Here are the latest ransomware-related news stories from the past week!
Crinetics Pharmaceuticals
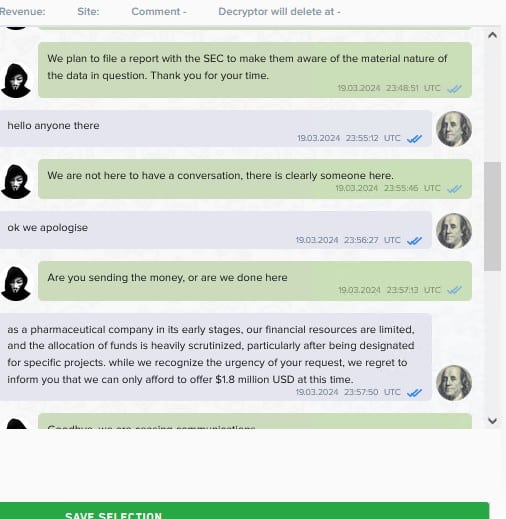
Ransomware group Lockbit Thursday posted chat logs that it says took place between itself and Crinetics Pharmaceuticals. The conversation apparently shows negotiations breaking down over LockBit’s $4 million ransom demand.
Crinetics in mid-March announced it was investigating a cybersecurity incident after it discovered “suspicious” activity on an employee account. LockBit claimed responsibility for the attack around the same time, saying it stole confidential data.
Crinetics has not confirmed LockBit’s claim.
Pensacola, FL
The city of Pensacola, Florida is notifying an undisclosed number of people that their private information was compromised in a March 2024 data breach.
The impacted data includes first and last names, Social Security numbers, ID card numbers (e.g. driver’s license), passport numbers, military ID numbers, and health insurance policy numbers. An investigation of the incident wrapped up on April 2, 2024.
The attack took down the city’s phone lines and several online services, including bill payment, and the FBI came in to investigate the incident. No cybercriminal groups has taken responsibility for the attack as of time of writing.
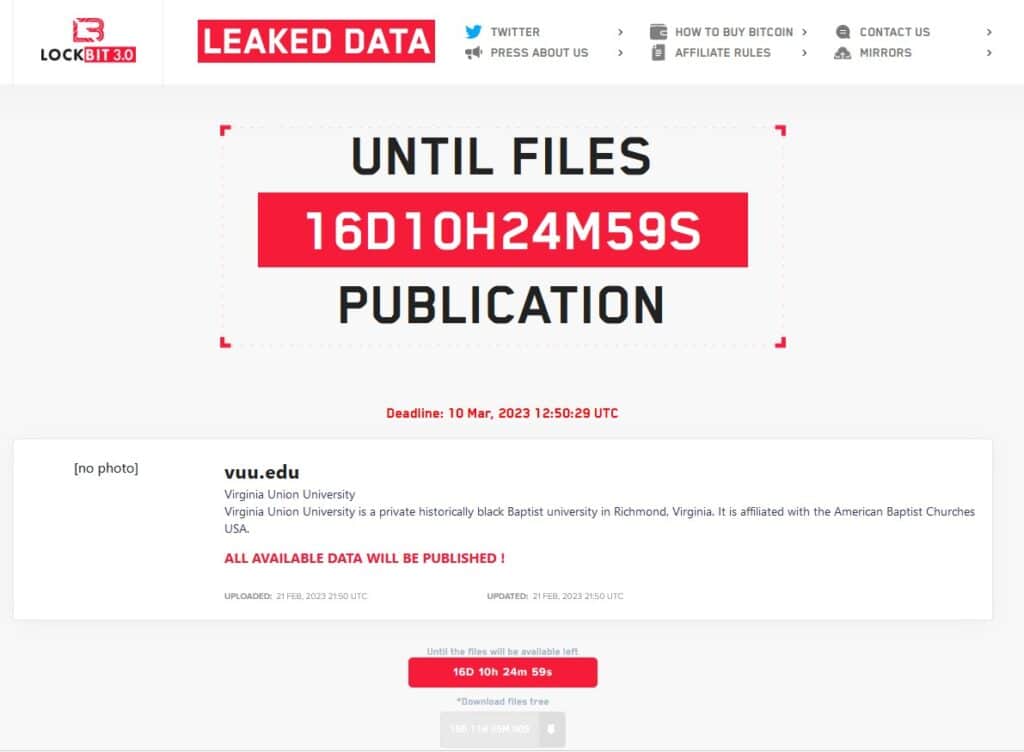
Virginia Union University
Virginia Union University on May 1 began issuing data breach notifications to those involved in a cyber attack back in February 2023. A cyber attack that was claimed by the LockBit ransomware gang at the time.
