Do you suspect that your computer or phone has been hacked? We’ll show you 10 clear signs you can use to tell if your device has been compromised. Being able to recognise them might just save you some serious trouble if spotted early enough.
Signs that your device has been hacked
Today’s cyber threat landscape has become more complex and challenging. The number of cyberattacks and data breaches has skyrocketed in the last few years, both in size and scope. It has become cheap and easy to hack computers and mobile devices, thereby giving cybercriminals unauthorized access to your personal devices and data.
The primary goal of security is to protect the confidentiality (data not stolen), integrity (data not modified) and availability (service remain uninterrupted) of computer systems and data. Anytime a system is hacked, data is leaked, an account is hijacked, or any other security incidents occur, you can be certain that one or more of these principles has been violated. Although most hacking incidents take place undetected, there are several tell-tale signs that your device is under attack.
1. Denial of access to your device, key system settings, or data
If you suddenly observe that you have been denied access to your computer or phone, it’s possible your device has been hacked. Denial of access can mean that you can no longer login to your device because your password has been changed by the intruder, you can no longer access key system settings such as factory reset or system restore options, or you’re subject to a ransomware attack.
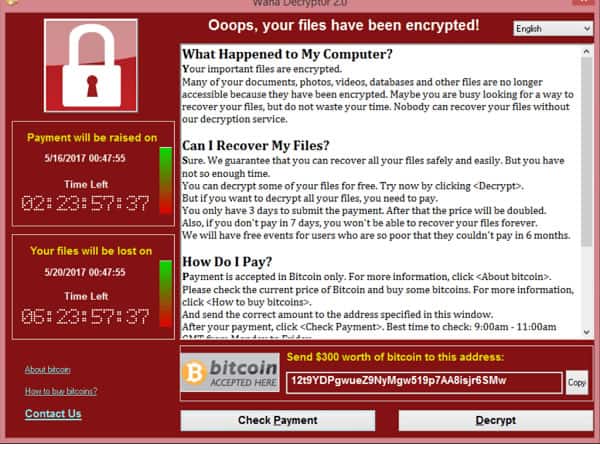
Ransomware is a type of malware that prevents users from accessing their computer device or personal files. It demands a ransom payment in order to regain access. Since 2012 ransomware attacks have seen a global exponential increase. In 2022, the FBI’s Internet Crime Complaint Center (IC3) received 2,385 ransomware complaints that cost victims over $34.3 million. Figure 1.0 shows a typical ransomware message display.
If access to your device is denied as a result of password change, you stand a chance to benefit from available password recovery options for your device. If you have multiple accounts setup on the affected device, you can use one of them – or preferably the Admin account – to regain access to the system. If you’re denied access to factory reset or system restore settings, get the system boot to Safe Mode (with networking) and clean it up with a good anti-malware such as Malwarebytes.
If it’s a ransomware attack, the best option is to format or flash the affected device and restore lost data from previous backups. If you don’t have a reliable backup you may have to gamble with paying the ransom, although there is no guarantee that you’ll get your data back.
The good news is that there are some cybersecurity firms that have figured out a way to reverse-engineer many ransomware strains. They can help you recover your files without paying the ransom.
2. Appearance of unknown applications you did not install
If you notice unknown programs, apps and/or processes running on your device, it is often a sign that an intruder has gained access to your device. Those unknown programs or processes may even appear legitimate to fool a user into thinking it’s harmless.
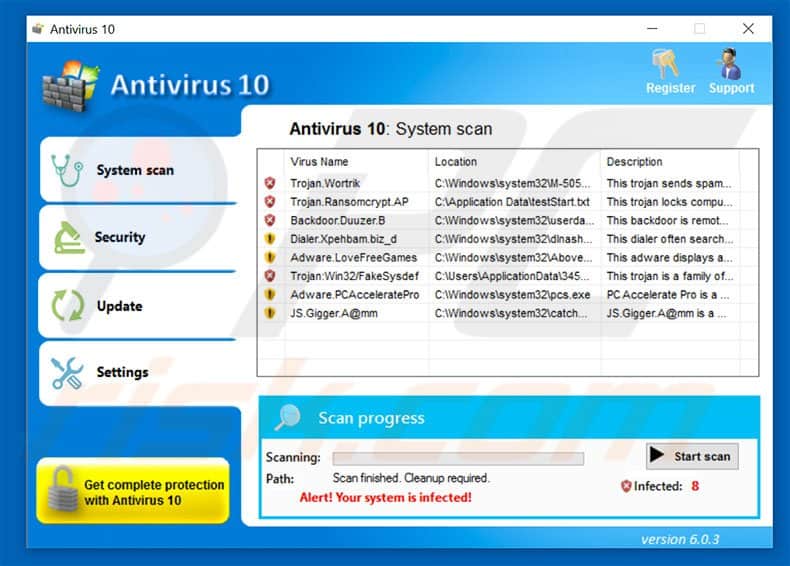
A typical example is malware that masquerades as an antivirus product that automatically scans your device and claims to find dozens of malware infections on it (see Figure 2.0). If you’re using a Windows machine, you can tell you’re infected when you notice that your computer’s antivirus program, firewall, task manager and/or registry has been disabled or changed. Malware may disable these applications to help cybercriminals block response options or any warnings that would appear while they are on your device.
