
Online stalking, also known as cyberstalking or online harassment, is a problem that has largely arisen as part of the internet era. Just like offline stalking, it can have a devastating impact on victims. Several trends contribute to the ease in which cyberstalking may be carried out. These include accessibility to vast amounts of personal information (for example, through social media) and the variety of ways in which we can communicate (through various platforms and apps).
While the psychological profiles of online stalkers tend to quite closely match those of offline stalkers, there are a couple of differences. Cyberstalkers are more likely to be ex-partners of their victims and are less likely to approach their victims. However, most cyber stalkers do use some offline tactics.
Cyberstalking can cause severe emotional (and sometimes physical) distress to victims. What’s more, it can be difficult to prove, especially if the perpetrator is good at covering their tracks. In this post, we reveal more about online stalking, including some real examples, and discuss the laws around cyberstalking. We also provide lots of tips to help you protect yourself against cyberstalkers and explain what to do if you become a victim of this crime.
What is cyberstalking?
Cyberstalking or online stalking is a broad term for using online technology to victimize others. Cyberstalkers may use a variety of methods such as social media, email, and instant messaging to harass, bully, or threaten victims.
Typically, cyberstalking involves communication between the stalker and the victim, but in some cases, there may be no attempt at contact. For example, a cybercriminal might set up a fake social media account in someone’s name for the purpose of embarrassing the victim.
To illustrate online stalking as it happens in the real world, let’s take a look at some examples of cyberstalking, including many cases which have already been prosecuted:
Unwanted services
In Utah, Loren Okamura was accused of tormenting Walt Gilmore and his adult daughter online for over a year. He sent threatening messages to the daughter and posted her address online. He also sent over 500 people to their home for unwanted services that included tow trucks, food delivery, and prostitutes. Okamura was indicted in October 2019 on charges including cyberstalking and interstate threats, as well as transporting people for prostitution.
Rejection revenge
On December 5, 2019 in Nebraska, 20-year old Alec Eiland received a two-year federal prison sentence for cyberstalking. Eiland used social media to threaten, harass, and stalk two women who had rejected him romantically. Among other things, he demanded nude photos and threatened rape and other acts of violence. He posted one woman’s contact information online alongside an invitation for solicitations for sex.
Fake kidnapping
Jessica Nordquist, a cyberstalker who went as far as faking her own kidnapping, was jailed by a London court in December 2018 for four and half years. The US national carried out an extensive cyberstalking campaign against her ex-boyfriend. She sent him a barrage of texts and emails and created more than a dozen Instagram accounts for the sole purpose of harassing him.
As part of the campaign, she even sent him messages and images supporting fake claims she had been kidnapped and assaulted. The charges laid against her included stalking involving serious alarm or distress, malicious communications, and perverting the course of justice.
Parkland victims’ relatives
As if the relatives of the Parkland school shooting victims hadn’t been through more than enough, many were cyberstalked by Brandon Fleury, aged 22, from California. He admitted to sending threatening messages to family members of some of those killed in the shooting at Marjory Stoneman Douglas High School in Parkland, Florida in 2018. He created multiple fake Instagram accounts used to taunt victims’ relatives at the end of 2018 and in early 2019. In March 2020, Fleury received a sentence of five years in prison.
Law school rejection
Cyberstalking incidents often involve rejected would-be suitors or former partners. However, a case in Delaware involved an attorney being victimized by a rejected interviewee. Ho Ka Terence Yung launched an attack on the victim, who was an alumni interviewer at a law school that rejected Yung. The victim and his family were subjected to harassment for 18 months.
Among other things, Yung attributed racist, violent, and sadistic posts to the victim, and accused him of sexual assault and child molestation. He even had prostitutes and men interested in casual sex go to the victim’s home. Yung was sentenced to a prison term of 46 months in February 2019.
Hacked home cameras
Recently, a spate of cyberstalking attacks involved home surveillance systems. In these cases, cybercriminals torment victims using the very things that are supposed to keep people safe. One terrifying example involved a man hacking the Ring camera of a Mississippi family and beginning a conversation with an eight-year-old girl.
As you can see from the above examples, anyone can be a victim of cyberstalking, and for any reason (or no reason at all). Victims could be chosen at random, or someone might use cyberstalking in retaliation after a disagreement, breakup, or rejection. Businesses can become targets of cyberstalking by competitors or people disagreeing with their practices.
