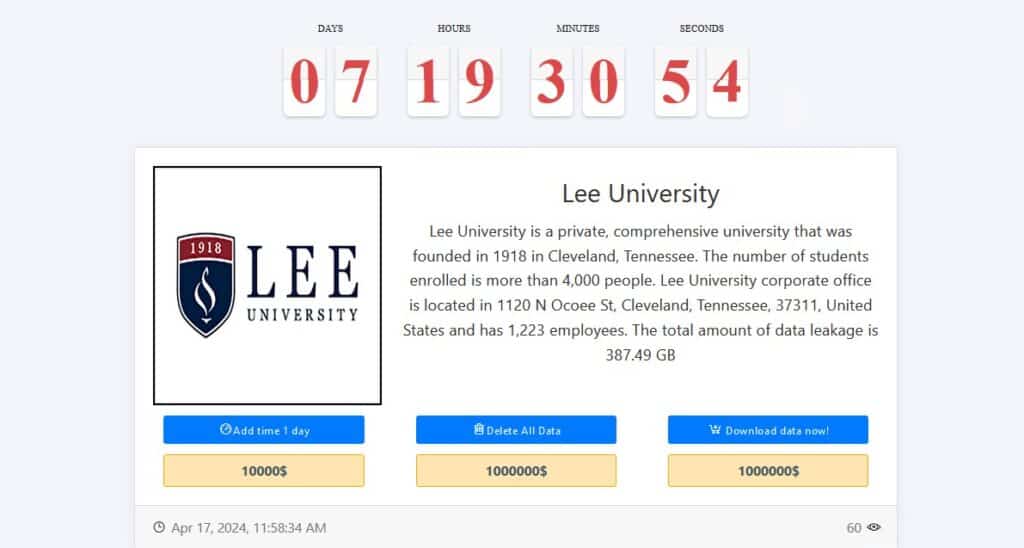
Lee University
Ransomware group Medusa is demanding $1 million for the safe return of data it says it stole from Lee University in Tennessee. The University yesterday announced it was investigating a “potential security incident” that it discovered on March 22, 2024.
Lee University didn’t share what data or systems were affected, and hasn’t confirmed Medusa’s claims. Medusa says it stole 387.5 GB of data from the school.
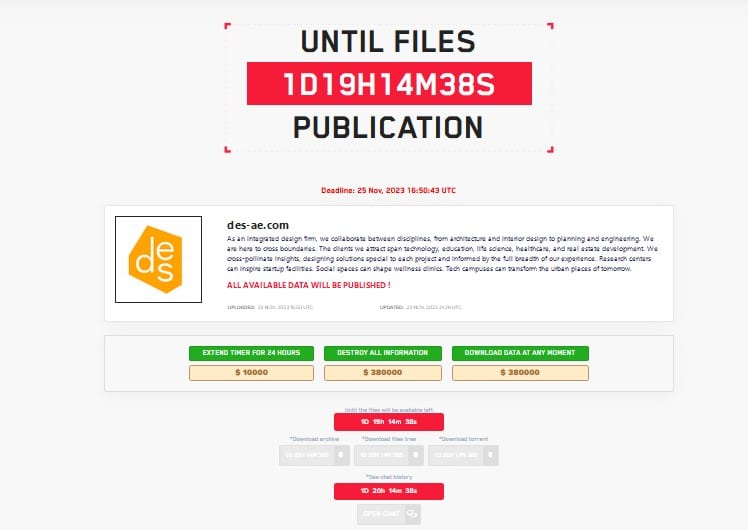
DES Architects + Engineers
California architecture firm DES on April 16, 2024 notified 1,144 victims that their personal data was stolen in a ransomware attack. The compromised data included financial account numbers, credit card numbers, Social Security numbers, names, passport numbers, medical information, health insurance information, and dates of birth.
