Malicious advertising, or malvertising is a common technique that cybercriminals use to initiate their attack campaigns. They may pay for display ads or even take over entire ad networks. When site visitors come across these ads, the attackers leverage a range of different techniques to infect them with malware, often without even requiring the target to click on the ad. That’s right, it’s possible to be attacked purely by visiting a site that hosts malicious ads.
What are malvertising attacks used for?
Malvertising is one of the many techniques that cybercriminals use to initiate their attacks. In general, their ultimate desire is to try and make money (although sometimes they are involved in espionage or sabotage). To get to this end goal, they usually have to install malware at some stage of the process.
Historically, cybercriminals have often accomplished this over email, whether by spearphishing individual targets or blasting out spam in the hopes of tricking users into downloading treacherous software.
Instead of meeting their targets in their inboxes, malvertising gives attackers the opportunity to infect people’s computers as they surf the web. When site visitors come across malicious ads that have been planted by cybercriminals, they may be forced to download the malware automatically. Alternatively, sneaky tactics may be used to trick them into clicking and executing the download.
What happens next will vary from attack to attack. Sometimes the site visitor directly downloads the malicious payload. At other times they may be redirected, shuffled around, and forced into executing malicious code bit-by-bit until finally the attacker has the malware they really want on their victim’s computer.
The ultimate payload may be one of the following, or a combination of them:
- Spyware – This type of malware can take screenshots, take over the microphone and camera, log keystrokes, and even seek out passwords as well as other sensitive information. Attackers use these details to penetrate systems even further, to extort people, or even to commit identity theft.
- Ransomware – When ransomware makes its way onto a target system, it searches through the folders and locks down any files that it thinks may be important. Attackers then demand that victims make ransom payments with cryptocurrencies, saying they will send victims a key that can unlock the files if they comply. Even in cases where victims pay up, there’s no guarantee that the attacker will send them the key. If they’re unlucky, they may end up with their files permanently locked up and down the thousands of dollars of the ransom payment.
- Trojans – These are often used to give attackers backdoor access to a system, as a vehicle to install other malware on the target, or to steal financial details and other data.
- Bots – Attackers may use malware to recruit slave devices as part of a botnet. They can then either rent out the devices and computers under their control, or they can use them themselves to launch DDoS attacks, phishing scams and other attacks.
- Cryptojacking – Also known as crypto mining malware, attackers sneakily install crypto mining software on a target’s computer, then use its resources to mine cryptocurrencies like Bitcoin for themselves. While it’s relatively benign compared to the other attacks, it can slow down a victim’s computer and take up their bandwidth.
- Adware – Attackers can make money by installing software that displays ads on their target’s computers. Each time an ad is displayed or the user makes a click, the attacker makes a tiny bit of money. Over time, this amount adds up, especially across thousands or millions of computers. Adware also tends to be relatively mild compared to the other types of malware listed above.
Cybercriminals may use the payload to directly gain funds, such as through crypto mining or the extortion involved in ransomware. Alternatively, they may seek out deeper access to their targets’ systems, so that they can steal customer data, intellectual property, or even sabotage assets.
The difference between malvertising and adware
Malvertising and adware can easily be confused, because they both involve advertising and nefarious intentions. The main difference is that malvertising uses ads to spread malware, whereas adware is a type of malware, and it can end up on target computers in a number of ways.
Malvertising does not make money for the attackers by itself; it’s merely a pathway to make money. It can lead to ransomware, spyware or any of the other payloads mentioned in the previous section. Adware makes money for attackers in a direct manner, because advertisers pay them each time an ad is displayed to a user, or whenever users click on the ads.
To put it another way, malvertising is a method for mounting attacks, whereas adware may be the ultimate goal. Malvertising can even be used to spread adware, by using ads to manipulate users into downloading and running the adware.
Where do internet users encounter malvertising?
You may come across malvertising wherever you see online ads. This includes banner ads and popups on websites, advertisements that appear before videos and even ads that show up in applications.
Such ads generally aren’t displayed by the website directly. Instead, they are loaded from a third-party source known as an ad network. Ad networks function as intermediaries between websites that show ads and the advertisers that want their ads shown to site visitors. These ad networks aggregate ads, matching supply and demand between the advertisers and publishers.
