UPDATE: November 15, 2021 – Stripchat have now acknowledged a breach incident. In addition to continuing their investigation into the incident they state they are also communicating with data protection authorities to reduce any potential harm.
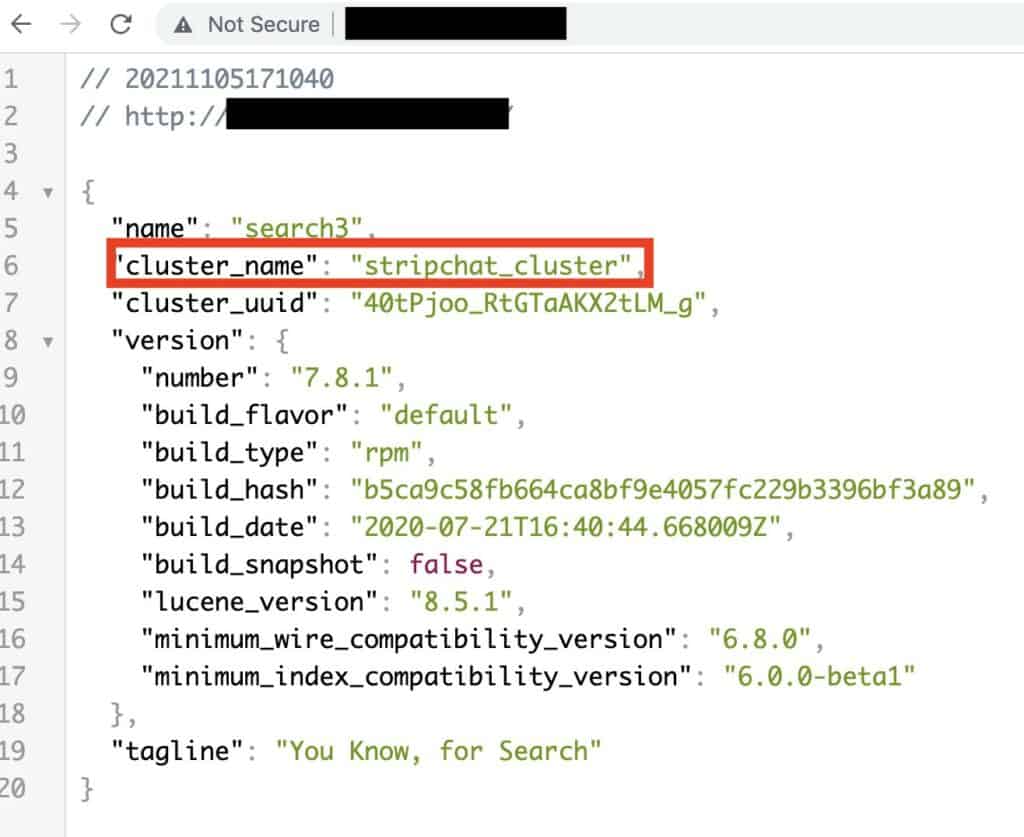
Comparitech’s cybersecurity research team led by Bob Diachenko discovered an exposed database that appears to belong to live sex cam website Stripchat.
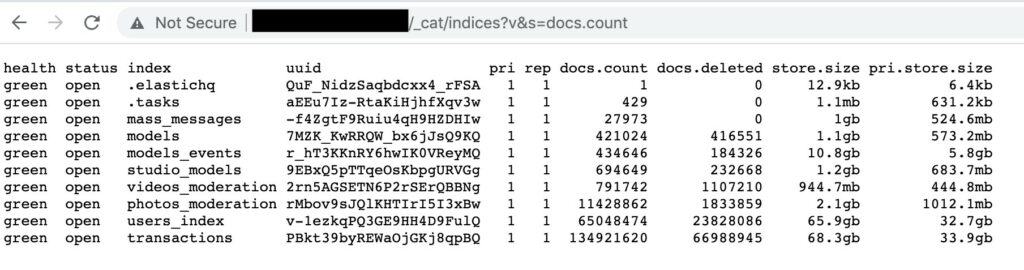
The exposed database makes multiple references to Stripchat and consists of nearly 200 million records. Exposed data includes email addresses, usernames, and IP addresses, among other info, seemingly about the site’s users and models.
Comparitech discovered the exposed database and alerted Stripchat on November 5, 2021 in accordance with our responsible disclosure policy. The database was secured two days later.
Our usual process is to contact the affected party so that they can investigate the incident and take appropriate action including informing affected users.
We reached out to Stripchat multiple times via email and Twitter but Stripchat has not responded nor acknowledged our disclosure or requests for comment at time of publishing.
Timeline of the exposure
The database was accessible on the internet without a password or any other authentication required. Here’s what we know happened:
- November 4, 2021 – The database was indexed by search engines.
- November 5, 2021 – Diachenko discovered the database, determined the owner, and sent an alert to Stripchat per our responsible disclosure policy.
- November 7, 2021 – The database was no longer available.
We do not know how long the database was exposed for prior to being indexed by search engines. Our honeypot experiments show that attackers can find and access unprotected databases in a matter of hours.
