
With so much of our lives spent online, digital security has never been more important. A single mistake or oversight can lead to our personal information being released to the public for all the world to see. The simple truth is, as long you’re using the internet, you’re vulnerable. Unless, of course, you’re using highly secured network access, or you’re accessing websites and data online through secured encryption methods.
In this article, we’ll discuss two tried and tested ways of increasing your online security: SOCKS5 proxy and VPN, we’ll discuss the difference between them and help you figure out which one will work best for you.
Encryption methods: HTTPS is great, except when it isn’t
Some aspects of online encryption and data security are taken care of for you. That’s because most websites have a vested interest in preventing hackers from grabbing your data. Data breaches are a growing problem and an extremely expensive one at that. Yahoo can certainly attest to this, having paid over $350 million in legal fees after more than 3 billion accounts were breached in 2016.
There’s been a rapid uptick in the number of websites using HTTPS, with around 95 percent of all sites listed by Google encrypting user traffic this way. Websites with HTTPS encryption typically utilize Secure Sockets Layer (SSL) encryption. This creates a secure connection between your computer and the website’s hosting servers. Once connected, the data transfers between your computer and the website’s servers are encrypted. The information is scrambled, as is typical of encryption methods, with the data unscrambled using secure keys on both ends. It’s pretty easy to identify when a website is using HTTPS as well. Just look to the website address:
Even Google uses encryption methods for its search engine. But don’t be fooled. Although HTTPS encryption is far more secure than the encryption-lacking HTTP protocol, it’s far from an end-all security method. Anyone snooping in on your online activity or the website’s servers can still see what you’re viewing and steal data or your identity. On a similar note, as wonderful as HTTPS encryption is, it does not hide your location. Someone can still identify who you are through your IP address and connect that to publically available information.
HTTPS is a good, secure method to help ensure your data isn’t stolen during the transfer process, but it’s not securing your identity online, and it’s not keeping your data wholly private.
The tried and true virtual private network (VPN)
Virtual Private Networks (VPNs) are perhaps the most common method for securely connecting, downloading, and surfing online. All computers that use internet connections are part of a larger, shared network. If you connect to the internet through your internet service provider, the ISP assigns your computer a unique IP address and sends you on your merry way through their network, connecting you to the rest of the web. Unfortunately, it’s then very simple for the ISP to monitor your activity. And any government or government organizations that have access to the ISP’s data can do so too.
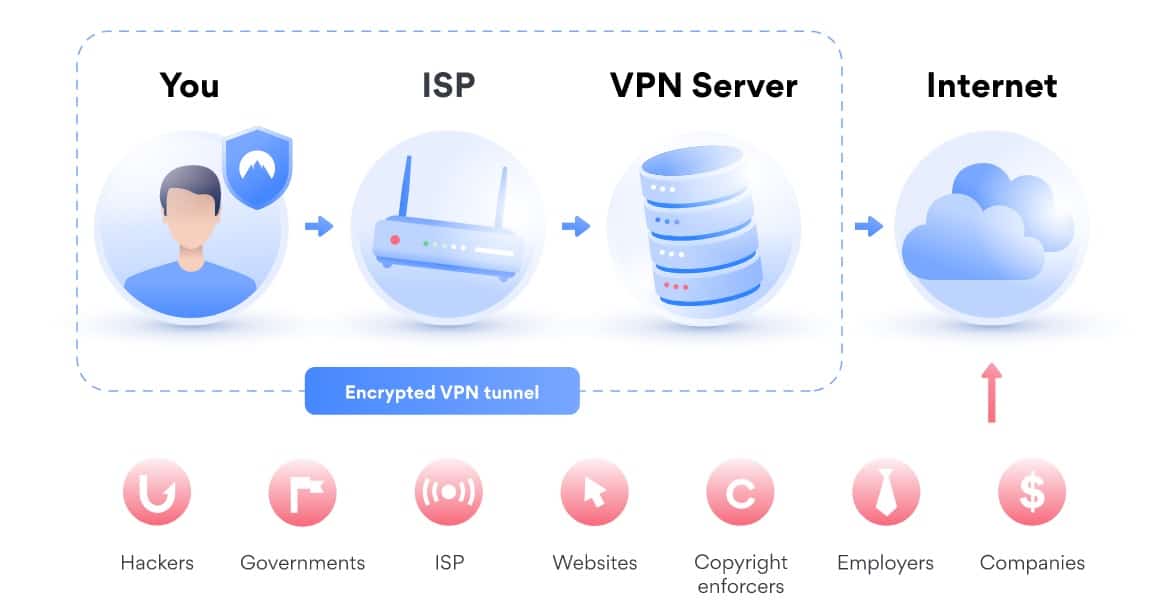
VPNs, however, create a secure tunnel between you and a private server. You connect online through your ISP as usual, but you then connect securely and directly to a specific server.
