Businesses need tools to monitor, detect, and respond to security threats in real-time. Security Information and Event Management (SIEM) tools are critical for centralizing and analyzing security data across an entire network, enabling businesses to proactively manage and mitigate risks. IT professionals, security analysts, and network administrators are the primary users of SIEM solutions, often relying on them to streamline security operations and reduce the manual workload of managing vast amounts of event data.
For security teams, SIEM tools provide invaluable insight into potential threats, security breaches, and system vulnerabilities, empowering them to act quickly before a breach occurs. IT administrators and compliance officers also rely on SIEM systems to ensure regulatory compliance by maintaining detailed logs and automating reporting. However, buying or implementing SIEM software is not without its challenges.
A primary pain point is the complexity of managing and configuring these systems, often requiring highly specialized skills to interpret data and fine-tune alerts. Additionally, the volume of false positives generated by some SIEM solutions can overwhelm security teams, leading to alert fatigue and slower response times. Finally, integration with existing infrastructure can be cumbersome, making it critical to choose a SIEM platform that is flexible, scalable, and easy to deploy.
SIEM tools can address the following issues in your organization
- Lack of real-time threat monitoring can delay response and mitigation.
- Manual log analysis can be inaccurate and may not provide the insights you need for troubleshooting.
- Difficult to detect insider threats and unauthorized access.
- Lack of a unified dashboard can make it difficult to track events, user activity, and other network anomalies.
- Limited workflow integration with other tools, limiting the ability to quickly track and resolve security vulnerabilities.
This guide will explore top SIEM tools that address these challenges, helping organizations streamline security management and enhance their cybersecurity posture.
According to the martech company 6sense, there are over 24,000 companies in the SIEM space. You probably don’t have the time to sift through that many providers, and in most cases, the top providers are “top providers” for a reason. Their tools work well, they have the size and staff to support your implementation, and they’re more likely to have a clear product roadmap.
With that said, here is our SIEM tools list featuring the best software for small, medium, and enterprise-level businesses:
- ManageEngine Log360 EDITOR’S CHOICE This on-premises package includes a log server and a SIEM tool to provide automated security scanning, activity analytical tools, and compliance auditing facilities. The package also includes a threat intelligence feed. The software runs on Windows Server. Start a 30-day free trial.
- Graylog (FREE PLAN) This log management package includes a SIEM service extension that is available in free and paid versions and has a cloud option.
- ManageEngine EventLog Analyzer (FREE TRIAL) A Log Management Tool that manages, protects, and mines log files. This system installs on Windows, Windows Server, and Linux.
- Trellix Helix This cloud-based system provides advanced persistent threat protection and uses SOAR to activate your existing security products for threat responses.
- Heimdal Threat Hunting and Action Center This platform adds threat detection and response functions to on-premises AVs from its cloud base.
- Datadog Security Monitoring A cloud-native network monitoring and management system that includes real-time security monitoring and log management. Comes with over 600 vendor integrations out-of-the-box.
- Microsoft Sentinel A cloud-native SIEM solution offering real-time threat detection, intelligent security analytics, and automated response capabilities.
- Elastic Security This package applies SIEM rules to the Elastic Stack group of products and provides live threat detection plus historical analysis. Available as a SaaS package or for installation on Windows, macOS, or Linux.
- Logpoint SIEM Using UEBA for baselining, this package implements AI-drive anomaly detection for threat hunting and can instruct third-party tools in response playbooks through an integrated SOAR module.
- SolarWinds Security Event Manager One of the most competitive SIEM tools on the market with a wide range of log management features.
- Fortinet FortiSIEM This security package from a highly respected provider can be combined with other Fortinet products and is offered as a hardware appliance, a virtual appliance, or as a service on AWS.
- Splunk Enterprise Security This tool for Windows and Linux is a world leader because it combines network analysis with log management together with an excellent analysis tool.
- Rapid7 InsightIDR This combined XDR and SIEM operates threat hunting in the cloud based on data collected by site agents.
- Exabeam LogRhythm SIEM Cutting-edge AI-based technology underpins this traffic and log analysis tool for Windows and Linux.
- LevelBlue (formerly AT&T Cybersecurity) Great value SIEM that runs on Mac OS as well as Windows.
- Security Onion This package is a compendium of open source, free intrusion detection systems. Runs on Linux or cloud accounts.
If you need to know more, explore our vendor highlight section just below, or skip to our detailed vendor reviews.
Best SIEM Tools for Automated Security Alerts highlights
Top Feature
All-in-one SIEM with log consolidation
Price
Free: $0/yr, Basic: $300/yr, Standard: $995/yr, Professional: $1,995/yr, MSSP: $1,995/yr
Target Market
Medium to enterprise-level businesses
Free Trial Length
Free trial (30 days)
Additional Benefits:
- Consolidates logs from on-prem and cloud systems
- Provides real-time threat detection and alerts
- Automates compliance reporting (HIPAA, GDPR, PCI-DSS, etc.)
- Supports integration with service desk tools
- Enhances threat detection with live threat intelligence feed
Features:
- Log collection and consolidation from 700+ sources
- Windows Event and Syslog integration
- File integrity monitoring and Active Directory controls
- Built-in compliance templates for major standards
- EventLog Analyzer and SOAR capabilities
Top Feature
Customizable open-source log management
Price
Graylog Open: Free, Graylog Enterprise: $1,250/mo, Graylog Security: $1,550/mo, Graylog API Security: $1,550/mo
Target Market
Security teams and IT admins across all business sizes
Free Trial Length
Free version
Read more ▼
Top Feature
Real-time log analysis with compliance reporting
Price
Free: $0, Premium: $595/yr, Distributed: $2,495/yr
Target Market
IT admins and compliance teams in SMBs
Free Trial Length
Free trial (30 days)
Read more ▼
Top Feature
Advanced threat detection with automation
Price
Negotiated pricing: contact the vendor for details
Target Market
Enterprise security teams and SOCs
Free Trial Length
None
Read more ▼
Top Feature
Centralized threat detection with automated response
Price
Negotiated pricing: contact the vendor for details
Target Market
Security teams in medium to enterprise-level businesses
Free Trial Length
None
Read more ▼
Top Feature
Datadog Security Monitoring
Price
Cloud SIEM: $5 per million events/month
Target Market
Cloud-native businesses and DevOps teams
Free Trial Length
Free trial (14 days)
Read more ▼
Top Feature
Cloud-native SIEM with SOAR automation
Price
Pay-as-you-go: $5.22/GB, Reserved plans start at $342.52/day for 100 GB/day
Target Market
Enterprise security teams and hybrid cloud environments
Free Trial Length
None
Read more ▼
Top Feature
Real-time threat detection with scalable analytics
Price
Standard: $95/mo, Gold: $109/mo, Platinum: $125/mo, Enterprise: $175/mo
Target Market
Security teams and IT admins in medium to enterprise-level businesses
Free Trial Length
Free trial (14 days)
Read more ▼
Top Feature
Unified SIEM with UEBA and SOAR
Price
Negotiated pricing: contact the vendor for details
Target Market
Security teams and IT administrators in medium to enterprise-level businesses
Free Trial Length
None
Read more ▼
Top Feature
User-friendly SIEM with real-time event correlation
Price
Starts at $3,292
Target Market
IT professionals and security teams in small to medium-sized businesses
Free Trial Length
Free trial (30 days)
Read more ▼
Top Feature
Integrated SIEM with UEBA and automated response
Price
Negotiated pricing: contact the vendor for details
Target Market
Medium to large enterprises and MSSPs with complex security needs
Free Trial Length
None
Read more ▼
Top Feature
Advanced real-time threat detection and analytics
Price
Negotiated pricing: contact the vendor for details
Target Market
Security operations teams and large enterprises
Free Trial Length
Free trial (15 days)
Read more ▼
Top Feature
Cloud-native SIEM with UEBA and automated response
Price
Essential: $3.82/asset/month, Advanced: $6.36/asset/month, Ultimate: $8.21/asset/month
Target Market
Security teams in medium to enterprise-level organizations
Free Trial Length
Free trial (30 days)
Read more ▼
Top Feature
AI-powered analytics with SOAR integration
Price
Negotiated pricing: contact the vendor for details
Target Market
Security teams and IT professionals in medium to enterprise-level organizations
Free Trial Length
None
Read more ▼
Top Feature
Unified SIEM and XDR with integrated vulnerability scanning
Price
Negotiated pricing: contact the vendor for details
Target Market
Small to medium-sized businesses and MSPs seeking managed security solutions
Free Trial Length
None
Read more ▼
Top Feature
Open-source IDS combining Suricata, Zeek, and Elastic Stack
Price
Free
Target Market
Security professionals and SOC teams seeking an open-source, scalable threat detection platform
Free Trial Length
Free and open-source
Read more ▼
SIEM Features Comparison Chart
Product/Features | ManageEngine Log360 | Graylog | ManageEngine EventLog Analyzer | Trellix Helix | Heimdal Threat Hunting and Action Center | Datadog Security | Microsoft Sentinel | Elastic Security | Logpoint | SolarWinds | Fortinet | Splunk |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Log File Management, Messages, & Historical Analysis | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Live Monitoring | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Alerts | Email, SMS | Email, text, Slack, and more | Email, SMS | Customized alert management | Threat Telemetry Visualization and XTP/MITRE ATT&CK Visualization | Email, Slack and PagerDuty | Email, Logic Apps, Webhooks, ITSM (e.g., ServiceNow), and Automation Rules Alerts | Email, Slack | Email, SSH, SNMP, HTTP, or Syslog | Email, SMS | Configurable email alerts | |
| Compliance Reporting | PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA. | HIPAA, PCI, FERPA, COPPA, GDPR, & More | PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001 | HIPAA, PCI | HIPAA, PHI, GDPR | HIPAA, PCI DSS, SOC 2 Type II, ISO 27001, ISO 27017, ISO 27018, CSA, STAR, FedRAMP, GDPR, CCPA | HIPAA, PCI DSS, GDPR, SOC 2, ISO 27001, and more | HIPAA, PCI DSS, SOC 2 Type II, ISO 27001, ISO 27017, ISO 27018, ISAE 3000, SOC 2, SOC 3, CyberGRX, TISAX, FedRAMP, CSA STAR | Schrems II, HIPAA, GDPR, PCI-DSS and SOX | HIPAA, PCI DSS, SOX, ISO, DISA STIGs, FISMA, FERPA, NERC CIP, GLBA, and more | PCI-DSS, HIPAA, GLBA, and SOX | Product offerings differ: ISO 27001 Certification, SOC 2 Type II Report, HIPAA, PCI DSS, FedRAMP, FIPS 140-2 |
| Operating System: | Windows Server | Linux or Cloud | Windows, Windows Server, and Linux. | Windows Server, Mac OS X, several Linux distributions | Windows, macOS | Cloud-based | Cloud-based | Windows, macOS, Linux, and cloud | Linux or Cloud | Windows | Hardware, VMware, Hyper-V, KVM, OpenStack, and AWS | Windows and Linux |
Free Trial or Demo | 30-days | 2GB Free Plan | 30-days | Free Trial | Free Demo | 14-days | Available | 14-days | Demo | Free Trial | Demo | 15-days |
Bonus: SIEM Software Guide
Key points to consider before selecting SIEM tools for automated security alerts
When selecting a SIEM tool for automated security alerts, it’s crucial to carefully evaluate several factors to ensure the tool aligns with your organization’s needs and security goals. Below are the key points to consider:
1. Integration Capabilities
Ensure the SIEM tool can integrate seamlessly with your existing network infrastructure, applications, and other security tools. The ability to collect and analyze data from a variety of sources will ensure comprehensive monitoring and threat detection. Common data sources include firewalls, endpoint devices, and cloud services.
2. Customization and Flexibility
Look for a solution that allows customization of alert thresholds, data collection processes, and reporting formats. A flexible SIEM tool can adapt to your specific security requirements and the unique needs of your organization, whether you need to adjust detection rules or create custom dashboards.
3. Scalability
As your organization grows, so too will the volume of security data. Choose a SIEM tool that can scale with your organization’s evolving needs, handling an increasing number of data sources and users without performance degradation.
4. Ease of Deployment and Use
Consider how easy it is to deploy, configure, and use the tool. A user-friendly interface and intuitive workflows can significantly reduce the learning curve and improve operational efficiency for security teams.
5. False Positives Management
SIEM tools are often prone to generating false positives. Look for tools with advanced analytics and machine learning capabilities to minimize alert fatigue by accurately distinguishing between genuine threats and benign events.
6. Regulatory Compliance Support
If your organization is subject to regulatory frameworks (e.g., GDPR, HIPAA), ensure the SIEM tool offers features to facilitate compliance, such as built-in reporting templates and secure log management.
7. Cost and Licensing
Assess the pricing structure of the SIEM tool, including upfront costs, subscription fees, and any additional costs for support, training, or advanced features. Choose a solution that provides a balance between functionality and budget constraints.
8. Vendor Support and Community
Evaluate the level of customer support and resources available from the vendor. Look for a vendor that offers 24/7 support, detailed documentation, and a strong user community to assist with troubleshooting and best practices.
How to calculate ROI for SIEM tools
Calculating the Return on Investment (ROI) for a SIEM tool involves assessing both the direct and indirect benefits of implementing the tool against its total cost. Here’s a step-by-step process to help you calculate the ROI:
Determine the Total Costs of the SIEM Tool
Include all costs associated with the SIEM tool:
- Initial Investment: The upfront costs of purchasing the software and hardware (if necessary).
- Ongoing Costs: Subscription fees, maintenance costs, support, and any additional licenses or services.
- Deployment Costs: The costs for installing, configuring, and integrating the tool, including labor costs (e.g., IT staff, consultants).
- Training Costs: Any costs associated with training staff to use the SIEM effectively.
Identify Quantifiable Benefits
Quantifiable benefits are the direct, measurable outcomes that result from the SIEM tool’s implementation. Some examples include:
- Reduced Data Breaches: Calculate the potential cost savings from preventing data breaches, which can involve fines, legal fees, and reputation damage. Use industry average costs for data breaches to estimate savings.
- Reduced Incident Response Time: Faster detection and response to security incidents can lower the impact of a breach. Measure how much time is saved by automating alerts and improving detection.
- Reduced False Positives: Decreasing the number of false alerts reduces the time and resources needed to investigate each event. Calculate the cost savings in terms of labor hours saved by more accurate alerts.
- Improved Compliance: If the SIEM tool helps meet regulatory compliance requirements, it may reduce the risk of non-compliance penalties, auditing costs, and legal fees.
Estimate Indirect Benefits
Although harder to quantify, indirect benefits can also contribute to ROI:
- Improved Security Posture: A stronger security stance can reduce the likelihood of attacks and improve organizational resilience, though the financial value may not always be easy to measure.
- Increased Productivity: With automated security event management, your IT and security teams can focus on more strategic tasks, leading to improved overall productivity.
- Enhanced Reputation: A company known for having robust cybersecurity is more likely to attract and retain clients. The value of enhanced reputation can be linked to improved customer retention or new business opportunities.
Calculate the ROI
The basic formula to calculate ROI is:
Where:
- Net Benefits = Total quantifiable benefits – Total costs
- Total Costs = All costs associated with the SIEM tool (as mentioned earlier)
Example:
Let’s say the total cost of the SIEM tool (including initial investment, ongoing costs, and deployment) is $100,000, and the quantifiable benefits (reduced data breaches, reduced incident response time, etc.) amount to $300,000.
This means that for every dollar spent on the SIEM tool, the company gains $2 in value.
Consider Payback Period
Another helpful metric is the Payback Period, which measures how long it will take for the SIEM tool to pay for itself based on the cost savings or benefits achieved:
For example, if the total costs of the SIEM are $100,000 and the annual net benefits (savings or reduced costs) are $50,000, the payback period would be:
By calculating ROI and considering the payback period, you can better assess the financial effectiveness of your SIEM investment.
The Essential Features of SIEM Tools
Not all SIEM systems are built the same. As a result, there is no one-size-fits-all. A SIEM solution that’s right for one company may be incomplete for another. In this section, we break down the core features needed for a SIEM system.
- Log Data Management As mentioned above, log data management is a core component of any enterprise-scale SIEM system. A SIEM system needs to pool log info from a variety of different data sources, each with its own way of categorizing and recording data. When looking for an SIEM system, you want one that has the ability to normalize data effectively (you might need a third-party program if your SIEM system isn’t managing disparate log data well).
Once the data is normalized, it is then quantified and compared against previously recorded data. The SIEM system can then recognize patterns of malicious behavior and raise notifications to alert the user to take action. This data can then be searched by an analyst who can define new criteria for future alerts. This helps to develop the system’s defenses against new threats.
- Compliance Reporting In terms of convenience and regulatory requirements, having an SIEM with extensive compliance reporting features is very important. In general, most SIEM systems have some kind of onboard report generating system that will help you to conform to your compliance requirements.
The source of requirements of the standards that you need to conform to will be a major influence on which SIEM system you install. If your security standards are dictated by customer contracts, you don’t have much leeway on which SIEM system you choose — if it doesn’t support the required standard, then it won’t be any you’re used to. You may be required to demonstrate compliance with PCI DSS, FISMA, FERPA, HIPAA, SOX, ISO, NCUA, GLBA, NERC CIP, GPG13, DISA STIG, or one of many other industry standards.
The Best SIEM Tools
1. ManageEngine Log360 (FREE TRIAL)
Tested on: Windows Server environment
Best for Medium to Enterprise-Level Businesses: ManageEngine Log360 offers comprehensive log management and threat detection capabilities, making it suitable for organizations with complex IT infrastructures that require robust security monitoring.
Price: Free plan = $0 per year; Basic plan = $300 per year; Standard plan = $995; Professional plan = $1,995 per year; MSSP plan = $1,995.