What information was exposed?
The Elasticsearch cluster contained about 200 million records in total, comprised of several databases:
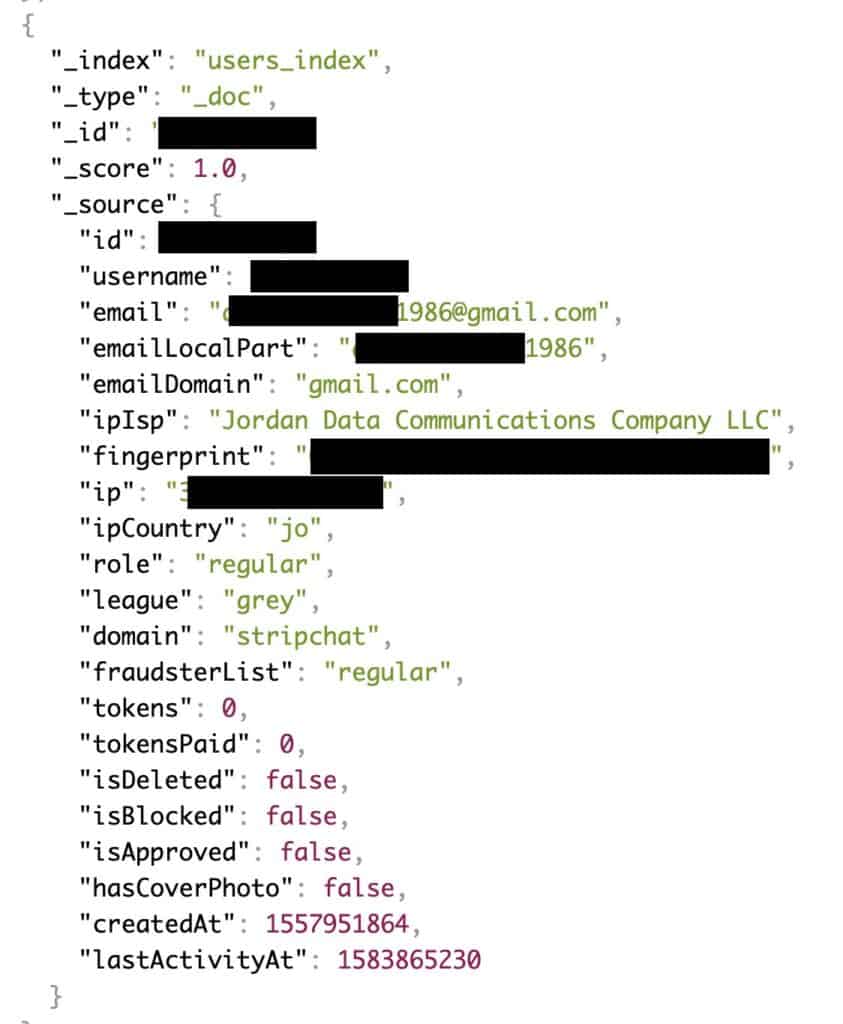
A user database containing circa 65 million records, each with some or all of the following info:
- Email address
- Username
- IP address
- Internet service provider
- Tip balance
- Timestamp of account creation
- Timestamp of last activity
- Blocked status
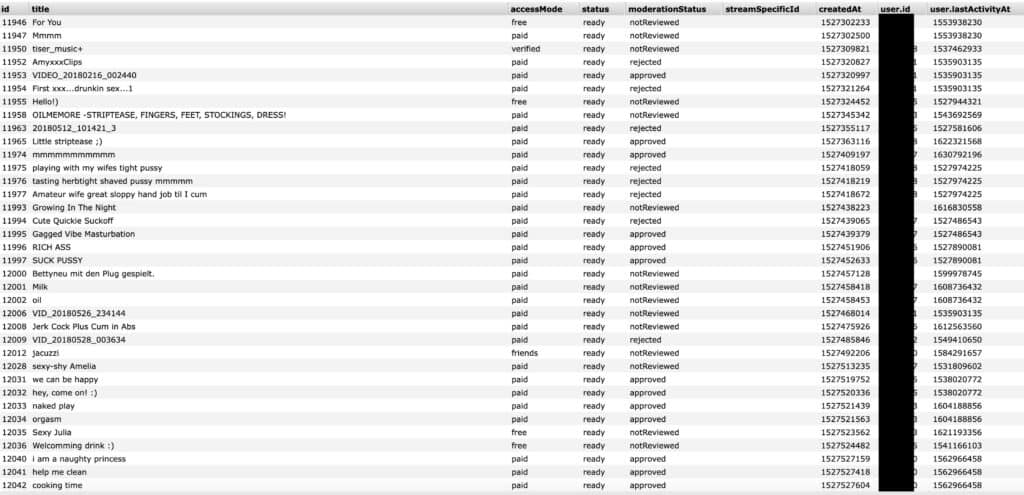
A model database of about 421,000 records, each with some or all of the following info:
- Username
- Gender
- Studio ID
- Live status
- Tip menus and prices
- Strip score
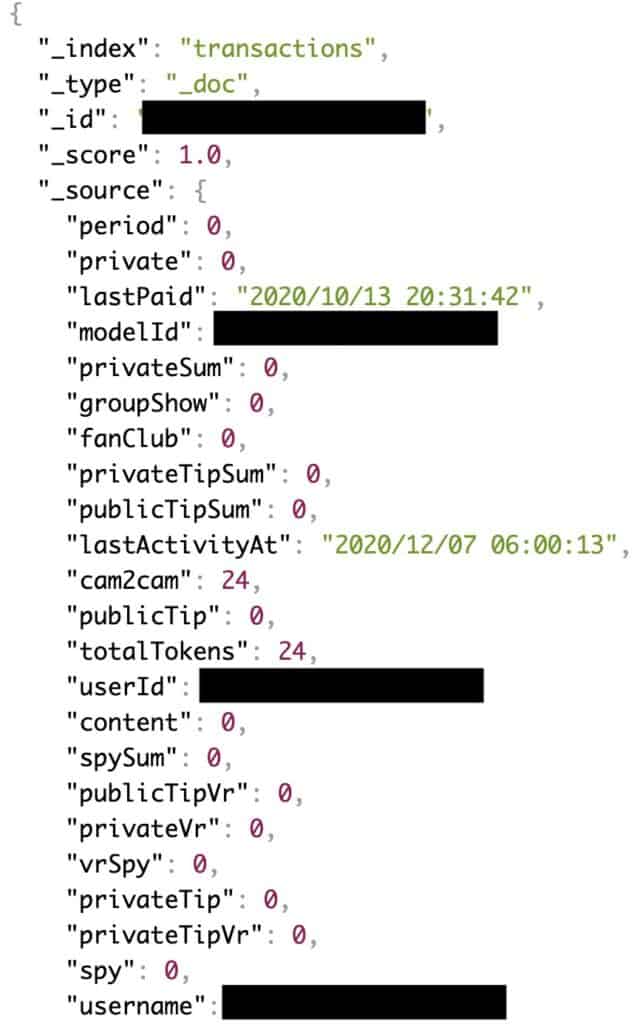
A transaction database of circa 134 million records with information about tokens and tips paid by users to models, including private tips.
A moderation database of about 719,000 chat messages sent to models, including both private and public messages. Each record contains the user ID of the viewer who sent the message.
Dangers of exposed data
The exposure could be a digital and physical threat for both Stripchat viewers and models. IP addresses, which can be used to approximate someone’s location, are particularly worrying. They could enable someone to find and stalk, harass, or even assault someone in the database.
Aside from physical violence, the identifying information could be used to extort, bully, or humiliate victims who thought their online activities were private.
Lastly, victims should be on the lookout for targeted phishing emails from fraudsters posing as Stripchat or a related company. Never click on links or attachments in unsolicited emails. Stripchat says that if “you have any doubts regarding a message or an email received from us, our models or users, do not hesitate to contact our customer support and we will be at your disposal”.
About Stripchat
Stripchat is an adults-only website featuring live webcam performances, usually of nudity or sexual activity. The company was founded in 2016 and is incorporated in Cyprus.
A company blog post notes Stripchat saw a 72 percent increase in traffic in 2020 following the start of the Covid-19 pandemic, including more than 900 million new users and 300,000 new models.
