Penetration tests, or pen tests as they’re colloquially known, primarily consist of hacking or cyber-attacking your own system so that you can determine if there are any vulnerabilities that can be exploited by third parties.
This process is used to strengthen a web application firewall, and it provides a great amount of insight that can be used to improve our system’s security, which is vital for any kind of organization. Pen tests simply are much more effective and efficient with the aid of specialized tools, and that’s why today we will be exploring the best ones out there.
Here is our list of the best penetration testing tools:
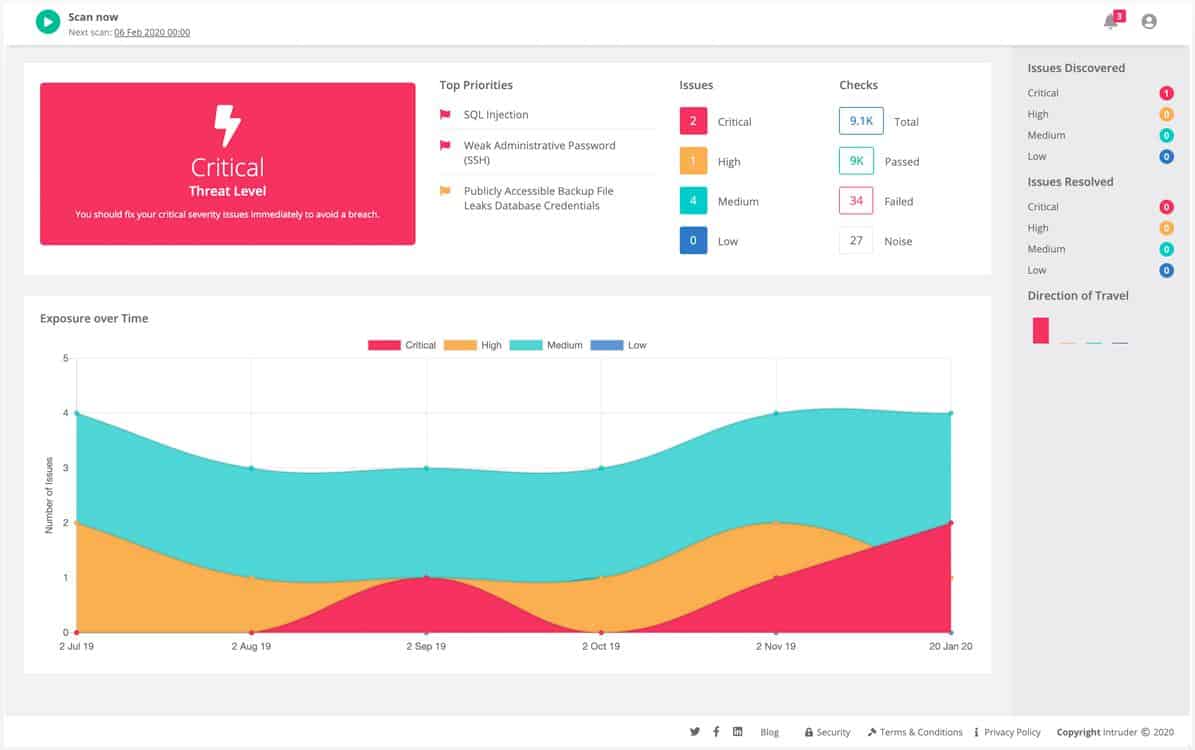
- Intruder Automated Penetration Testing EDITOR’S CHOICE A cloud-based subscription service that constantly scans a client’s system for vulnerabilities. The highest plan includes human-led penetration testing.
- Network Mapper (NMAP) Free and open-source utility for network discovery and security auditing.
- Metasploit Lightweight command-line tool, trusty for assessing and keeping you on top of threats.
- Invicti Security Scanner This package offers continuous testing, periodic vulnerability scanning, and on-demand scanning that can be used for penetration testing. This service is available for installation on Windows and Windows Server and it is also offered as a SaaS package.
- Acunetix Scanner Offered as a vulnerability scanner or a penetration testing tool, this service speeds up system weakness detection and can operate from an external position or within the network. Runs on Windows, macOS, and Linux or as a SaaS package.
- Indusface Penetration Testing Services This is a consultancy system that not only offers penetration testing tools but provides a team of white hat hackers to do the testing for you.
- BeEF Solid command-line tool, great for monitoring the network’s ‘open door’ – the browser – for any unusual behavior.
- Wireshark A trusty network protocol analyzer with a well-known user interface, packs a lot of power.
