As streaming services ramp up their efforts to cut down on password sharing, an emerging Netflix account hack may give the company and its users something to worry about. Dozens of websites are already offering free access to Netflix, no password required.
The hack relies on an easy web-browser-based bypass to access other users’ paid or free trial accounts. There’s also little Netflix or other streaming services can do about it without dramatically impacting user experience.
Over the past 12 months, a growing number of websites began openly advertising what they term “Netflix Premium Cookies.” The code from these browser-based files can be shared and, when implemented correctly, completely bypass Netflix’s account security methods, allowing total access to a premium Netflix account without the need for login credentials or payment.
Using this method, anyone can easily avoid paying for a Netflix account. We’ve found that at least some of these freely-available Netflix session cookies access registered trial accounts that were likely created just for this purpose. However, we also found this account bypass method can also be used with stolen Netflix user data from paid accounts.
Based on what occurred in 2018 following Facebook’s own cookie-stealing malware threat, it’s possible some of these “free” Netflix cookies are instead stolen and not offered via free trial accounts. In either case, this method violates Netflix’s Terms of Service for account sharing.
Through our ongoing research into Netflix, we discovered:
- Over two dozen websites either regularly post, or have posted, Netflix cookie data (usually advertised as “Netflix session cookies”). This allows anyone to bypass normal account security methods and illegitimately access the Netflix content library.
- Some websites update (or claim to update) their cache of Netflix cookies as frequently as every hour.
- A majority of these websites were registered within the past 12 months, which may indicate a new campaign to capitalize on this bypass method.
- Many of these websites now appear high on Google Search results.
Almost every website now uses what are known as “cookies” to store visitor information. As you visit a website, the site’s servers tell your computer or device to create and store a small file that contains information about your visit. If you’re logging into an account, the file will also contain anonymized information via code that lets the server know who you are upon subsequent website visits.
Cookies make the web significantly more useful and faster and create a less time-consuming browsing experience. They are also used to track users’ interests and behaviour.
The persistent cookies like those Netflix and many other streaming services use make it possible to access your accounts without the need to re-enter your username and password each time you visit. They’re notably useful for tho
se who stream through smartphone or tablet apps, TV-connected devices like the Roku or Amazon Fire TV, or through smart TVs.
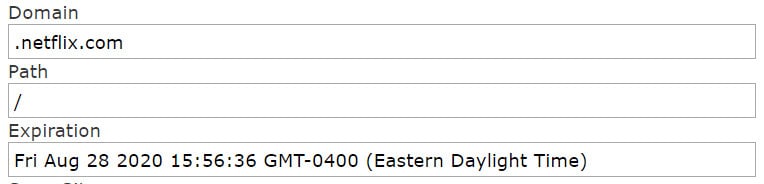
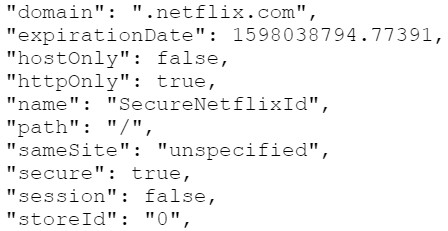
When you visit a website and log into your account, the website’s server directs your device to create and store a small file that contains rudimentary information and security “flags”. Notably, the cookie file holds information on the date the file was created, when the file will expire, a unique ID, and additional flags that help secure the cookie from certain types of hacking and misuse.
For example, here is what is part of what your session cookie file might look like after you visit the Reddit homepage:
{ "domain": ".reddit.com", "expirationDate": 1631368533.249147, "hostOnly": false, "httpOnly": true, "name": "token", "path": "/", "sameSite": "unspecified", "secure": true, "session": false, "storeId": "0", "value": "eyJhY2Nlc3NUb2tlbiI6IjM0NzE3NjE3LVFNdDJnMHg3ei0zT2U3YkhpRzE1SWpSRS1ONCIsInRva2VuVHlwZSI6ImJlYXJlciIsImV4cGlyZXMiOiIyMDE5LTA5LTExVDE0OjU1OjM0LjUzOVoiLCJyZWZyZXNoVG9rZW4iOiIzNDcxNzYxNy1WRW9KOHdqOXE1U3YyMkRvZWtUTG5ldUo3N1kiLCJzY29wZSI6IiogZW1haWwiLCJ1bnNhZmVMb2dnZWRPdXQiOmZhbHNlfQ==.2", "id": 14 }
The website’s servers also create a similar file with your session data.