Online stalkers can be very good at covering their tracks, using fake social media profiles and apps that help them evade monitoring. Indeed, many cyberstalkers prolong their attacks because they believe they are invisible online. While there are many tools to help them remain anonymous, law enforcement can often find ways to catch up with them.
Laws against cyberstalking
Cyberstalking is a relatively new crime and it continues to evolve alongside ever-advancing technology. So how does cyberstalking fit within the legal system? The answer to that depends on which country you’re in.
US
In the US, cyberstalking is considered a criminal offense. However, it’s not explicitly covered under federal law. Instead, laws focused on harassment, slander, and stalking, along with the Violence Against Women Act, can be used in cyberstalking cases. But since these laws weren’t written with cyberstalking in mind, they don’t provide the scope that is necessary for some cases. In some situations, the laws are open to interpretation, which means the victim may not be adequately protected.
At the state level, more than a dozen states have enacted anti-cyberstalking laws. California was the first state to do so in 1999 when it introduced a new electronic stalking law under Penal Code 646.9 PC. Other states to have banned harassment or stalking via electronic devices include New York, New Hampshire, Illinois, Hawaii, Connecticut, Arizona, Alabama, Wyoming, Oklahoma, Florida, Alaska, Texas, and Missouri.
Canada
In Canada, the Department of Justice outlines cyberstalking under its criminal harassment law. Section 1.6 of the handbook begins by saying:
Criminal harassment can be conducted through a computer system, including the Internet. The elements of the offence remain the same, it is just that technological tools are used to commit the offence.
It goes on to provide examples of acts that may constitute cyberstalking, including sending harassing messages, gathering information about the victim (including using spyware), engaging in “cyber-smearing” (attempts to destroy the victim’s reputation), tracking a victim using GPS technology, and sending malware to the victim’s computer, among others.
The maximum term for a criminal harassment offense is 10 years, but it’s noted that it may be prosecuted alongside other applicable offenses such as voyeurism, defamation, extortion, intimidation, and identity fraud.
UK
The UK’s original Protection from Harassment Act 1997 covered harassment but didn’t explicitly discuss stalking. The Protection of Freedoms Act 2012 amended the former and introduced a new section (2A. Offence of stalking).
While this doesn’t specifically talk about cyberstalking, it does offer examples of acts associated with stalking that could easily apply to online stalking. These include contacting a person by any means, monitoring someone’s use of the internet or electronic communication, and publishing content that may relate to a person or purport to originate from someone else.
Australia
In Australia, the Stalking Amendment Act (1999) covers cyberstalking. It doesn’t mention online stalking or cyberstalking directly, but it does call out contacting someone through the use of any technology. When it meets other specific criteria, this can constitute a form of stalking.
There has been debate about some cyberstalking laws as there are cases in which there is a fine line between cyberstalking and free speech. However, these cases are more often those that concern public figures such as politicians.
How to stop cyber stalking
As you can see from the experience of others or perhaps your own, online stalking is a serious matter. Thankfully, there are lots of things you can do to help mitigate online stalking before or after it has begun. Of course, this is not to say that anyone invites this sort of activity. Rather, these tips will help lock down your digital privacy, limiting the ability of a malicious party to discover information about you and access your online accounts.
1. Don’t post personal information online
In the age of social media, it can be very tempting to share information about yourself, even if you feel uncomfortable doing so. Sharing quickly becomes oversharing and social media has made it trivially simple for criminals (including stalkers) to track and torment their victims.
Posting information about your home and family, your place of work, or where you like to hang out can be dangerous. Sharing your personal email address or phone number online is also a bad idea.
Note that even if you have stopped sharing personal information, it’s possible that old snippets could still be publicly available, for example, in forgotten accounts or profiles. If you’re unsure, it’s worth doing an online search for your name (and any other names you have gone by) to see what information is out there.
While a simple Google search can show you any obvious information that’s out there, a stalker may be delving deeper. OSINT (Open-Source Intelligence) refers to intelligence consisting of information collected from publicly available sources, including social media sites, public records, and chat forums.