The attack took place between September and October 2023, and DES discovered it on October 19, 2023. Ransomware gang Lockbit claimed the attack on its leak site in November. It demanded $380,000 in exchange for not selling or publicly releasing the data.
Cherry Health
On April 16, 2024, healthcare company Cherry Street Services, Inc. (“Cherry Health”) began notifying 184,372 of a data breach following a ransomware attack in December 2023. The stolen data includes health insurance and patient ID numbers, treatment information, Social Security numbers, prescription details, and financial account details, putting patients at risk of health benefits fraud and identity theft.
No ransomware groups have publicly claimed responsibility for the attack.
Numotion
Numotion, a US manufacturer of wheelchairs and other mobility solutions, on Monday notified 4,190 people of a data breach that compromised names, Social Security numbers, dates of birth, and employment information.
Ransomware group Black Basta claimed the attack, which took place from February 29 to march 2, 2024.
We do not know how much the ransom was or whether Numotion paid it. Numotion hasn’t stated if any of the compromised data belonged to customers, nor how attackers managed to break in.
St. Cloud, Florida
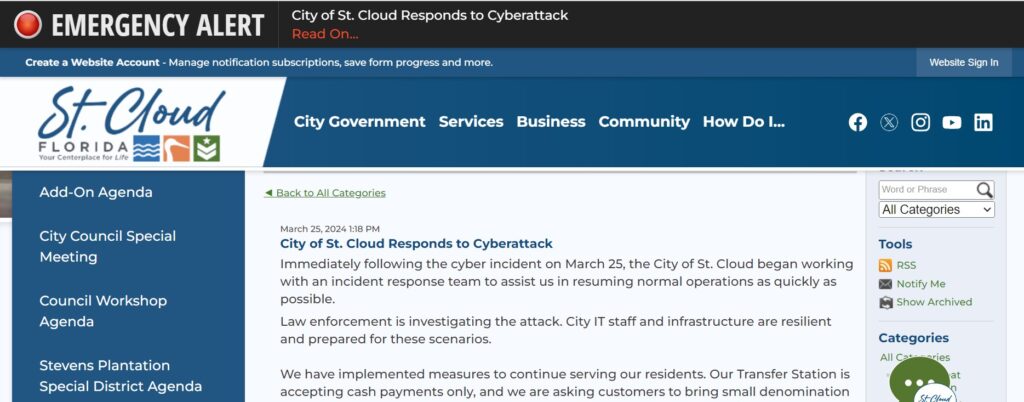
Ransomware gang, Hunters International, on April 16 added the City of St. Cloud, Florida, to its data leak site. On its site, Hunters International claims to have stolen 1.4 TB of data, which includes 719,597 files.
On March 25, the City of St. Cloud confirmed it was dealing with a cyber attack and was working to resume normal operations “as quickly as possible.” The St. Cloud Police Department confirmed that it was a ransomware attack.