When you leave and then try to access most websites sites or apps again, your device sends the persistent cookie to the website’s servers. The website verifies the unique ID, accesses your account details against the one it has stored, and then lets you waltz right in for your after-work TV binge or Amazon shopping spree.
All of this usually happens in just a few seconds, which is why you can tap on your Netflix app or go to the site in your browser and get to the profile selection screen almost instantly.
How long do persistent cookies last?
Persistent cookies can be designed to last for almost any length of time. The intervals are described in the cookie using seconds, and there isn’t much of an upper or lower bound. That means your persistent cookies could last anywhere from a few minutes to a few thousand years.
How long the cookie lasts is dependent on the website or service you’re using, as each company dictates to its web developers how long its own cookies should persist. It’s only when those cookies are designed to stick around after you’ve closed your browser or app that they fall into the category known as “persistent cookies”. Those cookies designed to delete when you leave the site are known as “session cookies” (although most sites offering Netflix cookies incorrectly refer to them as just “session cookies”).
Netflix’s persistent cookies are usually designed to last for about 365 days, which is also common among many websites. Unless you intentionally log out of Netflix or manually delete your cookies, those files will continue to let you into your Netflix account until the cookie expires.
Importantly, your Netflix cookies and any other persistent cookies do not have your password and username attached to them. If someone were to steal your Netflix cookie data, it couldn’t be used to steal your password, although it could still be used to access your account. The problem, indeed, is not that the cookies contain secure passwords, but that they bypass the need for passwords altogether.
Generally speaking, these secure cookie files should only exist in two locations: each individual computer or device you use for your accounts, and the company’s servers whose services you’re accessing. So even though you stream Netflix from multiple devices, each of those devices has its own, unique session cookie.
Persistent cookies are designed to allow access to password-protected accounts without the need to re-enter account security information. However, they are not restricted to specific devices and do not contain any information that identifies or hardcodes a specific device or location to them. That means they don’t contain, for example, unique MAC addresses or IP addresses.
That also means if someone copies and shares that cookie file or just the data held within it, then it becomes possible to use that information to access a normally password-protected account. And with increasing frequency, that’s exactly what people are doing.
EditThisCookie
Most web users lack the technical knowledge or skill to edit cookie data the hard way. That’s where Chrome browser plugins like EditThisCookie for Chrome come in. These plugins make it easy to import and export cookie data without any skills or programming experience.
In fact, using this browser plugin, one can import and export existing cookie data in a few seconds. The only difficulty, at least until recently, would have been getting one’s hands on another Netflix user’s session cookie data.
Over the past 12 months, however, Google began indexing over two dozen websites offering “Netflix session cookies”, most of which also provide instructions for how to use the EditThisCookie Chrome extension to put the cookies into effect. Many of these sites did not just begin appearing high on Google searches in the past 12 months; most were also created within the past 12 months.
Additionally, most of these sites purposefully hide their ownership information. We did find one site that we were able to trace back to an individual developer in India. At the time of writing, he had not returned an emailed inquiry for more information on where these cookies are sourced.
While I tested this method internally from one web browser to another on the same computer (Chrome to Opera), we verified that this works with cookies obtained externally.
We exchanged Netflix cookie data between myself and another Comparitech editor. Using EditThisCookie, I was able to access the Netflix account of our senior editor Paul Bischoff, for example, without needing his login information. All I did was:
- Copy his cookie data (sent to me via a text file)
- Use the “Import function” in the EditThisCookie Chrome plugin
- Paste the cookie data
- Refresh the browser page pointing to Netflix
In a few seconds, I had access to his account. I found I had complete privileges, as well, including the option to change his password, the email address associated with the account, and the option to log him out of his devices. I could also see the IP addresses of his most-recently-used devices (information that could be used to institute a DDoS attack or in a SWATTing attack) and his browsing history.