- w3af Python-based network protocol analyzer with similar features to Wireshark, yet very extendable.
- John the Ripper Great command-line password cracker to test how secure the user passwords on your network are.
- Aircrack mainly focuses on wifi security and known vulnerabilities.
- Burp Suite Pen Tester Comprehensive set of tools, great for analyzing and tracking traffic between servers and client browsers.
The objective of a pen test is not only to find vulnerable elements of your security system but also to check the compliance of your security policy in your organization, measure the awareness and scope of any security issues, and to take a look at the possibility of what disasters could befall your network in the event of a real foreign-entity cyber-attack.
See also: Courses to learn ethical hacking online
In essence, penetration testing allows you to reveal areas of weakness that you might not have otherwise considered. Often, organizations are stuck in their ways (or simply become apathetic), but pen testers offer an unbiased and fresh perspective that will result in strong improvements and the adoption of a more proactive approach.
The best Pen Testing Tools
Our methodology for selecting penetration testing tools
We examined the penetration testing tools on the market and analyzed tools based on the following selection criteria:
- A suite of tools that offer a range of functions from one console
- A mix of task automation and tools to support manual actions
- Systems that will automatically log all actions to take the burden of note-taking off the technician
- Automated test reporting
- Tools that offer specialized hacking facilities for specific types of IT systems, such as networks, wireless systems, or operating systems.
- A free trial or a money-back guarantee to provide a no-risk assessment of paid tools or tools that are free.
- A good mix between low price and powerful capabilities – value for money.
Given that a penetration test is meant to provide such important information, its success depends on using the right tools. This is a complex task, so automated tools make it easier and more effective for testers to identify the faults. So, without further ado, here are the top 11 tools for pen testing (in no particular order), according to our in-depth analysis:
1. Intruder Automated Penetration Testing (FREE TRIAL)
Intruder is a cloud-based service that scans client systems for vulnerabilities. During onboarding, Intruder does a full system sweep, looking for existing vulnerabilities. After that, the Intruder service makes periodic scans of a client system, triggered by the discovery of new hacker attack vectors that have revealed new vulnerabilities.
Key Features
- Cloud-Based: Operates fully from the cloud, facilitating remote scanning.
- Advanced Graphics: Utilizes sophisticated analytics for detailed vulnerability insights.
- Results Integration: Consolidates test outcomes for comprehensive reporting.
- Real-Time Discovery: Detects new assets and services exposed to the internet, such as subdomains, APIs, and login pages.
- Emerging Threat Scans: Proactively checks for newly discovered vulnerabilities soon after they are disclosed.
Why do we recommend it?
Intruder Automated Penetration Testing is a vulnerability scanner. This service operates from the cloud and provides external scanning. Higher plans add in internal scanning through the installation of an agent. The system will also scan Web applications and cloud platforms. The system provides on-demand scanning as well as scheduled scans.
The services of Intruder are charged for on a subscription basis. There are three plan levels: Essential, Pro, and Verified. The Essential plan offers an automatic monthly vulnerability scan. With the Pro plan, customers also get the option to launch scans on demand. The Verified plan offers the monthly scan plus an on-demand facility plus human-driven penetration testing.
Who is it recommended for?
This package is a little more affordable than many of the other options on this list. However, it still would be out of reach of small businesses. This is a vulnerability scanner rather than a penetration tester, so it cuts out the expense of hiring human penetration testing experts.
Pros:
- Automated Scans: Capable of running scheduled and on-demand vulnerability scans.
- Scalable Service: Cloud-based architecture makes it easily scalable to suit various business sizes.
- Intuitive Interface: Features a user-friendly dashboard for both high-level and detailed views.
- Expert Testing Option: Includes human-led penetration tests in its premium plan, ideal for thorough security assessments.
- Prioritization: Uses threat intelligence, including CISA’s Known Exploited Vulnerabilities (KEV) list and exploitation predictions, to help prioritize issues.
Cons:
- Complex System: The platform’s advanced features can be challenging to fully utilize without prior experience.
The Intruder service is available for a 14-day free trial.