NordVPN, one of the largest VPN services available, provides a helpful graphic to visualize what we mean:
The secure tunnel created by a VPN means a direct connection is created between you and the websites you’re trying to access. Hackers, governments, and even your own ISP can no longer see what you’re doing.
The benefits are pretty clear, but a VPN is also limited in many ways. Because your data has to travel further and is encrypted and decrypted several times over in the process, your original internet speed gets significantly reduced. On a similar note, if you’re connecting to a VPN server that’s far away from you, you’ll experience a reduction in speed.
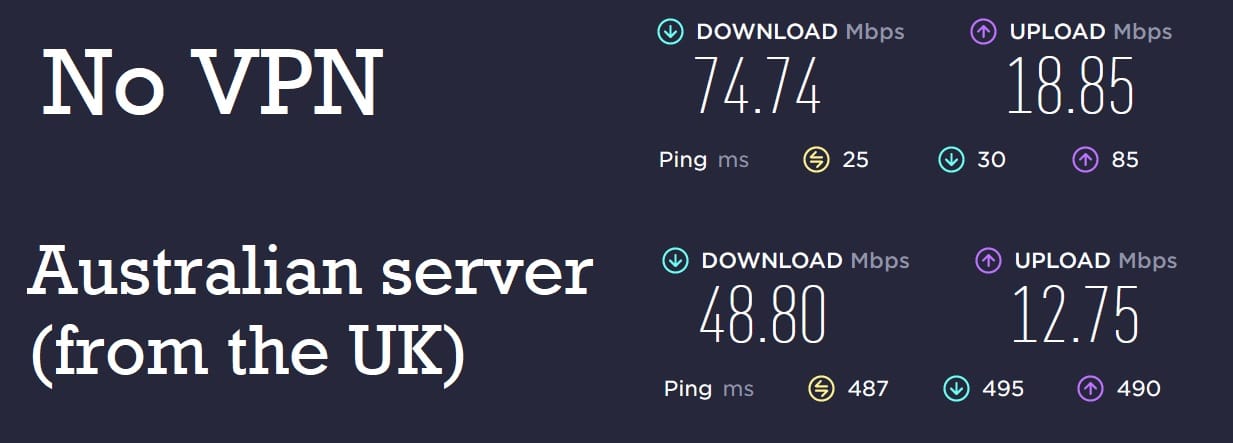
Take, for example, what happens when you’re in the U.S. and connect to a VPN server in Australia versus when you’re not connected to a VPN server at all:
The ping (the time it takes for a packet of data to travel back and forth between two locations) rises dramatically. The increased ping should not increase users too much, in so far as a high ping does not always equate to slower download speeds. However, higher ping can also be an indication of a rather packed server, something that is often the case with more popular VPN services and free VPN services in particular. Usually, VPN services get around this by increasing the number of servers they offer.
As for download speeds, here’s a simple comparison between what speeds (in seconds) are like downloading through a paid VPN service (NordVPN), free VPN (TunnelBear) and no VPN. Note that we used British VPN servers to keep things as fair as possible:
As evidenced by the results, downloading without a VPN gives the best speeds, while VPNs significantly impact download speeds. As is common, the paid VPN service was faster than the free service. For more information on VPN speeds, check out our article on the fastest VPN services and on why measuring VPN speed is not straightforward.
VPNs are also limited by the security measures implemented by the hosting VPN company. Most paid VPN services ramp up their security efforts, offering all forms of high-level encryption as well as maintaining strict log-free policies in most cases.
The SOCKS5 proxy server question
So, is there a way to connect securely to a VPN without the added data slowdown? Yes, proxy servers do just that. Indeed, a proxy server acts just like a VPN, but without the added encryption. A proxy server assigns you a new IP address as you connect to the server and then routes you to wherever you’re trying to go. There is some security in that. Anyone looking in will perceive your location differently due to the new IP address. However, the lack of encryption means that the data is basically unsecured. One of the most secure kinds of proxy, SOCKS5, works to alleviate some of the insecurity involved.
