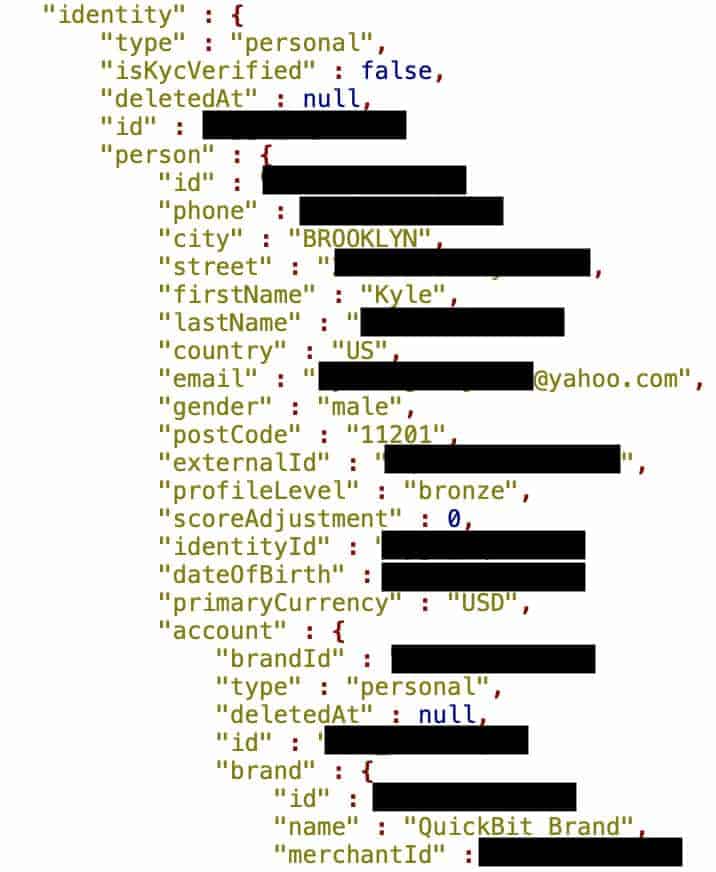
A QuickBit.eu database containing more than 300,000 records was left open such that anyone online could view its contents. On July 2, 2019, Comparitech, along with security researcher Bob Diachenko, made the discovery. The exposure was the result of a publicly available MongoDB database.
QuickBit is a cryptocurrency retailer that allows customers to purchase cryptocurrency using a credit card. They listed on NGM Nordic MTF stock market on July 11th with an initial market cap of SEK 207 million ($22m).
The exposed records appear to contain information about individual transactions facilitated by the platform.
Timeline of the data leak
The MongoDB database containing transaction records was made publicly available with no authentication required. Here’s what happened, step-by-step:
- June 28, 2019: The database was first indexed by Shodan.
- July 2, 2019: We discovered the exposed data
- July 2, 2019: Diachenko immediately notified QuickBit via email.
- July 3, 2019 (or sooner): Within 24 hours of Diachenko sending the notification, the MongoDB database in question was pulled offline.
- July 11, 2019: A second email requesting comment was sent by Diachenko to QuickBit’s general email address and to that of the managing director.
- July 13, 2019: We sent a third follow-up email to QuickBit’s managing director, a conversation with the operations team ensued.
- July 15th, 2019: QuickBit explained they take user privacy and security seriously commenced a full internal security audit following our conversation.
- July 19th, 2019: QuickBit published a report for their shareholders and the market outlining the issue
Although we know how many records were exposed, it is unclear how many QuickBit users were affected by the leak. We also don’t know if any malicious parties accessed or copied information from the database during the roughly six days it was exposed.
QuickBit commented:
“The company has immediately taken the necessary measures to secure the system concerned. Our own initial investigation shows that neither QuickBit nor the company’s customers have been harmed”
What information was exposed?
The database held 301,470 ‘events’ records. An event presumably refers to a transaction that has taken place via the platform. The information for each transaction included the following:
- Full name
- Full address
- Email address
- Gender
- Profile level (Gold, Silver, or Bronze)
- Date of birth
- Payment information (type of credit card used and first six and last four digits)
- Source currency and target currency (for example, USD to BTC)
- Transaction amount
There was also a ‘social number field’ present but with null values.