In its data breach letter, VUU says it first detected unauthorized activity on its systems on February 13, 2023. On April 1, 2024, it was discovered that certain files containing personal information might have been acquired or accessed by unauthorized individuals. The number of affected individuals is unknown.
Affected data includes names, SSNs, dates of birth, and state issued ID number (e.g. driver’s license).
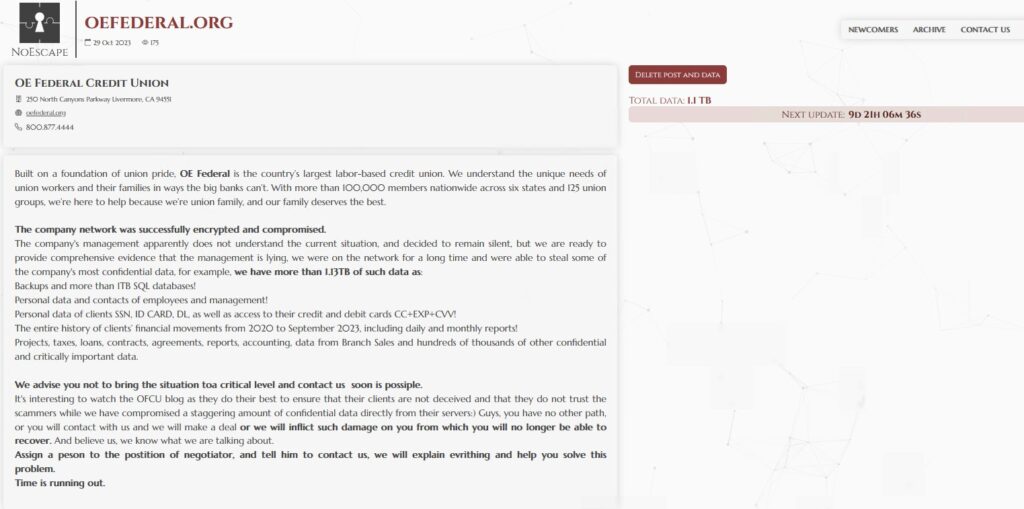
OE Federal Credit Union
OE Federal Credit Union this week notified an undisclosed number of people about a data breach that took place at the end of October 2023. The data includes “Social Security number, date of birth, bank and/or financial account information, routing number, credit and/or debit card number, expiration date, Taxpayer Identification Number, driver’s license or government ID number, username and password, passport number, medical procedure information, clinical or treatment information, medical provider name, medical record number, prescription information, and health insurance information.”
Ransomware group NoEscape claimed the attack on October 29, 2023, and claimed to have stolen 1.13 TB of data.
The Philadelphia Inquirer
The Philadelphia Inquirer on April 29 notified 25,549 people of a data breach that compromised their personal and financial information.
The breach took place in May 2023. In an update posted April 26, 2024, Inquirer CEO Lisa Hughes stated that Social Security numbers, driver’s license numbers, financial account information, and medical information might have been accessed.
Ransomware group Cuba claimed the attack at the time, saying it stole “financial documents, correspondence with bank employees, account movements, balance sheets, tax documents, compensation, source code.” The Inquirer has not confirmed Cuba’s claims.
