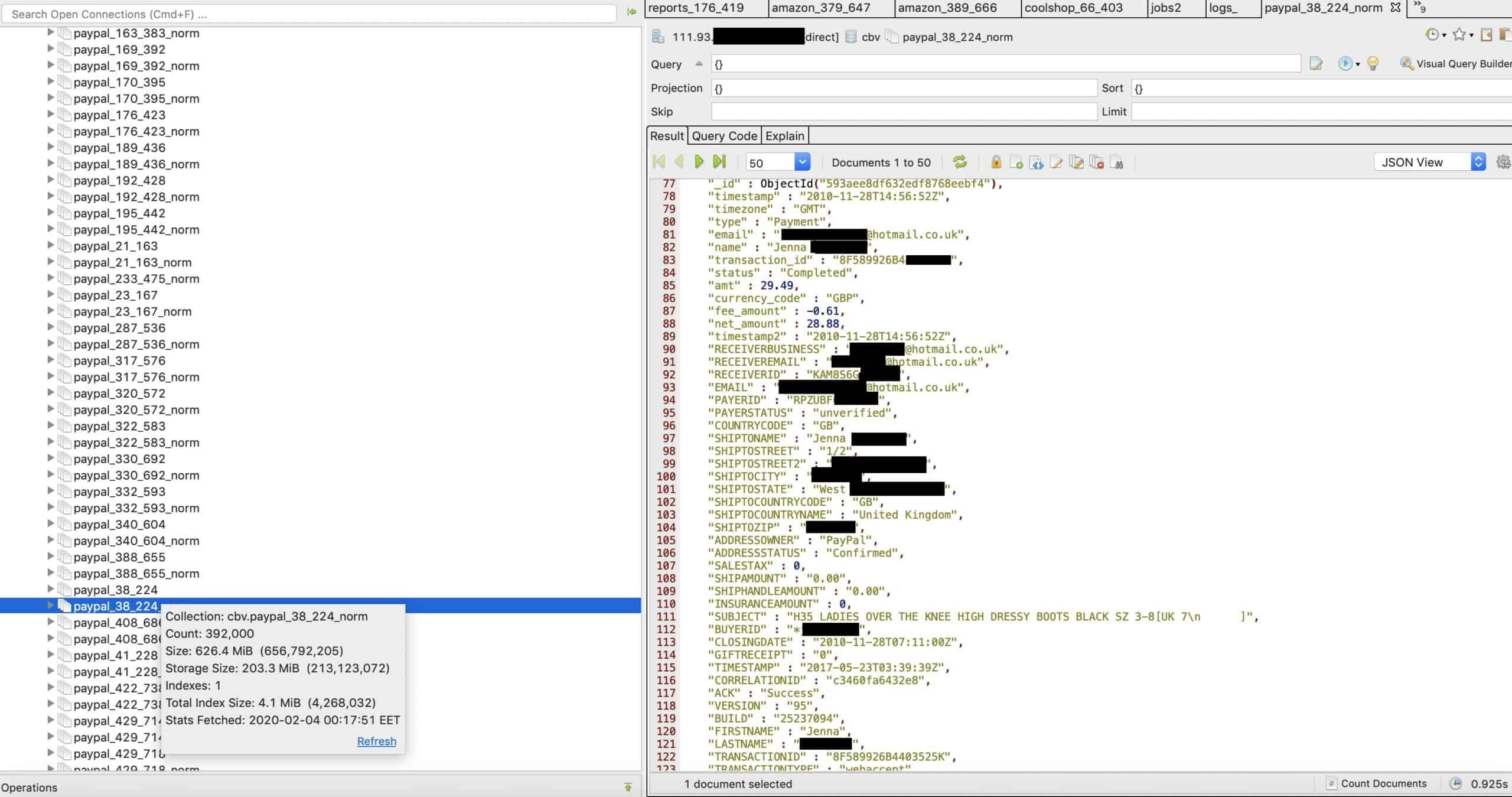
A software vendor used by small retailers in the EU exposed a database of nearly 8 million sales records on the web without a password or any other authentication required to access it. The documents contained sales records including customer names, email addresses, shipping addresses, purchases, and the last four digits of credit card numbers, among other info. Anyone could find and access the data.
The vendor’s app pulled sales records from marketplace and payment system APIs like that of Amazon UK, Shopify, PayPal, and Stripe to aggregate retailers’ sales data and calculate value-added taxes for different EU countries. At this time, we do not know the exact number of retailers or customers affected.
Comparitech’s security research team led by Bob Diachenko uncovered the exposed Amazon Web Services server containing the MongoDB database on February 3, 2020.
Diachenko took steps to responsibly disclose the data exposure as quickly as possible, but other unauthorized parties could have accessed the information in the meantime. The data could be used by bad actors to phish or scam customers with targeted messages.
An Amazon spokesperson replied to Comparitech’s request for comment, saying relevant authorities were made aware of the incident, and no passwords or full payment information was included in the data set:
“We were made aware of an issue with a third party developer (who works with a number of Amazon sellers), who appears to have held a database containing information from several different companies, including Amazon. The database was available on the internet for a very short period of time. As soon as we were made aware, we ensured the third party developer took immediate action to remove the database and secure the data. The security of Amazon’s systems was not compromised in any way.”
