Many teachers make use of the internet to provide class materials and information, but it can be hard to both be on the internet and also maintain some sort of privacy. Information is inherently neither good nor bad and is spread with the same efficiency regardless. In addition to that peril, the internet can and is used by students to stalk teachers and the reverse is also true. This online privacy guide for teachers contains some pointers on how to maintain a separation of personal and professional life online.
Social media
Some schools outright forbid students and teachers from connecting on social media. Depending on the social media platform, that may or may not be enough to maintain separation. Some social media platforms like Twitter don’t require any sort of connection to read a person’s Tweets unless the account is locked down.
Use friend lists
The original incarnation of Facebook had one concept of connecting people: you were “friends” in the normal human way. Facebook originally strove to mimic those real relationships online but the concept of two-way friending isn’t really an accurate portrayal of human friendships.
Not all of our friends are interested in the same things. There are friends that would go to a sci-fi movie with me, and there are friends that would prefer to go to yard sales with me. It’s also important to recognize that we have deeper levels of friendships with some people that others. While it is OK if everyone knows I was recently promoted at work, I would only want a small subset of people to know about some other, more personal matter. For these reasons, and probably others, Facebook introduced the concept of segregated friend lists in 2007.
You can create friend lists within Facebook and then assign your friends to those lists. Using the example in the previous paragraph, some people may have an ‘acquaintance’ list that promotion messages can go to, and then a ‘family list’ that personal messages should be limited to. It’s not too far of a stretch to see how you can also create a ‘class’ or ‘students’ list to filter what information should go to those groups. One thing to keep in mind is that your Facebook privacy option will usually remain set to the last friend list you published to. This can cause problems if you forget to change that when you post next.
Use a Page or Group rather than friending students
Around the same time, Facebook introduced the concept of Pages which was originally aimed at businesses. A business is able to create a page which Facebook users can follow with the important distinction that the followers of the page do not become the page owner’s Facebook friend. This introduced a much needed level of separation on Facebook and continues today. However, Pages are public by default which may not be what you want.
Facebook Groups have been around in some form since nearly the beginning. Groups have better privacy settings than Pages and are probably more suitable for a teacher/class type scenario. Creating a Facebook group for your class or students is a reasonable way to provide information to them without opening up your entire Facebook world to them. It’s also easier to “get it right” when posting to your group than it is when posting to your personal Facebook. When doing the latter, it’s important to check the friend list you’re posting to each time to ensure you don’t post to the wrong friend list.
Regardless of the method you chose, it is important to remember that you only have control over what you post. You have little control over what other people post, or what Facebook reveals to your friends through its algorithms. To protect against the latter, a group is the better way to go.
Watch your commenting
Commenting is especially complicated on Facebook. If you comment on a friend’s post, other people may see that post even if they are not your Facebook friend.
If you comment on a public post such as a public newspaper page, your comment can be seen by the general public. This has the potential to transmit information you want to keep private such as your views on a topic, or perhaps even the fact that you follow that page at all.
Consider your user name
It’s worth noting that Facebook specifically states that your name must be the one you use in “everyday life”. Anecdotally, it seems pretty clear that this policy is not enforced and it seems fairly easy to get by with some mild obfuscation. Using your middle name as your last name, for example, can be enough to foil casual stalkers without treading too far across the naming policy.
Enable your timeline review
Facebook has a feature that allows you to review posts you’ve been tagged in before they show up in your timeline. It’s called timeline review and while I have it enabled, it’s not a silver bullet. Timeline review ensures that content you’re tagged in can’t appear on your own timeline without your approval. It does nothing to stop people from posting the content in the first place on their own timelines and Facebook specifically states that the content may still show up in “other places on Facebook”.
Related: 15 Facebook privacy and security tips
Twitter and instagram
Twitter and Instagram are much less complex than Facebook which brings some benefits and some disadvantages. Twitter is excellent for immediate, time sensitive information such as school closures or moved assignment deadlines, but less useful for more detailed information. Instagram may be useful if your class has a large visual component, but it’s not terribly good at getting feedback or publishing complex information. However, either may be useful for your particular needs.
Use of a handle
Using a generic handle that has nothing at all in common with you is a good start. If you’re trying to hide that you’re a teacher, stay away from handles that make people think of schools or teachers. Likewise with your profile picture. If you’re an English teacher, using a dictionary as your profile picture can lead people into figuring that out. If you’re really stuck you can use a handle generator – but it’s best to pick from the generic names already listed than specifying details about yourself. Doing the latter will just end up generating a handle that may identify you.