You are most likely to find malvertising in the murkier parts of the web, such as pornography sites, online gambling dens and internet-based havens for illegal activity. It’s also common on smaller websites. You can expect to encounter it anywhere that the site owners aren’t overly scrupulous, or lack the knowledge or resources to keep these malicious ad campaigns at bay.
Although you are more likely to encounter malvertising on dubious sites, that doesn’t mean you should drop your guard when browsing more mainstream and well-regarded pages. Malicious ads have previously made their way onto the New York Times and BBC websites, into Skype, and on Windows 10 apps. This ubiquity is why you always need to stay vigilant.
How do attackers get their ads onto websites and in apps?
Cybercriminals have three different ways that they can mount malvertising campaigns:
- By paying for the ads – If attackers are feeling flush, they can do what everyone else does when they want to show ads – they pay site owners or advertising networks to display their ads. The only difference is that the cybercriminals push malicious ads onto viewers, and they can result in far worse scenarios than simple annoyances.
- By compromising an ad network – Another common attack technique involves taking over an entire ad network. Hackers can compromise a legitimate ad network and use it to spread their malicious ads instead. This technique is useful for spreading ads on more tightly guarded websites, just like in the attack against the New York Times, the BBC and other websites discussed in the previous section.
- By building their own ad agencies – This method isn’t as common because it’s a lot more work, but it’s still a possibility. A good example is the 2017 Zirconium attacks, which involved a cybercriminal that created 28 fake ad agencies, and was responsible for delivering an estimated one billion malicious ads.
Why can attackers buy ads to distribute malware? Why isn’t malvertising blocked?
It may seem odd that attackers can just buy ads and use them to infect site visitors with malware. For the most part, publishers and ad networks will try to avoid displaying malicious ads, but they don’t prevent site visitors from encountering them in all cases. The reasons behind this are usually either:
- The publishers and ad networks may not care – If an attacker is willing to pay them, they may turn a blind eye to infectious ads. This is especially true in the dodgier parts of the web. The operators of an illegal gambling site will suffer a smaller amount of reputational damage than the New York Times or Facebook would if malware is discovered in their ads.
- They may not know – Smaller websites and ad networks may not have the knowledge or resources to detect malware in their ads. Even when checks are in place, attackers may use sophisticated techniques that hide the malicious code.
Modern internet ads can be complex and contain executable content. This complexity opens up the door for deception and maneuvering, and hackers have developed a number of ways to avoid detection.
When trying to slip malware past advertising networks, platforms and publishers, the most popular techniques include obfuscation, redirection, fileless malware, and steganography.
Obfuscation
Obfuscation involves making code difficult for humans and programs to understand. It has legitimate applications, like protecting intellectual property, but it can also be used to sneak malicious code into ads.
By writing malicious code in a way that hides its true nature, hackers can confuse both humans and scanners. If no one can detect that an ad is malicious, then there’s no obvious reason to prevent it from being displayed. When hackers carefully obfuscate their code, it’s easy for them to slip malicious ads past the gatekeepers.
Redirects
Redirection is a relatively common part of the online experience. Companies may redirect site visitors from an old website to the new one, from slight misspellings of the URL to the intended page, and for a number of other reasons.
The practice is also implemented in legitimate ads. If you click on an ad, you may be redirected through a number of pages before you arrive at the correct destination. Sometimes site visitors are redirected to a specific page according to data that the ad gleans from the individual’s browser. This process is known as fingerprinting.
While this may seem shocking, the aims are usually no more sinister than attempting to advertise more effectively. However, cybercriminals can also take advantage of this technique to hide their malicious ads.
In the simplest form, hackers redirect all site visitors that click on an ad, taking them to a malicious page. This is easy to detect and doesn’t end up being overly effective. Hackers can make the attack more sophisticated by fingerprinting visitors and specifically looking for those running outdated software that makes them vulnerable to attack.
When those with the latest updates come across these malicious ads, the fingerprinting process will indicate that they aren’t vulnerable, and redirect them to a normal page. These visitors may never know that they were stumbling around the opening of a trap.
They are generally redirected away from the attack because it doesn’t make sense to send someone to the next step if the cybercriminals know that the attack won’t work against them.
Because of this, hackers often only redirect visitors toward the elevated stages of the attack if they are vulnerable and it is likely to succeed against them. The majority of visitors may never even come close to these stages.
