What is NIDS / Network Intrusion Detection Systems?
The risks that threaten your network security are now so comprehensive that you really don’t have a choice on whether or not to implement network-based intrusion detection systems. They are essential. Fortunately, you do have a choice over which NIDS tool you install.
All of the tools on the list are either free to use or are available as free trial offers. You will be able to take a couple of them through their paces. Simply narrow down the list further according to the operating system and then assess which of the shortlist features match the size of your network and your security needs.
NIDS is the acronym for network intrusion detection system. NIDS detect nefarious behavior on a network such as hacking, port scanning and denial of service.
Related post: The Best IDS Systems List
Here is our list of the best NIDS tools:
- ManageEngine Firewall Analyzer EDITOR’S CHOICE A solid vendor-agnostic firewall log and policy management tool. It supports a wide range of firewalls and security devices through agentless integration. Start a 30-day free trial.
- Snort An open-source Network Intrusion Detection System (NIDS) that analyzes network traffic in real-time, detecting malicious activity, intrusions, and potential security breaches with customizable rule sets and alerts. Runs on Windows, Linux, and Unix.
- AlienVault OSSIM This long-running free SIEM system provides both HIDS and NIDS systems, offering discovery and network inventory creation for asset management as well as intrusion detection. Runs on a VM.
- SolarWinds Security Event Manager A HIDS package with NIDS features. This comprehensive security tool runs on Windows Server and can process packet capture files generated by Snort.
- Zeek Previously known as Bro, this is a highly respected free NIDS that operates at the Application layer.
- Suricata This tool applies both anomaly-based and signature-based detection methodologies.
- IBM QRadar This cloud-based SIEM tool combines HIDS and NIDS capabilities.
- Security Onion A compendium of functions drawn in from other open-source HIDS and NIDS tools.
- Open WIPS-NG A free tool for defending wireless networks.
- Sagan A HIDS that can operate as a NIDS, given a live data feed for input.
- Splunk A widely-used traffic analyzer with HIDS and NIDS capabilities.
The purpose of NIDS
Intrusion detection systems look for patterns in network activity to identify malicious activity. The need for this category of security system arose because of changes in hacker methods in reaction to earlier successful strategies to block malicious activities.
Firewalls have become very effective at blocking inbound connection attempts. Antivirus software has successfully identified infections carried through USB sticks, data disks, and email attachments. With traditional malicious methods blocked, hackers turned to attack strategies such as Distributed Denial of Service (DDoS) attacks. Edge services now make those attack vectors less threatening.
Today, the Advanced Persistent Threat (APT) is the biggest challenge to network managers. These attack strategies are even now used by national governments as part of hybrid warfare. In an APT scenario, a group of hackers gain access to a corporate network and use the resources of the company for their own purposes as well as getting access to company data for sale.
The collection of personal data held on company databases has become a profitable business, thanks to data agencies. That information can also be used for malicious purposes and can also feed back into access strategies through doxing. The information available on company customer, supplier, and employee databases are useful resources for whaling and spearphishing campaigns. These methods have been used effectively by con artists to trick company employees into transferring money or disclosing secrets personally. These methods can be used to blackmail company workers into acting against the interests of their employers.
Disgruntled employees also present problems for corporate data security. A lone worker with network and database access can wreak havoc by using authorized accounts to cause damage or steal data.
So, network security now has to encompass methods that go far beyond blocking unauthorized access and preventing the installation of malicious software. Network-based intrusion detection systems offer very effective protection against all hidden intruder activity, malicious employee activity, and con artist masquerading.
What is the difference between NIDS and SIEM?
When seeking new security systems for your network, you will encounter the term SIEM. You may wonder whether this means the same as NIDS.
There is a great deal of overlap between the definitions of SIEM and NIDS. SIEM stands for Security Information and Event Management. The field of SIEM is a combination of two pre-existing categories of protection software. There are Security Information Management (SIM) and Security Event Management (SEM).
The field of SEM is very similar to that of NIDS. Security Event Management is a category of SIEM that focuses on examining live network traffic. This is exactly the same as the specialization of network-based intrusion detection systems.
What is the difference between NIDS and HIDS?
Network-based intrusion detection systems are part of a broader category, which is intrusion detection systems. The other type of IDS is a host-based intrusion detection system or HIDS. Host-based intrusion detection systems are roughly equivalent to the Security Information Management element of SIEM.
While network-based intrusion detection systems look at live data, host-based intrusion detection systems examine the log files on the system. The benefit of NIDS is that these systems are immediate. By looking at network traffic as it happens, they can take action quickly. However, many activities of intruders can only be spotted over a series of actions. It is even possible for hackers to split malicious commands between data packets. As NIDS works at the packet level, it is less capable of spotting intrusion strategies that spread across packets.
