The popular internet privacy service NordVPN published a blog post earlier this week denying allegations that they are harvesting user data and operating a botnet through their VPN client. Nord invited their users to see for themselves that there’s no validity to the charge by using Wireshark, so I took them up on it. Here’s how you can do the same.
The legal filing against Tesonet
Apparently a recent lawsuit kicked off Nord’s campaign to defend themselves from their online accusers. The suit, which was filed in Texas court against Nord’s partner Tesonet, alleges that NordVPN ripped off a competitor’s technology and used it to build a botnet that would force Nord users to act as exit nodes.
Correction: An earlier version of this article incorrectly stated Hola’s lawsuit was against NordVPN. The lawsuit was filed against Tesonet, a partner of NordVPN.
The company that Tesonet allegedly stole from is none other than Hola, who made news in 2015 after it was shown that the formerly-popular free VPN provider had an insecure backdoor in their VPN client, among many other things. This is significant, because Hola’s fall from grace was major news at the time, and if Nord were doing the same thing it would seriously tarnish their credibility.
So I fired up Wireshark and discovered that Nord is absolutely not engaged in building any sort of botnet, and clearly is not doing what Hola did and continues to do.
Checking for a Hola-style malware botnet
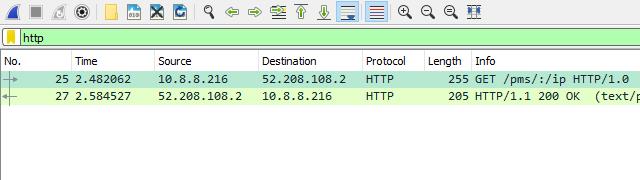
In order to come to that conclusion, I connected to the NordVPN client and started Wireshark. I set Wireshark to capture traffic on the encrypted connection that Nord creates when it’s installed.
I let the session run for five minutes with Chrome closed to ensure that any traffic being generated was coming from a system service and not my own browsing. You can see from the capture that my private IP address is in the 10.8.8.0 subnet, which is what Nord’s clients use.
Over the course of those five minutes, Plex media server, which I have installed and running, exchanged a message back and forth with the plex.tv backend.
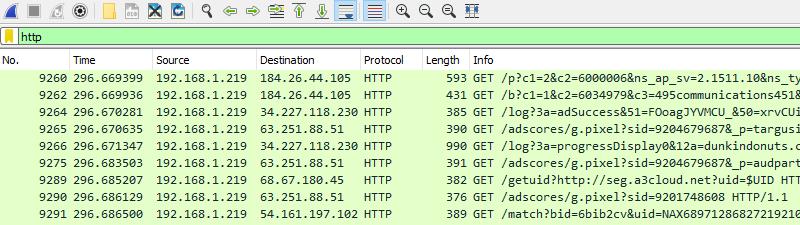
I also tested the current version of Hola, so I could see for myself if the traffic matched up with the allegations in the lawsuit. I ran the capture in exactly the same way, five minutes with my browser closed.
A minute or so after the installation was complete, Hola started sending requests from my computer to the web. It mostly hit advertising servers, which makes me wonder whether or not Hola’s paying customers—the ones with access to free VPN users’ bandwidth—may be using Hola to inflate their own ad revenue.
Regardless, you can see the difference. In my opinion, there is absolutely no way that NordVPN is running a botnet using Hola’s intellectual property.
Does that really mean they aren’t spying on you?
Some other VPN providers have been accused of sniffing their users’ secure connections and providing the information to law enforcement. No allegations of monitoring connections in this way have been leveled against Nord, but I was already checking things out so I decided to see for myself.
Checking for promiscuous mode with NMap
NMap ships with a script called sniffer-detect that sends malformed ARP packets to a host, then reports whether or not these packets were rejected.
A network adapter running in promiscuous mode will behave oddly in some circumstances, saving packets that would otherwise be rejected, because the driver is instructing the network adapter to pass all traffic along to the CPU for logging.
Note that I used a custom version of the script which I changed to make it display results even if the host isn’t running in promiscuous mode. In the original version, secure hosts display no results.
NordVPN doesn’t seem to be collecting user data
Based on my testing, I don’t see any evidence that NordVPN is harvesting user data or running a botnet. The lawsuit seems to me to be baseless, and part of a broader smear campaign against NordVPN.
