You might be looking for data protection software and wonder what the sales websites mean when they talk about “data at rest” and “data in motion.” Other terms you could see include “data in transit” and “data traffic.” Data can be stolen, damaged, or deleted, and those events can occur when that data is either being moved or static.
Some system activities involve a combination of data in motion and data at rest. For example, the standard for email transmission always consists of storing the email on a mail server. Therefore, to protect data fully, you need to secure it both at rest and in motion.
Here is our list of the best security systems for data at rest and in motion:
- ManageEngine Endpoint DLP Plus EDITOR’S CHOICE Identify, categorize, control, protect, and log instances of sensitive data with this package. Threat alerts and activity logging are other important features. Runs on Windows Server. Start 30-day free trial.
- Endpoint Protector This data loss prevention system watches overall points on a system that can be used for data exfiltration. Available as a hosted service, as an app on cloud platforms, or for installation as a virtual appliance.
- Acunetix A vulnerability scanner for Web applications and networks. Available as a hosted SaaS platform or for installation on Windows, macOS, or Linux.
Protecting data at rest
There are several levels of protection that you can implement for data at rest. However, you will probably end up with at least two layers of security to protect the data stored on your system. The four types of protection that you need to consider for data at rest are:
- Endpoint protection
- Data loss prevention
- File integrity monitoring
- Cloud account security
You can read more about these security services in the following sections.
Endpoint protection
An endpoint protection system is usually called endpoint protection and response (EDR) because these security packages include mechanisms to shut down attacks on endpoints. There are two threats to your endpoints – malware, an automated method to steal or damage data, and intrusion, a manual attempt.
The core of an EDR is what used to be known as an anti-malware service. However, as manual threats also need to be spotted and blocked, anti-malware required systems to expand their capabilities; this is how EDR systems came about.
Data loss prevention
There is an overlap in the purpose of EDR and data loss prevention (DLP) systems by the methodologies of the two systems are different. DLP services watch all exits and block unauthorized data transfers. This could be in the form of files attached to emails or chat messages, the copying of files onto a memory stick, transfers over network applications, such as FTP, and, However, as the printing of documents.
DLP is necessary because it also blocks insider threats. Authorized users can disclose or damage data either accidentally or intentionally. The user could be a whistleblower or disgruntled. Tricksters might impersonate colleagues and fool a user into sending data.
Another type of insider threat is the disclosure of credentials because of phishing attacks. The result of a successful phishing attempt is called account takeover (ATOI). It is possible to buy security packages that address this tactic. ATO detection can also be integrated into EDR and DLP packages.
File integrity monitoring
There are two types of file integrity monitoring (FIM) services. The first of these protect critical system files from tampering. For example, log files must be stored and preserved in their original state if a business follows a data protection standard, such as PCI DSS, HIPAA, or GDPR. This is because external auditors will check these files for signs of data disclosure or misuse of personally identifiable information (PII).
Log files are also important sources of security information, and Security Information and Event Management (SIEM) systems mine logs for signs of intrusion or other malicious activity. Thus, log files should be protected from tampering because intruders know that they need to delete records from log files to keep them hidden.
FIM is also used to protect PII from inappropriate use. So, FIM involves finely tuning user groups and ensuring that only those accounts needing access to PII can get at those data stores. FIM for PII requires the security system to know where PII is held and how sensitive that data is. Thus, FIM systems are usually paired with sensitive data eDiscovery services. These categorize data by its degree of sensitivity. Therefore, the FIM system needs to be set up with security policies to direct different levels of security monitoring for specific categories of sensitivity.
Cloud account security
If your business uses cloud-based tools delivered on the Software-as-a-Service model, the package probably also includes storage space for data, such as log files. You might also have an account with a data storage service, such as OneDrive or Google Drive. Another commonly accessed cloud service is Web hosting.
In all of these services, your account is held on the same server as many other accounts. Therefore, you need to be sure that other account holders can’t break into your disk space, and you also don’t want the provider’s technicians to access your data.
Cloud providers ensure account privacy by fully encrypting the disk space allocated to each subscriber. This encryption is usually implemented with the Advanced Encryption Standard (AES) cipher with a 256-bit key. AES provides powerful, uncrackable encryption. Within that cloud account, you will need to set up user accounts.