EDITOR'S CHOICE
Intruder.io is our top pick for a penetration testing tool because it combines cutting-edge automated scanning technology with expert analysis to deliver comprehensive vulnerability assessments. Designed with ease of use in mind, Intruder.io is a cloud-based platform that simplifies penetration testing, making it accessible for organizations of all sizes, from startups to enterprises. Unlike traditional penetration testing tools that require deep technical expertise, Intruder.io streamlines the process by providing automated scans, actionable insights, and prioritizing vulnerabilities based on risk, which helps organizations stay ahead of potential threats. The tool stands out for its ability to detect a wide range of vulnerabilities, including those related to web applications, networks, and cloud infrastructure. Intruder.io regularly updates its vulnerability database to stay current with the latest security threats, ensuring that your organization’s systems are always evaluated against emerging risks. The platform’s scanning capabilities are both comprehensive and accurate, identifying security weaknesses across various areas, such as OWASP Top 10 vulnerabilities, misconfigurations, and outdated software components. Furthermore, Intruder.io offers integration with popular security tools, such as Slack and Jira, enabling teams to respond quickly to identified vulnerabilities. The tool’s reporting feature is clear and detailed, offering prioritized recommendations based on severity, so security teams can focus on high-risk vulnerabilities first.
Download: Get a 14-day free trial
Official Site: https://portal.intruder.io/free_trial
OS: Cloud based
Related post: The Best Web Application Firewalls – Buyer’s Guide
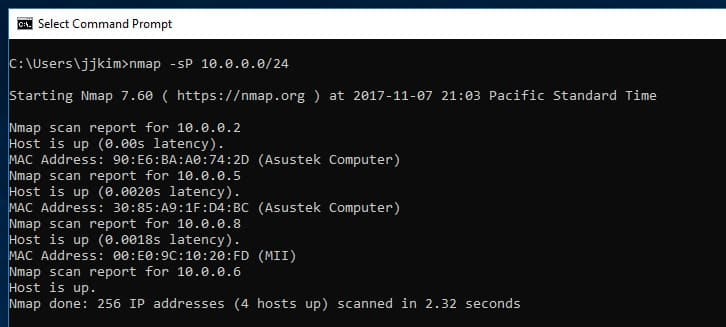
2. Network Mapper (NMAP)
NMAP is a great tool for discovering any type of weakness or holes in the network of an organization. Plus, it’s also a great tool for auditing purposes. What this tool does is take raw data packets and determine which hosts are available on a particular segment of the network, what OS is in use (aka fingerprinting), and identify the different types and versions of data packet firewalls or filters that a particular host is using.
Key Features
- Hacker Favorite: Commonly used in both legitimate and illicit network exploration.
- Audit Utility: Essential for network security audits and diagnostics.
- Command Line Operation: Quick and efficient command line interface for advanced users.
Why do we recommend it?
NMAP is a standard component of any pentesters toolkit and it is also widely used by hackers. This is because the command line system can be automated to cycle through a series of tests and it provides port scanning utilities as well as device discovery. The tool is old but it costs nothing.
Just like the name implies, this tool creates a comprehensive virtual map of the network, and it uses it to pinpoint all the major weaknesses that can be taken advantage of by a cyber-attacker.
Who is it recommended for?
If you do a pentesting course, you will be taught how to use NMAP for system reconnaissance. The tool is often included in attack viruses for lateral movement in networks. The NMAP system takes time to learn because it has many command line switches that alter its functionality.
Pros:
- Security Analysis: Helps in identifying vulnerabilities such as open ports and unusual traffic.
- Community Supported: Benefits from a robust open-source community for continuous improvement.
- Accessible Syntax: Provides a command line syntax that is relatively easy to learn.
Cons:
- No Native GUI: Primarily command line-based, lacking a graphical interface; though Zenmap offers a GUI alternative.
NMAP is useful for any stage of the penetration testing process. Best of all, it’s free.
Related post: Alternatives to Microsoft Baseline Security Analyzer
3. Metasploit
Metasploit is an exceptional tool because it’s actually a package of many pen testing tools, and what’s great is that it keeps evolving and growing to keep up with the changes that are constantly coming up. This tool is preferred by both cybersecurity professionals and certified ethical hackers, and they contribute their knowledge to the platform to help it grow, which is great. Metasploit is powered by PERL, and it can be used to simulate any kind of penetration testing you need. Plus, Metasploit is customizable and only has a process of four steps, so it’s super quick.
Key Features
- Comprehensive Toolkit: Combines multiple penetration testing tools into one package.
- Efficient Testing: Executes tests rapidly, enhancing productivity.
- Automated Reporting: Streamlines the reporting process with automatic generation.
Why do we recommend it?
Metasploit is widely used in the pentesting industry. The tool has a free version, called Metasploit Framework, and a paid edition, called Metasploit Pro. Unsurprisingly, the free version has a lot more users than the paid system. This tool is developed and maintained by Rapid7, which also produces a vulnerability scanner.