Lock down your account to approved followers
Unlike Facebook’s options to target your posts via a page or friend lists, Twitter and Instagram have an “all or nothing” approach to account privacy. You can simply lock down your account to approved followers, or have your account open to the public.
To do this in Twitter, click your profile icon and go to the Settings and Privacy option.
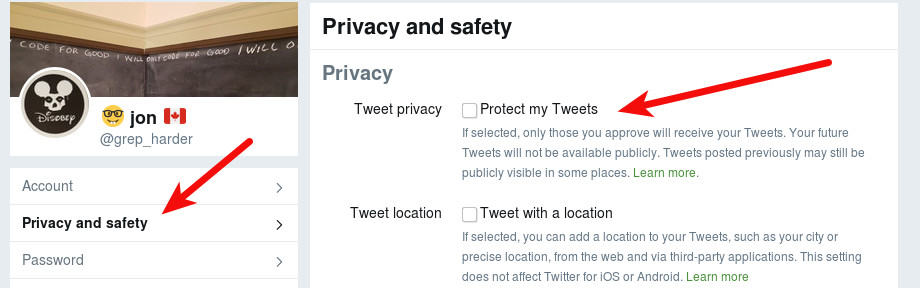
The select the Privacy and Safety option and click the Protect my Tweets option.
For Instagram, you’ll need to use the app. Click the profile button (the head and shoulders icon), then the three dots in the top right corner to open the Options menu. Scroll down to Account, and enable the*Private Account* option.
Even if you opt to lock down your account, keep in mind there’s nothing stopping those followers from finding creative ways to share your content anyhow. The easiest way to circumvent any privacy control is for an approved follower to take a screenshot of your post and then re-publish it more publicly.

The internet in general
Professor and school rating sites
There are some educational rating sites on the internet such as Rate My Professors. This type of site allows students to rate their experience with teachers and schools. Unless someone posts something slanderous about you, there’s not much that can be done about these sites. But, it is good to be aware that they exist and may contain information that you did not necessarily want on the internet.
School websites
Some schools provide each teacher or each class with a website to use for course material. Using this page is probably the best solution for privacy since it’s wholly separated from your personal life and contained with the hierarchy of the school network.
Most schools have professional I.T. staff whose duties usually include running the internal website infrastructure. Since the school has a vested interest in being seen as secure and reliable, you may find better security controls and backups built into school sites.
Compartmentalized school websites also have the advantage of providing students with a specific way in which to contact you and submit assignments. Using your personal email for such things can lead to data leakage that can end up sharing information you didn’t intend to with students.
Personal websites
Some of us have personal passions that have little or nothing to do with our professional work. In doing so, we may also maintain a personal website which can be hard to hide from inquisitive eyes. If you have such a website and you don’t want students finding it, you have a bit of a challenge on your hands.
Private domain WHOIS information
Register your domain name at a registrar that offers WHOIS privacy. WHOIS is exactly what it sounds like; it is a tool that answers the question “Whois the owner of this domain?“. The Internet Corporation for Assigned Names and Numbers (ICANN) is the body that oversees the registration of domains names worldwide. Among other requirements, it insists that domain owners can be contactable via information available in a domain’s public WHOIS listing. This doesn’t technically mean that your own personal information has to be listed in the WHOIS database; many registrars offer WHOIS privacy as an add-on during domain registration. This will change your domain’s public WHOIS information to something generic, although the registrar is required to relay emails to the domain owner. Some Top Level Domain (TLD) domain registrars do not publish domain ownership records by default such as the Canadian .CA registrar. To contact a .CA domain owner, you’ll usually need to fill out a form that does not divulge anything.
If you’ve already registered a domain without WHOIS privacy, it’s best to discard that domain and not use it for a private project. This is because domain ownership history is usually traceable which can reveal you as a previous owner of a domain.
Stylometry
Generally considered an advanced investigative technique, stylometric analysis would be easier when used against a teacher. Styolomery is the analysis of linguistic style. It is typically used to correlate works of an unknown author against works of known authors with an aim to identifying the unknown author.
The more work of the known author, the greater the degree of success. This is because we can all change how we write some of the time, but it’s hard to change how we write all of the time. Teachers tend to have a huge and publicly available trove of writing which makes this type of analysis easier to do with less skill required.