HIDS examines event data once it has been stored in logs. Writing records to log files creates delays in responses. However, this strategy allows analytical tools to detect actions that take place at several points on a network simultaneously. For example, if the same user account is used to log in to the network from dispersed geographical locations and the employee allocated that account is stationed in none of those places, then clearly the account has been compromised.
Intruders know that log files can expose their activities and so removing log records is a defensive strategy used by hackers. The protection of log files is, therefore, an essential element of a HIDS system.
Both NIDS and HIDS have benefits. NIDS produces quick results. However, these systems need to learn from a network’s normal traffic to prevent them from reporting “false positives.” Particularly in the early weeks of operation on a network, NIDS tools have a tendency to over-detect intrusion and create a flood of warnings that prove to be highlighting regular activity. On the one hand, you don’t want to filter out warnings and risk missing intruder activity. However, on the other hand, an overly-sensitive NIDS can try the patience of a network administration team.
HIDS gives a slower response but can give a more accurate picture of intruder activity because it can analyze event records from a wide range of logging sources. You need to take the SIEM approach and deploy both a NIDS and a HIDS to protect your network.
Network Intrusion Detection Systems detection methods
NIDS use two basic detection methods:
- Anomaly-based detection
- Signature-based detection
Signature-based strategies arose from the detection methods used by antivirus software. The scanning program looks for usage patterns in network traffic including byte sequences and typical packet types that are regularly used for attacks.
An anomaly-based approach compares current network traffic to typical activity. So, this defense strategy requires a learning phase that establishes a pattern of normal activity. An example of this type of detection would be the number of failed login attempts. A human user might be expected to get a password wrong a few times, but a brute-force programmed intrusion attempt would use many password combinations cycling through a rapid sequence. That is a very simple example. In the field, the activity patterns that an anomaly-based approach looks for can be very complicated combinations of activities.
Intrusion detection and intrusion prevention
Spotting intrusion is step one of keeping your network safe. The next step is to do something to block the intruder. On a small network, you could possibly enact manual intervention, updating firewall tables to block intruder IP addresses and suspending compromised user accounts. However, on a large network, and on systems that need to be active around the clock, you really need to roll through threat remediation with automated workflows. Automatic intervention to address intruder activity is the defining difference between intruder detection systems and intruder prevention systems (IPS).
Fine-tuning of the detection rules and the remediation policies is vital in IPS strategies because an over-sensitive detection rule can block out genuine users and shut down your system.
The best Network Intrusion Detection Systems tools & software
This guide focuses on NIDS rather than HIDS tools or IPS software. Surprisingly, many of the leading Network Intrusion Detection Software are free to use and other top tools offer free trial periods.
Our methodology for selecting a network-based intrusion detection system
We reviewed the market for NIDS packages and analyzed the tools based on the following criteria:
- Live traffic analysis
- Packet inspection
- Anomaly detection
- A threat intelligence feed
- Triage to speed up processing and reduce CPU usage
- A free trial or a free tool that provides a risk-free assessment opportunity
- Value for money from a tool that provides adequate security and is offered at a fair price or a free tool that is worth installing
With these selection criteria in mind, we looked for competent network intrusion detection systems that have good reputations and have proven track records.
1. ManageEngine Firewall Analyzer (FREE TRIAL)
ManageEngine Firewall Analyzer is a centralized, vendor-agnostic platform for analyzing firewall logs and policies across multi-vendor networks. It identifies threats in near real-time through agentless collection from firewalls, VPNs, proxies, and IDS/IPS.
Firewall Analyzer is a strong NIDS-adjacent tool. It is ideal for visibility, compliance, and anomaly detection across firewalls. But if your goal is deep packet inspection and real-time intrusion blocking, you’d still need to pair it with a dedicated NIDS/NIPS engine like Suricata, Zeek, or Snort.
Key Features:
- Vendor-Agnostic Support: Supports firewalls from Check Point, Cisco, Fortinet, Palo Alto, and more.
- Log Analytics and Management: Agentless collection and analysis of firewall, VPN, IDS/IPS, and proxy logs with fast root-cause search.
- Firewall Policy Management: Finds redundant or conflicting rules. It recommends cleanups to improve performance.
- Real-Time Monitoring: Tracks VPNs, proxy activity, sessions, and bandwidth spikes to quickly detect anomalies.
- Compliance Management: Includes built-in reports for PCI-DSS, HIPAA, ISO 27001, NIST, GDPR, SOC 2, and others.
- Network Forensics: Provides detailed audits using raw log data and aggregated views.
Why do we recommend it?
We recommend ManageEngine Firewall Analyzer because it is one of the best centralized and vendor-agnostic solutions for managing, monitoring, and optimizing firewalls. Its agentless design means you can integrate it seamlessly with your existing infrastructure. This helps reduce or even eliminate the need for additional endpoint software. In addition, the software comes with built-in capabilities for policy analysis, which can help identify unused or misconfigured rules that could pose performance or security risks. It also provides actionable recommendations for remediation.