In the same way that attackers can filter between those who are vulnerable and those who are not, they can also filter away from setups that are commonly used by security researchers for detection, such as sandboxes and virtual machines.
If the fingerprinting process indicates that a potential target might actually involve a virtual machine, it can redirect them to a legitimate page, rather than the malicious one. This can prevent researchers from discovering the attack.
When redirection is structured intelligently, it can be incredibly effective for hiding malware. If publishers and ad networks are always redirected to seemingly legitimate pages whenever they mount their inspections, then they can’t detect the malicious pages that only a small number of vulnerable users may be sent to. This makes it another important tactic that hackers use to infect users without detection.
Fileless malware
Fileless malware doesn’t write to the disk, which makes it difficult to detect via traditional methods like signature detection, pattern analysis and file-based whitelisting. It also makes digital forensics challenging, since the malware is designed to leave no long-term trace on the system.
Hackers leverage these features to escalate attacks during their malvertising campaigns. Fileless malware allows them to hide their intentions, thus enabling the attack to spread further without detection.
Steganography
Steganography is another sneaky tactic that lets hackers hide malicious code. In a more general sense, steganography is the practice of hiding information in a way that makes it look like no information is present. It differs from cryptography, which is more concerned with protecting a message through means like encryption, rather than hiding its very presence.
A simple example of steganography is invisible ink. You can write an entire letter to someone with it, but it would still look like a blank piece of paper to an interceptor unless they knew how to uncover it.
Although the picture of the tree looks completely normal, it actually contains the picture of the cat hidden within it by steganographic software. Photograph of tree, contains hidden image by Cyp licensed under CC0. Steganography recovered by Cyp licensed under CC0
When it comes to malvertising, we sometimes see malicious code steganographically hidden in image files. These images can look completely normal, and the hidden code may only be detectable with specific steganographic software.
Hackers can use steganography to hide malicious code and evade detection from ad networks and site visitors. If the malicious code is extracted from these images when site visitors encounter them, it can then initiate attacks.
How can malvertising infect site visitors?
When people encounter malvertising through banners, popups or in apps, there are two main ways that it can infect users. The first is through social engineering. The second is by taking advantage of security vulnerabilities.
Social engineering
Have you ever come across an ad that warns you of a virus on your computer? The odds are that it’s actually a malvertisement – a ruse that aims to trick you into downloading some software that will supposedly clean up your computer.
In this classic scheme, it’s usually just a nefarious ad, and the target’s computer is fine. However, some people get scared by these ads and presume that they are legitimate warnings from their antivirus program.
They follow along with the instructions and download the program that will supposedly clear up the virus. The program is actually real malware that ends up infecting the computer – the visitor would have been completely fine if they simply ignored the warning.
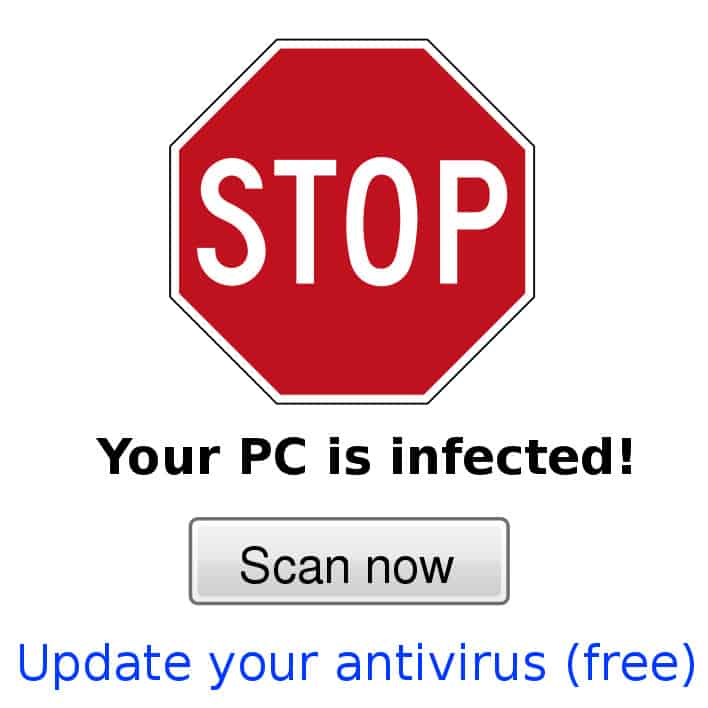 A typical malicious ad that uses social engineering to trick you into downloading malware. Stop sign by Syced licensed under CC0.