Comparitech also contacted PayPal, Stripe, and Shopify, but none gave comment on the record about the incident.
Timeline of the exposure
Upon discovering the misconfigured MongoDB database, it was not immediately clear who owned it. Diachenko first notified Amazon, which hosted the server and IP address where the data was stored.
“[Amazon] were quick enough to get back to me within 24 hours and started their own investigation,” Diachenko says. “Time was of the essence here, since millions of UK shoppers personal, payment and shipment information was at risk, so I started to analyze the content of database and after several days I made the connection to the ultimate owner.”
- February 2, 2020: The MongoDB database was first indexed by search engines.
- February 3, 2020: Diachenko discovered the database and immediately notified Amazon, which responded in 24 hours and began its own investigation.
- February 8, 2020: After further investigation of the data, Diachenko identified the owner. He contacted the company, which responded within the hour and shut down the database.
In all, the data was exposed for about five days. That would give less scrupulous data thieves plenty of time to find and steal the data, but we do not know for sure whether any other unauthorized parties accessed it.
What data was exposed?
The data was in the form of sales records from purchases on Amazon UK, Ebay, Shopify, and some other marketplaces. Many of the purchase records were aggregated from payment systems like like PayPal and Stripe.
An Amazon spokesperson tells Comparitech the email addresses and credit card details (last four digits) were not exposed from Amazon, and MWS does not vend that kind of information.
Some Ebay purchases were affected, but that data did not come directly from Ebay, an Ebay spokesperson told Comparitech. “We investigated and found that no eBay systems were compromised and no data was taken from eBay,” the spokesperson said. “The incident appears to be related to a PayPal API, which is under independent control and not managed by eBay.”
The vast majority of records personally identified customers in the UK, including:
- Customer names
- Shipping addresses
- Email addresses
- Phone numbers
- Orders (items purchased)
- Payments
- Redacted credit card numbers (last four digits)
- Transaction and order IDs
- Links to invoices for Stripe and Shopify
Although we know about 8 million records were exposed in total, that does not mean 8 million people were affected. Each record is an individual sale, but a single customer might account for multiple sales.
The database also included hundreds of thousands of Amazon Marketplace Web Services (MWS) queries, an MWS authenticaiton token, AWS access key ID, and a secret key.
Dangers of exposed data to customers
The personally identifiable details of millions of EU customers could be leveraged by criminals for targeted phishing and scams. If thieves managed to steal the data before access was secured, they could send sales-related messages posing as PayPal, Amazon, or the other marketplaces and payment systems that the app works with.
Given that thieves would know detailed information about customers and their purchases, these messages could be quite convincing. They could trick victims into handing over passwords or payment information through targeted phishing emails and fake websites, for example. Amazon UK customers who use PayPal should be particularly wary of fraudulent messages.
This exposure exemplifies how, when handing over personal and payment details to a company online, that info often passes through the hands of various third parties contracted to process, organize, and analyze it. Rarely are such tasks handled solely in house.
Although a third-party software vendor was responsible for the database, affected customers will likely lay blame on the vendors who use it and the marketplaces where they made purchases.
The Amazon MWS queries and login info could be used to query the MWS API and request specific records from vendors’ Amazon MWS sales databases. Vendors should immediately change their MWS passwords and secret keys.
About APIs
Online marketplaces and payment systems like Amazon and PayPal allow third-party software developers to create apps that merchants can use to access and manage sales data. In this case, the vendor assisted merchants in aggregating sales and refund data from multiple marketplaces and calculating value-added tax (VAT) for cross border sales in the EU.
Developers are required to properly secure data upon receipt, storage, usage, and transfer. Failure to comply with data protection protection policies can result in suspension or termination of API access.
One of the steps Stripe takes to help users potentially mitigate security incidents is to scan public code repositories, merchant applications and other websites for our secret API keys. If it sees a specific user’s secret key publicly visible somewhere, Stripe automatically emails them with a description of where we saw it, such as a URL or line number. It does not seem that would have prevented this incident, however.
Comparitech elected not to publicly disclose the name of the vendor responsible for the database because it is a legitimate small business. Our intent is to raise awareness and mitigate harm to customers who might be affected, not to punish mistakes. Given that the vast majority of customers are probably not aware their data ever passed through this vendor’s hands, we do not believe there is much to be gained from exposing it.
How and why we discovered this incident
Comparitech and security researcher Bob Diachenko collaborate to uncover unsecured personal data that’s been exposed on the web. Upon finding exposed personal data, we immediately take steps to identify responsible parties and notify them.
After responsible disclosure, we investigate the data to learn who is affected and what personal information was leaked. Once the data has been secured, we publish a report like this one to raise public awareness and curb potential harm to end users.
Our goal is to head off any malicious attacks that leverage personal data, such as identity theft and phishing.
Previous reports
Comparitech and Diachenko have worked together on a number of data incident reports affecting millions of people, including:
- 250 million Microsoft customer service and support records exposed
- 267 million Facebook user IDs and phone numbers exposed online
- 2.7 billion exposed email addresses from mostly Chinese domains, 1 million of which included passwords
- Detailed personal records of 188 million people found exposed on the web
- 7 million student records exposed by K12.com
- 5 million personal records belonging to MedicareSupplement.com exposed to public
- 2.8 million CenturyLink customer records exposed
- 700k Choice Hotels customer records leaked