We also love the tool’s real-time monitoring engine, which captures bandwidth usage, user activity, and traffic anomalies. This is perfect for helping security teams detect and respond to incidents faster. If your business is in a regulated industry, you’ll find its automated compliance reporting especially valuable. This helps generate audit-ready documents for multiple frameworks without extensive manual effort. And last, but not least, the inclusion of VPN, IDS/IPS, and proxy log analysis makes it an all-in-one network security visibility platform.
Who is it recommended for?
Firewall Analyzer is perfect for MSSPs that need to manage multi-vendor firewall fleets. It is also ideal for organizations in heavily regulated sectors such as finance, security, healthcare, and energy. We also recommend this software if you are looking to scale your SMB deployments to distributed, multi-site enterprises. Especially if those require real-time monitoring or compliance automation.
Pros:
- Vendor Neutrality: Broad multi-vendor compatibility and agentless integration.
- Intelligent Policy Management: Comprehensive rule analysis and optimization capabilities.
- Built-in Compliance Support: Automated, multi-framework compliance reports.
- Proactive Visibility: Real-time monitoring with customizable dashboards and alerts.
- Enterprise Scalability: Scales from small to large, distributed environments.
Cons:
- Outdated UI Design: Interface design is functional but dated.
Pricing is available in three editions (Standard, Professional, and Enterprise) based on features and number of devices. Deployment is a download and install on Windows or Linux servers and integrates with a wide range of security systems. A 30-day free trial is available for all editions (Standard, Professional, and Enterprise).
EDITOR'S CHOICE
ManageEngine Firewall Analyzer is our top pick for multi-vendor firewall monitoring and compliance management. This is because it delivers an agentless, centralized view of firewall logs and rules. Its unique combination of features, like policy optimization, forensic investigation, and automated compliance reporting, makes it ideal for service providers managing distributed environments. Unlike other heavyweight SIEMs, Manage Engine Firewall Analyzer focuses on firewall and network security analytics. It stands out because it can be deployed quickly and remains cost-effective. In addition, its powerful scalability—from SMB deployments to MSSPs or enterprises—ensures it adapts to diverse use cases. Plus, its compliance automation saves countless hours of manual reporting. ManageEngine also provides strong support and documentation. So, the tool is quite approachable once deployed, even if the initial setup requires tuning.
Download: Get a 30-day FREE trial
Official Site: https://www.manageengine.com/products/firewall/
OS: Windows, Linux
2. Snort
Snort, owned by Cisco Systems, is an open-source project and is free to use. This is the leading NIDS today and many other network analysis tools have been written to use its output. The software can be installed on Windows, Linux, and Unix.
Key Features:
- Open Source: Freely available, fostering a supportive community for rule sharing and support.
- Packet Analysis: Captures and analyzes network packets for in-depth traffic inspection.
- Custom Rules: Allows for the creation and implementation of custom detection rules.
- Real-Time Traffic Analysis: Monitors network traffic in real-time to detect suspicious activities.
- Protocol Analysis: Analyzes various protocols such as TCP, UDP, IP, HTTP, FTP, and SMTP.
Why do we recommend it?
Snort is a widely-used NIDS and you can get it free of charge. This system is a little like Wireshark, but it provides pre-written detection rules that also make it a little like a SIEM. You can write your own rules to enhance the standard detection rules.
This is actually a packet sniffer system that will collect copies of network traffic for analysis. The tool has other modes, however, and one of those is intrusion detection. When in intrusion detection mode, Snort applies “base policies,” which is the detection rule base of the tool.
Base policies make Snort flexible, extendable, and adaptable. You need to fine-tune the policies to suit your network’s typical activities and reduce the incidences of “false positives.” You can write your own base policies, but you don’t have to because you can download a pack from the Snort website. There is a very large user community for Snort and those users communicate through a forum.
Who is it recommended for?
Anyone who runs a network is going to need to implement security measures and this is one of the best tools that are available. The quality of the detection system relies on the quality of the rules that you use. You can pay for a package of rules or get them for free from the community.
Pros:
- Community Support: Benefits from a large, active community for sharing rules and configurations.
- Versatility: Supports packet sniffing alongside log scanning for comprehensive traffic analysis.
- Preprocessors: Extracts useful information from protocols before the rules engine analyzes the packets.
- Logging and Alerting: Logs packets to disk and generates alerts for malicious traffic.
- OS Fingerprinting: Identifies operating systems on the network.
Cons:
- Support Dependency: Relies heavily on community for troubleshooting and support.
- Configuration Complexity: Requires fine-tuning to minimize false positives, demanding more user expertise.