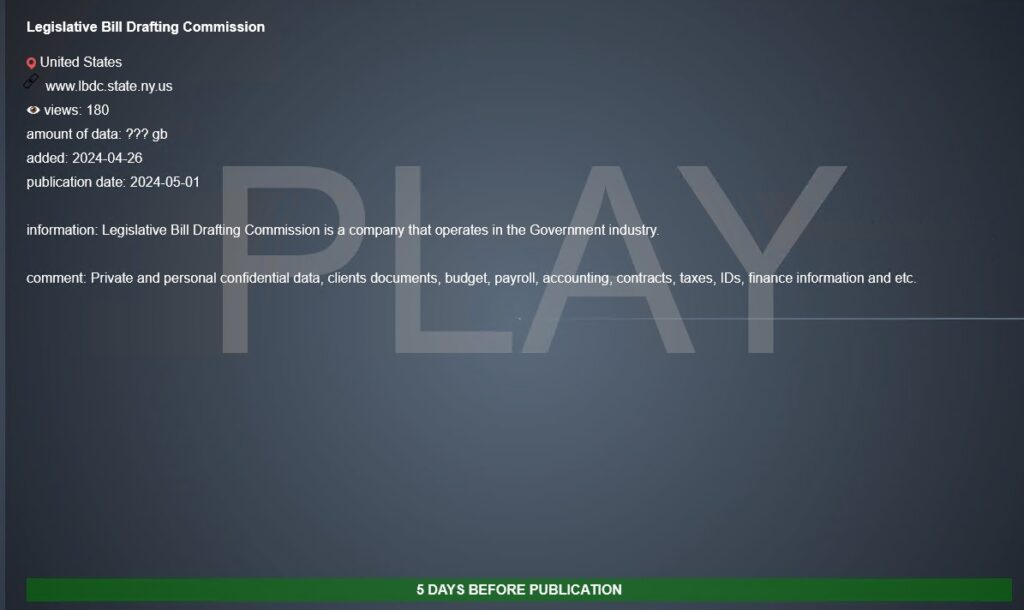
New York Legislative Bill Drafting Commission
Ransomware group Play over the weekend claimed a cyber attack on New York State’s Legislative Bill Drafting Commission. The group claimed to steal an undisclosed amount of data including “private and personal confidential data, clients documents, budget, payroll, accounting, contracts, taxes, IDs, finance information, and etc [sic].”
New York’s Bill Drafting Commission went down last week as a result of the attack, casting doubt on the passage of an already delayed state budget. New York State officials have not confirmed Play’s claim.
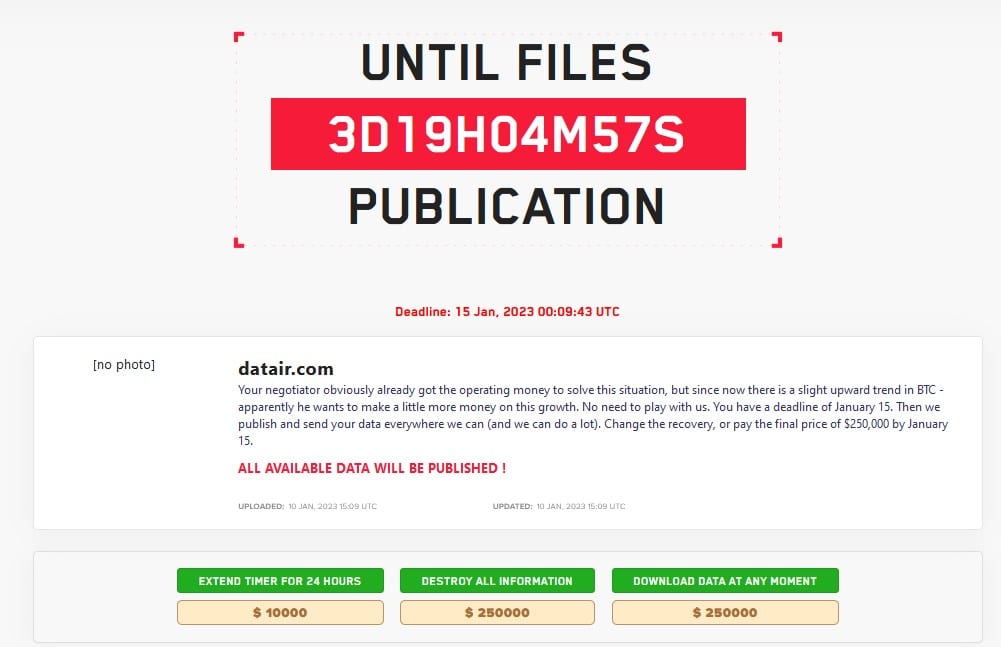
DATAIR
Software company DATAIR Employee Benefit Systems started notifying people of a data breach on April 29 following a ransomware attack way back in December 2022. LockBit claimed the attack and published its negotiation chats with the company. After communications broke down, LockBit demanded $250,000 and placed the organization on its data leak site.
Sterling Plumbing
Sterling Plumbing this week began notifying (PDF) and undisclosed number of victims about a March 2024 cyber attack. Sterling did not disclose what data was affected.
The attack was claimed by rnasomware group RA World.
Numotion
Wheelchair maker Numotion increased the number of victims notified about an April data breach to at least 10,957, according to newly issued notifications in South Carolina and other states.
Numotion on April 15 notified 4,190 people of a data breach that compromised names, Social Security numbers, dates of birth, and employment information.