VPN services NordVPN and Private Internet Access each provide SOCKS5 proxy servers to subscribers. NordVPN describes the benefit of SOCKS5 in this way:
“[The] main advantage of SOCKS5 is the additional ability to provide authentication so only authorized users may access a server. This makes it more secure than other proxy servers.”
Indeed, this is a problem we addressed earlier in our brief discussion of HTTPS. While you may be able to connect securely to a website and transfer data back and forth without anyone stealing or snooping on it, if someone has access to the server you’re connecting to, all of that security is effectively meaningless. Because SOCKS5 proxy servers use an SSH (secure socket shell) protocol, they can only be accessed through verification. Not just anyone can connect, and someone trying to gain access improperly has a large amount of encryption to deal with.
The benefit to a SOCKS5 proxy service is speed. The lack of encryption with a proxy server, and even a more secure SOCKS5, help ensure that faster speed. Keep in mind that for the most part, the data going back and forth is not really encrypted, just the access to the SOCKS5 proxy server. Most services that provide SOCKS5 proxies give advanced warning that the proxies are less secure. Take the upfront warning given by NordVPN, for example:
“SOCKS5 is not as secure or as fast as a VPN. It’s easy to confuse a SOCKS5 proxy with a VPN, but there are crucial differences. Like most proxies, SOCKS5 won’t encrypt your data, and will lower internet speed and stability.”
This is why SOCKS5 proxies are more popularly used for web activities that don’t involve connecting to different websites where your data may be easily obtained. Outside of less encryption, proxy servers also often log activity. This means that anyone who can get access to those logs can find out both who you are and what you were doing while routing data through the proxy. Additionally, proxy servers that have been hacked are more likely to push malware and viruses onto your machine.
SOCKS5 proxy VS VPN: which should you use?
As you might expect, there are clear benefits to using SOCKS5 proxies over VPNs and vice versa, it depends on what you are trying to achieve.
Here is when to use a SOCKS5 proxy vs VPN:
Best uses for SOCKS5 proxy servers:
- More bandwidth required
- Torrenting or using peer-to-peer services (speed purposes only)*
- Hiding your location
- Bypassing geographic or content blocking
- Improved security over regular proxies
Best uses for a VPN:
- Secure web browsing
- Torrenting or using peer-to-peer services (when more encryption and security is desired)
- Getting past firewalls
- Bypassing geographic or content blocking
- Better privacy protections than SOCKS5
SOCKS5 proxy vs VPN: which to use for torrenting and P2P
If your entire goal is to torrent or utilize a P2P service with the fastest speed, your best option may be to use a SOCKS5 proxy. However, the faster speed will come at the cost of significantly reduced privacy, at the risk of drawing attention to yourself from your VPN. However, if your goal is to torrent with the maximum amount of encryption and privacy, go with a VPN. The speed will be noticeably slower, but with the right VPN service, the damage can be lessened a bit (see our article on the best VPNs for torrenting for more details). Additionally, SOCKS5 proxies only connect select applications to the web, so it’s important to remember that some of your computer’s internet-related activities will not be hidden while connected to a SOCKS5 proxy.
If your goal is to do a large amount of web surfing, get past firewalls, or simply protect your entire online presence regardless of the online activity, you’re better off using a VPN. The speeds will be lower, but not unbearably, so if you utilize a higher-quality paid service like those from IPVanish and NordVPN. Both services, in fact, have both SOCKS5 proxies and VPN servers.
For a better idea on the additional benefits provided by VPN services, you can check our reviews of NordVPN, IPVanish, and Private Internet Access.
*Torrenting, while connected to a proxy, is not wholly anonymous. Your ISP may still be able to see that you’re uploading and downloading large amounts of data. The primary benefit to using a SOCKS5 proxy for P2P is the better upload and download speed, as well as the fact that monitoring organizations cannot connect the newly assigned IP address back to you. This results in more privacy than complete anonymity.
See also: The Best Socks5 VPNs
SOCKS5 proxy vs VPN: FAQs
Should I use both a proxy and a VPN?
You can technically use a proxy and a VPN at the same time, but there aren’t really very many cases where you’d want to. After all, a VPN encrypts your traffic and hides your location, so changing your IP address again using a proxy doesn’t really do very much for you unless you don’t trust your VPN provider to keep your source IP address private (in which case, we’d suggest switching to a different VPN provider entirely, ideally one that keeps no logs).
Even in this situation, there’s a heavy price to pay. Proxies and VPNs both slow down your internet speeds, and with both active, your connection will be bottlenecked by the slower of the two services. In short, we’d recommend choosing one or the other based on your activity instead of trying to use both simultaneously.