ManageEngine Log360 is an on-premises package that includes agents for different operating systems and cloud platforms. The agents collect log messages and send them to the central server unit. Agents integrate with more than 700 applications so they can extract information from them. They also process Windows Event and Syslog messages.
The log server consolidates log messages and displays them in a data viewer in the dashboard as they arrive. The tool also presents metadata about log messages, such as the arrival rate.
Log360’s key features
Log360 is a very large package that integrates several ManageEngine products. Its important features are:
- Log Collection: Gathers logs from both on-site and cloud systems.
- Log Consolidation and Filing: Organizes and consolidates logs for efficient storage and retrieval.
- Log Analysis Tools: Provides tools for in-depth analysis of logs, helping in identifying patterns and anomalies.
- File Integrity Monitoring: Monitors and ensures the integrity of files, detecting unauthorized changes.
- Compliance Reporting: Enables businesses to automate the generation of reports for regulatory standards like GDPR, HIPAA, PCI-DSS, and others.
Unique buying proposition
ManageEngine Log360 offers a comprehensive, user-friendly SIEM solution with real-time log monitoring, advanced threat detection, and automated compliance reporting, all in one platform. Its unique selling points lie in its integration with existing IT infrastructure, customizable alerting system, and support for a wide range of compliance standards.
Feature-in-focus: ManageEngine Log30’s EventLog Analyzer
This tool is a log management and security information event management (SIEM) tool that helps organizations monitor and analyze log data from across their network. It offers real-time log collection, threat detection, and compliance reporting, making it ideal for detecting security incidents and meeting regulatory requirements.
Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, ManageEngine received a 93/100 SupportScore. This means that ManageEngine is likely to provide a significant amount of customer and product support in a manner that works for most companies. That said, user experience will vary, and if you’re exploring ManageEngine, you should use this information to qualify the type of customer and product support you may receive, including asking for customer experience stories.
We recommend you book a discovery call with ManageEngine to learn more about the breadth and quality of its customer support and product support.
Why do we recommend it?
ManageEngine Log360 is a package of ManageEngine tools, including the EventLog Analyzer. You get all of the log management and threat hunting in the EventLog Analyzer package plus user activity tracking, file integrity monitoring, and Active Directory controls.
This SIEM receives a threat intelligence feed, which improves the speed of threat detection. If suspicious activity is spotted, Log360 raises an alert. Alerts can be sent through service desk systems, such as ManageEngine ServiceDesk Plus, Jira, and Kayoko. The package also includes a compliance reporting module for PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA.

Who is it recommended for?
Log360’s ability to reduce security complexity while providing in-depth, actionable insights into network activity makes it an ideal choice for businesses seeking efficient, scalable security management with minimal overhead. It is particularly beneficial for organizations seeking enhanced security and compliance without complex configurations.
Pros:
- Threat Intelligence Feed: Integrates a threat intelligence feed to stay updated on the latest security threats.
- Alerts Sent to Service Desk Packages: Sends alerts to service desk packages, streamlining incident response and resolution.
- Merges Windows Events and Syslog: Standardizes log formats by merging Windows Events and Syslog messages.
- Automated Threat Detection: Utilizes automated mechanisms to detect and respond to potential threats.
- Security Orchestration (SOAR): Coordinates with other security tools for automated system protection.
Cons:
- Limited Platform Support: Not available for Linux, potentially limiting its use in environments with Linux systems.
ManageEngine Log360 runs on Windows Server and it is available for a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Log360 is our top pick for a SIEM tool because it provides a comprehensive log manager that creates a large data pool for threat hunting. The log manager will collect log messages from any source, which includes Syslog, Windows Events, and application logs. This system will store all of those different logs in the same format. This consolidation process also enables logs to be searched as one body in the data analyzer of Log360. Compliance management is another major benefit of this package.
Download: Download a 30-day FREE Trial
Official Site: https://www.manageengine.com/log-management/download.html
OS: Windows Server
2. Graylog (FREE PLAN)
Tested on: Linux on a VM
Best for Small to Enterprise-level Businesses: Graylog’s open-source log management system is cost-effective and customizable, making it a good fit for smaller organizations with limited budgets and specific security needs, while its paid options scale nicely for larger organizations.
Price: Graylog Open = Free; Graylog Enterprise = $1,250 per month; Graylog Security = $1,550 per month; Graylog API Security = $1,550 per month.

Graylog is a log management system that can be adapted for use as a SIEM tool. The package includes a data collector that picks up log messages that derive from operating systems. It is also able to catch log data from a list of applications with which the package has integrations. The two main formats that Graylog will capture are Syslog and Windows Events.
Graylog’s key features
Graylog is available in both a free open source version and a paid SaaS platform. The system’s important features are:
- Data Collector: Provides a data collector to gather and manage log data for analysis.
- Application Integrations: Supports integrations with various applications, enhancing compatibility and data consolidation.
- Syslog and Windows Events: Capable of handling both Syslog messages and Windows Events for a comprehensive log management solution.
Unique buying proposition
Graylog’s unique buying proposition lies in its open-source, highly customizable log management platform. It offers real-time analysis, scalability, and an intuitive interface, with advanced alerting and security features. Ideal for centralized log management, Graylog integrates seamlessly across systems, providing businesses with robust, cost-effective, and flexible solutions.
Feature-in-focus: Graylog Security’s Investigation Timeline Visualization
Graylog’s Security Investigation Timeline Visualization allows security teams to visually track and analyze events in real-time. By presenting log data in a timeline format, it helps identify suspicious activities, correlate incidents, and streamline investigations. This visualization improves response time, enhances situational awareness, and supports more effective threat detection and remediation.
Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, Graylog received a 91/100 SupportScore. Graylog’s key support signals mostly flash green, making this a solid company to consider if you need a high degree of customer service and support. However, its SupportScore is no guarantee that you will receive the kind of support your company needs as user experiences will vary.
We recommend you speak directly with Graylog to learn more about the breadth and quality of its customer support and product support.
Why do we recommend it?
Originally a free, open-source system, Graylog has gathered a large and loyal user community through its years of operations. The more recent SIEM functions build on a solid log management tool.
The data collector passes log messages to a log server, where they are consolidated into a common format. The Graylog system calculates log throughput statistics and shows live tail records in the console as they arrive. The log server then files messages and manages a meaningful directory structure. Any of the logs can be called back into the data viewer for analysis.
The Graylog system includes pre-written templates for SIEM functions. These can be adapted and it is also possible to implement playbooks for automated responses on the detection of a threat.
Who is it recommended for?
Graylog is recommended for security teams, IT administrators, and organizations of all sizes that need a scalable, open-source log management and analysis solution. It is ideal for businesses seeking centralized log collection, real-time monitoring, and efficient troubleshooting across complex IT environments, with flexible search and powerful visualization capabilities.
Pros:
- Adaptable SIEM Functions: Offers adaptable SIEM functions for robust security monitoring.
- Orchestration with Access Rights Managers: Supports orchestration with access rights managers and firewalls, enhancing overall security posture.
- Consolidator: Acts as a consolidator, bringing together logs from diverse sources for unified analysis.
Cons:
- Won’t Install on Windows: One limitation is that Graylog won’t install on Windows, potentially restricting deployment options for users preferring Windows-based environments.
There are four versions of Graylog. The original edition is called Graylog Open, which is a free, open-source package with community support. That package installs on Linux or over a VM. The two main versions are Graylog Enterprise and Graylog Cloud. The difference between these is that Graylog Cloud is a SaaS package and it includes storage space for log files. The Enterprise system runs over a VM. There is also a free version of Enterprise called Graylog Small Business. That free plan is limited to processing 2 GB of data per day. You can get a demo of the full Graylog Cloud edition.
3. ManageEngine EventLog Analyzer (FREE TRIAL)
Tested on: Windows, Windows Server, and Linux
Best for: Small to Medium Businesses: This tool provides real-time log analysis and compliance reporting, suitable for organizations that require straightforward log management without the complexity of larger SIEM solutions.
Price: Free edition = $0; Premium = $595 per year; Distributed = $2,495 per year.