Ransomware group Black Basta claimed the attack, which took place from February 29 to march 2, 2024.
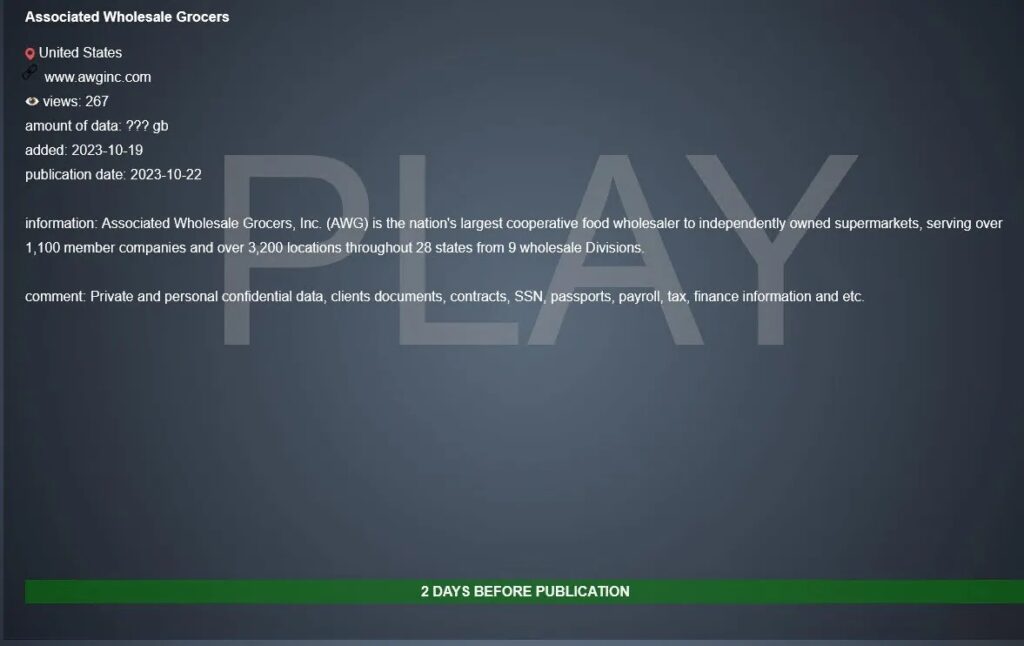
Associated Wholesale Grocers
Associated Wholesale Grocers on April 29 notified 26,579 people of an October 2023 data breach that compromised names, SSNs, and dates of birth.
Ransomware group Play claimed the attack.
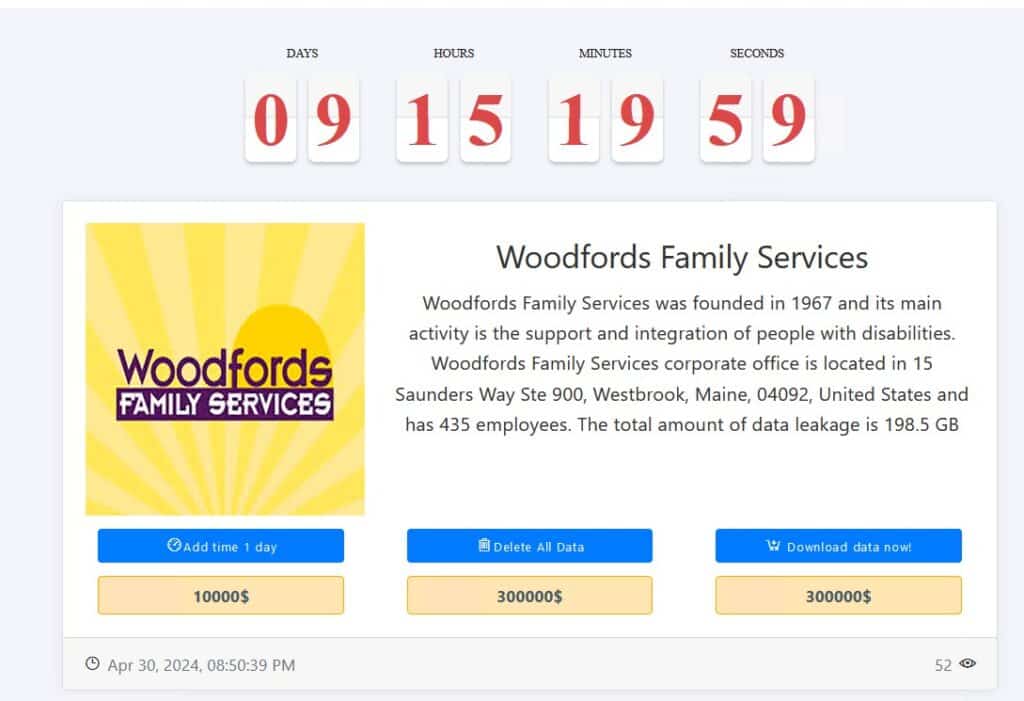
Woodfords Family Services (unconfirmed)
Ransomware group Medusa on April 30 added Woodfords Family Services to its leak site, demanding a ransom of $300,000 in exchange for 198.5 GB of allegedly stolen data. Woodfords has not confirmed Medusa’s claim.