If you find yourself in this situation, your best bet is to get rid of the malicious application by any means. Go through your list of installed apps and uninstall any suspicious application you can find. If you’re using a Windows machine, you can easily achieve this by booting to Safe Mode, and uninstalling suspicious programs. You also need to identify and terminate suspicious processes from the Task Manager. In addition, Malwarebytes is an excellent tool you can deploy to help you get rid of malicious applications on your machine.
3. Strange cursor movements and mouse clicks
It’s possible for a malicious third-party to remotely control your device and execute programs that you have the privilege to run, without your permission. If you see your device behaving as if someone else is controlling it, barring any known technical issues, your system is likely being exploited remotely.
If the mouse cursor is making orderly movements and clicks and opening applications – not just some random movements with no clear path of direction; you can be sure that someone else has full control. This kind of attack is dangerous and requires immediate action.
Unless you are really interested in knowing what the intruder is looking for, it is advisable to immediately disconnect the affected system from the internet or LAN. Use malware removal tools such as Malwarebytes to clean up the machine as a short term measure, change the Admin and other password access to the device, and get a professional to take a deeper look at the device.
4. Bogus browser toolbars and search redirection
You should be alarmed if you notice that your browser has strange new toolbars and plugins. Although it’s not unusual to have new toolbars in your browser after installing software from a known source, but unsolicited toolbars can mess with your browser settings (default homepage, search engine, etc.), and open the door to other malicious applications (such as keyloggers, Trojans, etc.), websites, and search redirection without your permission.
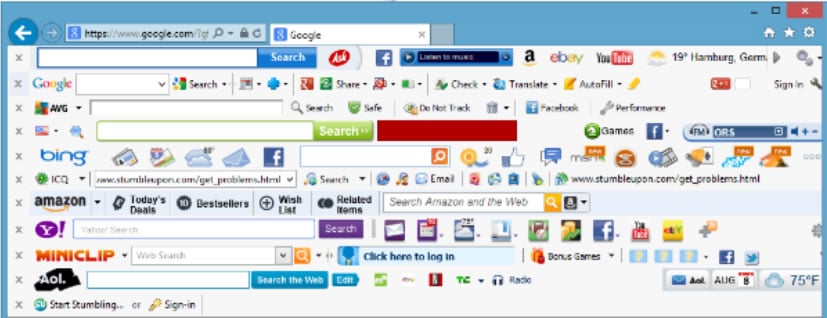
Redirecting users to particular websites for the purpose of generating traffic is a rewarding business for cybercriminals. They use bogus toolbars (as shown Figure 3.0 below) and other hidden programs to subtly interrupt your regular browsing, forcing you to other websites, or to download or purchase something regardless of what you searched for or the URL you clicked. It is so stealthily done that even the trained eye is easily fooled.
You can avoid malicious toolbars by applying caution when downloading free software that often bundles these toolbars alongside, and unchecking them when spotted. The first thing to do if you suspect a toolbar is to quickly uninstall it before they get the chance to wreak havoc. The longer they stay in your browser, the higher the risk of damage.
5. Your credentials and data exposed in a data breach
A data breach occurs when a cybercriminal gains access to a computer (personal or business) and steals your data. Determining whether or not your data has been breached can be a challenging task. Most breaches go undetected for years before the victim realizes what has happened. Your own systems may have already been compromised by cybercriminals. In many cases, you only find out when the cybercriminals decide to dump or put the data up for sale somewhere on the dark web.
Nevertheless, there are reliable online services that allow you to check whether your personal data has been compromised in a data breach. The most popular being Have I been Pwned? Others you can make use of are Identity Checker (which comes has a five-day free trial) and DeHashed. These services collect and analyze hundreds of database dumps containing billions of leaked personally identifiable information, and allow users to search for their stolen data.