Expert users make their own tips and refinements available to others for free. You can also pick up more base policies from the community for free. As there are so many people using Snort, there are always new ideas and new base policies that you can find in the forums.
3. AlienVault OSSIM
AlienVault OSSIM is a SIEM system. It stitches together HIDS routines with NIDS systems, so you get both types of IDS with this package. This system is one of the oldest intrusion detection systems around and it has gone through a few changes in ownership. It is currently owned by AT&T Cybersecurity which funds the development of the tool while keeping it free to use.
Key Features:
- Comprehensive Analysis: Offers detailed traffic analysis alongside log collection and correlation.
- Integrated IDS: Merges host and network intrusion detection for a layered security approach.
- Open Threat Exchange: Benefits from a global threat intelligence feed, enhancing its detection capabilities.
- Asset Discovery: Automatically identifies network assets for targeted security monitoring.
Why do we recommend it?
Despite being free, AlienVault OSSIM is one of the best security systems available. It combines functions of vulnerability management with threat hunting, so you get attack prevention as well as detection. This tool also provides a discovery function, so none of your assets are overlooked.
The OSSIM tool is able to scour your network and assemble an asset inventory. This service provides a list of devices for the OSSIM system to check. The tool performs a vulnerability scan and produces recommendations for system hardening.
A companion to the OSSIM system is the Open Threat Exchange (OTX). this complements the threat detection system and provides a blacklist of malicious sources. The OTX is gathered from across the world.
The data analysis service also compiles user profiles, identifying normal behavior and alerting for changes in that pattern. This provides an indication of account takeover or insider threats.
Who is it recommended for?
This system is suitable for use by businesses of all sizes. AT&T Cybersecurity offers a paid version, called USM Anywhere, which adds on more features. However the NIDS, discovery, and vulnerability manager are all on OSSIM, so many businesses would see no reason to pay for the higher version.
Pros:
- Inclusive Security: Combines vulnerability scanning with intrusion detection for comprehensive coverage.
- User-Friendly Interface: Features an attractive and intuitive dashboard for easy monitoring.
- Enhanced Visibility: Provides on-premises scanning and monitoring, ensuring detailed oversight of network activities.
Cons:
- Support Limitations: Lacks professional support, potentially complicating issue resolution.
- Cloud Blindness: Does not extend monitoring capabilities to cloud-based environments.
The free OSSIM system is an on-premises package that runs on a VM. Although it should be possible to use any virtualization system, users report more success with Virtualbox, which is available for free and runs on Windows, macOS, Linux, and Solaris. You can download the OSSIM ISO for free.
4. SolarWinds Security Event Manager
The SolarWinds Security Event Manager is mainly a HIDS package, but you can use NIDS functions with this tool as well. The tool can be used as an analytical utility to process data collected by Snort. You can read more about Snort below. Snort can capture traffic data that you can view through the Security Event Manager.
Key Features:
- NIDS and HIDS Integration: Seamlessly combines network and host intrusion detection capabilities.
- Snort Compatibility: Directly integrates with Snort for enhanced data analysis and threat detection.
- Event Correlation: Sophisticated algorithm that correlates diverse events to identify potential threats.
- Automated Remediation: Implements predefined actions automatically upon threat detection to mitigate risks.
- Comprehensive Alerts: Provides timely and detailed alerts for various threats, enhancing situational awareness.
Why do we recommend it?
SolarWinds Security Event Manager is a SIEM tool that collects and manages log messages, converting them into a common format and storing them in files. As log messages arrive, they are searched for signs of anomalous behavior. This detects malware activity as well as intrusion. Manual analysis is also supported.
The combination of NIDS and HIDS makes this a really powerful data security software. The NIDS section of the Security Event Manager includes a rule base, called event correlation rules, that will spot activity anomalies that indicate an intrusion. The tool can be set to automatically implement workflows on the detection of an intrusion warning. These actions are called Active Responses. The actions that you can get automatically launched on the detection of an anomaly include: stopping or launching of processes and services, suspension of user accounts, blocking of IP addresses, and notification sending by email, SNMP message, or screen record. Active responses make the SolarWinds Security Event Manager into an intrusion prevention system.
Who is it recommended for?
This package isn’t limited to intrusion detection because it also detects malware. The system also isn’t just able to scan networks because it collects log messages from endpoint operating systems and software packages as well. This system is an on-premises package that runs on Windows Server. It is suitable for large businesses.
Pros:
- Versatile Detection: Offers a robust combination of host and network intrusion detection systems, enhancing security coverage.
- Streamlined Analysis: Simplifies log analysis with intuitive filtering, reducing the need for specialized query languages.
- Rapid Deployment: Features numerous templates and rules for quick setup and minimal customization.
- Historical Insight: Advanced tools for analyzing historical data to identify anomalies and potential security breaches.
- Cross-Platform Support: Compatible with a wide range of operating systems, including Windows, Mac, and Unix-based systems.