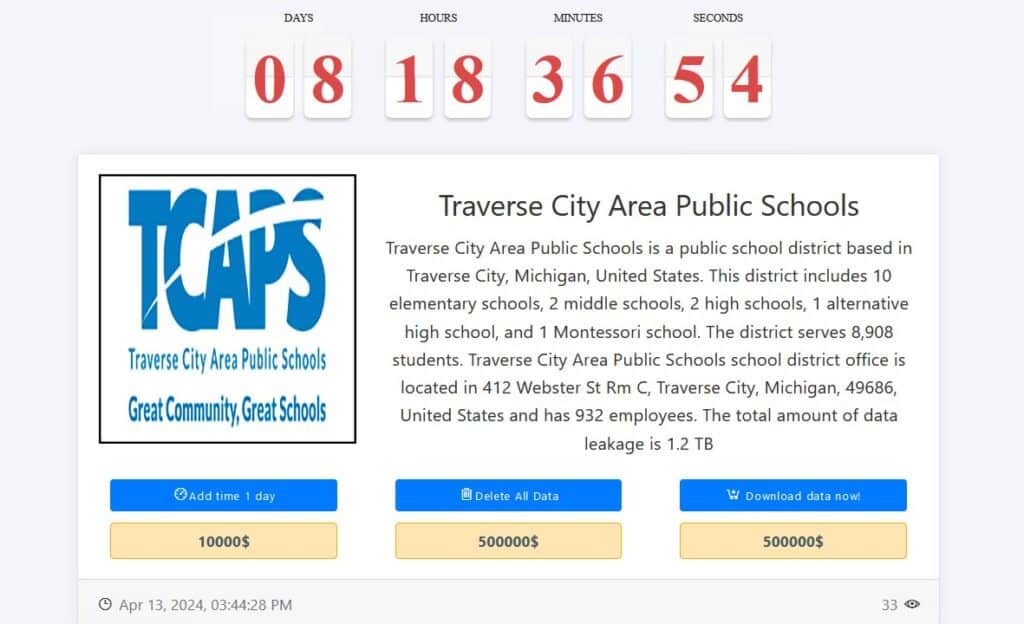
Traverse City Area Public Schools
Ransomware group Medusa over the weekend claimed an attack that forced Traverse City, Michigan area public schools to cancel classes two week prior. On its leak site, Medusa says it stole 1.2 TB of data, and is demanding a $500,000 ransom in exchange for not selling or publicly releasing it. The school district has not confirmed the ransom.
Traverse City Area Public Schools initially called the incident a “network disruption,” and canceled classes for the first two days of April. It has not stated whether any student or staff data was stolen, and we do not know what data Medusa is holding for ransom.
SMRT Architects & Engineers
SMRT issued a data breach notification to 348 people after a December 2023 cyber attack. Ransomware group Play claimed the attack.
The compromised data mainly pertains to employees and includes names and Social Security numbers.
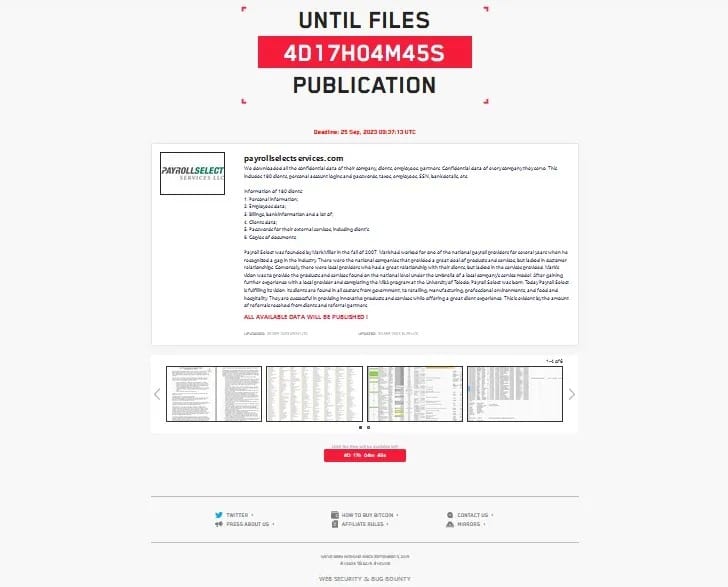
Payroll Select Services
Payroll Select Services sent a data breach notification (PDF) to an undisclosed number of victims regarding a September 03 cyber attack. Ransomware group Lockbit claimed the attack.
The data included names, addresses, dates of birth, financial info including banking and billing info, and Social Security numbers.
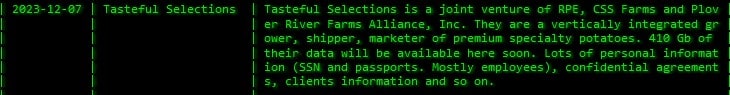
Tasteful Selections
Bite-sized potato company Tasteful Selections issued a data breach notification to an undisclosed number of people regarding a November 2023 cyber attack.