Netflix does require you to enter your current password if you want to change to a new one. But anyone who gains illegitimate access to your account can see your email address and phone number. This info could be cross-referenced with info exposed in past data breaches—easily obtainable on the dark web—potentially allowing a hacker to obtain a password and take over the account. That is why it’s always important to use a unique password for each online account.
The only thing I couldn’t do (thankfully), was gain access to his complete payment details (just payment name, the last 4 digits of the credit card used, and the card’s expiration date. Even still, that might be enough information to convince a less discerning bank representative to provide more account details over the phone.
I could also substitute his payment details with my own if I wanted to completely take over his account.
There are some possibilities to consider. Many of these sites sharing Netflix persistent cookies claim to be doing so legally. The typical statement they include is that these cookies are freely and equitably shared from individuals who personally pay for accounts, or register for free trials. At a minimum, that means they are flagrantly violating Netflix’s Terms of Service (ToS) regarding account sharing. And indeed, in testing, we located at least one cookie file shared on one of these sites that worked to access a free trial account.
However, with so many sites offering free cookies, and with many claiming to update them daily or even hourly, there’s the chance that some of these cookies could be stolen. There’s also recent precedent for this type of activity in light of the cookie-stealing Stresspaint malware Facebook encountered in 2018.
Frank Downs, Director of Cybersecurity Practices at ISACA, agrees. “This could be the result of several different actions,” he tells us.
“Yes, websites could be sharing cookie information, but… what may be more likely is that there is a serious vulnerability which attackers are able to exploit that is widespread. This may even be a disclosed vulnerability that has not yet been addressed by Netflix, let alone all of the partners that leverage Netflix’s streaming services.”
Netflix not willing to act
To his credit, Downs was spot on. According to a November 2018 Medium post by a cybersecurity researcher known as blueberryinfosec (Bbinfosec), Netflix is indeed aware of the vulnerability—and considers it “out of scope.” In other words: an end-user problem, not theirs. In his November 2018 post, Bbinfosec explained how he reported the issue to Netflix as part of its bug bounty program.
The number of websites sharing Netflix cookies and the aforementioned bypass method rapidly increased shortly after Bbinfosec posted his report.
If there is wide-spread cookie theft, it remains a mystery as to where these cookies may be stolen. The most likely answer is through older and less-secure devices infected with cookie-stealing malware operating similarly to Stresspaint, through XSS attacks, or from devices that are being hijacked through Man-in-the-Middle (MiTM) attacks.
Read more Netflix articles here:
To uncover the extensiveness of the potential threat, Comparitech conducted several tests to determine how many cross-site scripting (XSS) vulnerabilities exist that hackers could use to steal Netflix cookies, how many websites currently have those vulnerabilities, and whether an XSS attack could gather a Netflix user’s cookie data for external use.
More specifically:
- We used Shodan to search for 14,221 XSS vulnerabilities published on CVE, 204 of which had hosts online that were vulnerable to attack
- We found 28,173,468 instances where running services, like Apache, are affected by those XSS vulnerabilities
- The most common vulnerability we found was CVE-2018-17082 in PHP. It affects 4.8 million websites
Because of Netflix’s cookie policies, attackers can use any of the vulnerable services we found to steal Netflix session cookies. We tested it for ourselves in the lab and were able to use a compromised website and a known flaw in an old version of Firefox to steal a session cookie.
Netflix’s support of older devices
The problem extends beyond just vulnerable websites, however. Older devices create a security threat when cookies are involved.
According to ISACA’s Direct of Cybersecurity Practices, “outdated systems used by the victims make them more susceptible”.
Most Netflix users are likely streaming through updated devices, but Netflix still supports some older web browsers common among Windows 7 and Windows Vista operating systems. These lack some of the more recently updated cookie security flags that could help prevent cookie theft.
Netflix works on many older web browsers and many less-secure devices. The app can also be downloaded onto low-cost Android-based streaming devices sold through eBay or Amazon. Those devices could have had cookie-stealing malware pre-installed by the seller.