A typical malicious ad that uses social engineering to trick you into downloading malware. Stop sign by Syced licensed under CC0.
In the above example, attackers have launched a malvertising campaign that uses social engineering to trick the targets into downloading malware. This basically means that they are manipulating the user through a fake scenario, often leveraging fear to make them take the desired action – an action that is completely different from what the victim thinks it is.
Even though the victim’s computer was initially fine, they were scared into downloading the actual malware because the ad made them think that they already had a virus. There is a wide range of similar schemes, such as fake notifications for system updates or new versions of Flash.
The common thread is that they mislead the victim into taking an action that they would not have done if they knew what was really happening. No one downloads malware for fun, so hackers use social engineering as an effective technique for manipulating their victims into doing what they want.
Vulnerabilities
In certain situations, hackers have no need to trick their victims. A significant proportion of internet users neglect updates for their browsers, plugins, operating systems and other software. Updates often contain security patches that plug up the recently discovered holes in programs.
When people don’t have these latest updates, hackers can leverage the existing vulnerabilities to penetrate into their systems. The most shocking part is that it can all be done without the victim’s awareness or even a single click. This is known as a drive-by download.
Hackers take advantage of a wide range of outdated software in these attacks, but the most common ones include:
- Old versions of Windows and other operating systems.
- Unpatched browsers like Internet Explorer or Chrome.
- Outdated versions of Adobe Flash and other plugins.
In these attacks, users are often fingerprinted to see if they are vulnerable. Those susceptible to attacks are then redirected to pages with malicious code, which is often hidden by obfuscated JavaScript or other techniques.
The attacks ramp up and eventually bring a payload onto the targeted computer. This is often a Trojan, spyware, ransomware or some other type of malware.
Malvertising examples
Malvertising can take a range of different forms, with a variety of end goals. Here are some examples of malvertising campaigns:
BlackCat
In 2023, researchers at eSentire noticed that affiliates of the BlackCat ransomware group were launching Google Ad-based malvertising campaigns in an effort to find a way in to corporate networks. The attackers used paid adverts for software such as Slack and Cisco AnyConnect to convince corporate users to click on download links. Business users who did click the links had the Nitrogen malware downloaded onto their machines. Once in place, Nitrogen, which is “initial-access malware that leverages Python libraries for stealth”, paves the way for the launch of BlackCat ransomware.
NFT God
In early 2023, an influencer specialising in NFT-related content claimed to have lost “a life-changing amount” of nonfungible tokens (NFTs) and cryptocurrency after attackers used malvertising to install malware on his device. NFT God (aka “Alex”) told his followers that he’d clicked on a sponsored advertisement – rather than an official website – when trying to download open-source video streaming software. When he’d tried to execute the downloaded file, he inadvertently ran malware that stole saved browser passwords, Discord tokens, cookies, and cryptocurrency wallets, before sending them to a remote attacker.
The VeryMal campaign
The VeryMal campaign is interesting because it cycled through a variety of evasion techniques as its older methods became less effective. The group first received widespread attention in 2018 when it was discovered using steganography to hide redirection code.
When site visitors encountered the malicious ad, JavaScript would fingerprint them to see if they supported Apple fonts. Those that did were sent to the next step, which extracted code from pixels in the ad’s image.
The characters were drawn out individually, then collated into a string, which navigated to a page that hosted a fake Flash update. When potential victims reached this point, the group made use of social engineering to try and convince them that they needed to download the supposed Flash update.
Of course, it wasn’t really a Flash update, but a type of adware for Mac known as Shlayer. Those who were tricked into downloading it were exposed to unnecessary ads on their computer, which also drained resources and slowed it down.
By the start of 2019, the VeryMal group had switched up its tactics. Instead of hiding redirection code with steganography, it was using ad tags to retrieve a similar payload from Google Firebase.
Ad tags are pieces of HTML code that browsers use to retrieve ads from ad servers. Google Firebase is a cloud-hosted app development platform. The tag requests an entry from VeryMal’s Firestore database, then executes it through JavaScript.