The data included names, Social Security numbers, state-issued ID numbers (e.g. driver’s license), financial account info, and health insurance info.
AllCare Pharmacy
AllCare Pharmacy notified (PDF) an undisclosed number of people about a breach that it detected on September 21, 2023. The data included names, addresses, dates of birth, prescriptions, Social Security numbers, and credit card numbers.
Ransomware group Lorenz claimed the attack in October 2023.
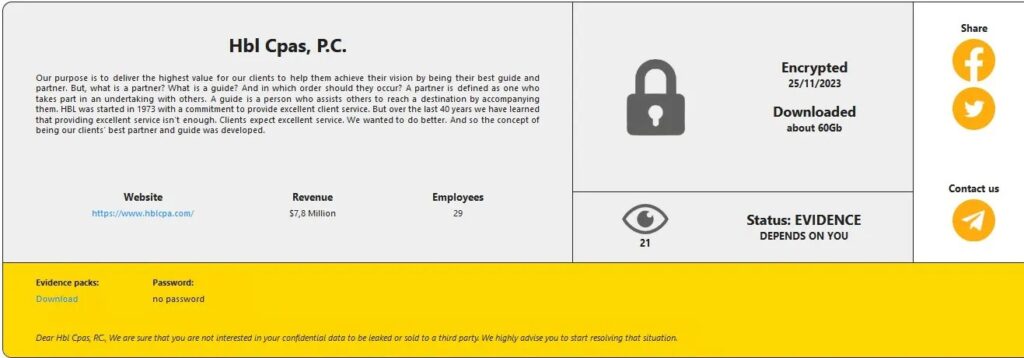
HBL CPAs
Arizona accounting firm HBL CPAs notified 1,206 people of a data breach that occurred on November 30, 2023. HBL didn’t discover the breach until April 5, 2024. RansomHouse claimed the attack.
The compromised data included names and state-issued ID card numbers (e.g. driver’s license number).
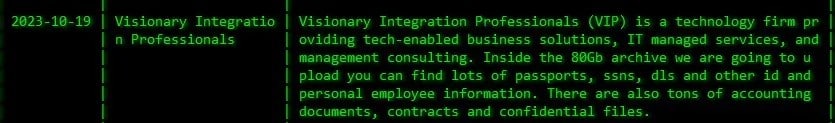
Visionary Integration Professionals
Visionary notified an undisclosed number of people about a September 2023 cyber attack that exposed Social Security numbers. Ransomware group Akira claimed to steal 80 GB of accounting documents from the company.
No ransom was paid, according to the notification letter.
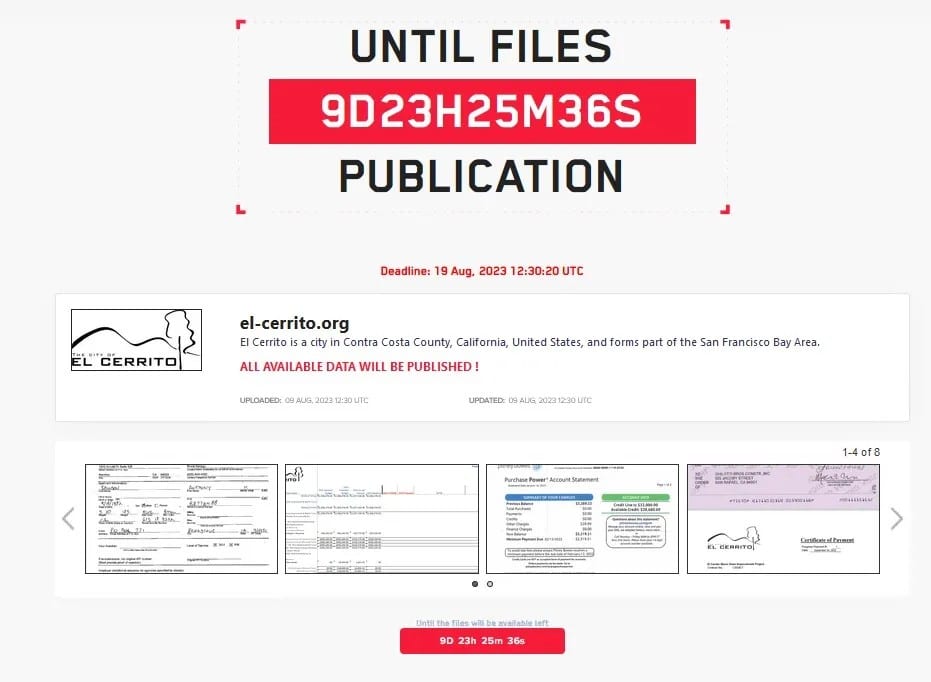
El Cerrito, California
The city of El Cerrito notified (PDF) an undisclosed number of people about a ransomware attack that was first confirmed in August 2023. Ransomware group Lockbit claimed the attack.