Users don’t need to register an account to view public cams, but an account is required to tip, chat, or make a session private. To create an account, users must enter a username and valid email address. Those wishing to “tip” models will need to purchase tokens by entering their payment details on the site.
Why we reported this incident
Comparitech’s cybersecurity research team regularly searches the web for unsecured database containing personally identifiable user information. When we find an unprotected server, we immediately begin an investigation to find out to whom it belongs, who could be affected, and potential consequences for end users.
After verifying the identity of the responsible party, we alert them according to our responsible disclosure policy. Once the data has been secured and our investigation completes, we publish an article like this one to raise cybersecurity awareness and curb harm to end users.
Previous data incident reports
Comparitech has reported on several data incidents similar to the Stripchat information leak:
- Personal info of 106 million international visitors to Thailand exposed online
- 35 million US residents’ personal details exposed on the web
- India visa agency exposes 6,500 traveler’s visa applications on the web
- Prison phone service Telmate exposes messages, personal info of millions of inmates
- Social media data broker exposes nearly 235 million scraped profiles
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database
-
US schools leaked 32 million records in 2,691 data breaches since 2005
-
5 billion records from previous data breaches leaked by cybersecurity company
Breaches involving personal data can be devastating. News stories often focus on the financial cost to the company, but the effects on those whose data is stolen can be long-lasting and multi-faceted. The mere association of a person’s data with a particular site — such as Stripchat — can make it easy for attackers to extort money from victims.
For example, gigabytes of user data was stolen from Ashley Madison — a website that claims to facilitate extramarital affairs — in 2015. The fallout from the attack — which continues even now — resulted in divorces, suicides and irreparable damage to reputations and families.