Additionally, anyone streaming through older TV-connected devices, or even smart TVs, may be far more susceptible due to less frequent and less effective device updates. Those using such devices “are susceptible to potential attacks for longer spans, providing a greater window of attack for the malicious actors,” Downs explained.
While it’s possible some of these site owners and their sources are operating with a sense of altruism, it’s also possible some may be complicit in Netflix account theft. The advertised and offered Netflix cookie data is possibly sourced privately from hackers and monetized through on-page ads on these sites.
In mid-2018, cybersecurity company Radware issued a warning about the virus “Stresspaint”. Couched inside a similarly named app called “Relieve Stress Paint”, the malware discreetly steals victims’ Facebook persistent browser cookies. Once Stresspaint’s programmers obtain these files, they can quickly bypass normal Facebook account security methods—including username and password requirements and multi-factor authentication—to illegally access Facebook accounts.
“Stresspaint” is alarming, but also not a novel approach to account theft. More technically referred to as “session hijacking”, this internet security threat is a known problem for almost any website out there that utilizes password-protected accounts. But it’s particularly problematic for widely popular websites, like Netflix, that use persistent cookies, or cookies that don’t automatically delete after you close your web browser.
In fact, account takeovers are a very real concern with this type of cookie abuse, as Netflix does not require you to enter your password to access your account settings.
Our in-house experiment only hints at the greater problem, however. There appears to be a highly noticeable increase in activity related to bypassing Netflix account security using session cookies. Between August 1 and August 26 of 2018, we found no websites indexed by Google for the term “Netflix session cookies”.
Just 12 months later, and during that same search period 2019, we found around a dozen sites actively posting Netflix user session cookies and instructions for how to use them. Several also use keywords such as “100% working” and “hourly updated”, and based on a review of the websites, many do appear to be updating their list of session cookies regularly.
Outside of that search timeframe, we located over two dozen websites with articles posted in late 2018 up through late August (when we completed researching) that offer Netflix cookies and cookie editing instructions. Most of these sites share the same website registrar, which may indicate common ownership.
Fast-forward to today, and there are several pages’ worth of sites indexed by Google offering Netflix user session cookies.
Does Netflix have a new security threat on its hands?
Netflix has been a well-known brand for nearly a decade. It’s unlikely session hijacking or even more mundane misuse of Netflix cookies is particularly new. However, past hijacking and account sharing activities likely occurred through the dark web or through private communication channels between hackers.
Yet it seems something changed in late 2018.
The number of websites competing to publish updated Netflix session cookies proliferated in the past 12 months. Although these sites offer these cookies for free, they make money from their endeavors with low-effort pages dripping with on-page ads. It’s possible some of these sites may even carry malware, or seek to steal Netflix cookies with the type of cross-site scripting attacks mentioned earlier.
Widespread vulnerability
Session hijacking of this kind is nothing new — as Facebook’s Stresspaint problem indicates. Based on current designs, almost any website that uses persistent cookies can be “hacked” through stolen cookie data.
For its part, Netflix is employing the security measures required of it to help protect users. Netflix’s servers are designed to create session cookies with industry-standard security flags, including “HttpOnly”, “Secure” and “SameSite”. In layman terms:
- HttpOnly prevents malicious website code from sharing cookie data to JavaScripts (often through attacks called XSS injection or cross-site scripting)
- Secure forces your web browser to only send the cookie through HTTPS
- SameSite disallows the cookie from sending to a different website
By analyzing the cookies we located through these free Netflix cookie sites, we found the company is employing all of the currently-available cookie protection protocols on its end:
Nevertheless, it’s also possible that there’s a virus out in the wild collecting Netflix user cookie data. Flaws in current cookie security can allow hackers to bypass the HttpOnly and Secure flags, making it possible for some Man-in-the-Middle attacks to still work and scrape data from Netflix users, particularly those streaming over public Wi-Fi.