The ManageEngine EventLog Analyzer is a Log Management Tool because it focuses on managing logs and gleaning security and performance information from them. The tool is able to gather Windows Event log and Syslog messages. It will then organize these messages into files, rotating to new files where appropriate and storing those files in meaningfully-named directories for easy access. The EventLog Analyzer then protects those files from tampering.
ManageEngine EventLog Analyzer’s key features
This tool is a log manager and also a SIEM system. Its best attributes are:
- Log Collection: Collects and consolidates log data from Windows Event logs and Syslog messages, providing a centralized view of system events.
- Live Intrusion Detection: Monitors real-time events for potential security threats or intrusions, allowing for immediate response to suspicious activities.
- Log Analysis: Analyzes log data to identify patterns, trends, and anomalies, facilitating the detection of security incidents or operational issues.
Unique buying proposition
ManageEngine EventLog Analyzer’s unique buying proposition lies in its comprehensive log management and real-time monitoring capabilities. It offers automated log collection, advanced analytics, and compliance reporting. With a user-friendly interface, scalability, and integration with security tools, EventLog Analyzer helps organizations efficiently detect threats, maintain security, and meet regulatory requirements.
Feature-in-focus: ManageEngine EventLog Analyzer’s Threat Analytics
ManageEngine EventLog Analyzer’s Threat Analytics provides real-time monitoring and advanced analytics to detect security threats. By analyzing logs for suspicious activities, it identifies potential risks and vulnerabilities. This feature enables proactive threat detection, enhances incident response, and supports compliance efforts, helping organizations safeguard their infrastructure and sensitive data.
Why do we recommend it?
EventLog Analyzer is available for Linux as well as for Windows Server, so this is a very good choice for businesses that run Windows endpoints but Linux servers because it can collect Windows Events while running on Linux.
The ManageEngine system is more than a log server, though. It has analytical functions that will inform you of unauthorized access to company resources. The tool will also assess the performance of key applications and services, such as Web servers, databases, DHCP servers, and print queues.
The auditing and reporting modules of the EventLog Analyzer are very useful for demonstrating data protection standards compliance. The reporting engine includes formats for compliance with PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001.

Who is it recommended for?
ManageEngine EventLog Analyzer is recommended for IT administrators, security teams, and compliance officers in small to medium-sized organizations. It’s ideal for businesses seeking a cost-effective, user-friendly solution for centralized log management, real-time threat detection, and compliance reporting. The tool is particularly beneficial for organizations with limited resources but strong security needs.
Pros:
- Multi-Platform Support: Available for both Linux and Windows environments, making it versatile and adaptable to different IT infrastructures.
- Compliance Auditing: Supports compliance auditing for major standards such as HIPAA, PCI, FISMA, ensuring that organizations can meet regulatory requirements.
- Intelligent Alerting: Helps reduce false positives by employing intelligent alerting mechanisms, allowing users to prioritize specific events or areas of the network effectively.
Cons:
- Feature-Dense Product: The product is described as being feature-dense, which may pose a challenge for new users who have never used a Log Management Tool.
ManageEngine provides a Free edition of EventLog Analyzer, which is limited to processing logs from five sources. The regular package is called the Premium edition, which is priced according to the number of log sources that will be used – 10 to 1,000. The top plan is the Distributed edition, which centralizes log management for multiple sites. That starts with 50 log sources. The EventLog Analyzer software is available for installation on Windows Server or Linux and it is also offered as a cloud-based SaaS package. Try the system with a 30-day free trial.
4. Trellix Helix
Tested on: Cloud/SaaS
Best for Enterprise businesses: Trellix Helix provides comprehensive threat intelligence and automation features designed for large organizations requiring extensive security operations and incident response capabilities.
Price: Trellix doesn’t publish a price list.

Trellix Helix is a SIEM service that is delivered from the cloud. The tool installs an agent on the network that is to be monitored, and this collects data from endpoints and network devices. This system includes several extra features that qualify it for the status of next-generation SIEM.
Trellix Helix’s key features
Trelix Helix has now expanded into a suite of tools. Its best attributes are:
- Advanced Threat Detection: Leverages AI and machine learning to detect sophisticated threats in real-time.
- Cloud-Based Threat Hunting: Utilizes cloud-based capabilities for threat hunting, allowing for scalable and efficient monitoring of potential security threats.
- Intelligence Feed: Incorporates an intelligence feed for real-time information on emerging threats and vulnerabilities to enhance proactive security measures.
- Integrates with Third-Party Security Systems: Enables seamless integration with third-party security systems, fostering interoperability and flexibility in the overall security infrastructure.
Unique buying proposition
Trellix Helix’s unique buying proposition lies in its unified security operations platform that integrates advanced threat detection, automation, and response capabilities. It offers seamless coordination across security tools, enhances incident management, and provides actionable insights. Helix’s scalability and real-time visibility empower organizations to strengthen security and streamline operations efficiently.
Feature-in-focus: Trellix Helix’s threat intelligence
Trellix Helix’s threat intelligence combines real-time data and advanced analytics to identify, prioritize, and respond to security threats. It aggregates global threat feeds, providing actionable insights that enhance detection and response capabilities. This empowers organizations to proactively defend against emerging threats, improving overall security posture and minimizing risks.
Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, Trellix received a 92/100 SupportScore. The company showed well in all five of our SupportScore signals, meaning you are more likely to get high-touch customer support and ongoing product support and development. However, there is no guarantee that this will be the case.
We recommend you book a demo or discovery call directly with Trellix to and ask for more information about how it supports existing customers.
Why do we recommend it?
Trellix Helix is a competent cloud-based next-generation SIEM. This tool provides heavy processing power without the need for the buyer to invest in a host for the software. You get extra value out of your existing security tools because this SIEM extracts data from them and sends back threat remediation instructions.

Trellix is a new brand. However, the Helix system is older – it was originally developed by FireEye. The system generates user and entity behavior analytics (UEBA) to profile each device and user. It establishes a standard activity pattern for each identity and then implements anomaly-based security analysis. That is, any deviation from standard behavior is flagged as suspicious. The strategy is ideal for identifying insider threats and account takeovers.
The package also has a threat intelligence feed, which guides the threat detection system in its search through uploaded log messages and network activity records. The tool uses integrations to extract data from on-premises security tools.
Who is it recommended for?
Trellix Helix is recommended for enterprise security teams, SOCs, and organizations seeking an integrated, advanced security operations platform. It is ideal for businesses that require a unified solution for threat detection, incident response, and automated workflows. The platform is particularly beneficial for large organizations with complex security environments and compliance requirements.
Pros:
- Value for Money Through SOAR: Provides value for money by incorporating capabilities, thereby enhancing efficiency and response times through automation.
- Adaptability to Attacks: Demonstrates adaptability by tailoring threat-hunting methodologies to align with the evolving tactics of hacker attack campaigns, ensuring a proactive defense strategy.
- Vendor Reputation: The fact that a reliable security tools provider designs Trellix Helix suggests a level of trustworthiness and expertise in the field.
- Scalable Architecture: Supports growth with a flexible, scalable design that adapts to evolving security needs across organizations.
Cons:
- Dependency on Internet Connection: A significant drawback is that Trellix Helix can’t operate if an attacker successfully blocks the site’s Internet connection.
Trellix doesn’t offer a free trial of the Helix system. However, you can register for a free demo.
5. Heimdal Threat Hunting and Action Center
Tested on: Cloud/SaaS
Best for Medium to Enterprise-Level Businesses: Heimdal offers advanced threat detection and response capabilities, making it appropriate for organizations with dedicated security teams needing proactive threat-hunting tools.
Price: Heimdal doesn’t publish a price list, so you have to request a quote from its sales team.

Heimdal Threat Hunting and Action Center is an add-on function to the Heimdal cybersecurity environment, creating a centralized threat detection and response service from data pooled from on-premises Heimdal products. The essential contributor to threat-hunting source data is the Heimdal Next-Generation Anti-Virus (HGAV) package. This system incorporates a mobile device management (MDM) and is available for Windows, macOS, Linux, Android, and iOS.
Heimdal Threat Hunting and Action Center’s key features
The Heimdal Threat Hunting and Action Center coordinates other Heimdal products. Its best features are:
- Centralized Threat Detection: Offers a centralized approach to detecting and managing security threats across computer systems and mobile devices.
- Data Gathering: Gathers and analyzes data from both computers and mobile devices, providing a comprehensive view of the security landscape.
- Comprehensive Threat Intelligence: Heimdal integrates threat intelligence feeds, providing up-to-date information on emerging threats.
Unique buying proposition
Heimdal Threat Hunting and Action Center offers AI-powered real-time threat detection, automated response, and centralized management, enabling businesses to proactively identify, block, and neutralize cyber threats. Its intuitive platform streamlines security operations, minimizes downtime, and protects critical assets, helping organizations stay ahead of evolving cyber threats.
Feature-in-focus: Heimdal Threat Hunting and Action Center’s one-click remediation
Heimdal Threat Hunting and Action Center’s one-click remediation allows security teams to swiftly respond to threats with a single action. By automating the process of isolating infected devices, blocking malicious IPs, or removing malware, it significantly reduces response time, minimizing potential damage and ensuring a fast, efficient recovery.
Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, Heimdal received an 88/100 SupportScore. This score was achieved thanks in no small part to the company showing positive signs across our SupportScore data signals. The likelihood that you will receive adequate customer support and product support is high but not guaranteed. You should consider talking directly to Heimdal’s team about its support capabilities.
We recommend you book a discovery call with Heimdal’s team and ask for more details and, if available, customer stories or examples of support.
Why do we recommend it?
Heimdal Threat Hunting and Action Center provides a private threat intelligence service for a company. It aggregates data from local devices and creates a centralized data pool for threat detection. Data exchange is two-way because detected threats trigger responses, which can include local system hardening for devices that have not yet been hit.
The Threat Hunting and Action Center won’t activate unless you have the NGAV system plus two other Heimdal products. This is because the unit that performs threat hunting, which is called the XTP Engine, relies on data uploaded by those on-premises products. “XTP” stands for Extended Threat Protection.
The systems that you can choose from are Network Security, Email Security, Patching & Asset Management, and Endpoint Security. If you have more than two of those as well as the NGAV, your threat detection and response capabilities will get even better.
The Action Center provides automated responses when the threat Hunting module detects a threat. These instructions not only tell the affected device how to shut down the threat but also informs all other devices to create system hardening. For example, this would block lateral movement by malware or an intruder.