The city has not publicly shared what information was compromised.
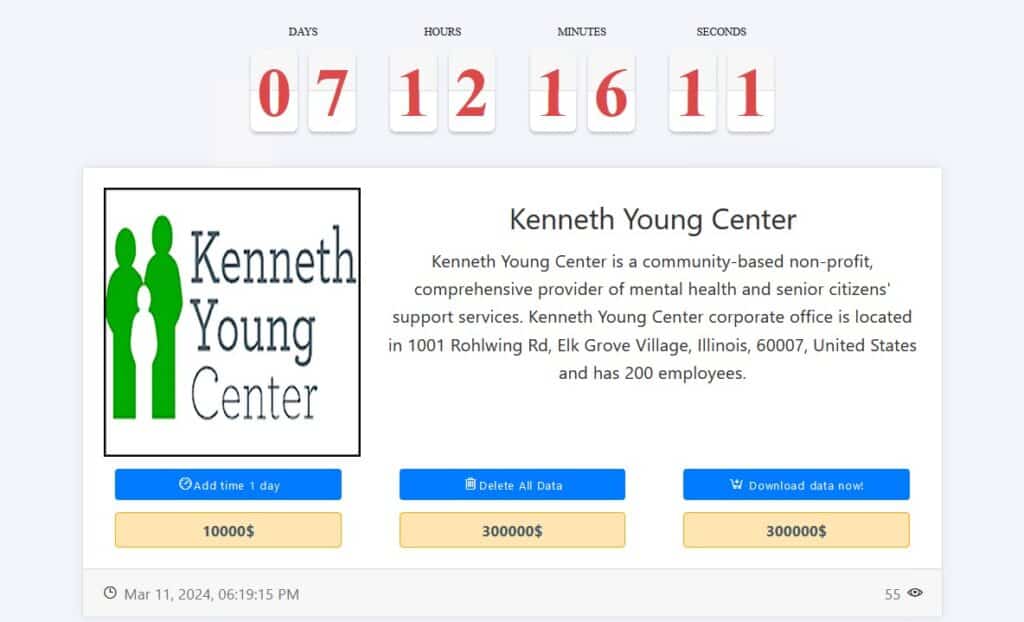
Kenneth Young Center
Social services not-for-profit Kenneth Young Center issued (PDF) notifications to an undisclosed number of people regarding a cyber attack that occurred last month. Ransomware group Medusa claimed the attack.
The data includes Social Security numbers, driver’s license info, financial account info, passport numbers, medical info, health insurance info, and dates of birth.
