Hernando County, Florida (unconfirmed)
Ransomware group Rhysida set a price of 40 Bitcoin, worth $2.84 million at time of writing, for what it says is data and files stolen from the Hernando County, Florida government.
The county earlier this month announced it had “experienced and interruption of the county-wide IT network.” Emergency services remain operational, but many other county operations were or still are delayed.
Comparitech has not confirmed whether the IT outage and the allegedly stolen data were part of the same attack.
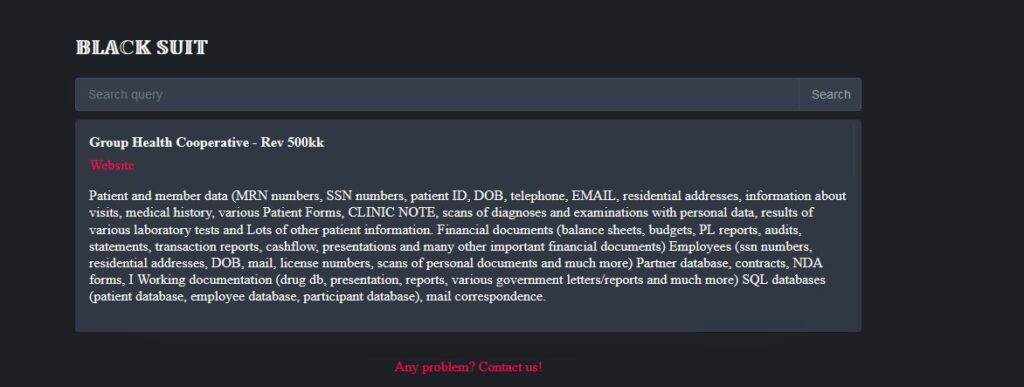
Group Health Cooperative of South Central Wisconsin
Group Health Cooperative of South Central Wisconsin issued a notification confirming a January ransomware attack affecting 533,809 patients and employees.
The compromised data includes personal health information, names, addresses, phone numbers, email addresses, dates of birth, Social Security numbers, member numbers, and Medicare and/or Medicaid numbers.
Ransomware group BlackSuit claimed the attack. It’s the second biggest ransomware attack this year so far, behind Loan Depot.
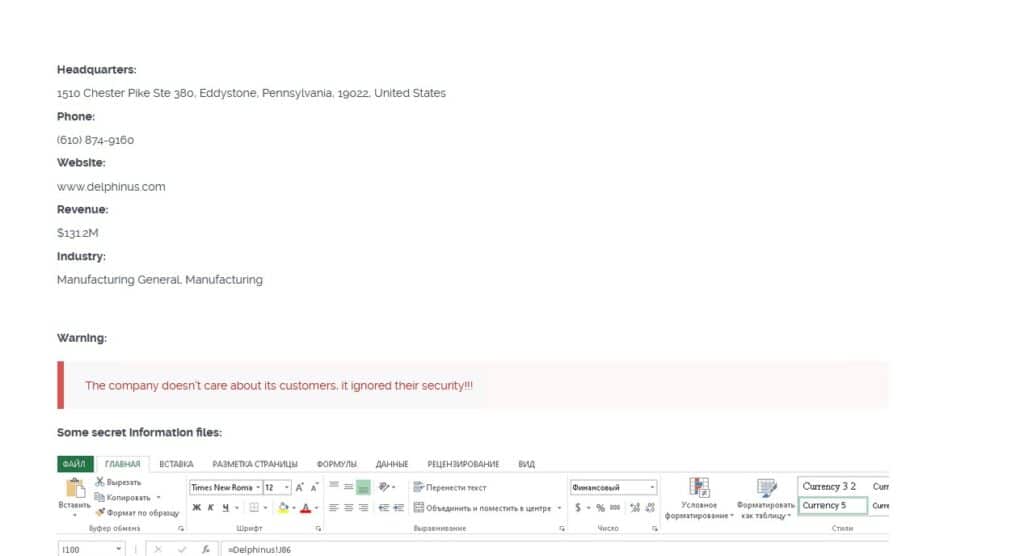
Delphinus Engineering
US Navy contractor Delphinus Engineering on April 11 confirmed an October ransomware attack that affected 2,232 people. The compromised data included names, Social Security numbers, dates of birth, and passport numbers.
The attack began on October 16, 2023, but wasn’t discovered until December 12, 2023 when ransomware group Cl0p claimed responsibility. Delphinus notified affected persons on April 10, 2024 following remediation and an investigation.
Cl0p posted a proof pack of the stolen data allegedly containing employee information, incident reports, contractor’s documents, agreements, and financial data.
McAlvain Companies
McAlvain Companies, an Idaho-based large construction firm, on April 4 confirmed a data breach that leaked confidential human resources info including employee Social Security numbers, names, addresses, and dates of birth.