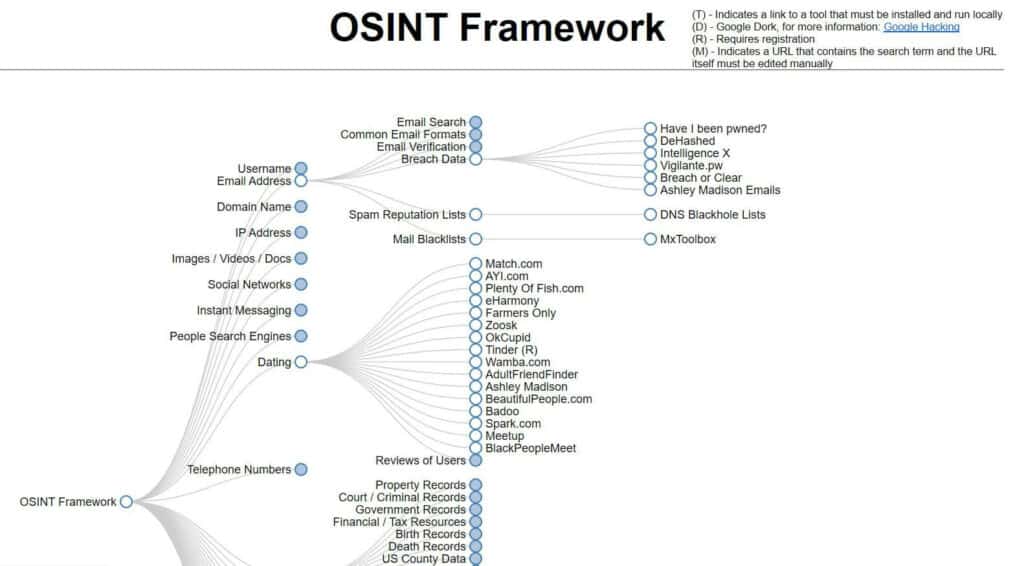
It can be used for constructive purposes such as improving your digital privacy or helping locate missing persons, but it can also be used maliciously.
With a little know-how, you can follow the OSINT framework to see what information is available about you online and then take the necessary steps to remove that information.
2. Tell your friends if you’re being stalked
It’s common for cyber stalkers to reach out to friends and family members of their victims, for example, to find out personal information or their whereabouts. They may even pose as their victim, for example, to ascertain information about their relationship with someone, or to spread hate messages on their behalf.
As such, if you think you’re being stalked, it’s better if your friends know to look out for anything out of the ordinary so it can be shut down before damage is caused.
3. Remove yourself from people search websites
One of the first things you can do to remove your personal information online is to reach out to people search directories and have them delete your information. Did you know that sites like BeenVerified, Intelius, and Spokeo scrape information from social media sites to create online directories? These are mainly intended for use by marketers, but could easily be used by online stalkers.
To remove your profile for these sites, most of them require that you fill out an opt-out form. Others make it more difficult and require that you subscribe to the service or mail a request along with copies of identification. With more than a dozen such sites out there, this can be a tedious task. If you’d rather have someone else do it, you can pay a service such as DeleteMe to opt-out of around 20 databases on your behalf.
4. Don’t post information about your location
Along the same lines, posting or revealing information about your location is not a good idea. Online harassment can quickly progress to offline stalking. If you’re doing things like “checking in” to a location on Facebook or allowing location sharing on various apps, you could be putting yourself in physical danger.
Geotagging photos is also an issue and is something that many users are unaware of. Cellphone cameras often have built-in location tracking so when you post a photo to social media, the location in which the image was taken may also be disclosed. You should be able to switch off this feature in your device settings. For example, iOS users can go to Settings > Privacy > Location Services > Camera and select Never.
Also let your friends know not to share information about your location, for example, by tagging photos you’re in or posting that they’re out and about somewhere with you.
5. Don’t accept friend requests from people you don’t know
If you have a Facebook profile, you’re no doubt familiar with receiving friend requests from others. You can change your privacy settings such that you choose what each person sees, but it’s far simpler if you limit your friend list to people who you’re happy sharing all of your posts with.
Plenty of people create fake profiles on Facebook for various reasons, but it’s often for the purpose of harassment. Facebook has some level of vetting, but it’s far from effective. It’s quite simple for someone to create a profile for the sole purpose of stalking you.
If you are having issues with someone, block them right away. On other platforms such as Twitter and Instagram, you can block specific profiles from following or messaging you.
6. Use strong passwords
This piece of advice is doled out time and again, but it remains an important one. Some online stalkers will attempt to hack into their victim’s accounts. They’ll then use them for various means, for example, posting lewd content or hate speech that appears to come from the victim.
If you use the same password across accounts, it only takes one data breach to enable criminals to hack into multiple social profiles, email platforms, and other accounts.
In addition, if someone has your email password and that email is linked to other accounts, it can be used to change the password for those accounts. This is because most password reset options work by sending you a reset link to your email.