Who is it recommended for?
Heimdal Threat Hunting and Action Center is recommended for security teams, IT administrators, and organizations of all sizes looking for proactive threat detection and response. It’s ideal for businesses seeking to enhance their endpoint security, streamline incident management, and gain real-time visibility into threats, offering a centralized platform for swift action.
Pros:
- Automated Responses: Implements automated responses to security threats, allowing for swift actions to mitigate and address potential risks.
- Provides Vulnerability: Offers not only real-time threat detection but also includes vulnerability scanning, addressing potential weaknesses in the system.
- Behavioral Threat Analysis: Heimdal uses advanced behavioral analysis to identify suspicious activities and potential threats.
Cons:
- Not a Standalone Service: One of the identified drawbacks is that Heimdal is not a standalone service. It’s essential to consider this when evaluating the product, as organizations may need to integrate it into existing security infrastructure or use it in conjunction with other services.
You can’t get a free trial of the Threat Hunting and Action Center because the tool is part of a whole package, and you can choose different on-premises elements for your implementation. The best way to explore this system before buying is to request a free demo.
6. Datadog Security Monitoring
Tested on: Cloud/SaaS
Best for Small to Medium-sized Businesses: Datadog’s cloud-native platform offers real-time security monitoring with easy integration, ideal for smaller organizations seeking a user-friendly solution without extensive on-premises infrastructure.
Price: Cloud SIEM costs $5 per million events per month.

Datadog is a cloud-based system monitoring package that includes security monitoring. The security features of the system are contained in a specialized module. This is a full SIEM system because it monitors live events, but collects them as log file entries, so it operates both on log information and on monitoring data. The service collects local information through an agent, which uploads each record to the Datadog server. The security monitoring module then analyzes all incoming notifications and files them.
Datadog Security Monitoring’s key features
The Datadog security monitoring services is officially called the Datadog Cloud SIEM. Its most important features are:
- Full Security Visibility: Provides comprehensive security visibility through integration with over 500 tools and services.
- Over 600 Vendor Integrations: Integrates with over 600 vendors, providing extensive compatibility with various tools and services.
- Unified Dashboard: Enables users to observe metrics, traces, logs, and other data from a unified dashboard.
- Out-of-the-Box Detection Rules: Provides robust pre-configured detection rules out-of-the-box for streamlined threat detection.
Unique Feature:
The Datadog security package is delivered in three units that include Posture Management to scan cloud systems for vulnerabilities and Workload Security for live security monitoring. The third stand is the Cloud SIEM, which implements security scanning for on-premises systems.
Unique buying proposition
Datadog Cloud SIEM offers a scalable, cloud-native solution designed for integration with cloud environments, providing real-time security monitoring, threat detection, and analytics across complex infrastructures. Machine learning-driven anomaly detection and automated threat response empower security teams to proactively identify and mitigate risks. Its unified platform integrates with over 450 data sources, offering a comprehensive, streamlined approach to security that’s flexible, scalable, and easy to use for modern cloud-based businesses.
Feature-in-focus: Datadog Cloud SIEM’s detection rules
Datadog Cloud SIEM includes more than 400 pre-written detection rules that use machine learning and customizable thresholds to identify potential security threats in real-time. These rules are highly adaptable, enabling users to fine-tune alerts based on specific risk factors and data sources, ensuring accurate and timely threat detection across cloud-based environments and infrastructures.
Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, Datadog received a 95/100 SupportScore. Datadog is highly likely to have strong, ongoing customer support and product support thanks to high scores across all five SupportScore signals. Nevertheless, this is not a guarantee, as your company may have a unique structure or needs that don’t align with the level of customer service that Datadog can provide.
We recommend you speak directly with Datadog to learn more about the breadth and quality of its customer support and product support.
Why do we recommend it?
Datadog Security Monitoring is a cloud-based SIEM that is a great choice for multi-site businesses. The service is also able to gather activity data from cloud platforms, making it ideal for a hybrid system. The Datadog platform includes a range of tools that can extend the security monitoring of this package with other functions, such as log management and an audit trail service.

Security events trigger alerts for the service in the console. The console also gives access to all event records. Logged messages are indexed and retained for 15 months. They can be accessed for analysis through the Datadog console or extracted and imported into another analysis tool.
The offsite processing capabilities reduce the processing demands on your infrastructure. It also makes it very easy to monitor remote networks. The analysis service has a pre-defined set of rules that will automatically detect known attack vectors.
Datadog updates the pool of detection rules automatically when new attack strategies are discovered. This means that the system administrators don’t need to worry about keeping security software up to date because that process happens automatically on the cloud server. It is also very easy for a systems administrator to create custom detection and mitigation rules.
Datadog offers a menu of specialist modules and all of them can be deployed individually or as a suite. You get greater functionality by combining modules, which are all able to share data about the monitored system.
Who is it recommended for?
Datadog Cloud SIEM is recommended for cloud-native organizations, DevOps teams, and security professionals looking for a scalable, real-time security monitoring solution. It’s ideal for businesses that require seamless integration with cloud environments like AWS, Azure, and Google Cloud, and need efficient threat detection, log management, and incident response in a unified platform.
Pros:
- Real-time Threat Detection: Allows users to start detecting threats immediately with default rules aligned to the MITRE ATT&CK framework.
- Gartner Survey Rating: DataDog scored 4.6/5 in a Gartner survey of IT customers, indicating high satisfaction among users.
- 14-day Free Trial: Offers a 14-day free trial period for users to explore and evaluate the platform.
- Data Integration: Takes input from 450 data sources, including cloud providers, apps, and security tools.
Cons:
- Overwhelming Functionality: The wealth of functionality provided by DataDog may be a little overwhelming for users, especially during the initial stages of use.
Datadog is available on a 14-day free trial.
7. Microsoft Sentinel
Test on: Due to a lock of trial options, this tool was not directly tested.
Best for Medium to Enterprise-Level Businesses: Microsoft Sentinel is a cloud-native SIEM solution that offers real-time threat detection and intelligent security analytics, suitable for organizations leveraging Azure services.
Price: Pay-As-You-Go at $5.22 per GB; a range of plans that start at 100 GB per day for $342.52 per day.

Microsoft Sentinel is a cloud-native Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) solution that leverages artificial intelligence and machine learning to provide real-time threat detection, proactive security analytics, and automated response capabilities. Built on top of Microsoft Azure, Sentinel integrates with various security tools and enables organizations to monitor and protect their entire IT ecosystem.
Microsoft Sentinel’s key features
Microsoft Sentinel is hosted on the Azure platform. Its best features are:
- Cloud-Native System: As a fully managed service, Sentinel is built on Microsoft Azure.
- Real-Time Threat Detection: Uses AI and machine learning to provide advanced threat detection.
- Integrated Security Analytics: Aggregates data from across your environment for security analytics.
Unique buying proposition
Microsoft Sentinel offers a scalable, cloud-native SIEM solution that integrates seamlessly with existing Microsoft and third-party tools. It provides advanced AI-driven threat detection, automated incident response, and centralized security monitoring, enabling businesses to detect, investigate, and respond to threats efficiently, all while reducing operational complexity and costs.
Feature-in-focus: Microsoft Sentinel’s behavior analytics
Microsoft Sentinel’s behavior analytics uses advanced machine learning to detect anomalies in user and entity behavior. By identifying unusual patterns, it helps pinpoint potential insider threats, compromised accounts, or malicious activity. This proactive approach enhances threat detection accuracy, reducing false positives and enabling faster, more effective responses to security incidents.
Comparitech SupportScore
Our SupportScore formula relates to the quality of support offered by a particular company rather than the support offered for a specific product. So, we are looking at Microsoft, rather than Microsoft Sentinel and Microsoft gets a very high score.
The SupportScore for Microsoft is 96 out of 100. This high score comes from the company’s size, profitability, and employee job satisfaction as much as the quality of its online and in-app help and its Customer Success team.
Why Do We Recommend It?
Microsoft Sentinel provides an entire platform for a Security Operations Center. It is a blend of both a SIEM and a SOAR. The tool scans log messages, like any traditional SIEM, but you can also feed in signals from other cybersecurity systems. This package minimizes human intervention, improving accuracy and efficiency.

Microsoft Sentinel can monitor various environments, including on-premises systems, Azure resources, and other cloud platforms like AWS and Google Cloud. It integrates easily with security solutions across hybrid environments, collecting data from various sources such as firewalls, servers, endpoints, cloud applications, and IoT devices. Sentinel can ingest security logs from virtually any system or platform, including Microsoft and non-Microsoft products.
The SOAR capabilities of Microsoft Sentinel expand and automate incident response. Sentinel uses playbooks to automate common security operations tasks, such as blocking suspicious IP addresses, sending notifications, or isolating compromised machines. These playbooks can be triggered by specific alerts or anomalies, providing an immediate automated response.
Who is it recommended for?
Microsoft Sentinel is recommended for enterprise security teams, IT professionals, and organizations of all sizes looking for a cloud-native SIEM solution. It’s ideal for businesses seeking advanced threat detection, automated response, and integration with Microsoft and third-party services. Its scalability and AI-driven analytics make it well-suited for dynamic, hybrid environments.
Pros:
- Security Automation & Orchestration (SOAR): Automated incident response workflows reduce manual intervention.
- Threat Intelligence Integration: Can accept external threat intelligence feeds.
- Multi-Environment Monitoring: It supports monitoring for on-premises, hybrid, and multi-cloud infrastructures.
Cons:
- Cloud-Dependent: No on-premises version.
Microsoft Sentinel’s pricing is based on retention and data ingested (per GB). While the solution provides various pricing tiers to accommodate different organizational needs, including pay-as-you-go and reserved capacity models, it can become costly for enterprises with large volumes of log data. To start using Microsoft Sentinel, users need an Azure account. Once registered, they can access Sentinel via the Azure Portal and begin configuring their environments.
8. Elastic Security
Tested on: Windows, macOS, Linux, and cloud
Best for Medium to Enterprise-Level Businesses: Elastic Security integrates SIEM capabilities with the Elastic Stack, providing scalability and flexibility for organizations with substantial data analysis needs.
Price: Four plans: Standard from $95 per month; Gold from $109 per month; Platinum from $125 per month; Enterprise from $175 per month.

The Elastic Stack is a group of free tools that can be used to analyze any dataset. This is a very widely used package that includes Logstash for log message collection, Elasticsearch for data assessments, and Kibana to display results. The group is also known as ELK. The problem most users will face when using ELK for security monitoring is that it takes a lot of work to set up your own search rules. However, Elastic Security is a paid package of all of the rules and settings that you need in order to make an SIEM system out of ELK.
Elastic Security’s key features
Elastic Security is part of the wider Elastic platform, which also offers system performance monitoring. Its best features are:
- Log Collection: The platform is designed to collect log messages from various sources, facilitating centralized log management.
- Log Analysis: Provides capabilities for both live and historical analysis of log data, allowing users to gain insights in real-time and retrospectively.
- Out-of-the-Box Threat Hunting: Offers out-of-the-box threat hunting capabilities, allowing users to search for potential security threats within the log data proactively.
Unique buying proposition
Elastic Security offers a unique buying proposition by providing real-time threat detection, robust security analytics, and scalable threat hunting in a unified platform. Its open-source foundation, combined with powerful machine learning and advanced data visualization, empowers organizations to proactively detect, investigate, and respond to security threats, enhancing overall protection.
Feature-in-focus: Elastic Security’s Attack Discovery
Elastic Security’s Attack Discovery leverages machine learning and advanced analytics to identify hidden threats in real-time. It analyzes large volumes of data, uncovering attack patterns and suspicious activities. By providing visibility into potential attacks early on, it enables proactive threat detection and faster response, enhancing overall security posture.
Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, Elastic earned a 95/100 SupportScore. This score means that Elastic performed well against our 5-point signal analysis for customer and product support and that you are highly likely to receive good service from his company. However, user experiences will vary, so you will need to verify what support looks like if Elastic is on your shortlist of vendors.
We recommend reaching out to Elastic’s team to learn more about how it supports both its customers and its products.
Why do we recommend it?
Although the Elastic Security package operates on your ELK installation, it doesn’t reserve the entire stack for its own use. You can still create your own data analysis tools alongside your constantly-running ELK SIEM system. This makes the Elastic Security service very good value for money.