Ransomware group Cactus claimed the attack last month. McAlvain has not stated how many people were affected, how attackers infiltrated its systems, or whether a ransom was demanded. McAlvain has 250 employees, according to its website.
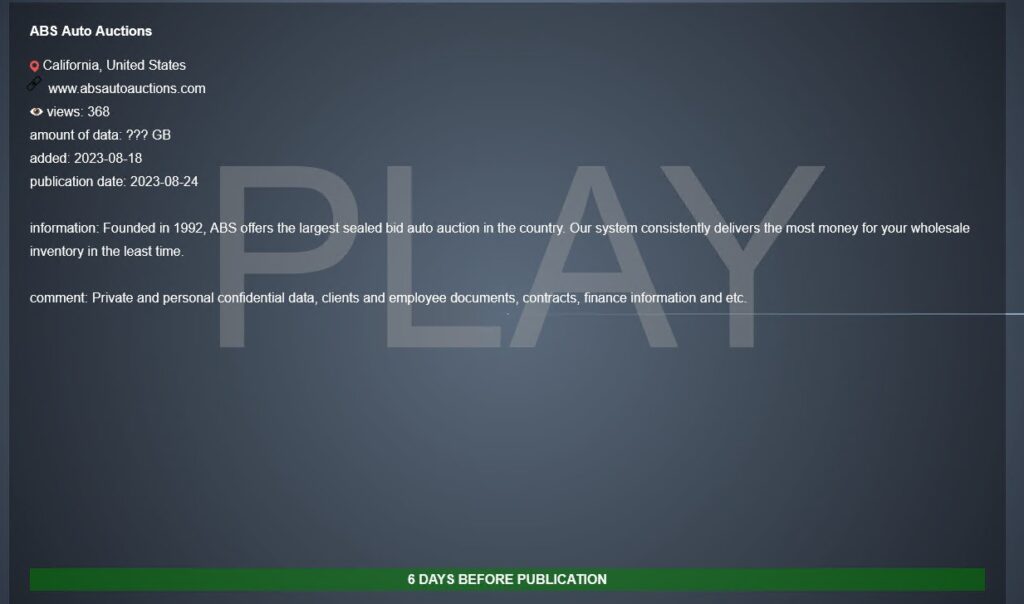
Eblock
Car auction website EBlock on Monday notified customers of a data breach affecting the personal information of nearly 2,000 people. The attack compromised users’ Social Security numbers, bank account and routing numbers, driver’s license numbers, names, and dates of birth.
Ransomware group Play claimed the attack in August 2023. It says it stole an unspecified amount of “private and personal confidential data, clients and employee documents, contracts, finance information and etc.”
EBlock says all impacted systems have been secured and restored, but nearly eight months passed between the attack and Eblock notifying customers.
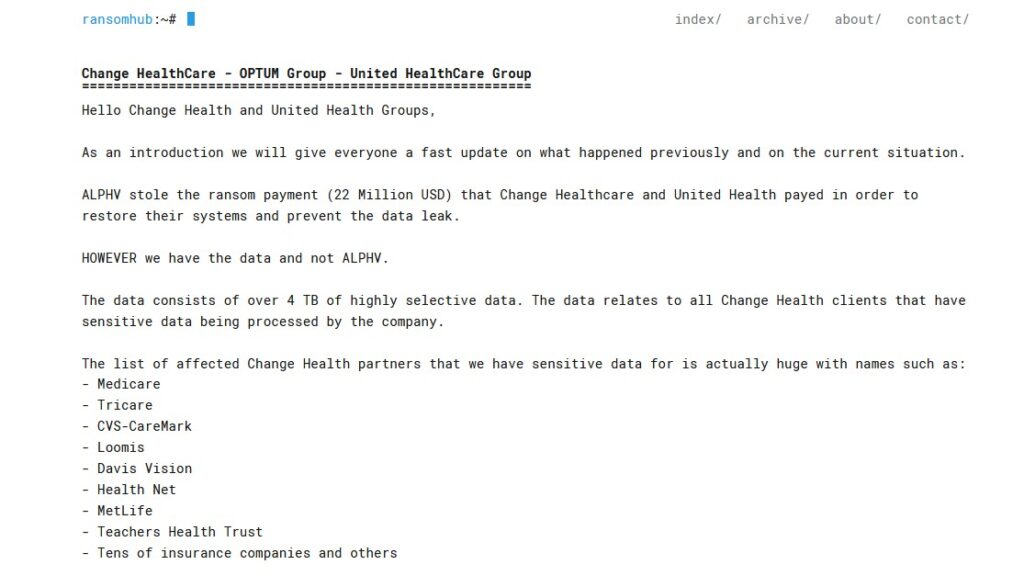
Change Healthcare (unconfirmed)
In response to a ransomware attack that caused days of outages across the US healthcare system, United Healthcare’s Change Healthcare subsidiary reportedly chose to pay $22 million to hackers.