The features available will help you determine the prepacked exploits you should use, and it also allows you to customize them; you can also configure them with an IP address and remote port number. What’s more, you can also configure the payload with the IP address and local port number. You can then determine which payload you’d like to deploy before launching the exploit at the intended target.
Metasploit also integrates a tool called Meterpreter, which displays all results when an exploit occurs, which means you can analyze and interpret results effortlessly and formulate the strategies a lot more efficiently.
Who is it recommended for?
Every pentester learns how to use the free Metasploit. The Metasploit Pro package is very expensive and would only be of interest to security consultancies – independent testers won’t be able to afford it. This system is a collection of tools and it is frequently used in pentesting training.
Pros:
- Highly Regarded: Favored by cybersecurity professionals and ethical hackers worldwide.
- Community-Supported: Benefits from one of the largest and most active communities in cybersecurity.
- Versatile Availability: Accessible in both a freely available framework and a feature-rich professional version.
- Extensive Customization: Offers significant customization options for tailored penetration testing.
Cons:
- Technical Complexity: Geared towards experienced users, posing a steep learning curve for novices.
Related: Metasploit Cheat Sheet
4. Invicti Security Scanner
The Invicti web application for pen testing is totally automatic. It has become very popular due to the fact that developers can use this on many different platforms for entire websites, including web services and web applications. It can identify everything pen testers need to know to make an informed diagnosis—from SQL injection to cross-site scripting.
Key Features
- Fully Automated: Conducts comprehensive automatic scans without manual intervention.
- Extensive Toolset: Bundles numerous tools for a thorough security assessment.
- Advanced Intelligence: Utilizes smart algorithms to enhance scanning precision.
- Rapid Scanning: Capable of quickly scanning up to 1,000 web applications simultaneously.
- Automated Reporting: Generates detailed assessment reports automatically.
Why do we recommend it?
Invicti Security Scanner is a vulnerability scanner but it can be used by penetration testers as well. Use this system to reveal a series of vulnerabilities that employ manual techniques to verify and prioritize the results. This system can be set up to run constantly and is useful for DevOps teams.
Another characteristic that makes this tool so popular is that it allows pen testers to scan up to 1,000 web apps at once while also allowing users to customize security scans to make the process robust and more efficient. The potential impact of vulnerabilities is instantly available; it takes advantage of weak points in a read-only way. This proof-based scanning is guaranteed to be effective, including the production of compliance reports among other great features, including the ability to work with multiple members for collaboration, making it easy to share findings; there’s no need to set up anything extra due to the fact that scanning is automatic.
Who is it recommended for?
Invicti has a range of applications. As well as providing vulnerability discovery automation for penetration testers, it can be deployed for Web application security scanning. The system can be used to check on live applications or run in a CI/CD pipeline as a continuous tester.
Pros:
- Visual Interface: Designed with a highly visual and intuitive user interface.
- Continuous Operation: Operates non-stop, ideal for ongoing security monitoring.
- Color-Coded Prioritization: Helps teams prioritize issues effectively with automatic threat scoring.
- Versatile Tooling: Includes tools suitable for both vulnerability scanning and penetration testing.
- Scalable Solutions: Available in various packages to suit different organizational sizes.
Cons:
- Professional Complexity: Best suited for security professionals, may be overwhelming for non-experts.
5. Acunetix Scanner
This is another automated tool that will allow you to complete pen tests without any drawbacks. The tool can audit complicated management reports and issues, and it can handle many of the network’s vulnerabilities. It’s also capable of including out-of-band vulnerabilities. The Acunetix Scanner also integrates issue trackers and WAFs; it’s definitely the kind of tool you can rely on because it’s one of the most advanced tools in the industry. One of its crowning achievements is its exceptionally high detection rate.
Key Features:
- High Automation: Streamlines pen testing with automated functions.
- Effective Tracking: Monitors results and progress effectively.
- Comprehensive Coverage: Scans for network software vulnerabilities.
- Configuration Checks: Assesses system settings for security weaknesses.
- Test Management: Coordinates and manages test plans efficiently.
Why do we recommend it?
The Acunetix Scanner is similar to Invicti in that it isn’t really a penetration testing tool but provides automated vulnerability scanning. This system provides external viewpoint scanning for Web applications. It can be linked to OpenVAS, which will run internal scans to discover network vulnerabilities.
This tool is amazing, covering more than 4,500 weaknesses. The Login Sequence Recorder is easy to use; it scans areas that are protected by passwords. The tool contains AcuSensor technology, manual penetration tools, and built-in vulnerability testing. It can crawl thousands of web pages quickly and also run locally or through cloud solutions.