Advanced paranoia
Hiding your WHOIS information and taking care to obfuscate your writing style is usually enough to fend off mildly determined adversaries. If you’re more determined to stay hidden then there are other things to consider.
Hiding DNS records
A common tactic used to uncover web site owners is to identify the hosting provider and issue DMCA or abuse complaints to the host. Some hosts will give up the web site’s owner information without too much a fight; others will fight tooth and nail to protect it. If your site does actually infringe on someone’s copyright, or break the laws in some countries, your web host may find themselves compelled to provide your contact information.
The best defence against this is to hide your DNS records to avoid your hosting provider from being discovered in the first place. There are several web proxy companies that can forward traffic for you, which means your DNS records would only reflect the proxy service and not the actual web host. These proxy services can also be compelled to provide your hosting information, but in general they are more privacy oriented and usually insist on properly filed and supported documentation before doing so.
Also keep in mind that domains usually have more than one DNS record. Domains usually have Mail eXchange (MX) records, and it’s not unusual for web hosts to create a set of default DNS records such as ‘cpanel’ or ‘ftp’. DNS records must be publicly available in order to function, and an adversary that knows this can query the DNS system for those common records to see if they exist. If those records do exist and they point directly to your hosting IP address, then your adversary has discovered your web host even if you’re using a proxy service. A site like DNS Dumpster can give you a sense of what DNS records are exposed for your domain.
Do not send mail from your web server
Most people buy a hosting package and set up their website as well as their email in that package. Email presents a special problem because there are hidden headers in emails that contain a lot of information. Email headers will contain the path the email took through the internet which includes the originating IP address. If you’re serving email from your web server, then your web server’s IP address will be listed as the originating IP address.
Return-Path: <v-bbcppbj_cdlnophcce_ebjepmha_ebjepmha_a@bounce.mkt3772.com>
X-Original-To: your@emailaddress.com
Delivered-To: your@emailaddress.com
Received: from mail3176.maritzcanada.mkt3772.com (mail3176.maritzcanada.mkt3772.com [208.95.133.168]) by mail.youremailhost.com (Postfix) with ESMTP id 434923000343 for <your@emailaddress.com>; Wed,6 Sep 2017 00:50:52 -0400 (EDT)In the example above, we can see that this email was sent from a mail server named mail3176.maritzcanada.mkt3772.com which has the IP address 208.95.133.168. Another variation on a domain WHOIS is an IP address WHOIS which shows the owner of an IP address. Using that, I find that this IP belongs to IBM which starts me down the road to identifying who has control over that particular server.
To make this work, your adversary has to get your domain to send an email to them. If you have a contact form or other type of form on your site that has the ability to send an email to a user, that can be used for this purpose.
Create a darkweb site
While Tor is not as anonymous as most people think, it still represents a fairly challenging obstacle to non nation-state adversaries. If you’ve ever set up a website before, you’ll only have to learn a few extra skills to set up a hidden Tor onion site. The bad news is that this means your visitors will also have to know how to use Tor. Depending on your intended audience, this may or may not be a problem for you.

After the fact
If you’ve discovered information online about you that you’d like removed, the first course of action should be to contact the site owner. If there is no contact information on the site itself, use a WHOIS lookup to see if you can find the site owner’s information that way.
If the information is on a social media site, each maintains its own method of requesting removal. Facebook’s privacy rights violation report form allows people to submit content that they wish removed but does not guarantee it will happen.
Likewise, both Twitter and Instagram have their own privacy violation reporting mechanisms. For any other social media site, searching for the phrase privacy right violation report and then the social media site’s name should bring you to the right place.
If you can’t get the information removed, you can try getting it removed from the search engines. The internet is a very large place and people rarely just stumble across sites. Most of the internet is discovered via the major search engines so removing content from a search engine (called de-indexing) is almost as good as removing the original content. Google accepts de-indexing requests here and will contemplate removing information such as personal banking information and personal images that were shared without your consent.
Don’t forget about the other search engines such as Bing and Yahoo. While they are much less used than Google, you should also attempt to get your data de-indexed from every search engine you can.
Some people will say that the only real way to defend your privacy in today’s online world is to stay offline entirely. That shows a basic misunderstanding as to how information gets online. You can only control what you put online, you have no control over what other people put online. Many organizations publish member information without consultation, and news stories frequently carry the names and details of members of the public. Ignoring the internet simply means that you’ll be unaware that this information exists and unable to take action to correct it.


Please review the Windscribe VPN please.
It’s on the list to do!