The code is obfuscated to avoid detection, and it fingerprints the target, only proceeding against those using Safari. Suitable candidates are then redirected to the fake Flash update page in the hopes that the attackers will be able to trick them into downloading the Shayler adware.
eGobbler
The eGobbler group was one of 2019’s most prominent malvertisers. In April, the group launched a huge campaign that targeted Chrome on iOS. Versions prior to 75 were vulnerable. According to Confiant, the campaign exposed an estimated 500 million user sessions in only six days.
In another burst from August to September, eGobbler reemerged even stronger. Confiant estimated that this grouping of attacks led to over 1.16 billion compromised impressions. At first, this second campaign seemed similar to the first, but it was actually redirecting WebKit browsers, such as Safari. When the code was de-obfuscated, it was shown to use iFrames to further the attack.
While the first attack mainly affected iPhones, 78 percent of the second iteration targeted Windows PCs. Almost 14 percent targeted Mac OS X, about 7 percent Linux, and 1.1 percent iOS. It made 82 percent of its impressions through Chrome, with just 10 percent via Firefox, 3.4 percent via Edge, and 2.2 percent through Opera.
Malicious ads would forcefully redirect susceptible site visitors, leveraging browser vulnerabilities to take them to attacker-controlled landing pages. Malicious payloads would then be delivered through a content delivery network (CDN).
The affected developers were notified of the attack at the beginning of August. A patch was issued for Chrome several days later. The fixes of iOS 13 and Safari 13.0.1 weren’t released until the second half of September.
Cryptojacking
Cybercriminals are crafty, constantly coming up with new ways to make money. One of the latest trends is cryptojacking, which involves subtly taking over an unwitting target’s computer resources and using them to mine cryptocurrencies such as Bitcoin or Monero.
This technique has even been combined with malvertising, with elaborate campaigns that allow attackers to force site visitors to mine for them, all through malicious ads.
In 2018, Netlab 360 reported a sophisticated series of cryptojacking attacks that used domain generating algorithms (DGAs) to stay one step ahead of security researchers.
The malicious ads were mainly hosted on pornographic websites. When susceptible targets visited these pages, they would be redirected to serve.popad[.]net, which hosted the JavaScript code coinhive.min[.]js.
This JavaScript code then secretly hijacked the target’s resources, using them to mine cryptocurrencies via Coinhive, all for the attacker’s benefit. While this attack may seem relatively benign, it can slow down the targets’ computers, overheat them, and is still considered malicious.
Even users of Adblock weren’t immune to this attack. While Adblock restricted access to serve.popad[.]net, the attacks used DGA technology to continually generate new domains, allowing the cybercriminals to stay ahead of security researchers. The constant wave of new domains meant that the malware always had active command and control centers, from which the attackers could continue to mine cryptocurrencies.
This feature made the attack campaign quite prolific, with three of its seemingly random domain names having Alexa rankings of 1,999, 2011 and 2071 at the peak of the campaign. Infecting multiple websites around the top 2,000 is no small feat for a cryptojacking attack.
RoughTed
The Malwarebytes team was studying the Magnitude exploit kit when they noticed a suspicious redirection chain, which they dubbed RoughTed after one of the domains they spotted. Upon further investigation, they discovered that RoughTed was connected to a huge and diverse malware campaign that peaked in March of 2017.
Malwarebytes estimated that domains related to the campaign accumulated around half a billion hits, while Check Point’s figures suggest that 28 percent of organizations across the globe were affected during the June campaign.
It has since been pointed out that RoughTed and the associated domains were actually part of ad network, AdMaven. The malvertising attempts were launched further downstream, and the attackers compromised ad agencies as a starting point for their campaign.
The standout features of the RoughTed campaign are not just its size, but its scope and diversity. Malicious ads were shown across thousands of publishers, some of which were in the Alexa top 500.
The campaign also featured sophisticated fingerprinting techniques and the ability to avoid adblockers. It could even detect those that were being deceptive about their geolocations and browser configurations.
One of its most common verification tactics involved checking that the installed fonts matched those of the browser that the site visitor claimed to have. If the fingerprinting process showed that the fonts did not match, then it was likely that the target was trying to mislead the attacker.
No matter what browser configuration a site visitor had, they would be redirected somewhere in an attempt to move the attack forward. The next steps depended on their browser, plugins, OS and unique vulnerabilities.