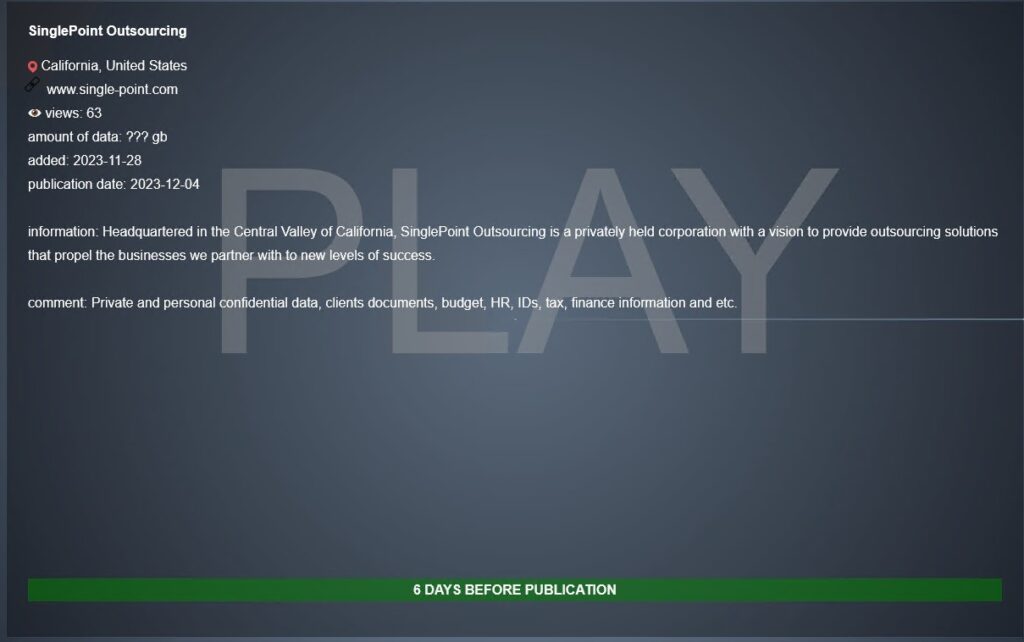
SinglePoint Outsourcing
SinglePoint has now notified 11,096 people about a cyber attack that was claimed by the Play ransomware group in November 2023. SinglePoint discovered the breach in January and publicly confirmed it in February 2024.
The data includes Social Security numbers, driver’s license numbers, and bank account info.
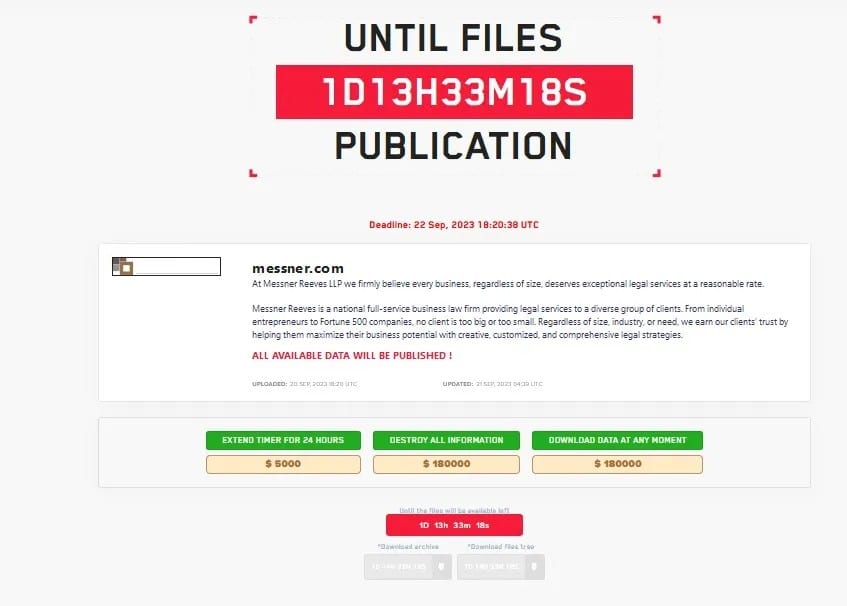
Messner Reeves LLP
Law firm Messner Reeves on Monday issued (PDF) a data breach notification regarding an attack that occurred in July and August 2023. Ransomware group LockBit claimed the attack and demanded $180,000 in ransom.
