People looking to stay anonymous online are often told to use a Virtual Private Network or Tor. The problem is that to the layman, it’s not always clear how these online privacy tools work. We’re of the opinion that everyone should understand the services they’re using to secure their internet activity, which is why below, we’ll explain the key differences between VPNs and Tor and explain how each can provide an additional layer of protection as you browse the internet.
First things first: what is a VPN?
Normally, when you visit a website, it can see your IP address, which allows it to work out roughly where you are and who your service provider is. VPNs effectively act as a middle man, using advanced encryption protocols to scramble your data, and sending it through a server somewhere else in the world.
This process hides your real IP address, shields your online activities from anyone who might be watching, and allows you to access geo-restricted services like Hulu from anywhere in the world (provided you choose a server in the right location).
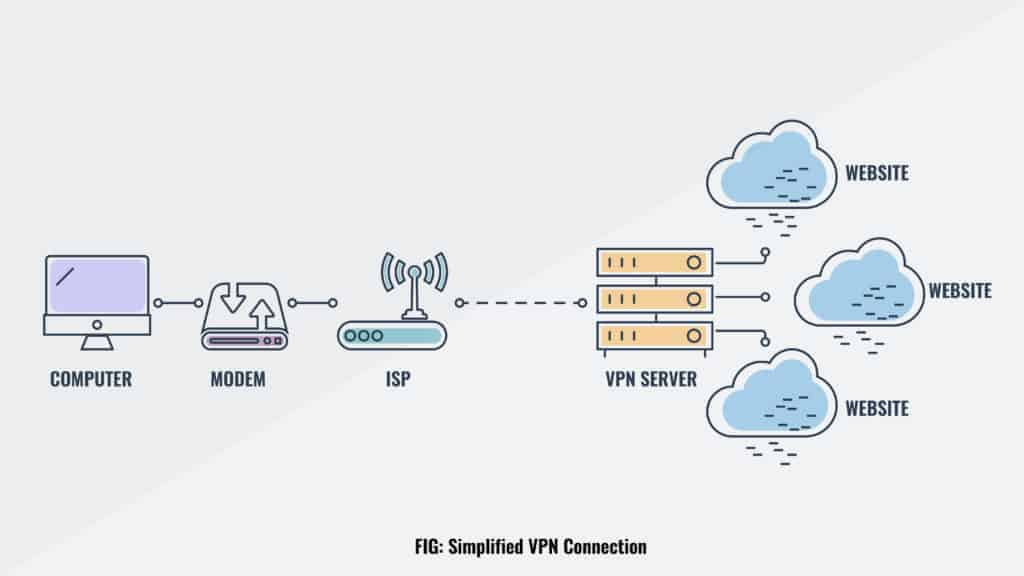 A VPN stops your ISP from seeing which sites you visit and prevents those sites from learning anything about your original connection
A VPN stops your ISP from seeing which sites you visit and prevents those sites from learning anything about your original connection
VPNs are a popular option for privacy-conscious internet users because they’re widely available, generally have reasonable connection speeds, and can be easily installed on most devices.
WANT TO TRY THE TOP VPN RISK FREE?
NordVPN is offering a fully-featured risk-free 30-day trial if you sign up at this page. You can use our top-rated VPN with no restrictions for a month. This is ideal if you’d like to try the service out before committing to a longer subscription.
There are no hidden terms—just contact support within 30 days if you decide NordVPN isn't right for you and you'll get a full refund. Start your NordVPN trial here.
What is Tor?
Tor is short for The Onion Router (sometimes called The Tor Network or Onion routing). It’s s a network of thousands of servers (or nodes) run by volunteers. When you try to access a website, Tor encrypts that request and sends it through a random selection of these middle servers. This means that your true IP address is effectively replaced with that of the final node in the sequence (which is known as an exit node).