Woodfords in December 2023 issued 17,285 notifications for what was most likely a separate cybersecurity incident that took place in June 2023.
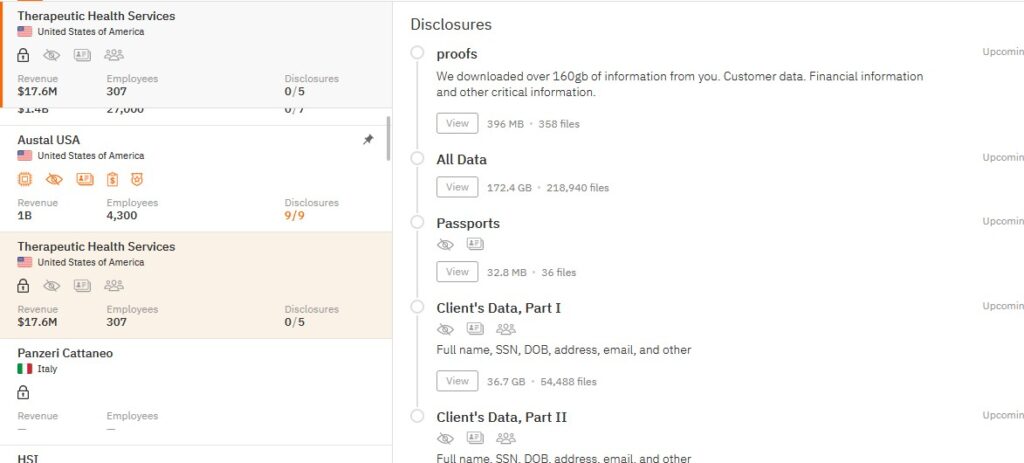
Therapeutic Health Services
Therapeutic Health Services on April 25 submitted a breach notification to the US Department of Health and Human Services’ breach reporting tool. It says 501 people were affected.
Ransomware group Hunters International claimed an attack on Therapeutic Health Services in March 2024. It posted a proof pack that contained passports and various client data.
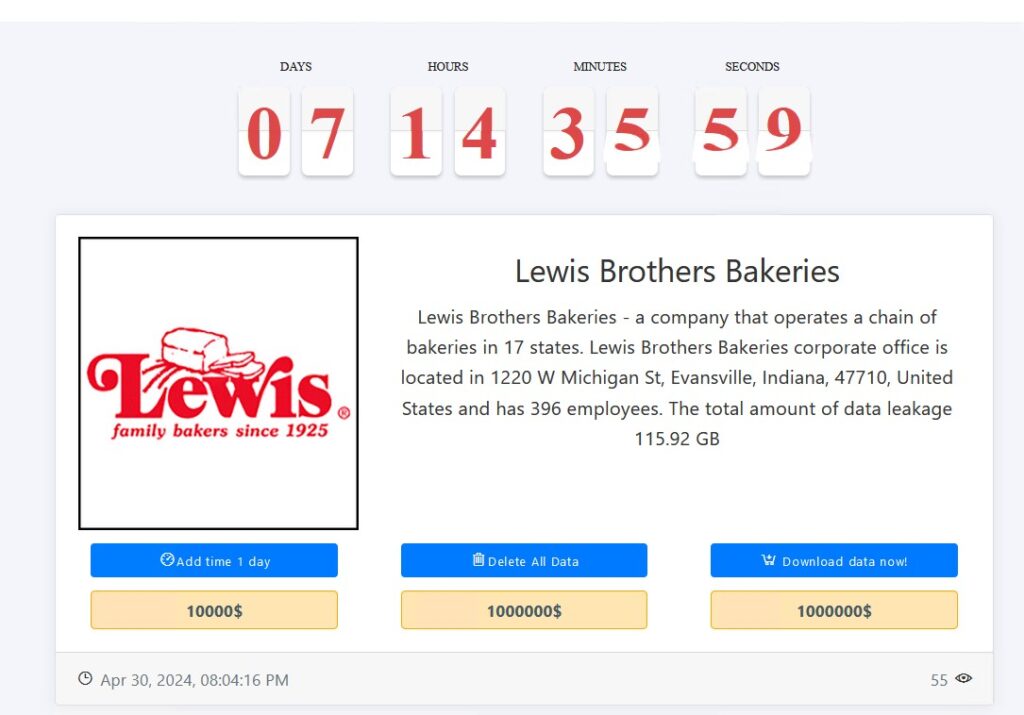
Lewis Brothers Bakery (unconfirmed)
Ransomware group Medusa added Lewis Brothers Bakery to its leak site and is demanding a $1 million ransom in exchange for 116 GB of data.