Messner Reeves hasn’t publicly stated what data was affected.
Alan Ritchey
Logistics company Alan Ritchey confirmed 4,657 Texans’ personal information was compromised in a February 2024 cyber attack. Ransomware group Black Basta claimed the attack. The company first started sending breach notifications in March.
Alan Ritchey has not publicly disclosed what information was compromised.
Arby’s (DRM)
DRM, a company that owns and operates more than 100 Arby’s restaurants, on April 17 sent a data breach notification (PDF) to 5,290 Iowa residents. The compromised data includes Social Security numbers, passports, driver’s licenses and medical information from a worker’s compensation claim.
Ransomware group Cactus claimed the attack, saying it stole 175 GB of data.
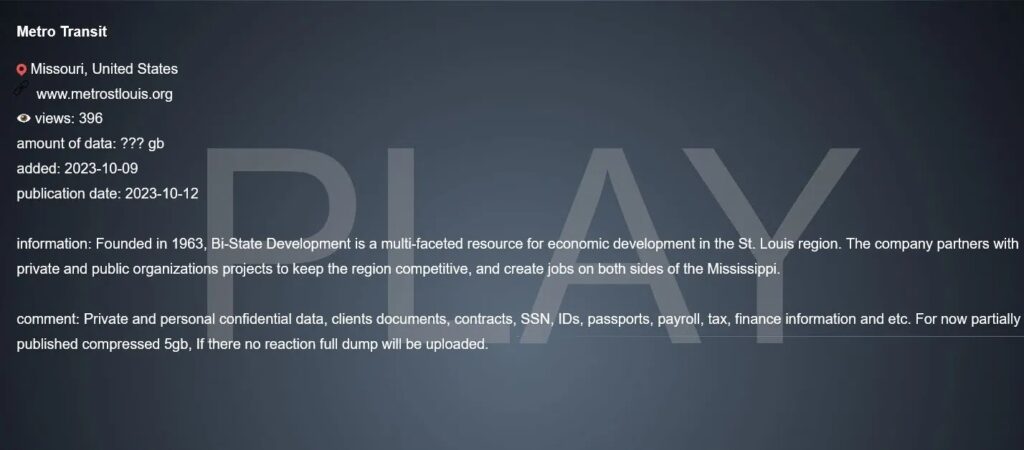
Bi-State Development (St. Louis Metro Transit)
Bi-State Development, which operates the St. Louis Metro Transit system, regional freightway, and downtown airport, and has notified 21,953 people about a data breach that occurred on October 1, 2023. It began notifying individuals on March 25, but didn’t announce the number of victims until April 18.
The data includes names and Social Security numbers. Ransomware group Play claimed the attack, but no ransom was paid.
Taft Stettinius & Hollister LLP
The law firm raised the number of victims affected by an October 2023 ransomware attack from 641 to 5,980. The breach wasn’t discovered until April 3, 2024, and the first batch of victims were notified on March 11.
Ransomware group BlackByte claimed the attack. The data included names and Social Security numbers.