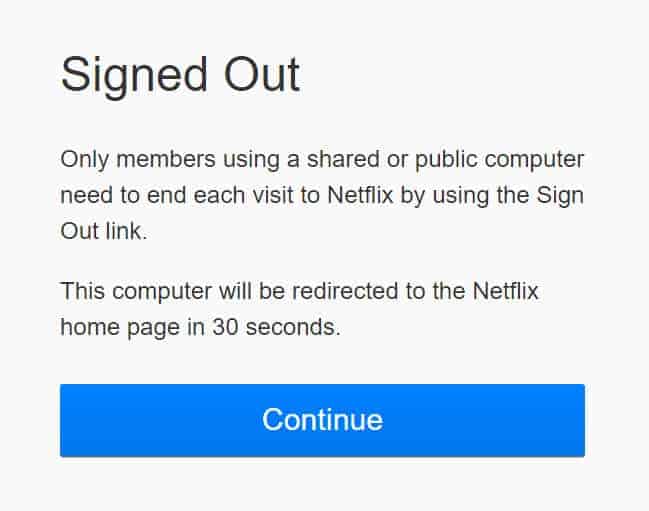
All that said, Netflix’s due diligence is somewhat marred by messaging from the company that intimates users have no concerns at all related to persistent logins. If you log out of your Netflix account on a web browser, for example, you may see this message on the logout screen:
Netflix states that “Only members using a shared or public computer need to end each visit to Netflix by using the Sign Out link.” However, consider the very real fact that Netflix persistent cookies can be stolen or abused. We’ve seen evidence of this already through Facebook’s malware issues, and our lab tests. This may not be the best advice for Netflix to give its users, even if it’s true most of the time. It’s more an issue of a want versus a need, in this case.
Netflix users don’t always need to log out, but in some cases, they very well may want to.
With tens of millions of users worldwide, it’s unlikely a high percentage of Netflix users have had their persistent cookies stolen. Nonetheless, those who are security conscious may want to take a few extra steps to prevent account takeovers or account abuse.
Check your email for new logins
Whenever a new device logs into your Netflix account, the service sends you an email to let you know. Check your email regularly, and look for new device login notifications from Netflix. Check the notification details and ensure that the device and location make sense. We found that you will get a new login email even if someone accesses your account using stolen cookie data.
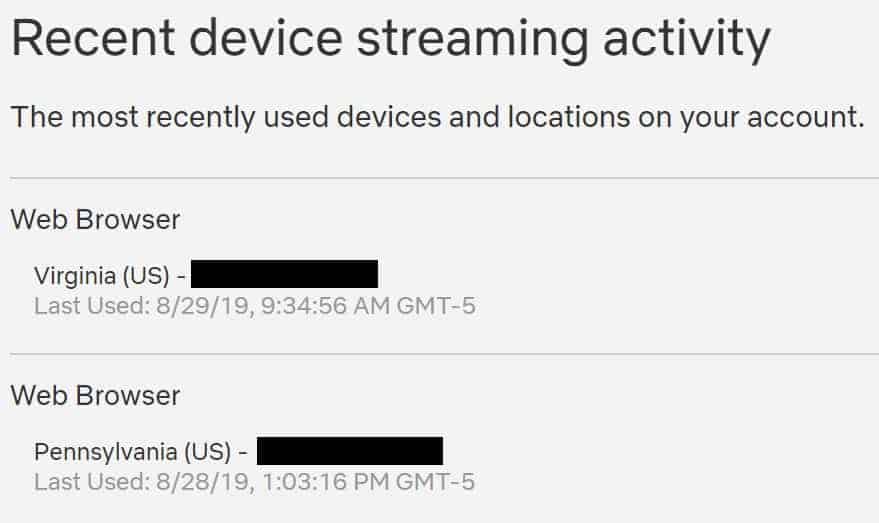
Check your recent device streaming history
In your Netflix account settings, find the section titled “Recent device streaming activity.” From there, review the most recent browsing activity, and look for any connections that might be out of the ordinary. Access from IP addresses in other countries or states you’ve never visited before may be a red flag. Note that if you’ve streamed Netflix through a proxy, such as a VPN, you may see IP addresses or locations that look unfamiliar.
Log out of all devices regularly
It may be a short-term inconvenience, but you can help prevent account abuse by logging out of all devices regularly. Thankfully, Netflix offers a handy option in your account settings that will automatically log out of all devices at once. The fewer devices you have with persistent logins on Netflix, the lower your chance of having a cookie stolen and abused.
