A database containing nearly 3 million records belonging to grocery rebate service SavingStar was left exposed on the web. Comparitech security researcher Bob Diachenko uncovered the unsecured MongoDB instance, which was left open to anyone with an internet connection.
We immediately notified SavingStar upon discovering the exposed data, which contained scanned receipts and customer data. SavingStar secured the database shortly thereafter.
SavingStar is a free app for iOS, Android, and the web that lets users link their grocery store loyalty cards, get rebates, and store the savings in their SavingStar account.
Timeline of the data leak
The MongoDB database was accessible to the public with no password or other authentication required.
On August 4, 2019, the database was first indexed by search engines. We discovered it two days later.
On August 6, after determining who owned the database, Diachenko immediately notified SavingStar. SavingStar took action to secure the database within a few hours on the same day.
The company responded by email to confirm:
“Upon learning of this incident, we immediately undertook an investigation to identify and remedy the root cause. Our investigation revealed that after a recent patch update, a firewall issue inadvertently exposed limited data for about two days. We have no evidence that any data was removed from this database, disseminated or otherwise misused, and within hours of discovery, we corrected the issue so that there is no longer a vulnerability. Maintaining the security and confidentiality of our data is a critical part of who we are and we take that responsibility very seriously.”
What information was exposed?
The records contained a variety of information, but the bulk of the data is comprised of scanned receipts and a list of users who used Facebook to log in to the app:
- More than a million links to scanned receipts stored on an AWS S3 bucket
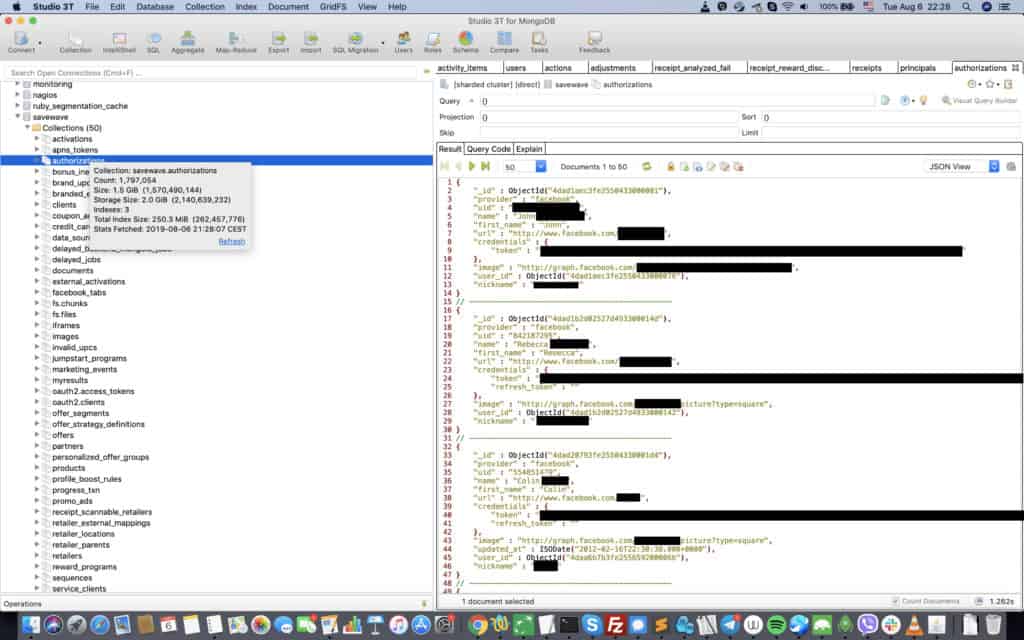
- 1,797,054 Facebook-authorized users (full name, nickname, Facebook profile URL, login token, image link)
- 3,771 credit card profiles (no payment details)
We also found a small number of user records that SavingStar says is “internal data” and “not associated with any of our members:”
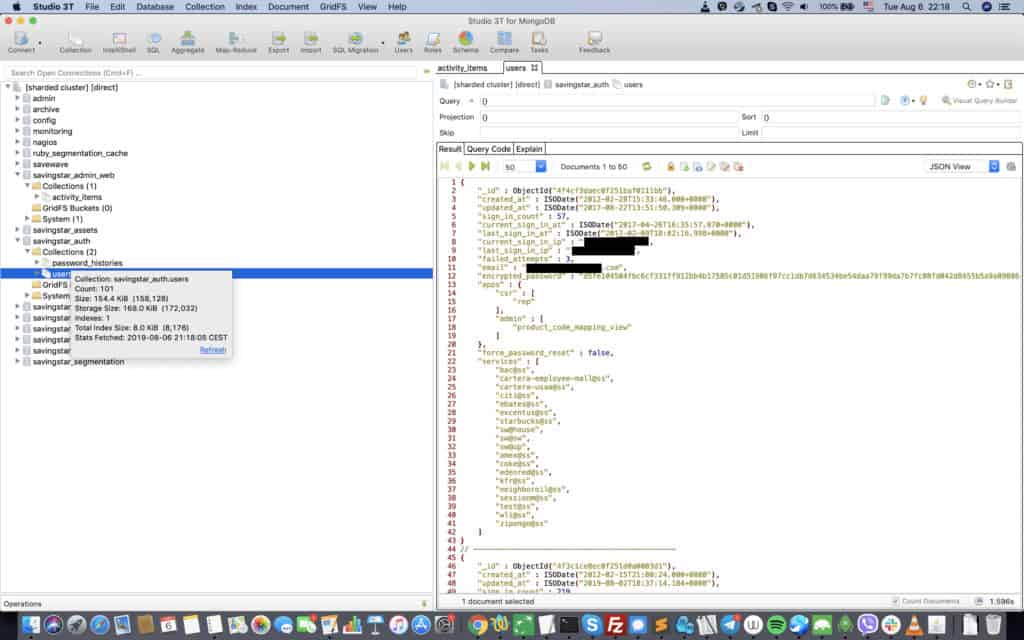
- 101 authorized users’ data (sign-in IP address, email address, and encrypted password)
- 189 records with passwords histories
Diachenko says the receipt scans were stored on a separate Amazon S3 bucket. General access to it was disabled, but the receipts could be accessed through direct links listed in the MongoDB database.
Receipts vary from merchant to merchant, but they typically include:
- Date and time of the purchase
- Items purchased and price totals
- Name and location of the business
- Sales tax
- Payment method
- Return policy
The credit card profiles did not include any payment details such as credit card numbers, expiration dates, or CVV numbers.
We do not know whether anyone else gained unauthorized access to the database before it was secured.
Dangers of exposed data
The links to scanned receipts were associated with individual customer IDs. That information could be used to uncover users’ shopping histories.