In addition to those records, we also discovered 143 records with internal credentials, including merchants, secret keys, names, passwords, secret phrases, user IDs, and other information.
Implications of exposed data of this nature
Perhaps the most concerning part of this leak is the 143 records that contained things like user IDs, passwords, and secret phrases. Depending on the platform setup and who this information pertains to, this data could potentially give malicious parties full access to registered accounts.
As a result, anyone who obtained the data may be able to take over the account, carry out transactions, or view full payment information that can be used in credit card fraud. Criminals may even be able to access cryptocurrency balances held by the users involved.
Plus, when passwords are involved, there is the danger that ID and password combinations could be used to hack other accounts. After all, an alarming 52% of users reuse passwords, making account takeover via credential stuffing a low-hanging fruit for cybercriminals.
The bulk of the exposed records contained personal information such as name, address, email address, and date of birth, as well as limited financial information, including partial credit card numbers. Luckily, the credit card numbers were truncated; otherwise, it would have been trivially simple for anyone with access to the data to carry out credit card fraud using any of the credit card numbers.
That being said, the last four digits of a credit card, especially when coupled with detailed personal information, can be all it takes for a criminal to take over various accounts and even carry out identity theft. For example, a criminal might be able to use the last four digits of your credit card, along with your name, address, and date of birth, to convince a wireless carrier that they are an account holder for your account.
There is also plenty of information here for criminals to use to carry out targeted phishing attacks. These are used to glean additional information that can be used in subsequent attacks, such as credit card fraud or account takeover fraud.
If you’ve used QuickBit in the past, it may be necessary to change your QuickBit account password and check for any odd activity. As an extra precaution, you may want to cancel your credit card associated with the account, and if you store cryptocurrency funds in a QuickBit wallet, you might want to move them to another service. At the very least, it would be prudent to keep a close eye on your credit card activity and look out for suspicious login attempts and phishing emails.
About QuickBit
QuickBit is a Swedish company whose goal is to provide a means to purchase cryptocurrency quickly and simply. Currently, the site accepts Visa and MasterCard credit card payments to purchase Bitcoin and Bitcoin Cash with very little fuss. They listed on NGM Nordic MTF stock market on July 11th with an initial market cap of SEK 207 million ($22m).
As far as we know, this is the first exposure involving QuickBit. While the company didn’t respond to notification of the breach, it does have this to say about safety in it’s FAQ section:
“IS IT SAFE TO USE QUICKBIT?
Yes! Our main priority is to keep clients’ personal data safe and secure. We take great precautions around the security of our systems and are constantly monitoring for any suspicious activities…”
Cryptocurrency exchange security
Platforms that involve the buying, selling, or storage of cryptocurrency are big targets for criminals with plenty of high-profile hacks having been documented over the past few years. Even arguably reputable companies such as Binance have suffered hacks resulting in the loss of millions of dollars worth of cryptocurrency. A recent hack of the Bitpoint Exchange saw thieves steal $32 million worth of cryptocurrency.
As such, security should be at the top of the priority list for the providers of these services. Unfortunately, with pretty much anyone being able to set up shop as a cryptocurrency trader, you just never know what level of security you’re going to get.
How and why we discovered this leak
Our security research team scan the web identifying vulnerabilities and data leaks to help organizations fix these issues and make the Internet safer for all users.
Bob Diachenko, who uncovered this particular leak, uses his extensive cybersecurity experience and knowledge to find supposedly secure data that may have been accidentally or intentionally exposed. When a leak is discovered, his first priority is finding out who it belongs to and alerting the relevant organization so they can secure the information.
We then investigate the exposure further to find out the nature of the data and who it pertains to. We report on our findings in the hopes of alerting those affected so they can be aware of the risks and take any necessary action.
This initiative is undertaken with the view to limit the potential of personal information being accessed by malicious parties, and mitigate the risks involved if the data does fall into the wrong hands.
Previous reports
We’ve recently discovered other previously unreported data leaks, including one involving the records of 7 million K-12 students, and another concerning the personal information of 188 million people. You can also check out our articles on the biggest data breaches in history and the states that have the most data breaches.