You can adapt the Elastic Security package to take any source of data, such as application status reports as well as operating system log messages. The service isn’t limited to monitoring one site or platform, so you can channel source data into the SIEM from any site and also cloud services.
Who is it recommended for?
Elastic Security is recommended for security teams, IT administrators, and organizations of all sizes seeking a flexible, open-source security solution. It’s ideal for businesses looking for comprehensive threat detection, real-time monitoring, and incident response capabilities, with seamless integration into Elastic Stack for efficient log management and analysis across cloud and on-prem environments.
Pros:
- Deployment Options: Elastic Stack offers flexibility in deployment options, allowing users to choose configurations that suit their specific needs.
- Customizable with Extra Data Sources: Elastic Stack can be customized by integrating additional data sources, providing users with the flexibility to tailor the platform to their specific requirements.
- Scalable Security Analytics: Handles vast amounts of data, providing deep insights into potential security risks.
Cons:
- Requires Work to Set Up: The setup process might involve configuration and customization, which could be perceived as a potential challenge for users.
Elastic Security is included in all of the paid plans for the Elastic Stack system and the price is the same whether you host the software yourself or access it on Elastic Cloud. There are five price points and all of the editions include performance monitoring as well as the security package. You can assess any of the plans on Elastic Cloud with a 14-day free trial.
9. Logpoint SIEM
Tested on: Linux and Cloud
Best for Medium to Enterprise-level Businesses: Logpoint SIEM provides advanced analytics and compliance reporting, catering to organizations that need scalable solutions to handle extensive security data.
Price: Use the Price Calculator to work out how much your company would pay.

Logpoint is a security package that includes a SIEM, user and entity behavior analysis (UEBA), and security orchestration, automation, and response (SOAR). This represents a closed-loop security system that can manage your entire Security Operations Center (SOC). As the service’s name suggests, the core of the system is a log manager.
Logpoint SIEM’s key features
Logpoint can be self-hosted or accessed as a SaaS platform. Its main features are:
- Log Collection and Management: Facilitates the collection and management of logs for comprehensive security monitoring.
- User and Entity Behavior Analytics (UEBA): Utilizes AI and UEBA to analyze user and entity behavior for advanced threat detection.
- SOAR Capabilities: Incorporates Security Orchestration, Automation, and Response (SOAR) capabilities for automated incident response.
Unique buying proposition
Logpoint SIEM offers a unique buying proposition with its scalable, easy-to-deploy solution that combines advanced threat detection, real-time security monitoring, and efficient compliance management. Its centralized platform provides full visibility across environments. The platform uses machine learning and automated response to enhance security posture while simplifying security operations and reducing costs.
Feature-in-focus: Logpoint SIEM’s compliance management
Logpoint SIEM’s compliance management simplifies adherence to industry standards and regulations by automating data collection, reporting, and audit trails. It ensures continuous monitoring and real-time alerts for regulatory requirements, including GDPR, PCI-DSS, and HIPAA. This helps organizations reduce compliance risks, streamline audits, and maintain a secure, compliant environment.
Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, Logpoint received a 92/100 SupportScore. This means that Logpoint is more likely than not to provide high-quality customer service to most of its customers. However, that is not a guarantee. While its key signals point to this, you’ll need to verify the company’s support capabilities directly if they are on your shortlist of vendors.
We recommend you book a discovery call with Logpoint to learn more about the breadth and quality of its customer support and product support.
Why do we recommend it?
The integrated SOAR in the Logpoint package is a big cost save. This allows a security analyst to thread together all of the cybersecurity systems operating on a site, such as antivirus and firewalls, into a homogeneous unit that requires no manual intervention to identify and block threats quickly.
Logpoint collects and consolidates all of the log messages generated by your system on your sites and on cloud platforms. This creates a pool of data for threat hunting searches.
The UEBA provides a baseline of expected activity per user and per device, which also includes external users and activity sources. This is a Machine Learning strategy that drives most AI-based threat detection systems these days. Once a standard pattern of behavior has been recorded for each individual and endpoint or external IP address, the tool looks for deviations from that pattern. This catch-all strategy spots manual intrusion, automated attacks, insider threats, and account takeovers.

Responses can be automated by playbooks. The exact degree of automation is up to you and the SOAR service in the package means that secondary information can be fed in from more than 25,000 third party tools as part of the rule set for triggering a response. Those responses are implemented by updating your security tools or sending instructions. This will involve interactions with the access rights manager (ARM), firewalls, and on-device AVs. Logpoint can also generate alerts and tickets for your Service Desk system.
Who is it recommended for?
Logpoint SIEM is recommended for security teams, IT administrators, and organizations of all sizes that require a robust, scalable solution for security monitoring and compliance. It’s ideal for businesses seeking advanced threat detection, real-time incident response, and centralized log management, particularly in industries with stringent compliance requirements like finance and healthcare.
Pros:
- Insider Threat Detection: Specializes in detecting both external intruder threats and internal insider threats to enhance security.
- Threat Intelligence Feed: Integrates a threat intelligence feed for staying updated on the latest security threats.
- GDPR Reporting: Includes features for GDPR reporting, helping organizations comply with data protection regulations.
Cons:
- No Free Trial Period: The absence of a free trial period may limit the ability of potential users to explore and evaluate the platform before making a commitment.
Logpoint has three deployment options, which gives it a wide audience. It can be installed on Ubuntu Linux for on-premises operations or you can get it as a service on the AWS Marketplace. The company also offers Logpoint as a SaaS platform. There is no free trial, but you can request a demo to assess the package
10. SolarWinds Security Event Manager
Tested on: Windows Server
Best for: Small to Medium Businesses: SolarWinds offers an affordable and user-friendly SIEM solution, ideal for smaller organizations looking to enhance their security posture without significant investment, it medium-sized organizations and even larger ones may still find value here.
Price: Starts at $3,292

In terms of entry-level SIEM tools, SolarWinds Security Event Manager (SEM) is one of the most competitive offerings on the market. The SEM embodies all the core features you’d expect from an SIEM system, with extensive log management features and reporting. SolarWinds’ detailed real-time incident response makes it a great tool for those looking to exploit Windows event logs to actively manage their network infrastructure against future threats.
SolarWinds Security Event Manager’s key features
The SolarWinds system is an on-premises package. Its important features are:
- Simple Log Filtering: Features straightforward log filtering, eliminating the need to learn a custom query language.
- Dozens of Templates: Provides dozens of templates, enabling administrators to start using SEM with minimal setup or customization.
- Log Manager: Acts as a log manager with the capability to forward records to third-party tools.
- Historical Analysis: Provides tools for historical analysis, aiding in the identification of past security incidents
Unique feature:
This SolarWinds package runs on Windows Server and can be partnered by other SolarWinds tools to form a suite. The log manager in the package is able to collect log messages from all active components of an IT system, not just SolarWinds products.
Unique buying proposition
SolarWinds Security Event Manager offers a unique buying proposition with its user-friendly, cost-effective SIEM solution that combines real-time event correlation, automated incident response, and simplified compliance reporting. It provides fast deployment, scalability, and an intuitive interface, making it accessible for organizations of all sizes to manage security effectively and efficiently.
Feature-in-focus: SolarWinds Security Event Manager’s Cyberthreat Analysis Tool
SolarWinds Security Event Manager’s Cyberthreat Analysis Tool provides real-time monitoring and advanced analytics to detect and assess potential cyber threats. It uses machine learning to identify patterns, enabling proactive threat hunting and rapid incident response. This tool enhances security by uncovering hidden threats and offering actionable insights for faster mitigation.
Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, SolarWinds received an 89/100 SupportScore. This score means that SolarWinds is most likely to offer the range of customer and product support almost any of its customers might need. Although its weakest area is in employee job satisfaction, this may not impact the specific team providing customer service and product support.
We recommend you book a demo or discovery call directly with SolarWinds and ask more about its customer service, product support, and company culture.
Why do we recommend it?
The SolarWinds Security Event Manager is an on-premises service that is able to reach out to cloud platforms as well. This service can unify the monitoring of multiple sites and cloud services from its base on one of your servers.
One of the best things about the SEM is its detailed and intuitive dashboard design. The simplicity of the visualization tools makes it easy for the user to identify any anomalies. As a welcome bonus, the company offers 24/7 support, so you can contact them for advice if you run into an error.

SolarWinds Security Event Manager provides methods to collect, collate, and consolidate log messages as well as providing automated and manual analysis systems. This is an on-premises package that will gather log messages from many different services and devices, including network switches and routers, firewalls, operating systems, security software on endpoints, and typical applications, such as Web servers and file transfer utilities. The log messages are analyzed automatically as soon as they arrive and they are also filed. Log files are stored in a meaningful folder structure, which makes past log messages easy to locate and load into the Security Event Manager’s data viewer for manual analysis.
Who is it recommended for?
SolarWinds Security Event Manager is recommended for IT professionals, security teams, and small to medium-sized organizations looking for an easy-to-deploy SIEM solution. The on-premises software implements real-time log analysis, threat detection, and compliance reporting with minimal complexity. Its automated response capabilities make it a practical choice for streamlined security management.
Pros:
- Live Anomaly Detection: Utilizes real-time anomaly detection to identify abnormal patterns or behavior.
- Enterprise-Focused SIEM: Designed with an enterprise focus and offers a wide range of integrations.
- 30-day Free Trial: Offers a 30-day free trial period, allowing users to explore and evaluate the product.
Cons:
- Advanced SIEM for Professionals: Targeted as an advanced SIEM product for professionals, which may require time to fully learn and master the platform.
The software for SolarWinds Security Event Manager installs on Windows Server. Pricing is scaled to account for capacity requirements but the starting price is $2,877, so this isn’t a tool for small businesses. Get a 30-day free trial.
11. Fortinet FortiSIEM
Tested on: Hardware, VMware, Hyper-V, KVM, OpenStack, and AWS
Best for Medium to Large Businesses: FortiSIEM combines network monitoring and security management, catering to organizations that require integrated solutions for complex IT environments.
Price: Fortinet doesn’t publish a price list.

Fortinet FortiSIEM can be used as a standalone tool or combined with other Fortinet tools to create a full enterprise protection system called the Fortinet Security Fabric. Fortinet has an excellent reputation in the field of cybersecurity, and its hardware appliances are custom-built with specially designed microchips to provide high-speed data processing. The FortiSIEM can be included on a hardware device, or you can run it as a virtual appliance. The system is also offered as a service on AWS.
Fortinet FortiSIEM’s key features
FortiSIEM has a range of deployment options. Its best features are:
- UEBA Features: This boosts the platform’s ability to detect anomalies and potential security threats based on user and entity behavior.
- Attack Responses: The platform includes features for attack responses, allowing for automated actions to mitigate and respond to security incidents.
- Compliance Reporting: FortiSIEM includes compliance reporting features that assist organizations in adhering to regulatory requirements and industry standards.
Unique buying proposition
Fortinet FortiSIEM offers a unique buying proposition with its integrated security information and event management system, combining network visibility, advanced threat detection, and automated response. It provides seamless scalability, centralized management, and powerful analytics, enabling organizations to reduce risk, improve operational efficiency, and streamline compliance across complex IT environments.
Feature-in-focus: Fortinet FortiSIEM’s contribution to the Fortinet Security Fabric
Fortinet FortiSIEM enhances the Fortinet Security Fabric by providing comprehensive visibility and integrated threat detection across the entire network. It centralizes security data, correlates events, and automates responses, ensuring a unified defense approach. This integration strengthens security posture, enabling faster threat detection and response while enhancing overall operational efficiency.

Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, Fortinet earned a 95/100 SupportScore. This score means that Fortinet is most likely a high-quality service to consider if your company needs detailed and hands-on customer support and a product that is also well-supported for the long term. None of that is guaranteed to be true or guaranteed to be what you or current customers personally experience, however.
We recommend that you connect with Fortinet’s team to dig deeper into how it supports its product and its customers.
Why do we recommend it?
Fortinet is a leading provider of system security solutions and deserves to be included in any list of security service categories in which they have products. Including FortiSIEM as part of a SASE solution or adding it to the FortiGate firewall provides optimum security.
Fortinet FortiSIEM will collect and store log messages, which is an essential task for compliance with many data protection standards. FortiSIEM provides compliance reporting for PCI-DSS, HIPAA, GLBA, and SOX. Another important feature of this system is that it can be set up to implement automated responses to shut down the threats that it detects.
Who is it recommended for?
Fortinet FortiSIEM is recommended for large enterprises, MSSPs, and organizations with complex, multi-layered security infrastructures. It will appeal to businesses seeking an integrated, scalable SIEM solution that combines threat detection, incident response, and IT operations management. FortiSIEM is particularly suited for organizations needing enhanced security across both on-premises and cloud environments.
Pros:
- Choice of Data Processing Volumes: Fortinet FortiSIEM provides users with the flexibility to choose data processing volumes based on their specific needs and requirements.
- Security Assurance: FortiSIEM can be seamlessly combined with a firewall and traffic shaping service, providing a comprehensive security solution for network management.
- Options for Virtual Networks: Offers options to implement security measures specifically designed for virtual networks, catering to the needs of virtualized environments.
Cons:
- Higher-End Pricing: FortiSIEM prices are positioned at the higher end of the market, potentially making it less accessible for organizations with budget constraints.
The expansion of Fortinet’s implementation model to include virtual appliances enables the business to appeal to a wider audience than its original and still favored deployment system based on hardware appliances. The company offers a demo of its Fortinet SIEM and other products.
12. Splunk Enterprise Security
Tested on: Windows, Windows Server, and Linux
Best for: Large Enterprises. Splunk offers extensive data analytics and security monitoring capabilities, making it suitable for large organizations with significant data volumes and complex security requirements
Price: Splunk has two pricing models: workload pricing and ingest pricing. However, it doesn’t publish either tariff, so you have to contact the Sales team for a quote.

Splunk is one of the most popular SIEM management solutions in the world. What sets it apart from the competition is that it has incorporated analytics into the heart of its SIEM. Network and machine data can be monitored on a real-time basis as the system scours for potential vulnerabilities and can even point to abnormal behavior. Enterprise Security’s Notables function displays alerts that can be refined by the user.
Splunk Enterprise Security’s key features
Splunk Enterprise Security can be downloaded and run on Windows Server or Linux. Its best features are:
- Real-Time Network Monitoring: This feature allows organizations to actively track and respond to events as they occur.
- Asset Investigator: Asset Investigator feature enables detailed analysis and investigation of assets within the network.
- Historical Analysis: Facilitates historical analysis, allowing users to examine and analyze past events and trends.
Unique buying proposition
Splunk Enterprise Security offers a comprehensive, real-time security information and event management (SIEM) solution. Its unique value proposition lies in its ability to provide actionable insights through advanced analytics, machine learning, and a scalable platform, helping organizations detect, investigate, and respond to security threats efficiently and proactively.
Feature-in-focus: Splunk Enterprise Security’s risk-based alerting
Splunk Enterprise Security’s risk-based alerting (RBA) prioritizes security alerts based on potential risk, enhancing incident response. By using risk scores, RBA helps security teams focus on the most critical threats. It correlates events and behaviors, offering a more efficient, data-driven approach to detecting, prioritizing, and mitigating security risks.

Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, Splunk earned a 95/100 SupportScore. This score reflects Splunk’s strong showing against our 5-point signal analysis of the company data that can impact product and customer support capabilities. There is a strong chance that Splunk will offer exceptional customer support and product support, but this may vary across its customer base.
We recommend you book a meeting with Splunk’s team to learn more about what its customer support capabilities look like in real time.
Why do we recommend it?
Splunk Enterprise Security is a very flexible package that provides you with the base Splunk package for data analysis. You can create your own threat-hunting searches, analysis functions, and automated defense rules, as well as use the out-of-the-box rules that are included with this plan.
Regarding responding to security threats, the user interface is incredibly simple. When conducting an incident review, the user can start with a basic overview before clicking through to in-depth annotations of past events. Likewise, the Asset Investigator does a fine job of flagging malicious actions and preventing future damage.
Who is it recommended for?
Splunk Enterprise Security is recommended for large enterprises, security operations teams, and organizations with complex IT environments. It is suitable for businesses seeking advanced threat detection, incident response, and security analytics across diverse data sources. Splunk’s scalability and machine learning capabilities make it well-suited for organizations with high-volume, real-time security monitoring needs.
Pros:
- Behavior Analysis for Threat Detection: Utilizes behavior analysis to detect threats that may go unnoticed through traditional log analysis methods, enhancing the platform’s threat detection capabilities.
- Available for Linux and Windows: Offers compatibility with both Linux and Windows operating systems, providing flexibility in deployment.
- Easy Customization: Features an excellent user interface that is highly visual and offers easy customization options.
Cons:
- Non-Transparent Pricing: The pricing structure is not transparent and requires a quote from the vendor, which may make it challenging for organizations to assess the cost beforehand.
- More Suited for Large Enterprises: While suitable for large enterprises, the extensive features and potentially higher costs may make it less ideal for smaller organizations with simpler security needs.
You need to contact the vendor for a quotation so it’s clear that this is a scalable platform designed with larger organizations in mind. There is also a SaaS version of this Splunk service called Splunk Security Cloud. This is available for a 15-day free trial. The trial version of the system is limited to processing 5 GB of data per day.
13. Rapid7 InsightIDR
Tested on: Cloud/SaaS
Best for Medium to Enterprise-Level Businesses: Rapid7 provides user behavior analytics and incident detection, ideal for organizations seeking advanced threat detection without the overhead of traditional SIEM solutions.
Price: Three plans: InsightIDR Essential starts at $3.82 per asset per month; InsightIDR Advanced starts at $6.36 per asset per month; InsightIDR Ultimate starts at $8.21 per asset per month

Rapid7 InsightIDR is headlined as both an XDR and a SIEM. This cloud-based system installs agents on your site to collect and upload activity data. The system is supported by a team of security analysts who supplement the insights of the detection software. The tool also gets a threat intelligence feed, which sharpens threat detection toward current attack vectors.
Rapid7 InsightIDR’s key features
Rapid7 terms Insight IDR both as a SIEM and an XDR. Its most important features are:
- Endpoint Protection: InsightIDR includes features for endpoint protection, addressing security concerns at the individual device level.
- Network Security Scanning: The platform offers network security scanning capabilities for the identification and mitigation of vulnerabilities within the network.
- UEBA Capabilities: Incorporates UEBA features for the detection of anomalous behaviors that may indicate security threats.
Unique buying proposition
Rapid7 InsightIDR offers a unified security solution with advanced threat detection, incident response, and user behavior analytics. Its unique buying proposition lies in its ability to automate threat detection using a powerful combination of machine learning and human intelligence, enabling faster, more accurate response to emerging security threats.
Feature-in-focus: Rapid7 InsightIDR’s network traffic analysis
Rapid7 InsightIDR’s network traffic analysis provides deep visibility into network communications, helping detect suspicious activities and potential threats. By monitoring traffic patterns and analyzing network flows, it identifies anomalies, unauthorized access, and data exfiltration attempts, enhancing overall threat detection and response capabilities with real-time insights and proactive security measures.

Comparitech SupportScore
Based on our multi-point analysis of the key signals for effective customer and product support, Rapid7 earned a 94/100 SupportScore. This score means that Rapid7 scored well in every category we assess in predicting the likelihood of quality customer and product support. That will likely be the case with Rapid7 if you choose them as a vendor of choice, but it’s not guaranteed.
We recommend you contact Rapid7 directly to learn more about the effectiveness of its customer and product support.
Why do we recommend it?
InsightIDR is more of a “platform” than a “package” because it includes a collection of security systems. It provides multiple threat detection methods and also exploits the power of your existing security systems, such as firewalls and access rights managers. Threat response can be automated for immediate action.
This system combines several threat detection strategies. The threat intelligence feed provides indicators of compromise (IoCs), which are the foundations of a signature-based detection approach. The system also includes a user and entity behavior analytics (UEBA) module, which records a baseline of normal behavior for each user account and device – this is an anomaly-based detection method.
While collecting event data from each endpoint, this tool also gathers live network activity information. This combination provides the classic source data for a SIEM. The threat detection process is performed in the cloud on Rapid7 servers, thus lightening the processing burden on your servers.
Responses can be implemented through third-party tools. The InsightIDR service writes new firewall rules to block traffic from suspicious external sources and it can also instruct access rights managers to suspend accounts that seem to have been compromised.
The InsightIDR console helps system administrators create honeypots and traps to lure intruders into a dead end where they can be identified and blocked. The service is a time-saver and it creates fake data files and accounts with weak security as bait.
Who is it recommended for?
Rapid7 InsightIDR is recommended for security teams, IT administrators, and organizations of all sizes seeking a unified, cloud-based SIEM solution. It will suit businesses that need advanced threat detection, user behavior analytics, and incident response capabilities. InsightIDR is particularly useful for organizations looking for a scalable, easy-to-deploy solution with integrated automation.
See also: How to Create a Honeypot to Catch Intruders
Pros:
- Deception Technology: Provides deception technology utilities, enhancing the platform’s ability to detect and deceive potential attackers and improving overall security.
- Automated Threat Response: Provides automated threat response mechanisms and comprehensive action logging for efficient incident response and analysis.
- SOAR Capabilities: Incorporates SOAR capabilities that helps to streamline security processes and response actions.
Cons:
- Cannot Protect Offline Systems: Systems that are completely disconnected from the internet may not be protected, potentially impacting security coverage for offline environments.
InsightIDR provides compliance auditing and threat protection. It collects and stores system log messages, retaining them live for three months and then keeping them in an archive for 10 months. Archived files can be revived for compliance auditing.
You can get a 30-day free trial of Rapid7 InsightIDR.
See also: The Best HIDS
14. LogRhythm (Exabeam) NextGen SIEM Platform
Tested on: Windows, appliance, or cloud
Best for Medium to Enterprise-level Businesses: LogRhythm provides comprehensive security analytics and incident response capabilities, catering to organizations that need robust security intelligence solutions.
Price: Exabeam doesn’t publish its price list for LogRhythm, but you can request a demo to start your investigation into the NextGen SIEM.

LogRhythm (now part of Exabeam) has long established itself as a pioneer within the SIEM solution sector. From behavioral analysis to log correlation and artificial intelligence for machine learning, this platform has it all.
LogRhythm NextGen SIEM’s key features
LogRythm was recently bought out by rival SIEM producer Exabeam. The platform’s best features are:
- Sleek Interface: Features a visually appealing and highly customizable interface, enhancing user experience.
- Log File Management: Simplifies log file management through easy-to-use wizards, making it a user-friendly tool for setting up log collection and other security tasks.
- Guided Analysis: Provides guided analysis features, which can assist users in understanding and interpreting security data, aiding in effective incident response.
Unique buying proposition
LogRhythm NextGen SIEM offers a unified security platform that combines log management, network monitoring, and advanced threat detection. Its unique buying proposition lies in its AI-powered analytics, automated incident response, and comprehensive visibility, enabling faster threat detection, streamlined investigations, and enhanced security operations for organizations of all sizes.
Feature-in-focus: LogRhythm NextGen SIEM’s Security Orchestration and Automated Response (SOAR)
LogRhythm NextGen SIEM’s Security Orchestration and Automated Response (SOAR) streamlines incident response by automating repetitive tasks and workflows. It enhances operational efficiency, reduces response times, and minimizes human error. With integrated playbooks and seamless collaboration tools, SOAR empowers security teams to rapidly mitigate threats and improve overall security posture.
Comparitech SupportScore
The combined teams of LogRhythm and Exabeam provide a strong Customer Support service, which boosts the SupportScore of the provider. The systems of both companies also provide excellent in-app help and online guides. The business is stable and profitable, meaning that it is unlikely to go out of business and let buyers down.
With a large and stable business and excellent support features, LogRhythm gets a SupportScore of 91 out of 100.
Why do we recommend LogRhythm?
LogRhythm NextGen SIEM is a cloud-based service very similar to Datadog, Logpoint, LevelBlue, and QRadar. This tool is equally proficient to its rivals, so we couldn’t leave it out of our list of recommendations.