Cons:
- Learning Curve: Requires time and expertise to fully leverage the platform’s advanced features.
- Platform Limitations: Primarily designed for Windows Server, potentially limiting its deployment in diverse IT environments.
This is the top-of-the-line IDS available on the market today and it is not free. The software will only run on the Windows Server operating system, but it can collect data from Linux, Unix, and Mac OS as well as Windows. You can get the SolarWinds Security Event Manager on a 30-day free trial.
5. Zeek
Zeek (formerly Bro) is a NIDS, like Snort, however, it has a major advantage over the Snort system – this tool operates at the Application Layer. This free NIDS is widely preferred by the scientific and academic communities.
Key Features:
- Layer 7 Inspection: Specializes in application layer traffic analysis for detailed security monitoring.
- Dual Detection: Utilizes both signature and anomaly-based methods for accurate threat identification.
- Scripting Flexibility: Allows custom scripting for tailored detection and response actions.
Why do we recommend it?
Zeek is an open-source network security tool and it is free to use. This package scans network traffic looking for traffic patterns. By default, it doesn’t store packets but it generates statistics from the packet headers. The tool looks for patterns of behavior and it also spots anomalous activity.
This is both a signature-based system and it also uses anomaly-based detection methods. It is able to spot bit-level patterns that indicate malicious activity across network packets.
The detection process is handled in two phases. The first of these is managed by the Event Engine. As data is assessed at higher than packet level, analysis cannot be performed instantly. There has to be a level of buffering so that sufficient packets can be assessed together. So, Zeek is a little slower than a typical packet-level NIDS but still identifies malicious activity quicker than a HIDS. Collected data is assessed by policy scripts, which is the second phase of the detection process.
Who is it recommended for?
This package is a good choice for any business. The system is not too difficult to learn, although you do need to dedicate a little time to getting to know the capabilities of the tool. The system operates a buffer of packets so that it can scan several simultaneously.
Pros:
- Customizable Detection: Offers extensive customization for security professionals through scripting.
- Advanced Analysis: Capable of analyzing application layer traffic, providing insights beyond traditional NIDS.
Cons:
- Limited OS Compatibility: Primarily supports Unix-based systems, excluding a broader range of environments.
- Specialist Knowledge Required: Demands in-depth understanding of network protocols and intrusion detection for effective use.
It is possible to set up remediation actions to be triggered automatically by a policy script. This makes Bro an intrusion prevention system. The intrusion detection software can be installed on Unix, Linux, and Mac OS. Zeek can be deployed in conjunction with Dynamite-NSM, a free Network Security Monitor, to expand its capabilities and to take advantage of their advanced graphical displays of log data.
6. Suricata
Suricata is also a NIDS that operates at the Application Layer, giving it multi-packet visibility. This is a free tool that has very similar capabilities to those of Bro. Although these signature-based detection systems work at the Application level, they still have access to packet details, which lets the processing program get protocol-level information out of packet headers. This includes data encryption, Transport Layer and Internet Layer data.
Key Features:
- Application Layer Focus: Examines traffic at the application layer for granular threat detection.
- Snort Rules Compatible: Integrates seamlessly with Snort rules for expanded detection capabilities.
- Multi-Protocol Monitoring: Supports extensive protocol analysis including TLS, HTTP, and DNS for comprehensive coverage.
Why do we recommend it?
Suricata is very similar to Zeek. It buffers packets so it can check for fragmented attacks and it also applies rules looking for known indicators. This tool examines packet header to get port numbers and identify vulnerable devices, producing recommendations for ports that need to be closed.
This IDS also employs anomaly-based detection methods. Apart from packet data, Suricata can examine TLS certificates, HTTP requests, and DNS transactions. The tool is also able to extract segments from files at bit-level for virus detection.
Who is it recommended for?
This tool is recommended for any network administrator that wants to implement security measures. The system is free to use and you get a package of detection rules, which you can alter or create your own. The system can exchange data and rules with other threat detection packages.
Pros:
- Advanced Detection: Offers unique visibility into application-layer activities, enhancing threat detection.
- Efficient Packet Analysis: Efficiently reassembles and analyzes protocol packets for thorough inspection.
Cons:
- Community Size: Lacks the extensive community support found in tools like Snort, affecting resource availability.
- Usability: Faces challenges in user-friendliness and dashboard navigation, requiring improvements for easier management.
Suricata is one of the many tools that are compatible with the Snort data structure. It is able to implement Snort base policies. A big extra benefit of this compatibility is that the Snort community can also give you tips on tricks to use with Suricata. Other Snort-compatible tools can also integrate with Suricata. These include Snorby, Anaval, BASE, and Squil.