Who is it recommended for?
Use the Acunetix system to speed up the penetration testing process. You could run the scanner and then work through the list of revealed weaknesses to manually verify them. Away from pentesting, this tool is regularly used for live Web application security monitoring and for continuous testing in a CI/CD pipeline.
Pros:
- High Detection Rate: Recognized for its superior capability to detect a wide range of vulnerabilities.
- Integration Capacity: Seamlessly works with tools like OpenVAS for enhanced scanning.
- AcuSensor Technology: Employs advanced technology for more accurate scanning.
- Scalable Scanning: Capable of crawling thousands of web pages swiftly.
- Flexible Deployment: Available as both local and cloud-based solutions.
Cons:
- Lack of Trial Version: No trial available to test before committing to a purchase.
6. Indusface Penetration Testing Services
Indusface Penetration Testing Services offers the services of a white hat hacker team for you. Although this is not a “tool,” the service gives you a better test of your system security that an in-house team would probably perform. Unless you run the IT system for a very large organization, it is doubtful that your budget will stretch to a penetration testing team on staff full time. It is also unlikely that you will need penetration testing to be implemented every day of the year. Therefore, it is more cost-effective to hire an external team to perform the test for you.
Key Features:
- Expert Hacker Team: Utilizes a team of specialist white hat hackers for comprehensive testing.
- Remote Execution: Penetration tests are conducted offsite, ensuring unbiased assessment.
- Security Enhancements: Provides detailed recommendations for tightening security.
Why do we recommend it?
Indusface Penetration Testing Services is a consultancy that offers a pentesting team. So, this is not a tool for those looking for ways to perform their own penetration testing exercises but a team that will do it all for you. The team focuses on Web application, mobile application, and API security.
External penetration testers more accurately model the attack strategies used by hackers that IT department staff. The outsiders have no assumptions and no sacred cows. They won’t worry about breaking your system in the same way that IT operation technicians do.
The Indusface service is offered in three categories:
Applications Penetration Testing with particular focus on Web applications.
Mobile Application Penetration Testing that reaches back through all supporting microservices
API Penetration Testing Services that ensure those plug-ins and code libraries that you deploy don’t have security flaws
The tests are performed by a human team, so there are actually no limits to the services that these consultants can perform. Therefore, there is no set menu of services or price list. The results of a penetration testing exercise from Indusface are a report of all security weaknesses that were discovered and recommendations on how to repair those flaws.
Who is it recommended for?
Penetration testing consultancies are expensive, which is why cheaper, automated vulnerability management systems have become popular. However, it is recommended that even those businesses that regularly use vulnerability scanners should also bring in a pentesting team at least once a year. However,r not all businesses can justify the expense of this strategy.
Pros:
- Professional Expertise: Employs skilled ethical hackers to uncover security vulnerabilities.
- Continuous Service Option: Offers subscriptions for ongoing security assessments.
- Proactive Bug Resolution: Helps in prioritizing and addressing security threats effectively.
- Suitable for Large Scale: Ideal for larger organizations or those launching significant digital initiatives.
Cons:
- Limited to Larger Networks: More beneficial for enterprise environments, less so for smaller setups.
If you don’t have the time to investigate penetration testing and you just don’t have the skills in your team, it is just a lot easier to hire an expert instead.
7. BeEF
This kind of pen-testing tool is best suited to check web browsers because it’s designed to combat web-borne attacks. That’s why it tends to benefit mobile clients the most. The best thing about this tool is that it explores weaknesses beyond the network perimeter and the client system. Just keep in mind that this is specifically for web browsers because it will look at vulnerabilities within the context of a single source. It connects with several web browsers and allows you to launch directed command modules.
Key Features
- Browser-Specific Testing: Specializes in identifying vulnerabilities within web browsers.
- Mobile Device Compatibility: Effective in testing browser security on mobile platforms.
- In-Depth Threat Analysis: Conducts thorough searches for web-borne threats.
Why do we recommend it?
The Browser Exploitation Framework (BeEF) is a free tool and it is commonly used by penetration testers. This system can be used to exploit a browser as a way into a system either for reconnaissance or to deliver a payload. You would be able to make a quick assessment of an ingress point.
Who is it recommended for?
This system could be used to load in fileless malware or a system scan. The tool is available as an API that enables it to be integrated into a more complex attack. The system has a GUI front end, which makes it easy to use for infrequent users.
Pros:
- Focused Utility: Designed specifically for exploiting and testing web browser vulnerabilities.
- Open Source: Freely available with source code on GitHub for customization and improvement.