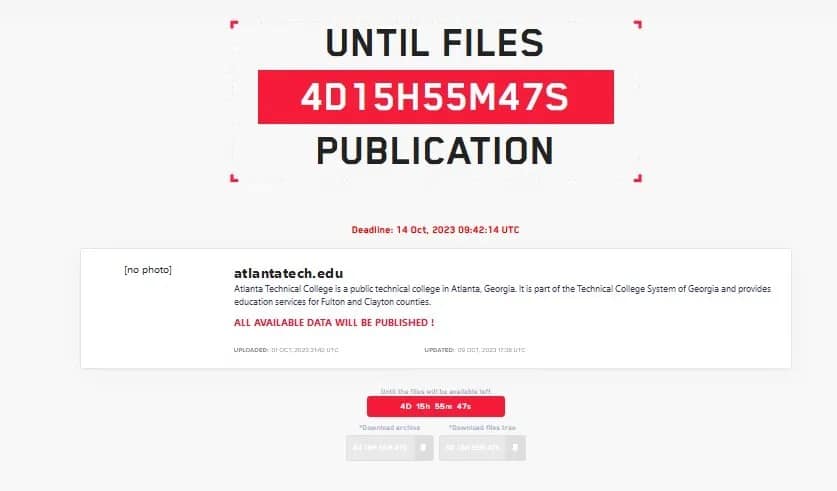
Atlanta Technical College
The College issued a notification (PDF) to 1,523 people regarding an August 2023 cyber attack. Ransomware group LockBit claimed the attack.
The data includes names and Social Security numbers.
Carl Buddig and Company
Lunchmeat manufacturer Card Buddig and Company on April 17 confirmed an April and May cyber attack that affected 11,830 people. No one has claimed responsibility as of time of writing. The data included names and state-issued ID numbers (e.g. driver’s license numbers).
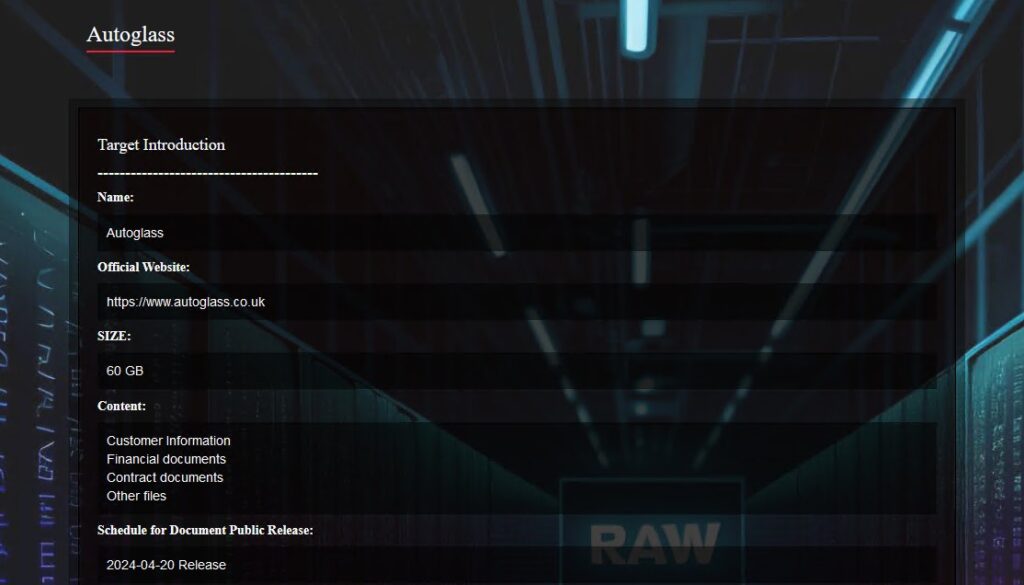
Autoglass (unconfirmed)
Ransomware group RA Team (a.k.a. RA World) on April 16 said it stole 60 GB of data from UK automotive glass maker Autoglass.
Autoglass has not verified the claim.
National Naval Aviation Museum (unconfirmed)
New ransomware group Dispossessor on Friday claimed to have hacked the National Naval Aviation Museum in Florida. The Museum has not verified the claim.
Delano Join Union high School District (unconfirmed)
Ransomware group Inc Ransom on April 17 claimed it hacked the DJUHSD. The district has not verified the claim.
Omni Hotels and Resorts (unconfirmed)
Ransomware group Daixin on Monday claimed an attack on Omni Hotels and Resorts, saying it stole records of all visitors from 2017 to present.
Omni has not verified Daixin’s claims.