7. IBM QRadar
This IBM SIEM tool is not free, but you can get a 14-day free trial. This is a Cloud-based service, so it can be accessed from anywhere. The system covers all aspects of intrusion detection including the log-centered activities of a HIDS as well as the examination of live traffic data, which also makes this a NIDS. The network infrastructure that QRadar can monitor extends to Cloud services. The detection policies that highlight possible intrusion are built into the package.
Key Features:
- Cloud-Based SIEM: Provides a flexible, cloud-based security information and event management system.
- AI-Driven Analysis: Employs artificial intelligence for enhanced anomaly detection and threat identification.
- Attack Modeling: Includes tools for simulating attacks, aiding in vulnerability assessment and mitigation planning.
Why do we recommend it?
IBM Security QRadar SIEM offers a similar strategy to the SolarWinds Security Event Manager in its network intrusion detection strategy. This service operates on log files and also pulls in SNMP records, which provides network activity detection. The system is based in the cloud and relies on a local data collector for source data uploads.
A very nice feature of this tool is an attack modeling utility that helps you test your system for vulnerabilities. IBM QRadar employs AI to ease anomaly-based intrusion detection and has a very comprehensive dashboard that integrates data and event visualizations. If you don’t want to use the service in the Cloud, you can opt for an on-premises version that runs on Windows.
Who is it recommended for?
The cloud location of this SIM tool makes it adept at collecting data from multiple sites, remote workers, and cloud platforms. The system is probably more than a small business would need and so its target market lies with large organizations. The attack modeling feature will appeal to penetration testers.
Pros:
- Remote Monitoring: Cloud-based infrastructure allows for monitoring across diverse locations and platforms.
- Customizable Dashboards: Offers highly adaptable visualizations for personalized security oversight.
Cons:
- Trial Limitations: A more extended trial period would be beneficial for thorough evaluation.
- Cost Considerations: Presents a significant investment, potentially out of reach for smaller organizations.
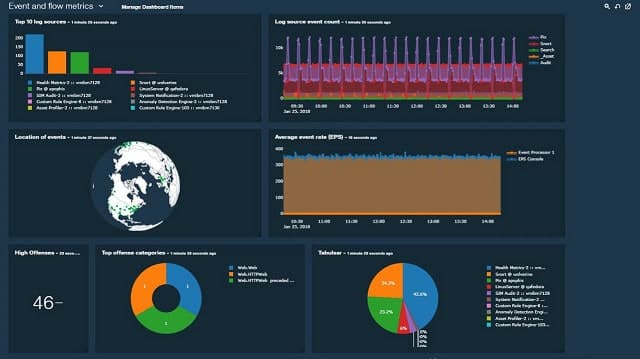
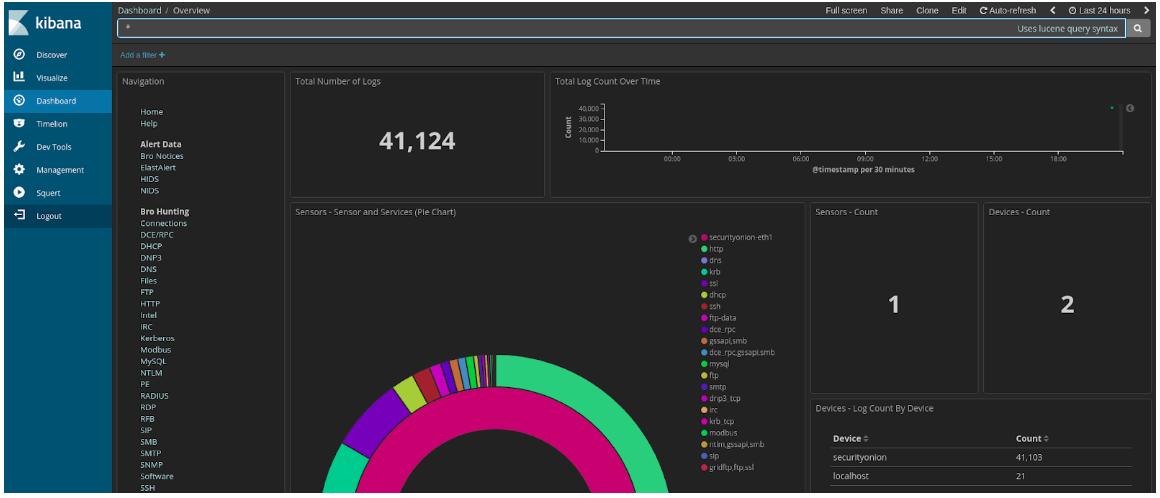
8. Security Onion
If you want an IDS to run on Linux, the free NIDS/HIDS package of Security Onion is a very good option. This is an open-source project and is community-supported. The intrusion detection software for this tool runs on Ubuntu and was drawn in from other network analysis utilities.
Key Features:
- Integrated Tools Suite: Bundles multiple IDS tools, offering both HIDS and NIDS capabilities.