As examples, some Windows users would be pushed to install potentially unwanted programs (PUPs). Fake Java and Flash updates were often used to trick targets into installing adware and other detrimental programs.
RoughTed could even bypass ad blockers in Google Chrome, then push a fake Chrome extension to the site visitor. If the target clicked anywhere on the page, their browser would be hijacked.
Alternatively, vulnerable users could be redirected toward the RIG or Magnitude exploit kits, which can install Trojans, crypto mining software, ransomware and other malicious programs.
The RoughTed campaign could also lead potential targets to tech support scams, where call center agents would try to convince them that they have a virus and then extort money out of them.
Those who run Macs could be redirected to adware installations, dangerous Chrome extensions could install themselves, and targets could even be redirected to dodgy surveys or the iTunes store. These many paths show just how sophisticated and diverse the RoughTed campaign was.
fiber-ads
Another major attack campaign was first reported by Malekal, a French IT website. It was later examined in more detail by Confiant, which revealed that the attackers had compromised 100 million ads in the first six months of 2019.
One of the most interesting aspects of the campaign was that it showed ads in Windows JigSaw, Outlook and other desktop applications. While in-app malvertising is a more novel approach, the attacker was also pursuing potential victims through traditional tactics, targeting site visitors through malicious browser-based ads as well.
The malicious ads displayed within Windows 10 desktop applications were often connected to the ads.creative-serving[.]com domain. This is an ad-serving domain owned by Platform161, an ad-purchasing platform. Platform161’s domain had been compromised by the cybercriminals.
The ads.creative-serving[.]com page first fingerprinted visitors. Suitable victims were redirected to a malicious ad that appeared to come from Microsoft. The ad offered visitors an iPhone XS, iPad Pro or Galaxy S10.
Of course, those who were tantalized into clicking on the ad weren’t sent a new device in mail. Instead, the site visitor would be sent along a number of sinister paths. One of these was the classic “You have a virus, click here to remove it” trick, which actually only infects visitors if they click it.
Alternatively, site visitors could be led to a survey that deceives them into signing up for monthly deductions from their bank accounts.
Confiant took a deeper look into the attacker’s actions, and it was able to connect them to a Hong Kong-based company called “fiber-ads”. fiber-ads has since changed its name to “Clickfollow”, but the same entity has used over 150 separate domains since 2017.
This business operates in a murky part of the advertising world, ostensibly serving as a middleman that attackers can use to display malicious ads across its network. It’s difficult to discern whether some of the malicious campaigns originate from fiber-ads itself, and what portion of the attacks come from its client-base.
Malvertising detection & prevention
Malvertising serves as the introduction for a significant portion of attacks in our online world. By minimizing its prevalence, we can help make the internet safer for everyone. This can be accomplished by improving our approaches to detection and prevention at all levels, including ad networks, publishers and individual internet users.
Ad networks
Cybercriminals will always pursue the most practical opportunities they have at hand to make money. Short of constructing a utopia, there is little we can do to eliminate this factor. Given that malicious ads provide a convenient starting point for cybercriminal attack campaigns, it then falls on the shoulders of advertising networks to restrict malvertising from being shown to site visitors.
One of their prime responsibilities is to scan ads for malicious code. There is a diverse range of software that scans for malware in several different ways. The most common are:
- Signatures – Signature analysis is one of the older forms of malware detection. When security researchers first discover a new strain of malware, they add the hash of the malware, known as the signature, to a database. Many antivirus products work by matching suspicious files against these databases, looking for code that indicates that the file contains a previously discovered form of malware.
- Behavior – A lot of malware operates along predictable behavior patterns. This analysis method involves looking for telltale malicious behaviors, then flagging code that appears to be acting along these lines.
Unfortunately, detecting malware isn’t always so simple. Cybercriminals have a strong interest in avoiding detection, and often use fingerprinting alongside evasive measures like obfuscation, steganography and redirection, so that they can slip malicious ads past the networks.
Even the most advanced and comprehensive detection systems can’t always prevent these sophisticated attempts. Therefore, ad networks also need to have plans in place for how they will quickly respond when they discover that malicious code has been displayed in their ads.