The Facebook data contains the most personally identifiable information. On top of that, Diachenko says the login tokens could possibly be used by a criminal to log into someone else’s SavingStar account and hijack it.
Although the authorized user data and password histories were not associated with real users, Diachenko says it could potentially compromise SavingStar infrastructure.
All SavingStar users should be on the lookout for targeted phishing emails related to SavingStar. They might receive fraudulent emails or Facebook messages that attempt to trick the victim into handing over additional information. Criminals could use the personal info found in this database to make the message more convincing.
Exposed MongoDB instances don’t just put data at risk. The instances themselves can be hijacked and used to spread malware or ransomware. Diachenko explains that cybercriminals can remotely access server resources or execute code to steal or destroy data held on the server.
About SavingStar
SavingStar is a grocery rebate service for iOS, Android, and the web that lets users earn cash back on purchases. Normally, users can use the app to link their store loyalty cards and select the rebates they want. When the user makes a purchase, savings are added to their account.
However, not all stores have loyalty cards. That’s where the scanned receipts come in. Customers can use the app to take a photo of a receipt to earn rebates in lieu of a store card.
Users can log in to the app using either an email and password combination or by signing in through Facebook. This is most likely where the Facebook tokens and some other data came from.
Once a user has racked up at least $20 in rebates, they can withdraw funds to a PayPal account or donate them to charity.
SavingStar’s website states it launched in 2010 and now has more than 8 million users. The Android app has a 4.2-star rating and more than 1 million installs on Google Play. The iOS version has a 4.1-star rating.
SavingStar is a subsidiary of Quotient Technology, Inc. A NYSE listed coupon company that also owns Coupons.com.
We found no record of prior public data incidents relating to SavingStar.
How and why we discovered this breach
Comparitech’s security research team scans the web for misconfigured and vulnerable databases. Our aim is to alert responsible organizations and help make the internet a safer place.
Bob Diachenko leverages his extensive cybersecurity expertise and experience to find and analyze data that’s been exposed. When he finds a leak, he immediately takes steps to notify the organization responsible for the data. We do not exfiltrate the data that we find.
Once disclosed, our investigation then continues and we learn about the nature of the data and to whom it pertains. We report our findings to raise awareness among affected consumers so they can take any necessary actions or precautions. We undertake this initiative to limit malicious access to personal information and mitigate harm if the data does fall into the wrong hands.
Previous reports
Comparitech teamed up with Diachenko to uncover several data leaks and breaches, including:
- 700,000 customer records belonging to major hotel franchisor Choice Hotels
- 7 million records of K-12 students
- 188 million personal data records from people search sites
- 300,000 records belonging to cryptocurrency exchange QuickBit