Users can also sign up to be notified if their credentials – such as a social security number of email address – appear in future dumps. When you find your personal information in the data dumps made available on those sites, you need no further proof that your data has already been hacked or compromised.
Once you have determined that your data was compromised, you also need to figure out what data was taken and how it can be exploited. Take action immediately by resetting all your compromised passwords before someone can exploit them. Contact your bank company if your payment card information was also stolen, and place a fraud alert on your name in a credit-reporting bureau.
6. You get locked out of your account
Cybercriminals love stealing passwords for obvious reasons, perhaps they know that most people are predictable and will reuse the same password for different accounts.
In many cases, after a computer or online account is hacked, cybercriminals change the password to enable them to take over the account. If the login password to your online account has changed, barring any technical glitch, it is a pointer that something has gone wrong – it’s highly likely that someone stole your login details and changed the password.
Phishing is one of the popular techniques used by cybercriminals to steal user login credentials. They attempt to obtain login credentials by disguising themselves as trustworthy entities to deceive the user into believing that the request is legitimate. Such scams usually redirect you to a look-a-like page where you unknowingly provide your account details to cybercriminals. This data-gathering process can be the first step in identity theft.
Again, the first thing to do in this instance is to quickly regain control of your account by attempting to change your passwords and security questions where applicable using a different device. Similarly, consider changing your passwords with other online accounts, especially if you are fond of reusing passwords.
It is also a good idea to inform your service provider, business associates, friends and family members on your contact list that you’ve been hacked, as the criminals may attempt to defraud your connections. Reporting a hack to service providers helps them track cybercrime and improve their security.
7. Your friends receive messages from you that you didn’t send
This is one of the easiest ways to tell you have been hacked. A friend was sleeping one night and was intrigued by the large number of missed calls and Whatsapp messages he received concerning an email purported to have been sent by him. He became curious and decided to check his email and realized there was a big problem – he had been hacked. Someone had gained access to his email account and had been making attempts to defraud everyone in his contact list.
There are also instances of folks receiving friends’ requests from someone already in their connection on Facebook. Do not ignore complaints from friends about emails or social media messages or connection requests they believe to have come from you. Keep a close watch on your “sent” folder, Instant Messages, or social media posts. If you notice emails, posts or suspicious activity that you don’t recognize, it’s likely that you have been hacked.
A SIM-swapping attack, also called SIM-jacking, is a popular type of account takeover technique employed by cybercriminals to intercept calls and SMS. Once the attack is successful, your phone will lose connection to the mobile network and the fraudster will receive all the SMS and voice calls intended for you. This allows them to intercept any one-time passwords sent to you via text, and thus circumvent any security features of accounts (email, bank accounts, social media accounts, etc.) that rely on two-step verification.
Once you have confirmed that your account has been hacked, that’s when the real work begins. Regaining control of an account may be as straightforward as following your documented incident response plan or by contacting a cybersecurity professional to help you.
Furthermore, consider securing your accounts with hardware-based two-factor authentication to minimize the chance of SIM swap attacks. At the very least, ensure you use unique strong passwords across your accounts. Use a password manager if you’re worried about keeping track of them.
8. You observe anomalous network traffic, data consumption, and performance degradation
Some cybercriminals are simply interested in stealing your computer or phone resources such as processing power, internet bandwidth, or SMTP capabilities. By infecting thousands of computers around the world, they can create what is called a “botnet” (a network of compromised computers controlled from one center), which can be used to send spam mails, crack passwords, mine cryptocurrency, or launch distributed denial of service (DDoS) attacks.
The cyber crooks may also infect your device with some other type of malware that causes an abnormal slowdown in your device performance, and/or sluggish or erratic internet connection. Your PC or phone may get unnecessarily hot, battery life drains faster than normal, and sudden spikes in bandwidth or data consumption occur even though your usage behavior hasn’t changed.
Your IP address might be blacklisted by web browsers and safe browsing plugins because it was found to be sending spam mails; and when you try to use a search engine such as Google or load a web page, it states there is unusual traffic from your IP and asks for recaptcha to confirm that you are not a robot.
You may also observe frequent repeated requests for login information when you access your Google, Apple, or Microsoft account. All these are clear pointers that your system has been hacked.
For the technically savvy, a packet analyzer such as Wireshark can help you see unusual traffic that is not associated with normal traffic from your system. If you see unexpected, strange traffic that you cannot explain, it’s probably best to kill the network connection and get a qualified network or security professional to begin an audit or incident response investigation.