- User-Friendly Interface: Includes a graphical user interface to facilitate ease of use for occasional testers.
Cons:
- Narrow Scope: Primarily targets web browser vulnerabilities, lacking broader network security capabilities.
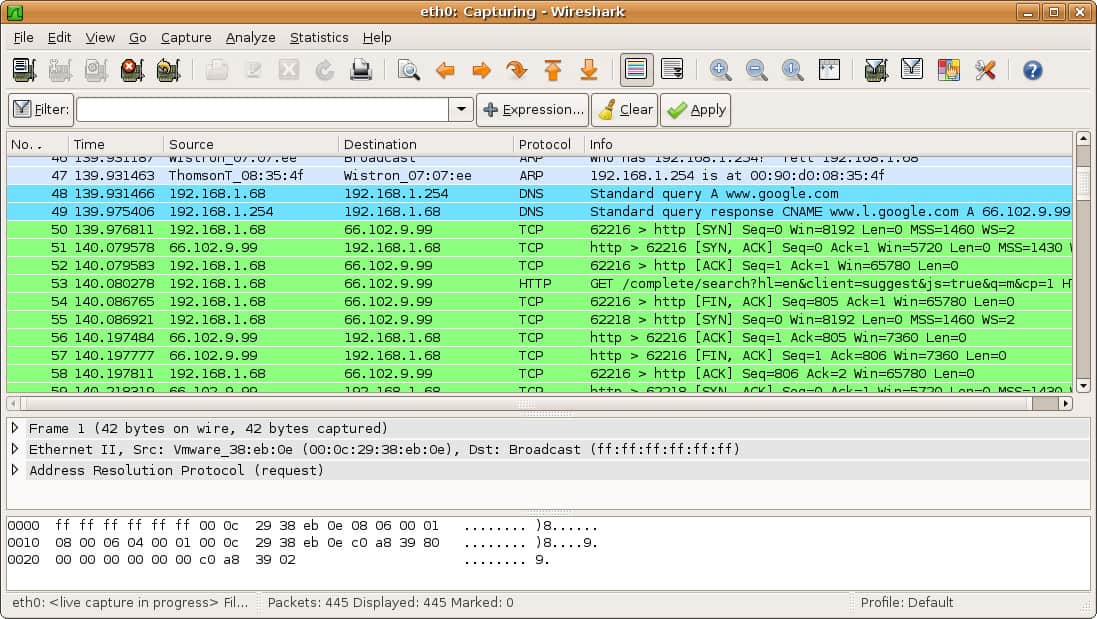
8. Wireshark
Wireshark is a network protocol and data packet analyzer that can fish out security weaknesses in real time. The live data can be collected from Bluetooth, Frame Relay, Ipsec, Kerberos, IEEE 802.11, any connection based on Ethernet, and more.
Key Features
- Highly Trusted: Renowned and extensively used for network analysis.
- Detailed Inspections: Reveals intricate details of packet headers.
- Clear Reporting: Generates easily interpretable results for stakeholders.
Why do we recommend it?
Wireshark is another key tool for penetration testers. You will need to be able to master the system’s complicated filtering and querying language to get the best out of it. This is a white box testing tool because you have to be inside the network to get the best out of it.
The greatest advantage this tool has to offer is that the results of the analysis are produced in such a way that even clients can understand them at first glance. Pen testers can do so many different things with this tool, including color coding, to enable a deeper investigation, and to isolate individual data packets that are of top priority. This tool comes in quite handy when it comes to analyzing security risks inherent to information and data posted to forms on web-based apps.
Who is it recommended for?
Everyone will need to be familiar with how Wireshark works because it can often help reveal insider info, such as unencrypted passwords and files in transit. Its use is required in many pen testing exams. The tool is free to use and is available for Windows, macOS, and Linux.
Pros:
- Robust Functionality: Offers comprehensive tools for deep network analysis.
- Community-Driven Development: Supported by a large open-source community for continuous enhancement.
- Data Retention: Capable of saving captured packet data for detailed post-analysis.
Cons:
- Complex Data Volume: Handles large datasets that can be overwhelming without proper filtering skills.