Many cases of cyberstalking involve a former or existing spouse or partner, someone who may be privy to account credentials. If there’s any chance that an ex-partner may harass you online, it’s a good idea to change your credentials as soon as possible and use different passwords for each account.
If you’re having trouble remembering passwords, a password manager such as LastPass or Dashlane can help.
7. Activate two-factor authentication (or two-step verification)
While these are two slightly different processes, the terms 2FA and 2SV are often used interchangeably. Enabling two-factor authentication means that two steps are required to access an account, or in some cases, make account changes. One step usually requires a password, and the second might involve an email or text confirmation, or a form of biometric identification such as a fingerprint or face scan.
These simply add an extra layer of protection to your accounts. However, as mentioned, if someone has access to your email account, or your phone for that matter, they may be able to bypass these safeguards.
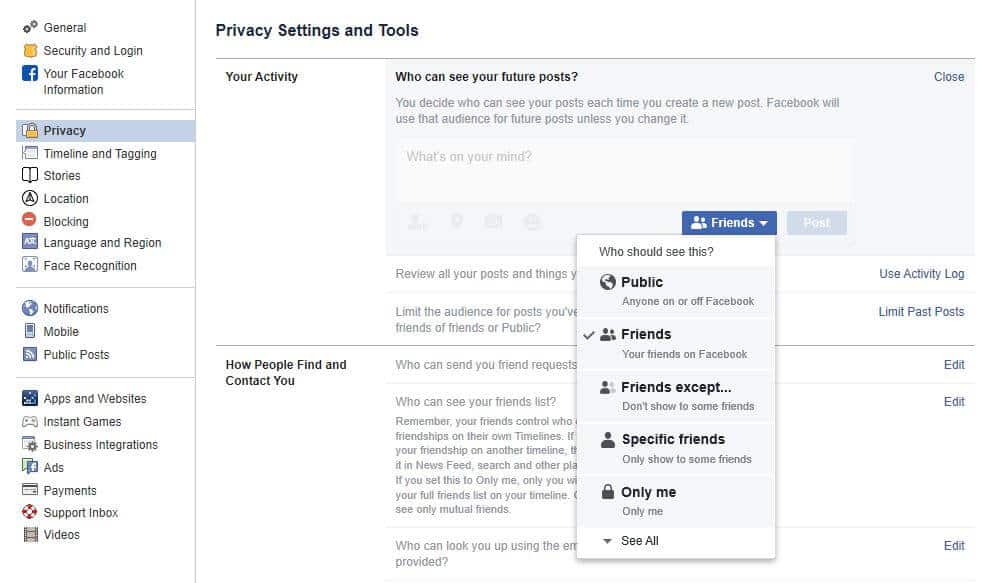
8.Tighten up your social privacy settings
Social media sites, such as Facebook, Instagram, and Twitter come with built-in privacy settings that you can adjust. For example, Facebook lets you decide who can see your profile, posts, friend lists, and friend requests.
It should be noted that these settings are usually set to give you the least privacy by default. In addition, these features are liable to change from time to time. As such, it’s worth checking your privacy settings periodically to ensure nothing has changed and that you’re getting the highest level of privacy.
9. Learn to spot suspicious emails and texts
A cyberstalker could use certain tactics that involve sending malicious emails and texts that don’t immediately appear as such. For example, a spear phishing email could look like it’s coming from a reputable sender when it’s really just phishing for information such as login credentials to a social media account.
In other cases, malicious emails may include links or attachments that lead to malware being downloaded onto the victim’s computer. This is a common tactic for installing spyware onto a user’s device and may lead to things like webcam hacking and keystroke logging (for discovering passwords).
Be wary of emails that request you respond to with any personal information. Check that they are genuinely coming from the purported sender by examining the email address for authenticity. Avoid clicking links and attachments unless you’re certain you can trust the sender.
Going back to the issue of webcam hacking briefly, this is a real problem that impacts victims across the globe. While antivirus software should be able to spot malware that’s controlling your webcam, you may want to cover it with tape or ensure your laptop is closed when not in use.
10. Find and remove spy apps
As a follow-on to the last tip, you may be concerned that someone has installed a spy app on your device. For example, a partner or ex-partner with physical access to your device can install an app that can track your location or spy on your communications. Or you could have unknowingly downloaded spyware from a malicious email or text. We go into detail about how to detect and remove spyware in a dedicated post.
