Apache HTTP Server, commonly referred to as Apache, is one of the most widely used web servers in the world, powering millions of websites and applications. Its popularity is due to its flexibility, open-source nature, and a broad ecosystem of modules and tools.
However, with great popularity comes increased scrutiny from attackers, making it critical to implement strong security measures to protect Apache installations from potential vulnerabilities and threats
Apache web server security involves a combination of best practices, configuration tweaks, and proactive monitoring to safeguard servers against unauthorized access, data breaches, and other cyberattacks. Properly securing an Apache server is essential not only for protecting sensitive data but also for maintaining uptime, safeguarding user trust, and ensuring compliance with industry regulations like GDPR, HIPAA, or PCI DSS.
Some of the key areas of focus in Apache security include securing configuration files, managing permissions, implementing HTTPS, and protecting against common threats such as Distributed Denial of Service (DDoS) attacks, SQL injection, and cross-site scripting (XSS). Leveraging tools like firewalls, intrusion detection systems, and robust logging mechanisms further enhances security and visibility.
This guide provides a detailed overview of how to secure an Apache web server. From basic settings and hardening techniques to advanced configurations and ongoing maintenance, we cover essential strategies to ensure your server remains resilient in the face of ever-evolving cyber threats. Whether you’re a seasoned administrator or new to managing web servers, these actionable tips will help fortify your Apache environment and keep your applications running securely and efficiently.
Why Apache Security is Important
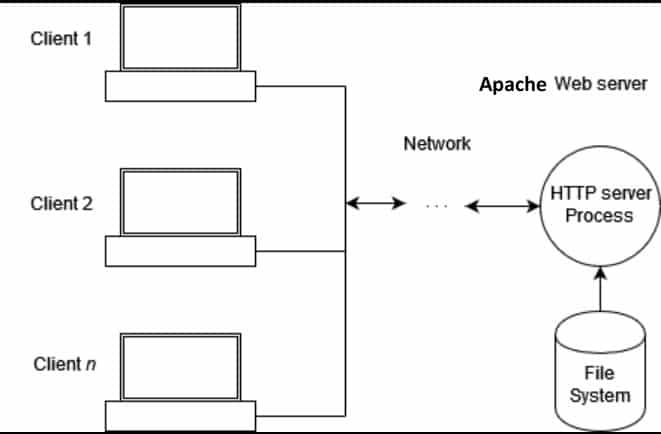
The web server is a crucial part of the world wide web and web-based applications. And the Apache web server is positioned as one of the most used web servers on the internet.
Many organizations and cloud-based applications depend on Apache web servers to get their services to users worldwide. Although the Apache webserver enables developers and organizations to publish their websites and web applications, despite those benefits, the Apache webserver can also expose your organization to unexpected security risks if not well managed.
By nature, Apache web servers are often placed at the edge of the network which makes it one of the most vulnerable services to be exploited and attacked. This is why Apache security is very important. Any vulnerability or misconfiguration in the Apache web server, or the underlying operating system, hosted applications, database, and the network will lead to exploitation and possible attack. This guide provides the necessary information and insight you need to harden and secure your Apache webserver.
Common Apache Web Server Attacks
Apache webserver can be attacked and compromised in many different ways, some of the most common examples include:
- Distributed Denial of Service (DDoS) Attack A DDoS attack on an Apache webserver attempts to overwhelm it by crowding it with several thousand HTTP requests at the same time, beyond its load limits. This causes an increase in CPU and memory usage. As a result, the system will slow and perhaps stop functioning completely.
- Buffer Overflow Attack A buffer overflow attack takes advantage of a condition created by a poorly written code or application in the web server in which the poorly written application while writing data to a buffer, overruns its capacity or the buffer’s boundary and then bursts into boundaries of other buffers, and corrupts or overwrites the legitimate data present. An example would be a Perl script program designed to request user input. Once the overflow condition has taken place the attacker can execute malicious code on the Apache server.
- Root Exploit This attack method enables a malicious actor to gain root access through the applications running as a root process on the Apache server. This allows the attacker to gain full control of the system.
- Website Defacement This allows an attacker to inject malicious code into a hosted application to gain access to resources or cause harm. Typical examples include SQL injection and cross-site scripting (XSS). Injection attacks are used to deface the website. The attacker may host malicious, unrelated, or embarrassing content on the Apache webserver or database; when the website is requested, it will display defaced web pages.
- Directory Traversal This is a vulnerability that enables an attacker to access beyond the Apache web root directory. This allows the attacker to execute OS commands and access sensitive information or restricted directories.
- Misconfiguration Attacks If default Apache configuration files are used, or unnecessary services are enabled, an attacker can compromise the Apache webserver through various attacks such as password cracking, injection attacks, and others.
Key Components of Good Apache Security
1. Access Control Access control measures protect the Apache server and resources from unauthorized access. The two main means of access control are authentication and authorization. For users or administrators to be able to access the server or a resource, they first must prove they are who they claim to be and have the necessary credentials, and rights or privileges to perform the actions being requested. Good Apache security requires strong access control measures including multi-factor authentication (MFA) to manage and control access to applications and resources.
2. Confidentiality and Integrity Confidentiality is the assurance that information is not disclosed to unauthorized individuals, programs, or processes. This means that control mechanisms need to be in place to dictate who can access Apache or data hosted on it and what the subject can do once they have access. These activities need to be controlled, audited, and monitored. Some security mechanisms that would provide confidentiality are physical and logical access controls, encryption, forcing all Apache connections over SSL/TLS, and database views, among others.
