A K12.com database containing almost 7 million student records was left open so that anyone with an internet connection could access it. On June 25, 2019, Comparitech and security researcher Bob Diachenko uncovered the exposure. The data leak involved a MongoDB instance that was made public.
K12.com provides online education programs for students. This exposure affected its A+nyWhere Learning System (A+LS) which is used by more than 1,100 school districts.
What information was exposed?
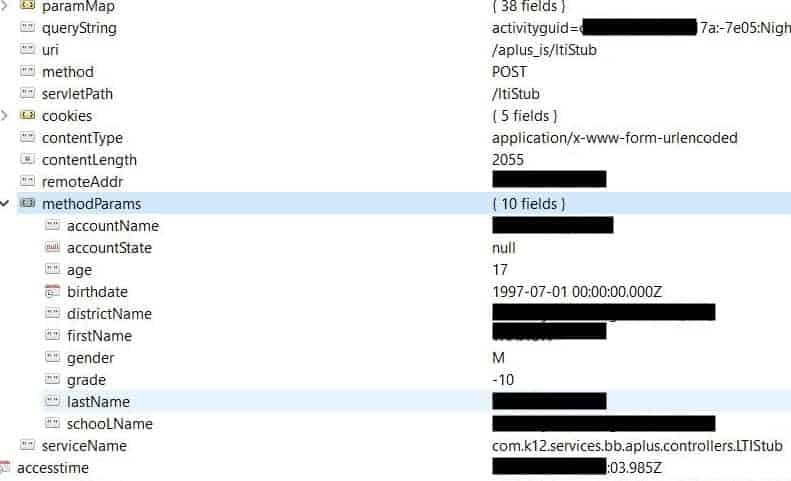
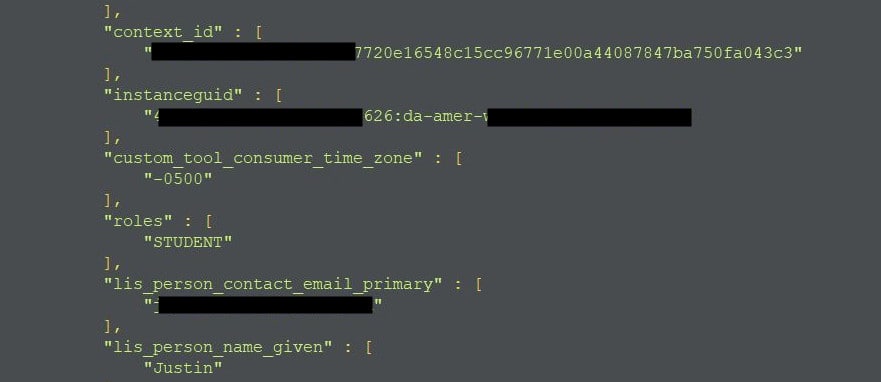
The exposed database held almost 7 million (6,988,504) records containing students’ data. The information held within each record included:
- Primary personal email address
- Full name
- Gender
- Age
- Birthdate
- School name
- Authentication keys for accessing ALS accounts and presentations
- Other internal data
In this instance, an old version of MongoDB (2.6.4) was being utilized. This version of the database hasn’t been supported since October 2016. What’s more, the Remote Desktop Protocol (RDP) was enabled but not secured.
As a result, the database was indexed by both the Shodan and BinaryEdge search engines. This means the records contained on the database were visible to the public.
We discovered the indexed data on June 25 but it had been public since June 23 and the database wasn’t closed down until July 1. So, in all, the data leak lasted just over one week. It’s unclear whether or not any malicious parties accessed the data during the exposure.
Diachenko was able to get in touch with K12 reps with the assistance of Dissent Doe, the administrator of Databreaches.net. K12 was very responsive and provided the following statement.
“K12 takes data security very seriously. Whenever we are advised of a potential security issue, we investigate the problem immediately, and take the appropriate actions to remedy the situation.”
Implications of exposed data
While the leak of this information isn’t as bad as, for example, the exposure of financial data or Social Security numbers, it does have its implications. These pieces of information can be used to target individual students in spear phishing and account takeover fraud. Having their school name made public could potentially put students at risk of physical harm.
If you or your child has used K12.com’s A+LS, be on the lookout for things like login attempts for various accounts and phishing emails. Having an email address made public may also result in an increase in volume of spam emails you receive.
About K12.com
K12.com provides online learning programs to individuals and schools. It appears that this exposure only affected its A+LS software. Depending on the setup, this system can be accessed by students through a desktop client on home or school computers, or through the web both inside and outside of a school’s network. Personal information such as name, email address, and date of birth is required for each student to create an account.
As far as we know, K12.com hasn’t been involved in any other data leaks in the past. However, this isn’t the first exposure affecting students in K-12 education and won’t be the last. Indeed, there were 122 K-12 cybersecurity incidents in 2018, involving 119 education agencies. As schools increasingly use technology, cybersecurity will continue to be a growing concern.