Most cloud storage and productivity suites, such as Microsoft 365, allow account administrators to set up individual user accounts. The management of these accounts is as essential on cloud services as it is on your network. In addition, they enable the activity tracing services built into cloud systems to provide helpful information.
Data in Motion
Protecting data in motion is a much simpler task than safeguarding data at rest. This is because data security for internet connections has been a big issue for a long time. There are very competent protocols in existence to block hacker attempts on data in transit. Capturing data as it crosses the internet requires excellent technical skills that many hackers just don’t have. The newer scam of tricking credentials out of users is a lot easier to perform.
When protecting data in motion, you need to look at the following services:
- Web transactions
- File transfers
- Team collaboration
As communication is the connective tissue between applications, the issues involved in securing data in transit are closely tied to data management at rest. The task of tracking activity with logs and tightly defining access rights spread across all resources in your system. So, when you have organized your system to secure data at rest properly, you have already performed most of the tasks needed to secure it in motion.
Protecting Web transactions
You no doubt activate and manage HTTPS for all of your Web connections. With that security service in place, you have pretty much covered your Web transaction security. In addition, periodic Web application vulnerability scanning will ensure that hackers do not have inroads into your core systems through your public-facing Web presence.
Web application firewalls can also give constant protection for your Web-based assets.
File transfers
The File Transfer Protocol (FTP) is one of the oldest systems used on the Internet, and it has worked well in all respects other than security. However, you should ensure that all of your data movement systems use SFTP or FTPS instead of FTP. Although you would choose to launch a secure file transfer system to move files, you don’t know what all of your applications are using.
System documentation and vulnerability scanning will give you insights into where file transfer activity is not adequately protected.
Team collaboration
Team collaboration systems require information to be shared. This results in the same data being both at rest and in motion. So, for example, if a group of people have access to the same document that is held on Google Drive and access it through Google Docs, that document is at rest on the Google server, its content is also frequently transferred back and forth between the Google Server and the browsers of the people who are updating it.
Fortunately, the security of those transfers is implemented by HTTPS, and the at-rest security is covered by the account encryption provided as standard by Google. Unfortunately, these security measures don’t block unauthorized disclosure by authorized users. So, your DLP solution will need to have the capability to monitor cloud resources as well as your network’s endpoints.
The best tools to protect Data at Rest and Data in Motion
You need a range of security services to protect data at rest and in motion entirely. Fortunately, some packages cover several of the functions that you should put in place for complete data security.
Our methodology for selecting a security tool for data at rest and in motion
We reviewed the market for data security systems analyzed tools based on the following criteria:
- A service that can cover several data protection requirements in one package
- Options for on-premises installation plus SaaS solutions
- A system that is compliant with data privacy standards
- A guided service that will automatically cover all data security issues that the system administrator might otherwise overlook or be unaware of
- Adaptable methods that can be adjusted by templates or manually.
- A free tool or a paid service that offers a free trial or demo for assessment
- Value for money, represented by a complete set of functions that provide proper security without costing too much
With these selection criteria in mind, we produced various options to suit businesses of all sizes.