Similarly, integrity means that information is protected from unauthorized modification to ensure that it is reliable and accurate. If any type of illegitimate modification does occur, the security mechanism must alert the user or administrator in some manner. Some security mechanisms that would provide integrity are public key infrastructure (PKI) and digital certificates.
3. Availability Availability is the assurance that the Apache web server and its hosted resources must be up and running and available to users at all times. Most web apps are hosted in the cloud with integrations to several other cloud and on-premises services. Your Apache web server must be designed and installed in a way that ensures that it is always available to respond to web page and application requests and that it can complete the process without a hitch. This can be achieved through fault tolerance, recovery mechanisms, high availability, and scaling Apache server across multiple servers to make it more resilient to DDoS attacks and guarantee availability.
Apache Security Best Practices
1. Harden your OS and keep it updated Apache runs on Linux, Windows, OpenVMS, and a wide variety of Unix-like operating systems. The idea behind OS hardening is to minimize exposure to threats by patching, installing necessary services, turning off unnecessary protocols, using access control lists (ACLs) to permit and deny traffic, and implementing other security measures to secure the OS and reduce the attack surface. This will make it difficult for your Apache installation to be easily compromised. If you fail to secure the operating system but make Apache as secure as possible, attackers will be able to exploit operating system vulnerabilities to successfully attack your Apache server. It’s also recommended that Apache server operators follow the Apache Server Announcements mailing list to stay up to date with the latest news from the Apache development team
2. Regularly Assess Vulnerabilities Vulnerabilities are among the common security issues that plague software. To strengthen your defenses against threats, you’ll need to regularly update your Apache server against known vulnerabilities. For hosted applications, vulnerability assessment and security testing provide a way to identify vulnerabilities and take the necessary corrective action to fix the gaps.
The more extensive an organization’s security testing approaches are, the better its overall security posture. Standard security testing techniques can be utilized to test and detect application vulnerabilities. You also need to pay attention to the OWASP Top 10 as it offers a useful overview of common web application vulnerabilities.
3. Adopt the Principle of Least Privilege The principle of least privilege is the idea that a user, program, or process should have only the bare minimum privileges and information which are essential to perform its intended function. This means disabling services such as directory listing, Etag header, Server Side Include, server version and banner, ServerSignature directive, and ServerTokens that give away useful information to attackers.
Similarly, consider locking down Apache to run only with the permissions necessary to run, and nothing more than that. The permissions can be expanded as necessary but should also be revoked when they are no longer in use. Consider configuring Apache to run as an unprivileged system user instead of root. This is done by setting the APACHE_RUN_USER and APACHE_RUN_GROUP variables in the /etc/apache2/envvars file.
4. Implement Access Control Measures Access control enables you to manage who is authorized to access Apache and its resources. One of the key elements of access control is authentication and authorization. The following are some of the ways you can implement authentication and authorization in Apache:
- Restrict access by password—access to sensitive locations can be restricted by setting password-based credentials, using the .htaccess and .htpasswd utility.
- Restrict access by IP—sensitive areas of your web server such as admin control panels, and hosted sites and applications should have strict access controls placed on them. Apache makes it easy to whitelist IP access to certain locations of your website and deny traffic to all other IP addresses.
- Disable .htaccess files—.htaccess files allow Apache to have its configuration extended outside its main config file, and this could present a security risk. To prevent this, it is best practice to lock down the Apache configuration by disabling .htaccess files.
5. Prevent DDoS Attack: Slowloris attack is a popular form of denial of service attack in Apache. It forces the Apache server to wait on requests from malicious clients taking a long time to send traffic, thus causing legitimate web requests to timeout or be ignored completely. Several Apache modules such as mod_limitipconn, mod_qos, mod_evasive, mod_ security, mod_noloris, and mod_antiloris have been created to reduce the likelihood of a successful Slowloris attack. Since Apache 2.2.15, Apache ships the module mod_reqtimeout as the official solution supported by the developers. Other mitigating techniques involve setting up reverse proxies, firewalls, load balancers, or content switches.
6. Install a Web Application Firewall (WAF) A WAF monitors, filters, and blocks HTTP traffic to and from a web service. ModSecurity is an open-source WAF that is native to the Apache webserver and has now evolved to provide a wide range of security features including HTTP request and response filtering capabilities across different platforms. ModSecurity makes it easy to monitor, log, and filter HTTP communications based on user-defined rules.
It is also deployed to provide protections against generic classes of vulnerabilities using the OWASP ModSecurity Core Rule Set (CRS). A properly configured WAF can protect your site from SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). The ModSecurity application firewall also forms an integral part of PCI DSS compliance requirements. ModSecurity can be installed by running the following command in your terminal: sudo apt install libapache2-mod-security2 -y
7. Monitor and Log Relevant Data It is important to monitor and log the events and activities going on in your Apache server, to help you identify issues and ensure it is performing optimally. Apache has a module called mod_log_config for data logging and another called mod_status which you can enable to gain some level of visibility into what Apache is doing at any given time, including a summary of performance data such as current CPU usage and the total number of requests made since the Apache HTTPD Server was started.
Apache also comes with a program called Fail2Ban—a log-parsing application that monitors Apache system logs for malicious activities and takes action against malicious clients by banning their IPs. There are also lots of third-party Apache monitoring tools that provide deeper visibility on the performance of your Apache server including log files, operating system, server usage, network metrics, and data flows. Consider deploying those tools in your environment for efficient performance monitoring and data logging. Keep log history as long as it is reasonable. In the event of a breach or compromise, you will be able to pull up those logs and audit them for possible anomalies.