The system is compatible with a massive range of devices and log types. In terms of configuring your settings, most activity is managed through the Deployment Manager. For example, you can use the Windows Host Wizard to sift through Windows logs.
This makes it much easier to narrow down on what is happening on your network. At first, the user interface does have a learning curve, but the extensive instruction manual helps. The icing on the cake is that the instruction manual actually provides hyperlinks to various features in order to aid you in your journey.
Who is it recommended for?
LogRhythm NextGen SIEM is recommended for security teams, IT professionals, and organizations of all sizes that require comprehensive threat detection, log management, and security monitoring. The package will help businesses seeking a unified, scalable platform with advanced analytics, automated incident response, and seamless integration for both cloud and on-prem environments.
Pros:
- User-Friendly Setup: Utilizes simple wizards for log collection and security tasks, making it accessible for beginners.
- AI and ML Integration: Leverages AI and machine learning for behavior analysis, enhancing overall threat detection capabilities.
Cons:
- Lack of Trial Option: The absence of a trial option may be a drawback for users who prefer to assess the software before committing to a purchase.
- Limited Cross-Platform Support: This limits versatility for organizations with diverse IT environments.
The price tag of this platform makes it a good choice for medium-sized organizations looking to implement new security measures.
15. LevelBlue (formerly AT&T Cybersecurity)
Tested on: Cloud/SaaS
Best for Small to Medium-sized Businesses: LevelBlue offers managed security services with SIEM capabilities, ideal for smaller organizations seeking outsourced security expertise.
Price: LevelBlue doesn’t publish a price list; you need to request a quote.

As one of the more competitively priced SIEM solutions on this list, LevelBlue is a very attractive offering. At its core, this is a traditional SIEM product with built-in intrusion detection, behavioral monitoring, and vulnerability assessment. LevelBlue has the onboard analytics you would expect from a scalable platform.
LevelBlue USM Anywhere’s key features
LevelBlue prefers to call its system security offering an XDR. Its best features are:
- Intrusion Detection: Detects and alerts on potential security breaches and unauthorized access attempts.
- Behavior Monitoring: Monitors the behavior of systems and users to identify anomalous activities indicative of security threats.
- Open Threat Exchange: Utilizes a collaborative platform for sharing threat intelligence and information with other users.
- Scanning and Assessment: Scanns log files and provide vulnerability assessment reports based on devices and applications scanned on the network.
Unique buying proposition
LevelBlue USM Anywhere offers a comprehensive, cloud-based security solution that combines SIEM, asset discovery, vulnerability assessment, and threat detection. Its unique buying proposition lies in its unified platform, ease of deployment, and scalability, enabling organizations to enhance their security posture with real-time monitoring, automated compliance, and proactive threat response.
Feature-in-focus: LevelBlue USM Anywhere’s vulnerability scanner
LevelBlue USM Anywhere’s vulnerability scanner continuously identifies and prioritizes security risks across an organization’s network. It automates vulnerability assessment, providing actionable insights into potential weaknesses. The scanner detects and categorizes vulnerabilities. This work enables proactive risk management, helping organizations address critical issues before they can be exploited by attackers.
Comparitech SupportScore
LevelBlue is a new company, but it inherits financial stability from its former parent, AT&T. The business has 1,200 employees and so has plenty of staff for its Customer Support team. The USM Anywhere system is also well supported by online documentation and in-app help.
Overall, LevelBlue does very well in our SupportScore calculations, gaining a score of 93 out of 100.

Why do we recommend it?
LevelBlue offers a comprehensive Security Information and Event Management (SIEM) solution that integrates multiple security capabilities into a single platform. This unified approach simplifies threat detection, incident response, and compliance management, reducing the complexity and cost associated with deploying and managing multiple security tools.

Who is it recommended for?
LevelBlue USM Anywhere is recommended for small to medium-sized organizations, IT security teams, and managed service providers (MSPs) looking for an easy-to-deploy, cloud-based SIEM solution. This system will interest businesses seeking comprehensive threat detection, compliance management, and incident response capabilities with minimal infrastructure, offering scalability and real-time visibility into security events.
Additionally, LevelBlue provides continuous, curated threat intelligence from its Security Research Team, ensuring that users stay ahead of emerging threats.
16. Security Onion
Best for: A blended solution to security services
Price: Free

We at Comparitech have been following Security Onion for at least the past five years. The tool is primarily an intrusion detection system, and it is an open source project, so you can download and use it for free. The company can’t really charge for the software because it was developed by taking the code of other open source security systems and tying them together in a single dashboard.
Security Onion’s key features
Security Onion is a blend of many other security systems. Its key features are:
- Comprehensive Detection Tools: Integrates tools like Suricata, Zeek, and Sysmon for threat detection.
- Network Monitoring: Real-time monitoring of network traffic to identify suspicious activities.
- Intrusion Detection Systems (IDS): Provides intrusion detection capabilities using Suricata and Zeek.
Unique buying proposition
Security Onion can be seen as a compendium of security tools. It takes the best of its rival systems and unifies them with a single dashboard. The team behind the tool has developed other services to make money, and they include training, a hardware appliance, and professional support contracts.
Feature-in-focus: Security Onion’s hardware appliance
Security Onion’s hardware appliance offers an all-in-one solution for network security monitoring. It is loaded with the Security Onion software, which integrates systems such as Suricata, Zeek, and Elastic Stack, providing an easy-to-deploy, scalable platform. The appliance includes storage, so it relieves your servers from needing to provide space for log files and historical analysis reports.
Comparitech SupportScore
The organization that produces and supports Security Onion is also called Security Onion. This enterprise has evolved from an open source project to try to gain an income from a product that can’t be charged for. So, the group offers consultancy services and a sales team for a network appliance.
This means that the company has something of a split persona when it comes to customer support. The open source software makes a loss and the group isn’t going to deepen that deficit by spending money on technical support services – users have to rely on community support. However, the company does offer support for its network appliances. The open source nature of SecurityOnion means that it only gets a SupportScore of 4.5 out of 10.
Why do we recommend it?
We recommend Security Onion for its comprehensive, open-source security monitoring capabilities. It integrates powerful tools like Suricata, Zeek, and Elastic Stack, providing robust network monitoring, intrusion detection, and log management. Its scalability, user-friendly interface, and active community support make it an ideal choice for efficient threat detection and incident response.