You can read more about each of these tools in the following sections:
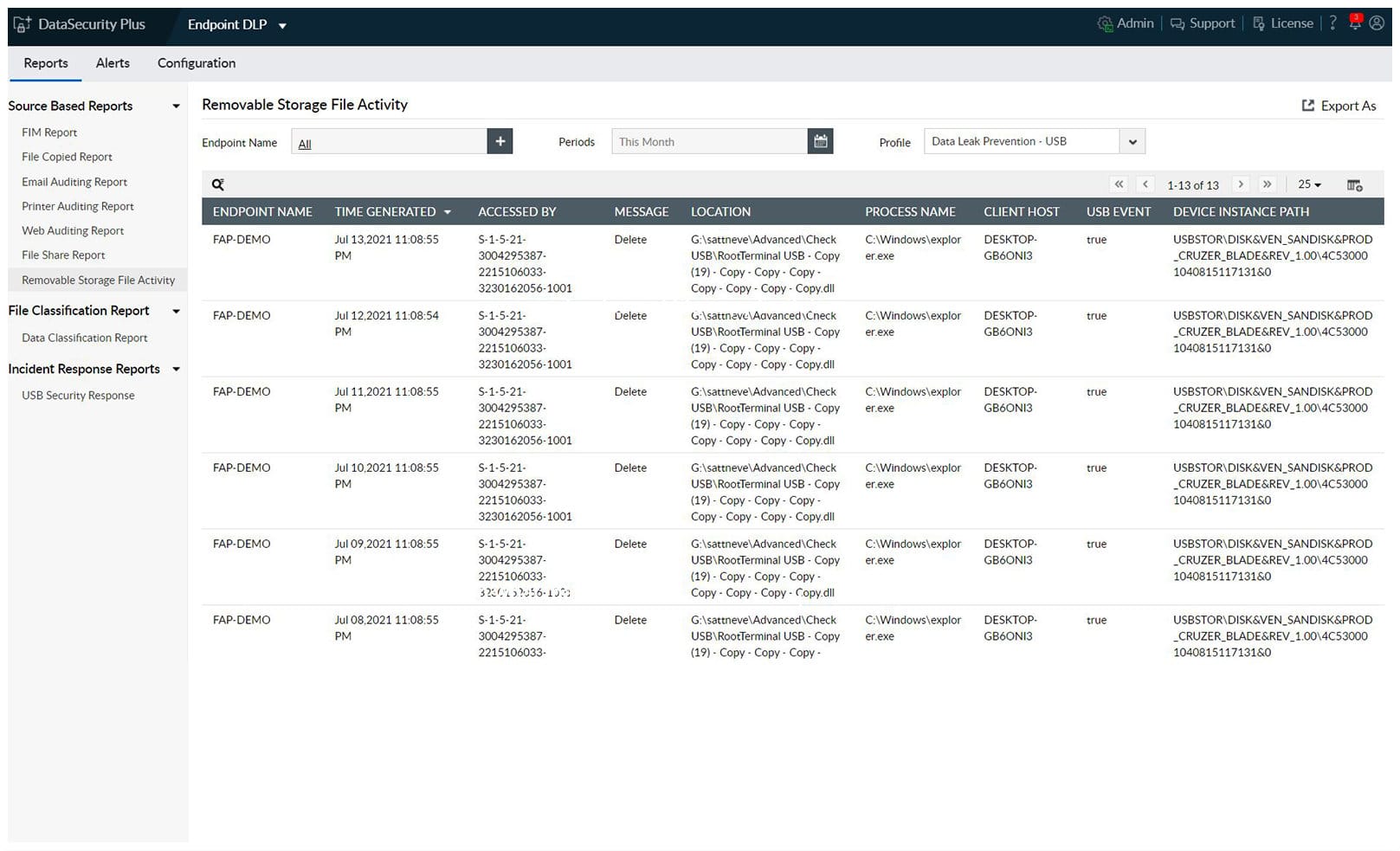
1. ManageEngine Endpoint DLP Plus (FREE TRIAL)
ManageEngine Endpoint DLP Plus is a data protection system that implements data loss prevention. Tools in this bundle of services include sensitive data discovery and classification. Identified stores of sensitive data are then protected with containerization, which only allows those files to be accessed by authorized applications, which in turn will have tight user authentication.
Key Features:
- File integrity monitoring
- Peripheral device controls
- Data loss prevention
- Insider threat protection
- Cloud protection
Why do we recommend it?
ManageEngine Endpoint DLP Plus is concerned with protecting data at rest and it has some protection for data in motion – namely cloud upload controls. Rather than just protecting data, this system manages access to data, either directly or through applications. It controls who gets access to which data and how.
As well as providing protection for data at rest Endpoint DLP Plus implements file movement lockdown. USB devices, email systems, and file transfer systems are monitored and blocked if a user tries to move a classified file through one of these channels. All of the activity related to marked stores of sensitive data are logged, which provides an audit trail for compliance reporting.
Who is it recommended for?
ManageEngine offers a Free edition of this package. It has all of the functions of the paid edition, which is called Professional, but it is limited to monitoring data on 25 endpoints. This is a great option for small businesses. Larger organizations would opt for the Professional package, which can be expanded to cover WANs.