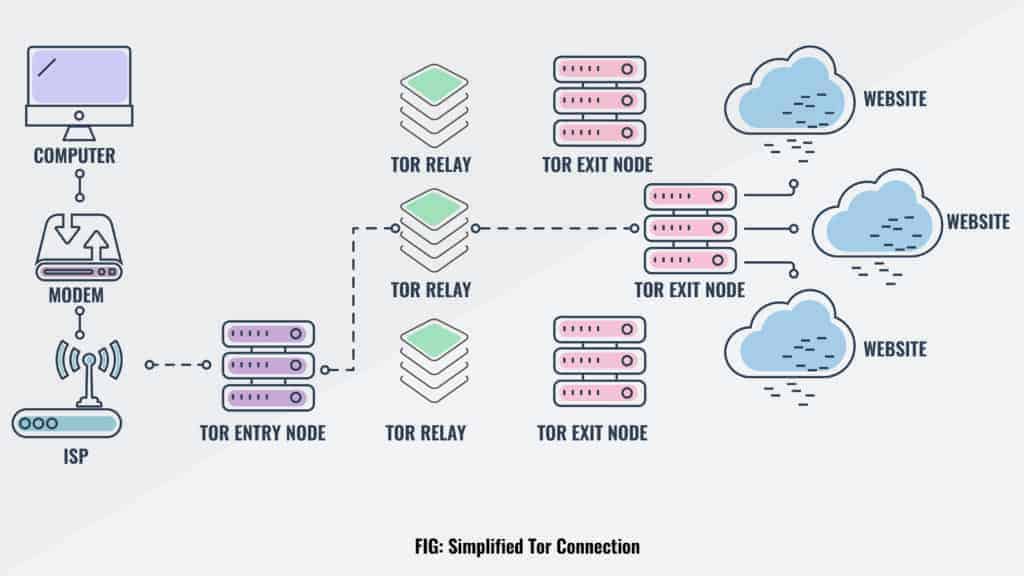 Tor keeps your activity private by effectively making it impossible for anyone to tell which servers your data passed through
Tor keeps your activity private by effectively making it impossible for anyone to tell which servers your data passed through
The problem is that encrypting data over and over takes time, which means Tor has a bit of a reputation for slow speeds. Still, there are thousands of sites on the dark web that can’t be accessed without the Tor Browser, so this is a sacrifice many are happy to make. Additionally, Tor allows you to access the wider internet in countries with repressive online censorship, making it a vital tool for free expression.
What is the difference between VPNs and Tor?
These technologies have quite a few things in common. For instance, VPNs and Tor both provide additional security by encrypting your traffic and concealing your original IP address. However, scratch beneath the surface and you’ll notice several significant differences. Let’s explore these below.
Centralized vs decentralized
The biggest difference is that a VPN is a centralized service. That means a central authority controls and manages connections. In this case, that’s the VPN provider, which is usually a private company. A VPN company might own and operate thousands of servers across the world for its users to connect to. While VPNs offer decent privacy and faster speeds, they do require users to trust the VPN provider to some extent.
Tor, meanwhile, is a decentralized network. In other words, no one owns or manages it, which means it can’t suddenly disappear one day. The only your data could be compromised is if a single organization was responsible for a large number of exit nodes, something that becomes less likely the more popular the service gets.
Single hop VPN vs Tor onion routing
A standard VPN connection passes your traffic through a single server. There are multi-hop VPNs that more closely replicate the technology underpinning Tor (albeit with faster speeds), but these are far from the norm.
Tor sends your data through no less than three relays at random. This means that every user benefits from multi-layer encryption, with one removed at each step of the way. This approach ensures that the people who own the middle nodes can’t see what you get up to online.
VPN apps vs Tor browser
Most major operating systems have VPN clients built-in. That said, in recent years, it’s become much more common for users to simply install an app. These are available for almost every device imaginable, including PCs, phones, and even routers. Good VPN apps can greatly improve the privacy and security of connections with features like leak protection, kill switches, obfuscation, split tunneling, and modulating IP addresses.
You can access Tor in a number of ways, but most users rely on the Tor browser. This is a Firefox-based web browser built with security and anonymity in mind. The Tor browser directs all web traffic through the Tor network. It doesn’t store your web history, doesn’t run scripts, and won’t keep cookies after you close it. Tor can be used in several other ways, ranging from entire operating systems like TAILS to communication apps like SecureDrop and Ricochet.
When should you use Tor?
Tor is better than a VPN for the following:
- Online anonymity: It’s almost impossible to trace a Tor connection back to the original user. You can safely visit a website without leaving any identifying evidence behind, whether on your device or the website’s server.
- Accessing the dark web: Tor can access the dark web (a.k.a. the darknet). This is mostly comprised of websites only accessible through a Tor connection and not found on Google. It’s often associated with illegal activity, such as black markets, but it’s used for a wealth of legal reasons as well.