By acting quickly, not only can an ad network help to limit exposure and potential infection, but it can also reduce any negative fallout that malvertising may bring against the network’s own reputation. An effective response plan doesn’t have to be purely altruistic. It can also prevent the ad network from looking bad in the eyes of its clients.
Ad network operators should also take care with their general security, to prevent hackers from easily compromising their networks and using them to spread malicious ads. Best practices such as unique and complex passwords, the principle of least privilege, two-factor authentication and anti-phishing training are just some of the core elements that ad networks need to implement to protect their businesses.
Grey area ad networks
The tactics mentioned above are only effective for legitimate advertising networks. Ad networks that operate in the shadows may be turning a blind eye to malvertising in return for payment, or they could even be directly involved in the campaigns. Of course, these ad networks aren’t going to go out of their way to protect site visitors from malvertising.
This is a difficult problem to address, due to the international operations of cybercriminal gangs and any advertising networks that may be tangled up in their sinister enterprises. Perhaps additional legislation, police crackdowns against these networks and the global cooperation of authorities could help to limit the viability of many dodgy ad networks.
However, even in the best-case scenarios, it’s likely that some malicious ad networks would persist due to the complexities of international regulation and policing. This leaves publishers and site visitors with some responsibilities to prevent their exposure to malvertising.
Publishers
In the online advertising ecosystem, publishers are simply the websites that host ads. Your go-to news website, most-visited blog and favorite forum would all be considered publishers if they display ads. Google and Facebook are considered publishers as well, however, they have their own ad networks.
Just like the ad networks, publishers also have a responsibility to combat malvertising. It doesn’t matter if it’s a blog that sees 100 hits each month or a site that gets a billion. Once again, it’s important to protect the website’s reputation, as well as helping to safeguard the overall online ecosystem.
Where possible, sites should scan their ads. Smaller websites may find free tools like VirusTotal useful. Most websites use ad networks to display their banner and other ads, for both efficiency and effectiveness purposes. Due to this outsourcing, and the dynamic ad displays that are customized to individual users, it may not be feasible for them to scan all of the ads that will be displayed on their websites.
This means that they need to make sure that they are only contracting with trustworthy networks that will carefully vet the ads for them. Publishers should take the following steps before settling on an ad network:
- Review the ad network’s reputation – If an ad network has a dodgy history, it’s unlikely that it will be upfront about it. A good place to start looking would be to ask colleagues or business associates for recommendations. Otherwise, running a web search could lead publishers to some decent candidates. Publishers should then take the time to research the organization’s history, and evaluate it based on any reviews that they can find.
- Conduct a Whois search – A Whois search is also a good idea because it will tell the publisher who registered the domain, when and where. Publishers need to make sure that this information matches what the company says about its origins. If there are discrepancies, publishers should consult the company to determine whether it is being deceptive.
- Ask the network what other clients they have – If the network can prove that other major organizations work with them, it indicates that it is trusted by other parties.
- Ask the network about its ad delivery paths and the security policies it implements.
- Consult the network on its ad practices – Avoid companies that resort to mischievous tactics like pop-ups and pop-under ads.
- Ask if it’s possible to individually whitelist advertisers – Whitelisting gives publishers control over which advertisers are displaying ads on their site. If they are diligent with their whitelisting, it can help to prevent malicious actors from advertising on their pages.
- Consider disabling JavaScript in ads if possible – Attackers often use JavaScript to infect vulnerable browsers.
Once publishers have settled on a trustworthy ad network, they still have their own responsibilities for preventing malicious ads. They should develop a strict content security policy and scan for malware where possible. Malicious ads can also be detected by logging the outgoing URLs, or by tracking browser errors with client-side tools like Airbrake or Sentry.
Individuals
Site visitors also have a crucial role in protecting themselves. We can’t completely eliminate malicious actors or incompetence in ad networks and publishers, so it looks like highly sophisticated criminals will continue to serve malicious ads in the foreseeable future.
If you want to browse the web safely and minimize the risk of being infected via malicious ads, then you should take the following precautions:
- Update your software – The software development process is imperfect, and vulnerabilities are discovered over time. Trustworthy companies will quickly patch any holes they discover, then send out the fixes as part of the next update. If you don’t install the update as soon as possible, you leave yourself open to one of the most common malvertising-related attack vectors: taking advantage of security exploits in outdated software. Protect yourself by either automatically or manually updating your operating system, browser and other software as soon as possible.