11. Use an antivirus software
If a stalker is trying to install malware on your device, one of your first lines of defense is good antivirus software. This will detect and block many malicious programs before they can find their way on to your device. It can also detect malware that’s already on your system, giving you the chance to remove it.
Note that you can install antivirus software on your mobile devices too. However, it’s worth noting that someone with access to your device could install a legitimate app for the purposes of spying on or tracking you, one that antivirus software doesn’t pick up. As such, it’s a good idea to regularly review your app installs and settings.
12. Use a VPN, especially when using public wifi
A Virtual Private Network (VPN) is a must when it comes to online security and privacy. It encrypts all of the internet traffic traveling to and from your device. This means that it will be unreadable to any snoopers who manage to intercept it. This is useful for a variety of reasons, including to prevent tracking by your Internet Service Provider (ISP) or government.
It also prevents anyone on the same wifi network as you from accessing your information. For example, if you’re using unsecured public wifi, such as in a coffee shop, mall, or college campus there’s the risk that a hacker might be lurking on the same network, ready to steal your information.

A VPN can also be useful on a shared home network where your information may otherwise be exposed to other users in the household. Since cyberstalking is common among ex-partners, it’s not too far-fetched to think that someone could sit outside your home, connect to your wifi network, and snoop on your activity. Aside from securing your router (more on that below), you can use a VPN to protect yourself in this scenario.
13. Log and report any cyberstalking activity
We’ll go into more detail about this below, but it’s important to log any activity that makes you uncomfortable, even if you don’t think it constitutes cyberstalking at that moment. These situations can quickly escalate, so it’s better if you have a full record of all activity when the time comes to report it.
Advanced tips for outsmarting online stalkers
The above tips are relatively straightforward to implement, requiring little investment and minimal tech-savvy. However, if you’d like to further secure your online identity, here are some more advanced tips you may want to consider the following:
- Use encrypted email
- Use the Tor browser
- Secure your router and IoT devices
Let’s look at these in more detail:
1. Use encrypted email
While many messaging services come with encryption, either by default or optional, most mainstream email service providers don’t have settings that let you encrypt messages. This means that emails are fully readable to anyone who intercepts them, including cyberstalkers.
Encrypting email isn’t all that simple for non-tech-savvy users, but we do provide a guide for email encryption if you’re interested.
The other option is to switch to a special encrypted email service such as Hushmail or Tutanota, although you’ll have to pay for a decent version of these services.
2. Use the Tor browser
Another way to maintain your anonymity online is to use the Tor browser. This encrypts all of your internet traffic and passes it through multiple nodes (volunteer computers), making it very difficult for someone to track you online.
The major downside to the Tor browser is that encryption drastically slows down your internet connection so it’s impractical to use all the time. Plus, its use is commonly associated with illegal activity, which is another turnoff for some users.
See also: Best VPNs for Tor
3. Secure your router and IoT devices
If you’re sharing a network with anyone else, they might be able to intercept your traffic and view or modify it. Many people don’t bother to change their router password, leaving them vulnerable to snoopers. It’s important to take basic steps to protect your home router such as changing the password from the default and following firmware updates (you can usually set these to install automatically).
Other things you can do to secure your router (if you have the option and ability) is to set the highest level of encryption (WPA2), restrict outbound and inbound traffic, and turn off WPS. You can find out about these and more steps in our guide to securing your wireless router. Note that if you’re in doubt about whether or not anyone has access to your network, you should use a VPN, even while at home.
Internet of Things (IoT) devices such as home assistants and security systems can pose risks too. They may be sending or receiving information that can be used to determine information about your day-to-day life or whereabouts. What’s more, as mentioned earlier, in-home cameras can be hacked allowing criminals to spy on and even communicate with you and your family members.
One of the most important things you can do to protect these and any devices is to install updates. These usually contain security patches that fix known vulnerabilities. You should also change the default passwords and “wake words” (for home assistants) and avoid storing any personal information on these devices.
How to report cyberstalking
Cyberstalking and online harassment are recognized as forms of stalking under various laws across the globe. If you’re experiencing cyberstalking, you should contact your local law enforcement. To help them help you, it’s a good idea to provide them with as much information as possible.
As mentioned, if you ever feel uncomfortable in an online situation, be sure to keep records of all communications or situations that have made you feel uncomfortable. You can keep a log of events in a simple spreadsheet, but even more helpful is photographic proof of events. Take screenshots of any activity that the stalker has undertaken as part of their campaign. It’s best to start this as soon as possible, even if something seems relatively insignificant. This way, you’ll be able to show how the situation has escalated over time if that’s the case.