Which costs more: a proxy or a VPN?
Proxies and VPNs are both available at a variety of price points, though generally, you can expect to pay a little more for a high-quality VPN provider since these have higher operating costs (thanks to their network of servers all over the world and the technical teams required to keep their encryption up-to-date).
It’s also possible to find free providers for both services, although this often comes at a cost of lesser security.
Will a free VPN keep me safe online?
Many people are hesitant to cough up money for a VPN service when there are countless VPN services available online for free. However, there’s a good reason why it’s better to pay for a VPN service than to go with a free one. Free VPNs often cap data or bandwidth, log your activity, and/or inject advertisements into your web browser. Not only do free services have fewer resources to pour into bandwidth and servers, but many are also lacking in security features.
Free VPNs are often ad-driven, displaying ads in their own apps, injecting ads into your browser, or both. As many of us may know by now, advertisements can be used by hackers (called “malvertising”) to infect computers with viruses and malware of various sorts. Ad-driven VPNs are hardly secure.
While price is important, we strongly suggest looking at other factors first. For instance, how fast is your chosen service? Is it secure enough for your needs? Has it handed over personally-identifiable data to authorities in the past? These are fundamental things to consider, especially if you’re going to trust a company with your personal information. And if possible, we recommend opting for a trustworthy, reliable paid VPN.
Can ISPs see Socks5 proxies?
Socks5 proxies can be used to mask a user’s IP address and maintain anonymity while online. However, it is important to note that ISPs can still see the user’s traffic when using a Socks5 proxy. This is because the Socks5 proxy only encrypts the data between the user and the proxy server.
Should I use a free SOCKS5 proxy?
No, we don’t recommend you use a free SOCKS5 proxy. While you can find free SOCKS5 proxies, they tend to suffer from a number of issues. In particular, free proxies will offer inferior performance due to the fact that they’re free and lack the necessary infrastructure. However, the main issue of free SOCKS5 proxies is that they may put your security and privacy at risk. Many free proxy services monitor user traffic. This data may then be sold to third parties.









Sorry but I never get such speed results, since VPN provider has limited speed too. For eg. right now:
No VPN: Ping 15ms; D 110Mbps; U 6Mbps;
ExpressVPN(UK): Ping 18ms; D 58Mbps; U 5Mbps;
The point I want to say, that on higher speeds it depends of VPN provider too.
I’m sorry, I don’t understand these points for VPN:
– “[…] (when more encryption and security is desired)”
– “Better privacy protections than SOCKS5”
VPN offering better privacy is only true if you’re talking about a shared SOCKS5 proxy (one that is accessed by many people). If you get yourself your own cheap Linux based VPS, you can set up your own private SOCKS5 tunnel using SSH and it’ll be just as private as any VPN.
As for encryption, I’m fairly certain the encryption of traffic tunneled over SSH is just as secure as traffic over VPN, if not more.
I think people need to remember that effective selective routing of internet traffic through a private SOCKS5 tunnel is more advanced than just connecting to a VPN (which just routes ALL your internet traffic through it). How well you’re secured very much depends on whether or not you’ve correctly configured all the relevant software to route your internet traffic through your SOCKS5 proxy. For example, remembering to configure your system to send/receive all DNS requests via proxy, not just your web browsing data.
In the end, SOCKS5 may require some more work/knowledge but it allows selective proxification and thus the ability you to avoid certain situations/problems faced when using VPN. Examples of problems include:
– Want to play a multiplayer game but VPN adds moderately or greatly to the ping (latency) so you need to turn it off every time you wish to play.
– Turning on VPN, starting a large HTTP download, then you wish to do something that requires turning off your VPN (such as playing a multiplayer game or connecting to an external server that identifies you by your original IP). You end up aborting the download or waiting (possibly for a long time) for the download to finish before you can turn off your VPN.
so using an encrypted torrent app like deluge plus SOCKS5 (important to make sure that it does not leak) my isp can’t detect me directly? i use to get copyright notices from my isp all the time then i read up on socks5 and ip leaks, remedied the situation in firewall to allow only a certain proxy to connect and zero notices! also use a web browser proxy when grabbing torrents. but sometimes i have trouble getting the torrent to start and have to turn off the proxy for a moment. doing this i still haven’t had any notices so its all good??
Turning off the proxy for torrents to start is definitely bad…. something is not right.