Pros:
- Sensitive data discovery and classification
- Data exfiltration controls
- Activity logging for compliance auditing
- Email security
- Data containerization
Cons:
- Not a SaaS package
ManageEngine Endpoint DLP Plus is a software package for Windows Server. The package is available in a Free edition, which is limited to monitoring files on 25 devices. You can get the Professional Edition on a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Endpoint DLP Plus is our top pick for a data security service because it delivers comprehensive, easy-to-use tools to protect sensitive information across endpoints without disrupting workflows. Its focus on data loss prevention (DLP) ensures businesses can safeguard confidential data from unauthorized access, sharing, or accidental leaks. One of its standout features is granular control over sensitive data. ManageEngine Endpoint DLP Plus allows organizations to classify and monitor data, applying policies tailored to different levels of sensitivity. This ensures compliance with regulations like GDPR, HIPAA, and PCI DSS, providing peace of mind for businesses handling critical information. The platform excels in monitoring and controlling endpoint activities. It can track how employees interact with data, whether copying files, using external drives, or sharing through email. The service will immediately block unauthorized actions. This functionality is especially crucial in preventing insider threats and mitigating the risks of unintentional data exposure. ManageEngine Endpoint DLP Plus also supports extensive reporting and alerting, offering real-time insights into data usage patterns. These reports not only enhance visibility but also help organizations identify and address vulnerabilities proactively. Another advantage is its user-friendly interface and seamless deployment, which make it accessible for businesses of all sizes. Its ability to scale ensures that even as your company grows, the tool remains an effective solution for protecting sensitive data.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/endpoint-dlp/download.html
OS: Windows Server
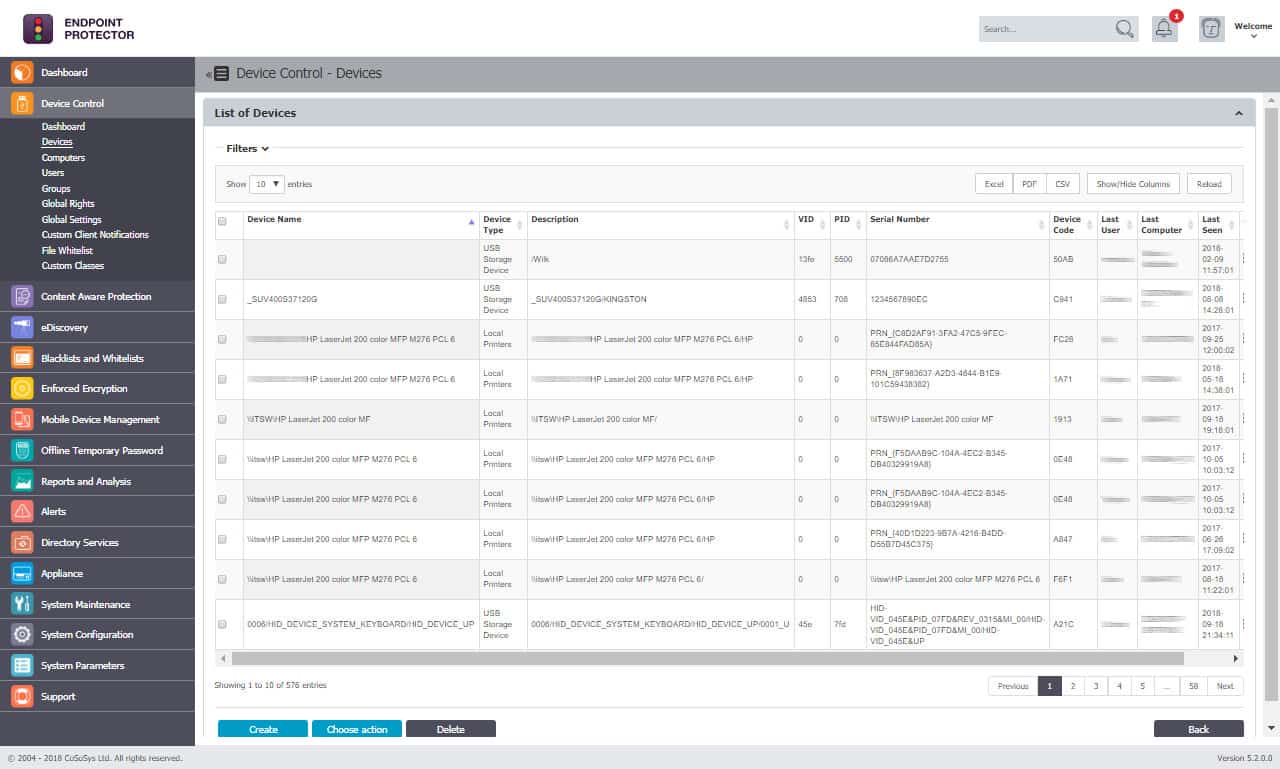
2. Endpoint Protector
Endpoint Protector is a data loss prevention system that operates on endpoints. It implements activity tracking on the device, which includes application usage. It also offers a sensitive data discovery and classification service.