Since screenshots can be doctored, it’s worth taking a picture of a message on the device with another camera. If you’re keeping track of phone calls or text messages, delete the person’s name from your contacts so that the phone number is visible. This will help serve as proof of who is calling if needed. Also, remember to save or record any voice messages as these may automatically expire after a specific period of time.
Cyberstalking FAQs
What's the best way of reporting cyberstalking?
You can report cyberstalking to the FBI. This requires filing a report with the Internet Crime Complaint Center (IC3). Cyberstalking best fits in the “Other Cyber Crime” category. Upon selecting this, you’ll be asked to provide pertinent information including your contact details and a description of the cyberstalking incident in question. Alternatively, you can contact the nearest FBI field office or report cyberstalking via tips.fbi.gov.






Are there companies that will come to your home for cyber security?
It depends on where you live but a service like Best Buy’s Geek Squad might be what you’re looking for. They can help you install cyber security software if you’re not comfortable doing it yourself. They can also provide ongoing tech support and help with things like virus and spyware removal. Most customers take their device to a store but house calls are an option in some areas, albeit at an extra cost.
How can I prove who my instagram stalker is? I have a business account and can’t set it to private. I know who it is, but need to prove it. They’ve made themselves pretty obvious at first but now trying to cover themselves up.This person has driven by my place of residence multiple times as well, so I’m afraid this will escalate. The courts don’t help me at this point, I just need proof.
You should seek professional legal advice or notify police and ask them what to do next. Even if you think you don’t have enough evidence, it’s worth having it on record. Make a record of every interaction, be it online or physical, including dates and times and present this when you report the situation to police. You could also try to go through Instagram’s reporting channels as well.
I’m being stalked and harassed by phone – Facebook and emails – is there a list or group that list the guilty parties -how can I bring it to peoples attention ?
Depending on where you live, there may be resources to help you with this. In the US, the National Center for Victims of Crime has a stalking resource center (https://victimsofcrime.org/stalking-resource-center/).
I’m not 18 and I do not want to have Police on my back. My stalker is also under 17, I know he cannot do anything since he’s in another country but I can’t take his messages anymore. “Don’t you worry about your sister?” or “I have your location”. I tried blocking him but he just keeps on making new accounts. I don’t know what to do. I feel unsafe.
Consider blocking the user from all relevant platforms and report the incidents to police.
PLEASE HELP US! We ARE BEING HACKED! CYBER CRIMES HAVE BEEN HAPPENING WITH US OVER 2 years NOW ! Cant TAKE IT ANYMORE!! They’ve been stalking us especially ME TOOK PICTURES OF ME ON THE TOILET PUT IT ON FACEBOOK! WONT GO TO BATHROOM WITH A LIGHT ON EVER AGAIN!! MY SIGNIFICANT OTHER IS IS ALSO VERY ILL ANXIITY !! And WE DONT KNOW WHAT YO DO , WE KNOW THESE PEOPLE MANU YEARS ! APPLE CANT REACH US THE LADYS BEEN TRYING SHES GIVIN UP ?
Record all evidence you can and report the harassment to your local police.
What options are available when the (cyber) stalker is in another country? The victim is in Canada, the stalker in the US. The victim has done all the things listed to prevent the stalker from accessing her and her information but other than going completely analog she is out of ideas. She has removed herself from the digital world as much as possible, and is suffering horrendously from the emotional abuse.
Keep a record of all incidences and report the harassment to local police. Even if the stalker is in another country, local law enforcement will likely have more luck getting a response from the operators of the platforms on which the abuse is taking place.
The person stalking me and my husband is a relative, but he is using a fake name, and account to do it. We know by things he says that it’s him, but how do I prove his identity?
Depending on how well he’s covering his tracks, law enforcement may be able to prove his identity through ISP and other records. Keep a record of all relevant communication or other activity and report the situation to your local police. It’s also worth reporting to any relevant platforms being used by the stalker.
My ex had been cyberstalking me prior to our separation and divorce. It has been non-stop for as long as 2008 and hasn’t stopped. He knows where I am and who I’ve been talking to and it’s being done through various technological means. I believe I’ve locked down my emaill accounts via a security key however, he has been able to track me via credit card purchases. He knows me well and even though we are states apart he has been relentless.