- Comprehensive Coverage: Includes well-known tools like Snort, Zeek, and Suricata for diverse security strategies.
- Forensic Analysis: Provides detailed, forensic-level analysis tools for in-depth investigation.
Why do we recommend it?
Security Onion is a bundle of free, open-source intrusion detection systems. Its elements include both HIDS and NIDS tools. You probably won’t use all of the tools in the package. For example, there are several HIDS tools and several NIDS tools but you only need one of each.
A number of the other tools listed in this guide are integrated into the Security Onion package: Snort, Zeek, and Suricata. HIDS functionality is provided by OSSEC and the front end is the Kibana system. Other well-known network monitoring tools that are included in Security Onion include ELSA, NetworkMiner, Snorby, Squert, Squil, and Xplico.
The utility includes a wide range of analysis tools and uses both signature and anomaly-based detection techniques. Although the reuse of existing tools means that Security Onion benefits from the established reputation of its components, updates to elements in the package can be complicated.
You can use Kibana with Security Onion for enhanced threat detection.
Who is it recommended for?
Security Onion is free to use. This is probably too much for a small business but it is possible that a large business that has many different types of operations could benefit from different types of NIDS tools running simultaneously. The package includes Kibana as a front end for the whole bundle.
Pros:
- Extensive Toolset: Offers a wide array of pre-integrated security tools, enhancing detection and analysis capabilities.
- Forensic Detail: Tailored for deep forensic analysis, offering packet sniffing and traffic replay options.
Cons:
- Linux Only: Limited to Linux platforms, restricting its use in diverse IT environments.
- User Interface: Relies heavily on Kibana for visualizations, lacking a more intuitive, built-in dashboard.
9. Open WIPS-NG
Open WIPS-NG is an open-source project that helps you to monitor wireless networks. The tool can be used as a straightforward wifi packet sniffer or as an intrusion detection system. The utility was developed by the same team that created Aircrack-NG – a very famous network intrusion tool used by hackers. So, while you are using Open WIPS-NG to defend your network, the hackers that you spot will be harvesting your wireless signals with its sister package.
Key Features:
- Wireless Focus: Specializes in wireless network monitoring, offering both packet sniffing and IDS capabilities.
- Open Source: Freely available, encouraging community support and development.
- Automated Countermeasures: Capable of actively responding to detected threats, enhancing network security.
Why do we recommend it?
Open WIPS-NG is a packet sniffer and security tool for wireless networks. A nice feature of this system is that its probe that picks up network traffic for analysis doesn’t place extra load on the network and its sniffing can’t be detected by intruders. It is able to shut down the attacks that it detects.
This is a free tool that installs on Linux. The software package includes three components. These are a sensor, a server, and an interface. Open WIPS-NG offers a number of remediation tools, so the sensor acts as your interface to the wireless transceiver both to collect data and to send out commands.
Who is it recommended for?
This tool is free to use and is an important addition to the security services for your business if you deploy wireless networks. This system is suitable for use by businesses of all sizes and should also be considered by public locations and hospitality businesses that offer free
WiFi to customers.
Pros:
- Wireless Expertise: Developed by renowned security experts, ensuring robust wireless monitoring.
- Lightweight Interface: Features a command-line interface, optimizing resource use and efficiency.
Cons:
- Complexity for New Users: May present a steep learning curve for beginners due to its technical depth.
- Limited OS Support: Primarily available for Linux, narrowing its applicability in varied IT landscapes.
10. Sagan
Sagan is a HIDS. However, with the addition of a data feed from Snort, it can also act as a NIDS. Alternatively, you can use Bro or Suricata to collect live data for Sagan. This free tool can be installed on Unix and Unix-like operating systems, which means that it will run on Linux and Mac OS, but not on Windows. However, it can process Windows event log messages. The tool is also compatible with Anaval, BASE, Snorby, and Squil.
Key Features:
- Log Analysis: Focuses on analyzing log files for HIDS capabilities, with the option to integrate NIDS via network feeds.
- Compatibility: Works well with other security tools, enhancing its functionality through integration.
- Geolocation: Incorporates IP address geolocation for additional context on potential threats.
Why do we recommend it?
Sagan is a free open-source log file analyzer that can be used for network intrusion detection. Essentially, this is a HIDS, but you can feed in traffic data that has been processed by other packages in order to make it a NIDS as well.
Useful extras built into Sagan include distributed processing and an IP address geolocator. This is a good idea because hackers often use a range of IP addresses for intrusion attacks but overlook the fact that the common location of those addresses tells a tale. Sagan can execute scripts to automate attack remediation, including the ability to interact with other utilities such as firewall tables and directory services. These abilities make it an intrusion prevention system.
Who is it recommended for?
