Our security research team has uncovered a critical vulnerability in the popular WordPress plugin WP WebinarSystem. Due to a flaw in their code, it is possible for attackers to store and execute malicious code on any server running this plugin. We recommend all users update immediately.
What is WP WebinarSystem?
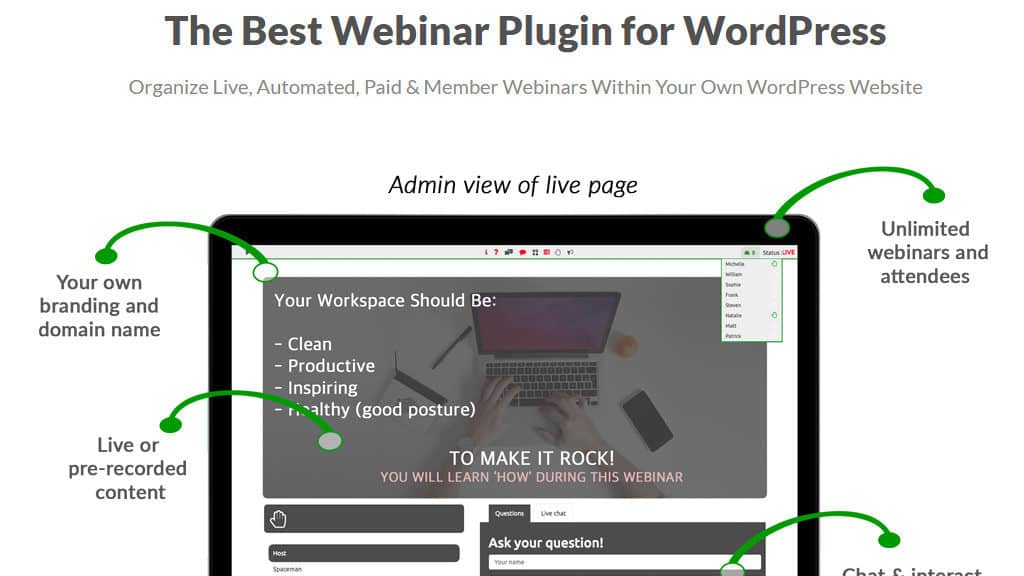
WP WebinarSystem is a WordPress plugin developed by KnockoutSoft Ltd. for the purposes of coordinating and hosting online webinars. The plugin makes it easy for users to “Organize Live, Automated, Paid & Member Webinars Within Your Own WordPress Website.”
It’s currently the most popular webinar plugin on WordPress, with over 40,000 active installations according to the manufacturer. WP WebinarSystem was first released in August of 2015. It offers both paid and free versions.
What is stored cross-site scripting?
A stored cross-site scripting (XSS) attack occurs when an application allows a malicious script to be injected and executed by a website or application. Stored XSS attacks are defined by the fact that the malicious code is stored by the vulnerable application, becoming a persistent feature which can be executed over and over.
Stored XSS attacks are particularly dangerous, since they may put a wide range of user data at risk. In particular, the entire DOM of the site can often be read or altered, along with a user’s session cookies.
WP WebinarSystem Critical Vulnerability Disclosure
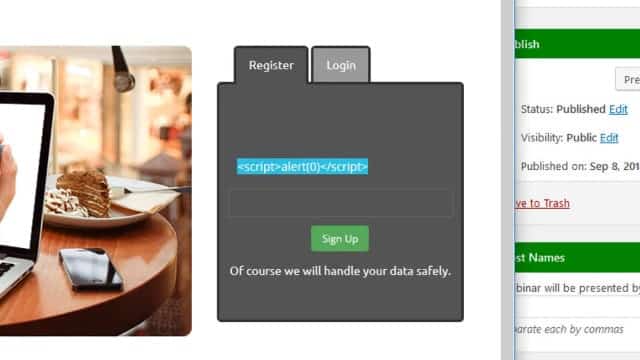
Our research has shown that WP WebinarSystem version 1.14 is vulnerable to a stored XSS attack, due to a lack of filtering in the email field of the signup form.
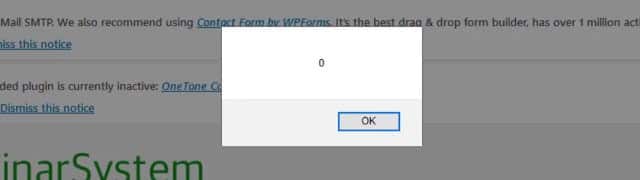
An attacker can enter malicious code in the email field, which is then run when the webinar creator browses the list of users that have signed up for the webinar.
We further believe that the malicious code is run with the privileges of the user managing the webinar, which means attackers are able to steal session cookies, potentially granting them complete control of the WordPress server.
We are confident in our determination that this is a critical threat, and urge all users to update to the latest version of WP WebinarSystem immediately.
Which versions are affected?
All versions prior to 1.14 and the corresponding paid releases are affected by this vulnerability. If you’re a free user, download an update from the WP WebinarSystem website immediately. Paid users should update the plugin from their WordPress dashboard.
Disclosure and response timeline
- We reported the vulnerability on October 6th, 2018.
- KnockoutSoft Ltd. replied to the report on October 7th, and we provided additional details and a proof-of-concept video.
- An update to the free version of WP WebinarSystem was issued on October 10th.
- An update to the paid version of WP WebinarSystem went live on October 20th.
- We published this disclosure on December 11th.
As you can see, KnockoutSoft Ltd. responded quickly to our disclosure and issued updates in a timely manner. There is no indication that the vulnerability was exploited by malicious actors in the meantime.
When asked for comment, “We take security very seriously and would like to thank Comparitech for bringing this issue to our attention.”
Has my WordPress server been affected?
It’s very hard to know for sure. But some of the warning signs you might look out for include:
- Odd or malformed names in the list of webinar participants
- Warnings or notifications that an unexpected script is trying to run
- Access from unknown IP addresses in your WordPress logs
But keep in mind there may be no signs at all. Hackers can craft a username that causes malicious code to be executed without changing the appearance of the name in the list of participants, without triggering a warning about unexpected scripts, and without leaving a trace in your WordPress access logs.
Update WP WebinarSystem to protect your site
KnockoutSoft Ltd. released an update for paid users which you should install through the WordPress dashboard. They have also released an update to the free version of the plugin which you can download from WordPress here.