Security Onion is an unusual product in that it provides many different tools in a bundle. However, the developers actually changed the code of the contributing elements to enable them to work together. Thus, it actually evolved into a new system. The tool will process log files but its main strength lies in its network monitoring services.
Who is it recommended for?
Security Onion is recommended for security professionals, SOC teams, and organizations of all sizes seeking an open-source, scalable solution for threat detection and network monitoring. The software is intended for those who need a comprehensive platform for intrusion detection, log management, and incident response, without relying on costly proprietary security tools.
Pros:
- Visualization Dashboards: Offers intuitive dashboards for easy monitoring and incident investigation.
- Alerting and Notifications: Provides real-time alerts to security teams based on detected anomalies.
- Full Packet Capture: Allows full capture and analysis of network traffic for deeper investigation.
Cons:
- No Version for Windows: Written for Linux.
The software for Security Onion was written for Red Hat Enterprise Linux (RHEL). However, it will also run on Ubuntu, CentOS, Debian, and Oracle Linux. You can load it onto an account with AWS, Azure, or Google Cloud Platform. Another option is to buy the Security Onion network appliance that has the software already loaded onto it.
Comparitech SupportScore Methodology
Our SupportScore assesses each B2B software vendor's likelihood of being able to effectively provide high-quality product implementation, as well as ongoing customer support and product support. While user experiences may vary, this analysis factors in 5 key signals that commonly influence a vendor's ability to support its products and customers.
Each vendor is different, so we recommend you utilize this data primarily as a way to encourage more meaningful conversations with chosen vendors. Our SupportScore factors in the following data:
- Total number of employees
- Revenue/funding
- Employee job satisfaction
- Identifiable customer success teams or employees
- Self-service documentation
These data points are calculated on a 0-100 scale, with variable weights based on category importance, and then averaged to produce an overall vendor score.
Check out our SupportScore Methodology post for a more detailed explanation of the SupportScore and why we believe it's a significantly important value-add while researching software vendors for your business.
What is SIEM?
SIEM (Security Information and Event Management) is an essential cybersec tool that collects and analyzes log data from your organization’s IT environment. It’s a centralized hub that can detect, analyze, and respond to security incidents. This helps your business proactively avoid damaging threats, including ransomware gangs.
Key Benefits of SIEM:
- Proactive Threat Detection: Identifies unusual behavior patterns to uncover potential attacks before they escalate.
- Centralized Visibility: Provides a unified view of security data across an organization’s infrastructure.
- Streamlined Incident Response: Enables faster reaction times to mitigate the impact of security breaches.
- Regulatory Compliance: Simplifies adherence to cybersecurity regulations with detailed log management and reporting tools.
- Enhanced Security Posture: Combines insights from historical data and real-time activity to fortify defenses.
Case study on the need for SIEM: Stuxnet
The now historically damaging malware Stuxnet is a prime example of why SIEM software exists and how it can be used to stop zero-day malware as well as other threats. Stuxnet, which Wired called “The World’s First Digital Weapon”:
“Stuxnet, as it came to be known, was unlike any other virus or worm that came before. Rather than simply hijacking targeted computers or stealing information from them, it escaped the digital realm to wreak physical destruction on equipment the computers controlled.”
Stuxnet arrived somewhere between the SIEM 2.0 and SIEM 3.0 eras, meaning many companies may have had SIEM in place, but many did not. Had adequate SIEM been around at the time, Iran’s nuclear fuel enrichment program may not have been ground to a halt.
Political intrigue and cyberweapon conspiracy theories aside, SIEM tools, alongside a robust matrix of intrusion detection systems (IDS), network segmentation, and, of course, regular system updates and patches, would likely have prevented one of the most dangerous pieces of malware from wreaking havoc on companies across the globe.
How SIEM works
SIEM works provides event information by analyzing data and integrating feedback to boost its machine learning algorithms. This improves the system’s ability to recognize and respond to threats in its environment. As it reads data from your network, it better understands the difference between normal and abnormal activity, allowing it to easily detect threats.
Key SIEM features:
- Threat detection and insights: Uses log data to identify attacks and provide a detailed understanding of how and why they occurred
- Adapts to complex IT infrastructures: Critical for modern organizations managing increasingly complex systems
- Addresses zero-day threats: Complements firewalls and antivirus tools by identifying threats that traditional measures miss
- Enhances compliance: Simplifies log management to meet industry-standard regulations and improve network transparency
- Prevents damage: Differentiates between legitimate and malicious activities to enhance system protection and minimize risks
Do SIEM Tools provide dashboards?
Yes, SIEM tools provide dashboards. In fact, the SIEM dashboard is one of the key features that you should be looking for and evaluating as part of your software buying process.
As far as SIEM dashboards go, the most important features include:
- Real-time threat monitoring and alerts: The ability to display and flag potential security threats in real-time
- Log aggregation and analysis: Centralized collection and correlation of log data from multiple sources
- Customization: Flexible interfaces that allow users to tailor views to their needs and priorities
- Threat intelligence integration: Incorporation of external threat data for better context and detection
- Incident response tools: Built-in features for investigating and responding to security incidents efficiently
- Compliance reporting: Automated reports to demonstrate compliance with regulatory standards
- User and entity behavior analytics (UEBA): Insights into unusual user behavior patterns to identify insider threats.
- Drill-down capabilities: Easy navigation from high-level views to detailed logs and event data
- Anomaly detection: AI-driven tools to detect deviations from normal patterns.
- Performance metrics monitoring: Real-time visibility into system performance and health
You purchasing process should take into account whether each tool’s dashboard includes the data you need, or has the ability to include that data.
Why Are SIEM Tools Important?
SIEM tools are important because of their ability to detect and prevent threats within modern organizational IT infrastructure. By analyzing log data from users, devices, and trackers, SIEM provides insights into past attacks, detects ongoing threats, and ensures compliance with industry regulations.
Key features of SIEM:
- Threat detection and insight: Uses log data to identify attacks and provide a detailed understanding of how and why they occurred.
- Adapts to complex IT infrastructures: Critical for modern organizations managing increasingly complex systems.
- Addresses zero-day threats: Complements firewalls and antivirus tools by identifying threats that traditional measures miss.
- Enhances compliance: Simplifies log management to meet industry-standard regulations and improve network transparency.
- Prevents damage: Differentiates between legitimate and malicious activities to enhance system protection and minimize risks.
As IT systems and threats targeting them grow more complex and security threats, SIEM has become a must-have solution. The explosion of zero-day attacks and the limitations of traditional security measures highlight the need for advanced threat detection and response capabilities. Additionally, with increasing regulatory demands, SIEM provides organizations with the type of transparency and compliance assurance they need to safeguard their systems, data, and finances.
Why trust us?
The team at Comparitech boasts extensive practical experience in technology, with experts specializing in IT systems, cybersecurity, and software solutions. The staff includes professionals with backgrounds in network administration, system architecture, and data security, providing them with technical knowledge to assess and evaluate a wide range of IT systems. This expertise ensures accurate, insightful reviews and recommendations, establishing Comparitech as a trusted authority in technology assessments.
Our methodology for choosing SIEM tools for automated security alerts
At Comparitech, we follow a rigorous and comprehensive methodology to evaluate SIEM tools for automated security alerts. Our approach ensures that only the most reliable and effective solutions are recommended to our users. Here’s an outline of our process:
1. Feature Set Evaluation
We assess the range of features offered by each SIEM tool, focusing on essential capabilities such as real-time monitoring, automated alerting, incident response, data collection, and analytics. We prioritize tools that offer flexibility, scalability, and ease of integration with existing IT infrastructure.
2. Ease of Use and Deployment
A tool’s usability is a key factor in our evaluation. We examine how intuitive the interface is, as well as the ease of installation, configuration, and deployment. Tools that require minimal training and reduce the burden on security teams are highly valued.
3. Accuracy and Alert Management
We look closely at the tool’s ability to minimize false positives and accurately detect genuine threats. SIEM tools that incorporate advanced analytics, machine learning, and customizable alert thresholds to reduce alert fatigue are preferred.
4. Performance and Scalability
We test the scalability of SIEM tools to ensure they can handle growing data volumes and evolving network demands. Tools that maintain performance and responsiveness under heavy workloads are favored.
5. Integration with Other Systems
Effective integration with existing IT infrastructure, including firewalls, endpoint protection systems, and cloud environments, is a top priority. We review how seamlessly each SIEM tool can be incorporated into various organizational ecosystems.
6. Support and Documentation
Comprehensive vendor support, user manuals, and troubleshooting resources are crucial. We assess the quality and availability of customer support, as well as community-driven resources like forums and FAQs.
7. Cost-Effectiveness
We analyze the total cost of ownership, considering initial licensing fees, subscription costs, and any additional expenses for training, maintenance, or support. Our focus is on finding tools that offer strong ROI relative to their pricing.
8. Security and Compliance Features
For organizations that must comply with industry regulations, we evaluate each SIEM tool’s ability to help meet security and compliance standards, such as GDPR, HIPAA, or PCI-DSS, through features like automated reporting and secure log management.
By following this methodology, we ensure that the SIEM tools we recommend provide comprehensive security, operational efficiency, and long-term value for businesses looking to enhance their cybersecurity posture.
Broader B2B Software Selection Methodology
At Comparitech, our approach to selecting B2B software tools is systematic and data-driven, designed to help businesses identify solutions that best align with their operational needs, objectives, and budget. We leverage industry expertise, hands-on testing, and user feedback to ensure our evaluations are thorough, accurate, and insightful. Here’s a breakdown of our broader B2B software selection methodology:
1. Identifying Business Needs and Goals
Before assessing any software, we start by understanding the core business challenges and objectives of our target audience. Whether it’s improving efficiency, reducing costs, or enhancing security, we identify the specific needs that each piece of software must address, ensuring that the recommended solutions align with organizational goals.
2. Comprehensive Feature Analysis
We conduct a detailed review of each software’s feature set, evaluating both essential and advanced functionalities. This includes assessing ease of use, customizability, integration capabilities, and the overall value each tool brings to the table. We prioritize features that contribute directly to solving real business problems.
3. Vendor Reputation and Reliability
We consider the reputation of the software vendor, examining their history in the industry, customer reviews, and their track record for delivering on promises. Established vendors with proven reliability and a commitment to product updates and improvements are prioritized.
4. Usability and User Experience
User experience is key to successful software adoption. We evaluate how intuitive and user-friendly each solution is, looking at aspects like interface design, ease of implementation, and the level of support needed for onboarding. Software with a low learning curve and good training resources is preferred.
5. Scalability and Flexibility
The ability of software to scale as a business grows is crucial. We assess how well each solution adapts to different organizational sizes and complexities, from startups to large enterprises. The flexibility to customize the software to specific business requirements also plays a key role in our evaluation.
6. Performance and Reliability Testing
We rigorously test the software’s performance, stability, and ability to handle large volumes of data or users. We consider factors such as uptime, response times, and the efficiency of the software in real-world use cases to ensure it delivers reliable performance under various conditions.
7. Cost-Effectiveness and Pricing Models
Understanding the total cost of ownership (TCO) is an integral part of our methodology. We assess the upfront costs, subscription fees, and any additional charges for support, training, or add-ons. We prioritize solutions that provide strong ROI while remaining affordable for businesses of different sizes.
8. Security and Compliance
Security is paramount in today’s digital landscape, particularly for businesses handling sensitive data. We evaluate each software’s security features, including encryption, data protection measures, and compliance with industry regulations (such as GDPR, HIPAA, or PCI-DSS). Tools that offer robust security and help businesses maintain compliance are highly valued.
9. Customer Support and Resources
The level of customer support and available resources is essential for ensuring a smooth experience with any software. We assess the quality of vendor support, including availability, responsiveness, and the range of support options, such as online guides, forums, and direct assistance.
10. Feedback and Reviews from Actual Users
We rely heavily on the experiences and feedback of actual users. Our evaluation includes analyzing third-party user reviews and conducting in-depth interviews with customers who use the software. This provides us with a clearer understanding of the software’s strengths and any potential limitations.
You can learn more about this strategy in our B2B software methodology page. By following this comprehensive methodology, Comparitech ensures that the B2B software solutions we recommend are not only effective and reliable but also tailored to meet the unique needs of businesses across various industries.
Related Posts
The following content offers additional insights on SIEM and network security:
- Everything You Need to Know About SIEM
- Best Free and Open Source SIEM Tools (great for small and medium-sized businesses with a limited budget!)
- SIEM Alert Guide
- Best Managed SIEM Services
- The Best Endpoint Detection and Response Tools


























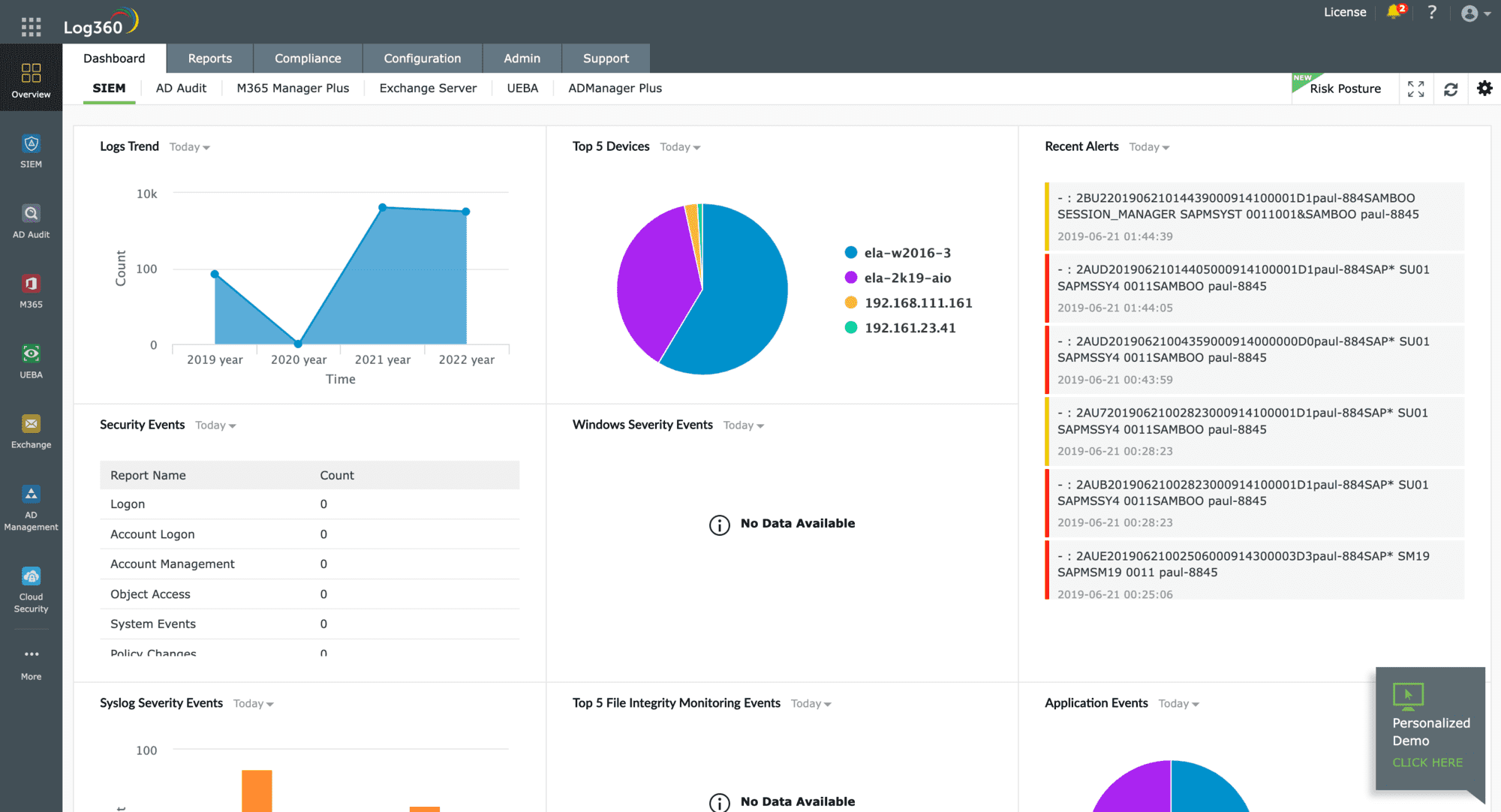
IBM QRadar has always ran on Linux and has been on RedHat Enterprise Linux for several years. Current version is RHEL 7.6. ArcSight is shouldn’t be recommended as R&D has pretty much come to a halt and most customers are migrating away from it besides the expense and overhead required to maintain the infrastructure.
Thanks for the heads up! We’ve changed that now.
The SolarWinds SEM requires an agent that installs Java.
Tim,
What isn’t discussed here (and by the way nice analysis of the tools) is what platforms (SaaS,PaaS,IaaS, hosted enviornments) that the SIEMs work with or not. This is an open issue with most tools.
Sarah
Best explanation on SIEM and SIEM tools. Difference between SIEM, SIM and SEM well explained in short.
The top 8 Tools under SIEM belt with the OS on which they can be installed and run for threat detection and threat analysis.
Thank you.
Awesome conceptual details about SIEM tools. Missed one opensource SIEM tool here OSSEC
Good information: Thanks for the education.