- Use a safe browser – Developers have come to realize just how serious the malvertising threat is. In response, recent versions of Chrome, Firefox and other browsers have a number of safety features to better protect their users. These include Google’s Safe Browsing, which maintains a blacklist of dangerous websites and warns users of possible attacks.
- Be wary of plugins – Insecure plugins are another common attack vector. You should only install the plugins that you absolutely need, and only if they come from well-regarded providers. This means no more unnecessary toolbars clogging up your browser screen and culling all plugins that you don’t regularly use. The fewer plugins you have, the smaller your attack surface area, which reduces the chances of an attacker being able to successfully exploit a security vulnerability in one of your plugins. Of course, the plugins that remain should also be updated as soon as new patches come out.
- Set Java and Flash to click-to-play – Hackers frequently take advantage of Java and Flash to begin their attacks. While a lot of security professionals would like to see them both shot into the sun because of the risks they bring, the reality is that completely disabling them will break a lot of web pages and end up giving you a much poorer online experience. A good compromise is to set them to click-to-play so that they only run (and potentially endanger your computer) once you have clicked on them. This puts the control back in your hands, allowing you to use them when necessary, without needlessly risking yourself when you don’t even want them to run.
- Install a scriptblocker – Scriptblockers like NoScript for Firefox and ScriptSafe for Chrome disable scripts from running by default. Just like click-to-play, this will break a lot of websites at first. However, these plugins allow you to whitelist the scripts you want to allow on certain pages. It takes a bit of work at the beginning, but they allow you to save your preferences at a granular level. This could mean that you allow JavaScript or Flash to always run on websites that you trust, while disabling them or perhaps temporarily allowing them on other sites.
- Install an adblocker – If a malicious ad is blocked, then it can’t infect you. Some will argue that adblockers are essential because publishers and ad networks aren’t being diligent enough in protecting against malvertising. Others would call adblockers unethical because they deprive websites of the advertising revenue that sites rely on to produce content. Whether you use an adblocker or not is a personal decision, but uBlock Origin for Firefox and Adblock Plus for Chrome can both help to secure your browsing experience. If you choose to use one, consider whitelisting websites that you value or supporting them in other ways.
- Run an antivirus program – Running an antivirus is an important way to detect or prevent malware from ending up on your system. For personal use, Windows Defender and the free version of Malwarebytes can accomplish a lot at no cost.
- Consider using anti-exploit software – Malvertising attacks often proceed by exploiting vulnerabilities in the browser environment. Programs like Microsoft’s Enhanced Mitigation Experience Toolkit (EMET) or Malwarebytes Anti-Exploit can monitor your browser for any exploit attempts and automatically stop them, helping to protect your system from these attacks.
- Make sure your firewall is running – Firewalls are an essential part of security, whether at the personal or enterprise level. In the case of malvertising, specific rules can be created to monitor iFrames, redirects and other common elements that cybercriminals use in their attacks.
- Avoid potentially dangerous websites – While malicious ads are occasionally seen on reputable websites, they are far more common on smaller sites as well as those that populate the darker areas of the web. Smaller sites may not have the resources or knowledge to effectively manage their malvertising risks, while gambling, filesharing and pornography websites are often havens for cybercriminals and their malicious ads.
Malvertising: An ongoing threat
Cybercriminals will work with whatever opportunities are at their disposal. A significant portion of the web is powered by ad revenue. This ubiquity, as well as the possibility of inserting malicious code into ads, has led to malvertising often acting as a starting point in cybercriminal attack campaigns.
While ad networks, publishers and site visitors can certainly do more to protect themselves and the overall ecosystem, attackers will evolve their tactics in conjunction. Although there is little we can do to avoid this arms race in the foreseeable future, the best path forward for everyone is to implement the security basics that we covered above.
Doing this won’t make ad networks, publisher or site visitors invincible, however, it will make it much more difficult for the attacks to be effective or financially viable. By following this advice, it’s likely that attackers will simply move on to the next, easier target, leaving your business or systems safe from the latest malvertising campaign.




Article quite comprehensive, but I wanted an inactive visual image of several insidious samples of these malverts and how each of them attempted to highjack your computer. I have seen those “your computer is infected” baloney before. That one is old news.