Despite the ransom reportedly being paid, however, another ransomware group now claims to possess the stolen data. RansomHub, a relatively new hacker group, says it has access to 4TB of the data originally stolen by ALPHV/BlackCat.
The claim has yet to be verified by Change Healthcare and its partners.
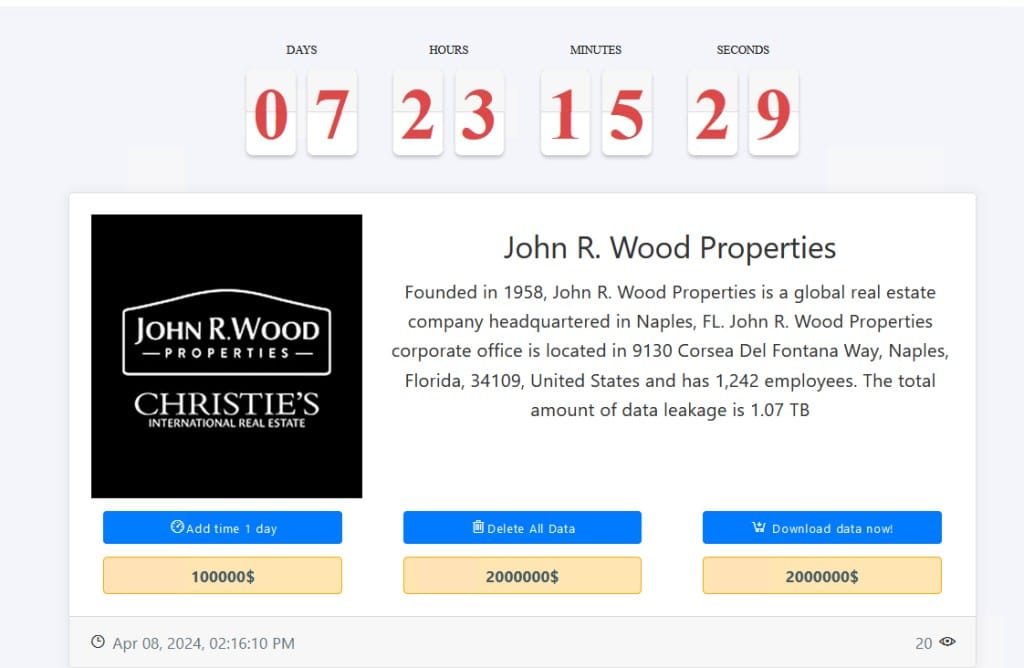
John R. Wood Properties (unconfirmed)
Ransomware group Medusa on April 8 claimed it hacked Florida real estate company John R. Wood Properties and stole 1.07 TB of data. On its leak site, Medusa demanded $2 million to delete the data and not sell or release it.
John R Wood has not confirmed the attack
Canopy Children’s Solutions
Following an April 2023 ransomware attack, Canopy in February 2024 started notifying 19,190 data breach victims that their personal information might have been compromised. However, victims in some states weren’t notified until this week.
The data included names, Social Security numbers, driver’s license numbers, state ID numbers, financial account info, medical info, and health insurance info.
Ransomware group Nokowaya claimed the attack, saying it downloaded 150 GB of private data.
St. Lucie, FL County Tax Collector’s Office
The St. Lucie County Tax Collector this week notified an additional 2,232 victims who were affected by an October 2023 data breach. That brings the total number of victims to 25,202. The data included names, Social Security numbers, and driver’s license numbers.
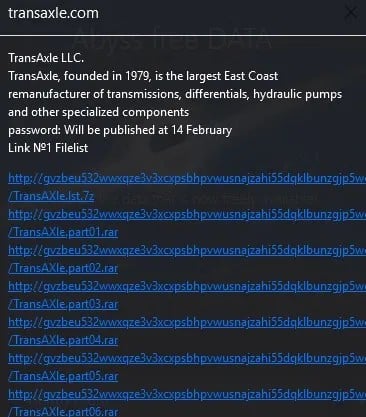
Transaxle
Auto part manufacturer Transaxle on Thursday confirmed a January ransomware attack that affected the personal info of 401 people. The data included names and possibly Social Security numbers. Ransomware group Abyss claimed the attack.
New Mexico Highlands University
The university confirmed a ransomware incident that forced the school to cancel classes and take several university systems offline, including the MyNMHU portal and payroll.
The University suffered a previous ransomware attack in October 2019.
The University has not stated whether any student or faculty personal information was compromised in the attack.
Benetton Group
Italian fashion brand Benetton Group confirmed a January 2023 data breach was the result of an attack from ransomware group Hunters International. Hunters claimed to steal more than 433 GB of files from the company. Benetton said no company activity has been compromised.