Use a strong password for your Netflix account
Although it won’t protect you from persistent cookie theft and abuse, it’s still important to use and maintain strong, unique passwords for your accounts. Netflix provides some assistance in this regard by issuing a warning when you enter a password that “is not secure or is too common”. Do not ignore this warning.
The best option is to use a password generator to create passwords, and use a secure password manager to store your passwords for easy access and reference.
Run a virus scan on all devices and use a real-time antivirus program
If you suspect your computer or other devices may be infected, run an antivirus program to check for any potential malware on your system. There are numerous free virus and malware removal tools available.
Unfortunately, you won’t be able to run virus scans on TV-connected devices or smart TVs, but your chance of having viruses installed on those devices is small.
We also recommend installing and using a real-time antivirus tool to help protect against future infections. We have a regularly updated list of the best antivirus software currently available. Good quality AV software provides comprehensive protection without slowing your system down.
If you’re particularly concerned about MiTM attacks, make sure you password protect your home wifi network with a strong password and monitor your home network’s users for any potential freeloaders. Try to minimize your streaming on, or access to, password-protected websites while using public wifi. Alternatively, use a VPN when on public wifi to prevent would-be attackers from captured unencrypted data.
Upgrade your older devices
As ISACA’s Frank Downs noted, older devices are a major security threat, especially for apps like Netflix that use persistent logins. If you’re still using older devices, it’s probably best to upgrade.
Most of the popular TV-connected streaming devices like Apple TV, Roku, and Amazon Fire TV regularly push software updates to their devices (even many of their older models). Smart TVs, however, are known to have less frequent updates and, at times, no updates at all for past models. You may be better off using a TV-connected streaming device for Netflix and other services for your living room or bedroom TV.
The internet’s current infrastructure is built around speed and convenience, and persistent cookies are an integral part of that. Ease of use comes at the cost of security and, in their current state, persistent cookies certainly have a security loophole that may be difficult to surmount without some major changes to how cookies are built.
Downs has a few recommendations for those who want to better secure their online activities. One is to use Brave Browser, a security-focused web browser that includes many privacy features that help prevent tracking and malicious web activity.
Practice vigilance
Netflix users may also want to think carefully about their own web browsing behaviors. “Users should keep an eye out for anything that looks suspicious and think twice before clicking,” Downs explains.
And for those users who want the maximum amount of security when using Netflix and any other site, there’s always the nuclear option: script blocking. This prevents unwanted JavaScript from running. “However,” Downs said, “that will degrade the online experience and users should be ready for that.”
Stolen Netflix cookies make it easier for hackers to completely take over a user’s account. Additionally, anyone using someone else’s Netflix account could gather enough information from a user’s settings to hack into other personal accounts.
After testing, we not only confirmed that this persistent cookie trick works, but that cookies can be stolen. Worryingly, there are millions of websites out there that could be used to steal Netflix cookie data. Although the sites offering Netflix cookies claim to be doing so legitimately, and we confirmed at least some are only offering cookies associated with free trials, they are at a minimum breaking Netflix’s ToS and, at worse, could be engaging in, or helping to fuel, Netflix account piracy.
Netflix says that it takes “account security seriously” and if users receive an email saying that their email address or other login details have been changed — and they did not request the change — they should immediately get in contact.
Visiting a site such as Have I Been Pwned will confirm whether your email address or other details have indeed been compromised and shared publicly.
Aaron Phillips contributed to this story.









Do cookies store a Unique Identification for the browsers? For Example, If the cookie can store information about the web browser when someone copies the cookie and uses it in a different browser server can validate the browser unique Id with the unique Id from the cookie.
Hi Dinesh,
The cookies do indeed store information about the specific browser you’re using. That’s why we were able to use the same cookie across different Chrome browsers and from Chrome to Opera (which is built on Chrome), but not from Chrome to Firefox, or vice versa. Structurally the cookie files look the same between Chrome, Firefox, Safari, etc., but the data stored does indicate the type of browser.