- Untraceable communication: Journalists and their sources, whistleblowers, activists, dissidents, and victims of crime who wish to remain anonymous use Tor to securely communicate. This way, there’s no need to fear tracking or leaving behind a trail of evidence.
Tor by default does not let you choose the location from which you access the web. In addition, most websites can recognize traffic coming from a Tor exit relay, which they can then block accordingly.
Although Tor is very secure, connections have to pass through Tor entry and exit relays. These relays are public, so your ISP and other third parties can know when you’re using Tor. Even if they can’t tell what you’re doing or who you are online, simply using Tor at all could raise suspicions because many people associate it with criminal activity. You can get around this with a Tor feature called bridges, but that’s a discussion for another article.
When should you use a VPN?
A VPN is better than Tor for these purposes:
- Unblocking region-locked content: Many streaming services only allow access to viewers from certain countries. A VPN lets you “spoof” your location by changing it to any country where the VPN provider operates servers, thereby bypassing region restrictions.
- Torrenting: VPNs are much faster than Tor, allowing far more bandwidth for P2P downloads. Some even offer port forwarding, giving you access to a wider range of peers.
- Securing public wifi: If you’re on-the-go and need to use public wifi, a VPN is more convenient. Its encryption prevents hackers from snooping and launching man-in-the-middle attacks, but won’t otherwise hamper your browsing experience.
- Bypassing censorship: If you’re somewhere like China where the government blocks huge swathes of the internet you can use a VPN to access censored content as if you were in another country.
- Prevent ISP throttling: Some internet service providers throttle certain types of internet traffic, such as torrents or video streams. A VPN will help you hide this activity, reducing the chance of throttling in the future.
- Accessing blocked content at work or school: If you work or study somewhere that restricts access to the web, a VPN can bypass these blocks.
A VPN can hide your IP address, but the VPN provider can still see connection data and traffic passing through its servers. Although most VPN providers say they don’t log this information, you do still have to trust them somewhat. Meanwhile, Tor uses a trustless system (more on that later). This is why many consumer VPNs have had independent audits of their privacy policies recently.
A VPN won’t get you into the dark web (although their use is still popular). You’ll need a Tor connection to access .onion websites.
Tor vs. VPN FAQs
Can I use Tor and a VPN at the same time?
Yes! It will have a negative impact on your internet speed, but it’s certainly possible. The easiest way is to connect your device to a VPN and launch the Tor browser. This will route outgoing traffic through the VPN first and then through the Tor network.
This setup will make it more difficult for third parties to track you. If your internet service provider frowns upon Tor connections, then the VPN will hide the fact that you’re using Tor.
Tor vs VPN: Which should I use?
Both Tor and VPNs have their uses, but which you use depends on what you want to do.
A good rule of thumb is to use a VPN all the time and use Tor when you need it. A VPN improves privacy without interfering with day-to-day web browsing and internet usage. Launch Tor when anonymity is critical or you want to access the dark web.
Can I use a free VPN instead of a paid one?
Yes, you can use a free VPN. However, our research shows that they tend to be far less concerned about privacy than their paid counterparts. Additionally, they usually come with strict bandwidth limits and may even lock certain features off unless you’re willing to pay up.
If you’re forced to pay anyway, why not start with a paid VPN and see how it goes? Most of these offer a 30-day money-back guarantee, giving you the chance to try them risk-free. If you’re not impressed, you can just cancel to get a full refund.
Are VPNs and Tor legal?
Our exhaustive analysis shows that VPNs are legal in most countries, with places like China and the UAE placing limits on which providers you can use rather than banning them outright. You remain liable for any crimes commited while connected, however.
Tor is still legal everywhere, though access has been blocked in China, Russia, and Saudi Arabia. The Tor Project actively advises against running an exit node from your home given the potential for other users’ illegal activities being linked to your IP address.
Disclaimer: Although we’ve spent hours researching this topic, we are not legal experts. As such, nothing we’ve said above should be taken as legal advice. We encourage you to consult local laws or perhaps even seek a professional’s opinion before attempting to use these services if there’s any doubt as to their legality.
Is Tor completely anonymous?
No service can provide complete anonymity and any that claims to is lying.
While Tor’s multi-layer, decentralized design can greatly improve your online privacy, the fact remains that exit node operators can see unencrypted user data. This becomes even more problematic when you realize that law enforcement have the budget and know-how to run vast numbers of nodes, effectively granting them access to a huge amount of supposedly-private data.