Related: Wireshark Cheat Sheet
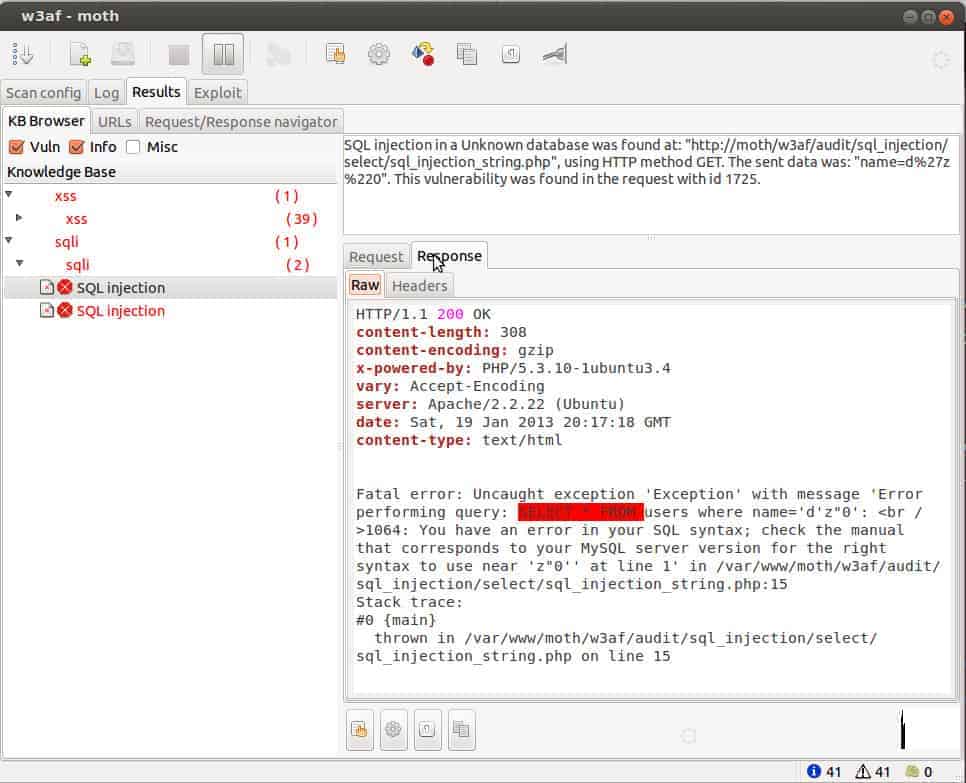
9. w3af (The Web Application Attack and Audit Framework)
This penetration-testing suite was created by the same developers of Metasploit, and its objective is to find, analyze, and exploit any security weakness that may be present in web-based applications. The package is complete and features many tools, including user-agent faking, custom headers to requests, DNS cache poisoning or DNS spoofing, and many other attack types.
Key Features
- Comprehensive Suite: A complete set of tools for web application security testing.
- Extensive Coverage: Addresses a wide range of network vulnerabilities.
- Reusable Parameters: Facilitates the saving and reusing of test configurations.
Why do we recommend it?
Like all the best penetration testing tools, W3af is free to use and runs on Linux. However, it isn’t part of Kali Linux. Use this tool to look for cross-site scripting (XSS), SQL injection, or password-cracking opportunities. This is an expandable and customizable tool – it is written in Python.
What makes W3AF such a complete tool is that the parameters and variables can be quickly saved into a Session Manager file. This means that they can be reconfigured and reused quickly for other pen tests on web apps, thus saving you a lot of time because you won’t have to re-enter all the parameters and variables every time you need them. Plus, the results of the test are displayed in graphic and text formats that make it easy to understand.
Yet another great thing about the app is that the database includes the best-known threat vectors and customizable exploit manager so that you can execute attacks and exploit them to the maximum.
Who is it recommended for?
All penetration testers would benefit from this tool. It is able to identify more than 200 exploits in Web applications and authentication exchanges. This program costs nothing, making it a very cheap and effective alternative to many of the pricey Web application security testing packages on the market.
Pros:
- Specialized Functionality: Tailored for web application auditing and penetration testing.
- Customizable: Allows for extensive customization, enhancing its utility for seasoned testers.
- Resource-Efficient: Operates as a lightweight utility, minimizing system resource usage.
Cons:
- Professional-Level Tool: Best suited for security professionals, less accessible for casual or home users.
10. John the Ripper
This is a well-known tool and is an extremely elegant and simple password cracker. This tool allows you to determine any unknown weaknesses in the database, and it does this by taking text string samples from a word list of complex and popular words that are found in the traditional dictionary and encrypting them in the same format as the password that’s being tampered with. Simple and effective, John the Ripper is a highly recommended addition to the toolkit of any well-prepared pen tester.
Key Features
- Popular Among Hackers: Frequently used within the cybersecurity community for its effectiveness.
- Command Line Interface: Operates primarily through command line for streamlined operations.
- Password Cracking: Specializes in identifying password vulnerabilities.