Related post: Best Anti-Spam Tools
9. You receive strange debit alerts
If you suddenly notice strange transactions on your bank account or credit card, a criminal has likely stolen your information, hacked into one of your accounts, or hijacked your device. Most times the criminals make purchases online or transfer funds to an account they control. Other warning signs to look out for include:
Strange transactions: Look out for debit of very small amounts from odd locations and time zones. Sometimes cybercriminals try to test the validity of your card with small purchases before making larger ones.
- Denied card: If your account is compromised, your account could be emptied or your card could be frozen by your bank, leading to denied transactions.
- Blocked card or login: If cybercriminals attempt to access your account from odd locations or try to guess your password too many times, access to your account may be blocked to keep it safe.
- Data breach: Financial institutions affected by a known data breach or leak can open the door to unauthorized access to your account(s) on different websites, especially if you’re in the habit of using the same password across the board.
The first step you need to take is to attempt to quickly regain control of your account by calling your bank to report the fraud and changing your pins, passwords and security questions. In fact, your financial institution is in a good position to help safeguard your account and possibly recover funds to your account.
Get your computer or smartphone audited and cleaned up if you suspect it has been compromised. It’s also critical that you seek to understand the tricks and weak spots cybercriminals like to exploit to defraud users. Examples include: weak passwords, phishing links, public wi-fi, and data breaches, among others. This will go a long way in protecting you from future cyber heists.
10. You observe frequent random pop-ups and more ads
Spyware (spy software), trackerware (tracker software), hijackers, adware (ad software), and other related malicious software may not be as lethal as viruses, but they can be extremely annoying and disruptive. If you notice lots of ads appearing on your screen, it is an indication that your device may have been compromised.
These ads might appear as pop-ups or they can be injected directly into web pages on your browser.
Apart from causing a nuisance, interrupting and/or slowing down your device; they can also create spam messages that lure you to click on them. Spyware and the likes can also be used to launch further malware attacks, remotely monitor your PC or phone activities, or modify the regular ads that you see in order to replace them with malicious ones.
Malwarebytes and Spybot – Search & Destroy are great detection and disinfection tools to use on your computer or smartphone.


I have a serious question for you, I believe my network has been compromised for sometime now, and I’ve tried everything I could think of to verify if I am correct or not, I’ve monitored my event viewer via Microsoft. While skimming through the logs, I see multiple logs that I am confused about, and I notice certain phrases in the logs that make me uncomfortable but Im nofor sure if its a malicious file, or its a file that needs to be ran, or executed. Is there anyway you can provide me with a list all Needed applications, and software needed by the compter? And as well as tasks/services I need to go through and get rid of alot, but i dont want to delete or disable something thats pertinent to the OS or Boot Config. Please help, I beleive my computer may be getting accessed remotely.
thanks for the info!¢
Firstly, start by installing and scanning you computer with an anti-spyware program such as Malwarebytes if you haven’t done that yet. They detect everything from malicious applications to keyloggers and spyware apps. Secondly, download and install TCPView on your system to enable you see and block processes on your computer that may be connected to a specific remote address. Thirdly, check your computer for open ports and block them–Nmap is a good online port scanner. Finally, check your Wi-Fi security (avoid public Wi-Fi), and review installed programs on your computer and uninstall suspicious/unknown ones. I hope this helps.
Hi Amakiri, I hope you won’t mind me contacting you but I wondered if you have any knowledge of cyber stalking? This has been happening to my family for quite a while and nobody can get to the bottom of it. One of the strangest things is that we had the same IP address for nearly 5 years from 2014-2019 even though Virgin Media says we have a dynamic IP address. The IP address changed when we installed a new router in 2019 but the old IP address that we had for nearly five years is still accessing our Apple account ie when we obtained data from Apple it shows that we logged on to the Apple account with the old IP address. This is just one of the odd things that has happened but I wondered if you might know why this would happen? We wonder if we are on an unknown network maybe and/or someone (my daughter’s ex) could be using a VPN. He was in possession of the computer for 9 months after they split up before he gave the computer to my daughter.
Thank you
Hi Joan, I totally understand your concerns. But are you really sure your IP address actually changed when you installed a new router? Installing a new router does not necessarily change your IP address. Your IP can only change when you specifically request a new one, or move to a different ISP. Even though your IP address is “dynamic”, your ISP is not constantly issuing a new IP address to your house every time you go online. The IP lease renewal process acts like a handshake between your ISP and home router. If the connection is still valid, the ISP will not disrupt service via provisioning a new IP address. I hope this helps.