Lewis Brothers has not confirmed Medusa’s claim.
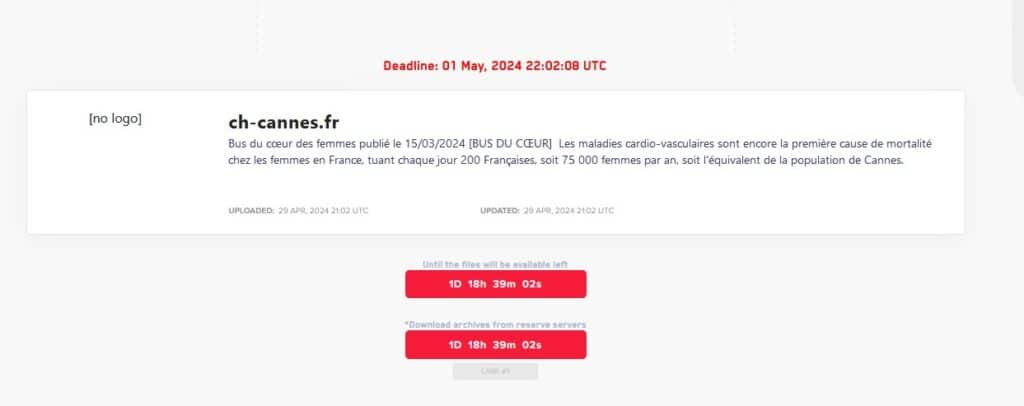
Cannes Hospital
Ransomware group LockBit on April 29 claimed an attack on Cannes Hospital, which has been suffering from a cyber attack for nearly two weeks. Cannes’ offical statment says it hadn’t received a ransom demand or detected any data theft as of April 17.
Chambers Construction
1996 LLC dba Chambers Construction Co. on April 29 notified 489 people of a March 2024 data breach that compromised names and Social Security numbers.
Ransomware group BianLian claimed the attack, saying it stole 4.2 TB of data, including finance and human resources files.
Worthen Industries
Worthen Industries on April 29 notified 693 people that their personal information was compromised in a November 2023 data breach. The data includes names and Social Security numbers, among other info.
Ransomware groups BlackCat, 8Base, and LockBit have all claimed attacks on the company.
Burch & Cracchiolo
Law firm Burch & Cracchiolo on April 23 started issuing data breach notifications (PDF) to an undisclosed number of victims regarding a May 2023 cyber attack.
The firm has not disclosed what data was involved, but ransomware gang ALPHV/BlackCat, which claimed the attack, says it stole 390 GB of internal company data including SSNs, credit card info, and financial data.
Coffee County, GA
Coffee County, Georgia on April 27 announced it might have been the victim of a ransomware attack. The county’s internet connection was cut off for two days as a precaution.
No ransomware group has claimed responsibility as of time of writing.
Lagunitas Brewing Company
Lagunitas on April 26 notified 2,979 people of a data breach that occurred in March 2024. The compromised data belonged to employees and their beneficiaries, and included names and state-issued ID numbers (e.g. driver’s licenses).
Ransomware group Black Basta claimed the attack.
Francis Howell School District
The District on April 25 started issuing data breach notifications (PDF) to an undisclosed number of victims regarding a February 2024 ransomware attack. The District has not publicly disclosed how many people were affected or what information was compromised.
No ransomware gang has claimed the attack as of time of writing.
Want more? Check out our ransomware tracker, updated daily!