Why do we recommend it?
John the Ripper is a component of Kali Linux, which shows that it is on the Offensive Security approved tools list. This system is a little dated but it keeps attracting a following because it is very good at password cracking. You can use your own dictionary with the command.
Who is it recommended for?
If you need to check on credentials security, you will need this tool. The package is free to use and runs on Linux, Windows, and macOS. There is a paid version available but it is the same program but easier to install. John the Ripper Pro is only available for Linux and macOS.
Pros:
- Efficient Password Testing: Highly effective at cracking passwords using dictionary-based attacks.
- Lightweight Utility: Minimal resource usage, making it an efficient tool for system administrators.
- Flexible Dictionary Use: Allows users to employ custom dictionaries for tailored testing.
Cons:
- No GUI: Does not offer a graphical user interface, which may limit its accessibility to less technical users.
11. Aircrack
Aircrack is a must-have tool to detect flaws inside wireless connections. Aircrack does its magic by capturing data packets so that the protocol is effective in exporting through text files for analysis. It’s supported by different operating systems and platforms, and it offers a great array of tools that will allow you to capture packets and export data, test WiFi devices and driver capabilities, and many other things.
Key Features
- Wireless Penetration Testing: Essential tool for evaluating wireless network security.
- Data Export: Allows for the exporting of captured data for further analysis.
- WiFi Analysis: Specializes in analyzing WiFi network vulnerabilities.
Why do we recommend it?
Aircrack-ng is a penetration-testing staple for wireless networks. It is widely used by hackers, because not only can it detect wireless network signals but it can crack passwords for access. You might also consider OpenWIPS-ng, which was created by the same person and is officially an intrusion prevention system.
Who is it recommended for?
If you need to investigate and probe wireless networks, this is one of the best tools around – even though it is quite old now. The tool is free to use and will run on Windows, Linux, Unix, and macOS. You can use this system to capture packets and then analyze them in other tools.
Pros:
- Dedicated Wireless Focus: Expertly handles wireless security assessments and audits.
- Broad Compatibility: Runs on multiple operating systems including Windows, Linux, Unix, and macOS.
- Encryption Cracking: Capable of decrypting weak wireless encryption to assess network security.
Cons:
- Narrow Scope: Limited to wireless security, lacking versatility for broader network testing needs.
12. Burp Suite Pen Tester
This tool contains all the essentials to successfully perform scanning activities and advanced penetration testing. It this fact that makes it ideal to check web-based apps, because it contains tools to map the attack surface and analyze requests between destination servers and the browser. It does so by using web-penetration testing on a Java platform. It’s available on numerous different operating systems, including Windows, Linux, and OS X.
Key Features
- Comprehensive Scanning: Well-suited for detailed scanning and penetration testing.
- Web Application Focus: Tailored for testing and securing web-based applications.
- Java Platform Optimization: Particularly effective for applications built on Java.
Why do we recommend it?
Burp Suite Pen Tester is another popular tool. It is very easy to use and you get the lower package for free. The higher functions are visible in the free tool but they are disabled. This does you a favor because the higher service is actually a vulnerability scanner.
Who is it recommended for?
Every penetration tester should get Burp Suite. However, the full version is very expensive. The free tool gives you all of the systems you need to operate as a penetration tester and its high price makes it only accessible to consultancies. The interface provides both data-gathering tools and attack systems.
Pros:
- Integrated Toolset: Offers a wide array of security tools in one package.
- Accessibility: The Community Edition is available for free, making it accessible to smaller entities.
- Cross-Platform Compatibility: Supports a range of operating systems including Windows, Linux, and OS X.
Cons:
- Complexity: The suite’s extensive features require time to learn and master effectively.
Conclusion
Pen testing is extremely important for the integrity of security systems in any kind of organization, so choosing the right tool for each individual job is essential. The ten tools presented here today are all effective and efficient for what they were designed to do, which means they will allow pen testers to do the best possible job to provide organizations with the information and forewarning they need. The goal here is to strengthen systems and eliminate any vulnerability that will compromise system integrity and security.
Penetration Testing FAQs
What are the main penetration testing methodologies?
Penetration testing requires white hat hackers to try to break into a system by any means possible. This is an intuitive art but methods fall into four categories:
- External methods: Try to break into a network from a remote location
- Internal methods: Activities that can be performed once in the system, modeling an insider threat or an advanced persistent threat.
- Web application methods: Using widgets and APIs in websites to access private systems.
- Social engineering methods: Using phishing and doxing to trick system users into disclosing access credentials.