Key Features:
- Cloud-based
- Protection for Windows, macOS, and Linux
- Blocks printing and copying
Why do we recommend it?
Endpoint Protector is an “allowlisting” system. All access to data is blocked by default and then the administrator sets up a list of applications that are allowed to access specific data stores and users that are allowed to use those applications. This is also a great way to block malware.
With a main module managing monitoring activities, endpoint agents for Windows, macOS, and Linux gather data and implement controls and responses.
Controls include USB activity management that can block all data from being copied onto memory sticks or just ban the movement of classified data. Similarly, the service monitors data movement attempts on cloud services and email systems, such as Outlook, Skype, and OneDrive. The printing of sensitive data can also be controlled. Access rights management tools work with security policies to control access to different levels of sensitive data held in files.
Endpoint Protector is a SaaS system, and it is also available on the relevant marketplaces of AWS, GCP, and Azure. It can also be installed as a virtual appliance.
Who is it recommended for?
This package is a good choice for any business because its mechanisms are very easy to understand and implement. You just need to learn how to use the console to set up an allow list and then you have full data protection. The system also provides a control for peripheral storage devices.
Pros:
- Provides a thorough strategy for the monitoring of sensitive data
- Quickly detects threats on an endpoint and communications that activity to other device agents
- Implements rapid responses to malware and intruder threats
- Controls all possible channels for data movement
- Improves access rights management
Cons:
- An integrated SIEM would have been nice to have
Endpoint Protector covers all of the services that data thieves can use to get data out of a network. So whether the con artists manipulate innocent users into sending data out or breaking into the system and stealing it themselves, Endpoint Protector will block them. You can get access to the demo.
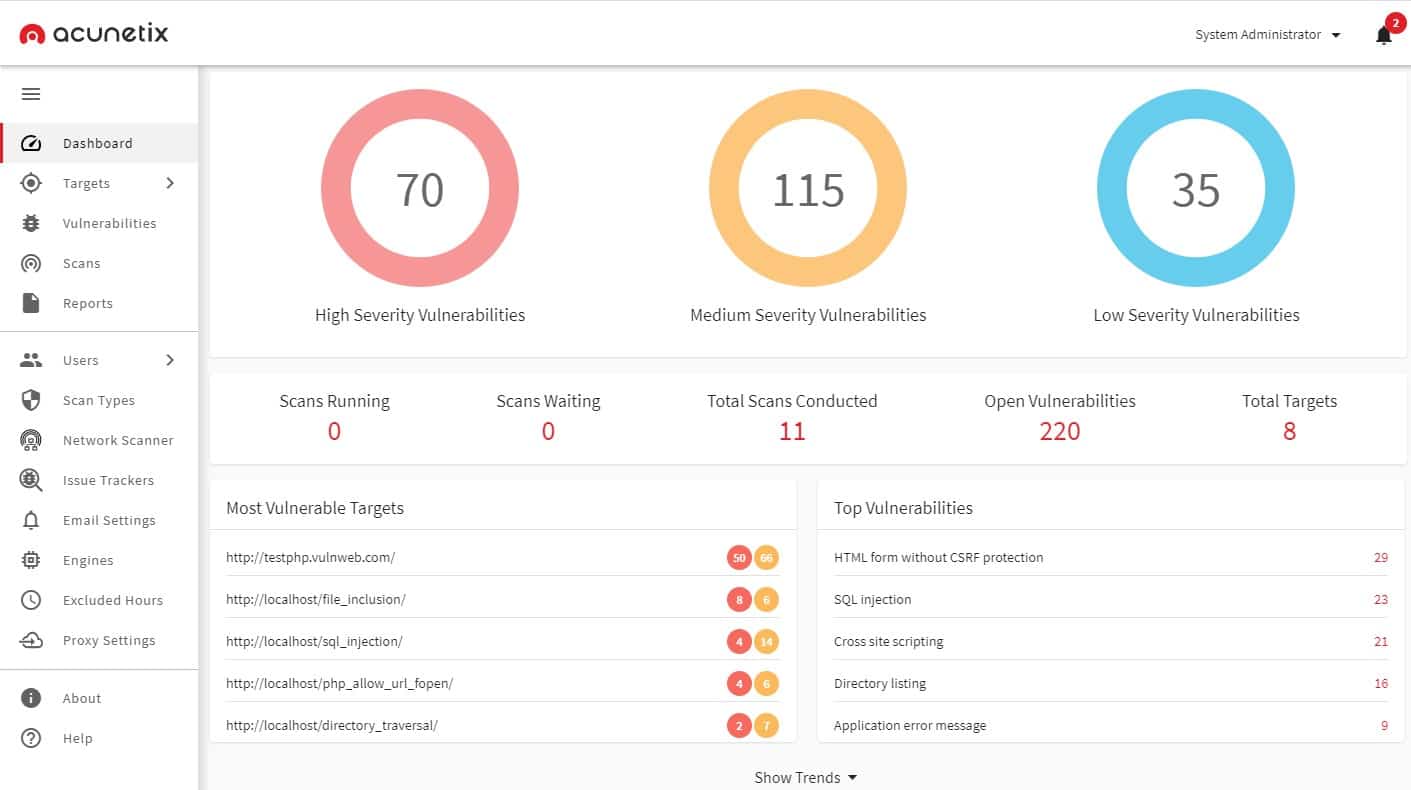
3. Acunetix
Acunetix is a Web application vulnerability scanner that seeks out 7,000 weaknesses, including the OWASP Top 10. There is also a network vulnerability scanner option for Acunetix, which can identify more than 50,000 potential exploits.
Key Features:
- Web application security testing
- Good for DevOps
- CI/CD pipeline integration
Why do we recommend it?