I reached out to Nord for comment and asked them about the recent allegations. Here’s what I was told:
“Hola VPN used their clients as an exit nodes to perform a web scraping. That means that users’ devices were used as proxies to send requests to the desired websites. Such behaviour can easily be checked and verified, all requests made by our apps are required for the service to properly operate, that’s it. NordVPN users have never been abused in any way, their traffic was never logged at any point of their connection.”
I also pushed them for clarification as to what ‘no logging’ really means, and Nord’s spokesman told me, “We do not log any traffic nor connection logs at any point, nor app, nor server level, nor anywhere in between. We don’t even troubleshoot our servers if something happens. If we’re noticing that any of our supported protocols aren’t working as they should, we immediately remove a server from production and only then investigating the issue.” [sic]
In my opinion, NordVPN is completely safe to use. But if you’re on the fence, install Wireshark and see for yourself. When you look at NordVPN and Hola side-by-side, the difference is clear.
Disclosure: NordVPN is an affiliate of Comparitech. Read more.








Sorry for being late on the topic but please could you tell me when the traffic from hola vpn started to appear and if there was any interaction with the mouse or keyboard from your end.
No interaction needed, traffic starts as soon as a certain Hola process is spawned and continues until Hola is uninstalled
Hi Aaron, I appreciate you taking time to actually run some tests before writing about this. I find it very interesting how some sites wrote articles to actually confuse people rather than explain things in a simple way. Anyway, what I saw today on Reddit caught my eye because it’s a completely different perspective on things. You can find it here: https://old.reddit.com/r/privacytoolsIO/comments/9d8szc/the_dark_side_of_the_vpn_industry_is_the_current/. Any thoughts about this?
It’s hard to believe that companies are going this far, making their hands dirty just to help their businesses, madness right? Anyway, your link doesn’t work anymore, I guess the article got deleted for some reason, but I found it in the archive here https://web.archive.org/web/20180906104637/https://medium.com/@derekjohanson_17934/the-dark-side-of-the-vpn-industry-a-different-look-into-the-nordvpn-data-mining-claims-c71082c53dcb
Restore Privacy called you guys out for publishing false information:
https://restoreprivacy.com/lawsuit-names-nordvpn-tesonet/
Hi David, thanks for sharing.
“But we must make something clear: there is no proof or allegation that the NordVPN app itself – or ProtonVPN for that matter – resells users’ bandwidth. While the lawsuit directly mentions NordVPN, Tesonet may well have embedded the software that enables the residential proxy network in apps other than NordVPN.”
I disagree with their definition of clarity in this case. The overwhelming implication in this matter is that NordVPN is behaving like HolaVPN. It’s not.
More debate is happening here: https://www.reddit.com/r/nordvpn/comments/9cui5r/nordvpn_is_not_running_a_botnet_heres_how_you_can/
I’m not eager to let bad actors spam these comments, so I’ll be containing the obvious trolls to Reddit and responding there as I’m able.
The assertions I’ve made in this article are very straightforward and backed up by evidence, but some have seized on the fact that we are a Nord affiliate to accuse Comparitech of acting as offsite PR for Nord. In truth, we’re an affiliate reseller of a lot of different VPN providers, and I’m not under any special obligation to defend NordVPN.
But the evidence against these claims is clear and obvious, and I stand by my work. I’m not going to see it undercut by people with a clear agenda for or against any particular VPN provider.
https://www.reddit.com/r/nordvpn/comments/7oqs4n/why_is_nordvpn_nordvpnservice_trying_to_connect/
Hi, thanks for reading.
What you’re seeing is Nord hitting a given domain to see if it has access. This is called a resiliency URL. If Nord can’t access that URL from your location, my understanding is that it switches servers until it can access it.
These URLs are only accessed when you’re browsing the web, which is much different than the way Hola behaves as you can see from my reproduceable testing above.
One way you can tell the difference between the way NordVPN makes use of resiliency URLs and how HolaVPN acts as a proxy is to use Wireshark to view the URL. HolaVPN typically hits ad beacons, while Nord will attempt to connect to the index of a website.
You can see a full list of Nord’s resiliency URLs under the Memory Forensics section here: https://www.reverse.it/sample/db1e8a649088cff15c86e3b56fd6e19862be9ce94b057c608c838cc1ecdf91ca?environmentId=120
I’d also point out your question was previously answered on Reddit here: https://www.reddit.com/r/nordvpn/comments/9cew69/little_snitch_reveals_nordvpn_wants_to_connect_to/