Sagan will give you a nice HIDS out of the box but it requires the addition of Snort and some tinkering in order to get it to do network detection as well. So, if you are only interested in a NIDS, you would be better off with Snort instead.
Pros:
- Flexible Integration: Supports data feeds from Snort, Zeek, and Suricata, offering versatile deployment options.
- Open Source: Free to use and modify, backed by a community for continuous improvement.
Cons:
- Limited Platform Support: Not available for Windows, restricting its use in mixed-environment scenarios.
- User Interface: May present challenges in navigation and clarity during extensive scanning operations.
11. Splunk
Splunk is a popular network traffic analyzer that also has NIDS and HIDS capabilities. The tool can be installed on Windows and on Linux. The utility is available in three editions. These are Splunk Free, Splunk Light, Splunk Enterprise, and Splunk Cloud. You can get a 15-day trial to the Cloud-based version of the tool and a 60-day free trial of Splunk Enterprise. Splunk Light is available on a 30-day free trial. All of these versions include data collection abilities and anomaly detection.
Key Features:
- Platform Flexibility: Available on-premises or in the cloud, catering to varied deployment needs.
- Comprehensive Monitoring: Combines NIDS and HIDS functionalities for all-around network security.
- AI-Enhanced Detection: Utilizes artificial intelligence for precise anomaly detection and threat analysis.
Why do we recommend it?
Splunk has transitioned from being a free tool for data analysis into a full commercial product with highly specialized monitoring capabilities. One of the packages available from Splunk is Splunk Enterprise Security, which has both HIDS and NIDS capabilities. Unfortunately, the free version has been removed.
Security features of Splunk can be enhanced with an add-on, called Splunk Enterprise Security. This is available on a 7-day free trial.
This tool enhances the accuracy of anomaly detection and reduces the incidences of false positives through the use of AI. The extent of the alerting system can be adjusted by warning severity level to prevent your system administration team from getting swamped by an overzealous reporting module.
Splunk integrates log file references to enable you to get a historical perspective on events. You can spot patterns in attacks and intrusion activity by looking at the frequency of malicious activity over time.
Who is it recommended for?
Splunk is a corporate solution for large enterprises. It is available in an on-premises package and as a cloud-based SaaS package. The software for those who want to run it themselves will install on Linux, Unix, and macOS. There is no version for Windows.
Pros:
- Cross-Platform: Supports both Windows and Linux, ensuring broad compatibility across IT infrastructures.
- Customizable Reporting: Features extensive reporting and dashboard capabilities for tailored security insights.
Cons:
- Cost Barrier: High pricing makes it less accessible for smaller organizations, positioning it towards larger enterprises.
- Learning Curve: Demands significant time investment to master, especially regarding its query language and setup process.
Implementing NIDS
Do you use a NIDS tool? Which did you choose to install? Have you also tried out a HIDS tool? How would you compare the two alternative strategies? Leave a message in the Comments section below and share your experience with the community.
Network Intrusion Detection Systems (NIDS) FAQs
Can NIDS and IPS work together?
Yes. NIDS and IPS work together very well. In fact, an IPS is just an IDS with extras. While an intrusion detection system spots unauthorized activity, an intrusion prevention system detects activity and then implements actions to shut that activity down. As an IPS has an IDS bundled into it, you don’t need to buy a separate IDS if you already have an IPS.
What does a network intrusion detection system do when it detects an attack?
Typically, an intrusion detection system is designed to identify anomalous behavior and raise an alert to draw attention to it. If you want a tool that will trigger remedial action on identifying an intrusion, you should be looking for an intrusion prevention system (IPS).
Where should a NIDS be placed to protect the entire network?
A NIDS needs to have access to all packets traveling around a network. In general, every packet passing over a network visits every device on it – it is just that the network adapter on each device ignores packets that aren’t addressed to it. So, the NIDS can be hosted on any device on the network just as long as that device’s network adapter has been placed in promiscuous mode to pay attention to all packets, not just those addressed to that device. If the network has several separate segments, such as with a demilitarized zone configuration, you can either host the NIDS on a connecting device, such as the router, or place a collector on the other segment that will communicate with the processing module resident on a host connected to the main network. A NIDS can also examine packets on a remote network if it has an agent installed there.
Image: Hacker Cyber Crime from Pixabay. Public Domain.













thanks for your knowledge i get all i wanted but please can i get a clear and understanding architectures on IDS and where to apply both NIDS and HIDS IDS
Hi, The key difference between NIDS and HIDS is that NIDS works on the network and HIDS works on endpoint information. Think of a NIDS as searching through the information that a network monitor collects. With a HIDS, the system searches through log messages for signs of malicious activity.
The processing module of an IDS can be located anywhere. If the server is in a remote location, it requires an agent on the monitored system that will send all of the necessary research to it.
Cheers,
Stephen