Acunetix is a vulnerability scanner that can also be applied as a development pipeline as a continuous tester. This tool ensures that hackers and data thieves can’t get into your system and steal data through weaknesses in mobile apps, websites, or Web applications.
Acunetix implements Dynamic Application Security Testing (DAST), Static Application Security Testing (SAST) and also includes an Interactive Application Security Tester (IAST), called AcuSensor. This is an excellent tool for protecting Web applications and thus, blocking ingress by intruders that would like to get hold of your sensitive data.
Who is it recommended for?
This system is aimed at DevOps teams. So, it is particularly useful for ensuring security in Web applications as they are developed and when they are released for public use. The service can also be used as a vulnerability scanner for on-demand or scheduled scans.
Pros:
- DAST, SAST, and IAST scanning
- Web application and vulnerability management
- Offers scans on-demand or continuously
Cons:
- No sensitive data monitor
This tool is suitable for businesses that need to prove compliance with PCI DSS, HIPAA, and ISO 27001. Acunetix is offered as a hosted SaaS platform, and you can also download the software for installation on Windows, macOS, and Linux. Assess Acunetix by accessing the demo system.
Data at Rest vs Data in Motion FAQs
What is data in motion and data at rest?
When data is stored, it is considered to be “at rest.” This specifically refers to when you save a file and close it. If you continue to access the data, it is not at rest, it is “in use.” When data is transferred from one device to another, it is “in motion.” Usually, data is only considered to be in motion when it moves across a network. This definition excludes the movement of a file from one directory to another. However, it does include copying a file onto a USB stick.
What are the 3 states of data?
The three states that data can be in are at rest, in motion, and in use. When you are working on a file, it is in use. Even if you save it, it is still considered to be in use if you do not close the file but continue to access it. The concept of data in motion refers to transferring the data to a different device across a network. This also includes moving data to a USB stick or sending it to a printer. Data at rest refers to storing data. If a file in a directory is not in use, it is at rest.
What do you mean by data in motion?
Data in motion refers to the transfer of data from one device to another. This is mainly concerned with transferring data over a network or the internet. Sending a file to be printed also defines it as data in motion and copying it onto a USB stick also counts as being in motion.