Amazon’s S3 buckets are the most popular means for apps, websites, and online services to store data in the cloud. So when data breaches and exposures occur, vulnerable S3 buckets are often cited as the target.
But Amazon Web Services is far from the only provider of cloud file storage. Google Cloud buckets, for instance, are also quite common, and they are just as vulnerable (due to misconfiguration) as their more popular counterparts, according to the latest research by Comparitech’s cybersecurity research team.
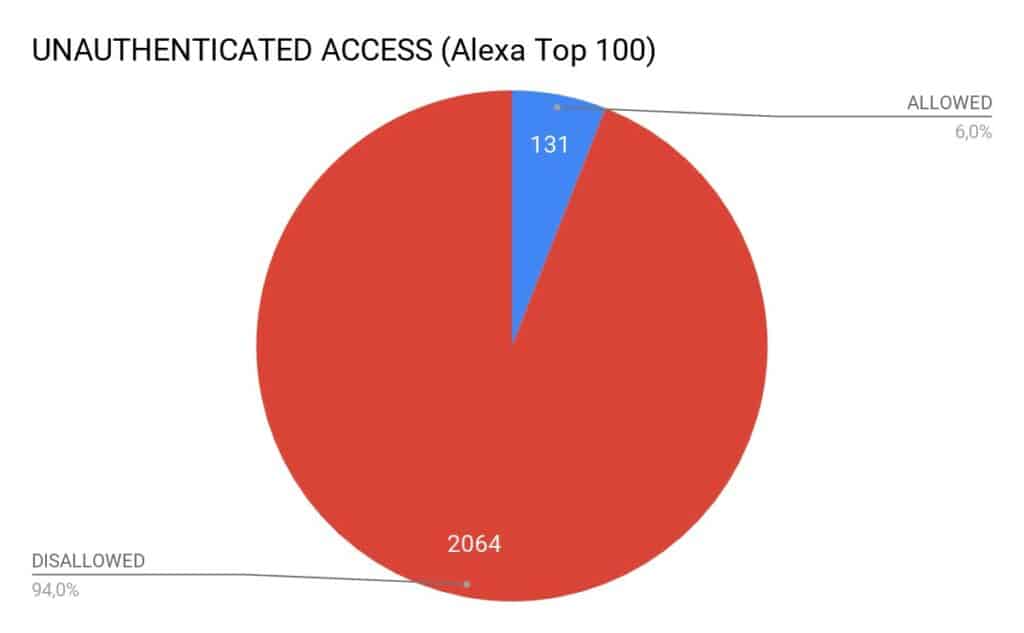
About six percent of all Google Cloud buckets are misconfigured and/or vulnerable to attack, according to an analysis of 2,064 buckets. 131 of the buckets were vulnerable to unauthorized access by users who could list, download, and/or upload files. Those buckets can contain confidential files, databases, source code, and credentials, among other things.
Attackers could exploit these vulnerabilities to steal data, compromise websites, and launch further attacks. These vulnerabilities are easy to exploit, our researchers say.
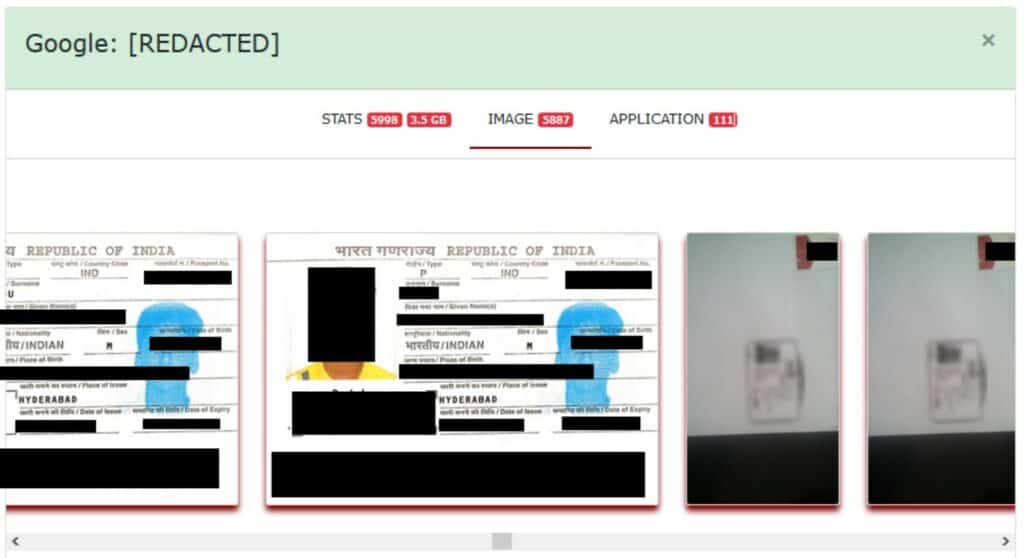
Among the exposed data we uncovered 6,000 scanned documents containing passports, birth certificates, and personal profiles from children in India.
Another database belonging to a Russian web developer included email server credentials and the developer’s chat logs.
Google declined Comparitech’s request for comment, but it did respond with some links to guidance on how to secure Google Cloud buckets, which you can find at the bottom of this article.
Finding exposed Google buckets
Google buckets adhere to a few naming guidelines that make them easy to find. Among them:
- Bucket names must contain only lowercase letters, numbers, dashes (-), underscores (_), and dots (.). Spaces are not allowed.
- Bucket names must start and end with a number or letter.
- Bucket names (or dot-separated components of names) must contain 3–63 characters.
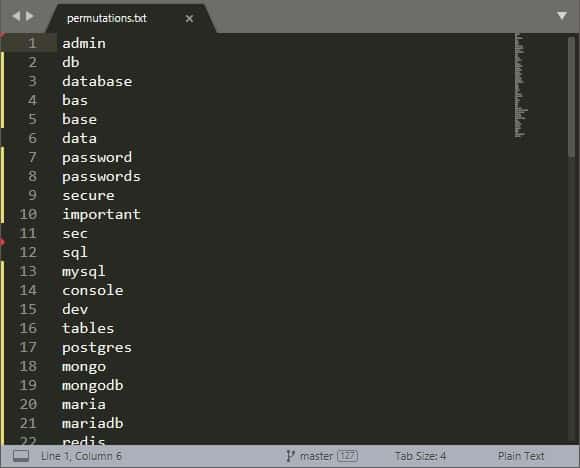
Our researchers were able to scan the web using a special tool available to both administrators and malicious hackers. They searched for domain names from Alexa’s top 100 websites in combination with common words used when naming buckets like “bak”, “db”, “database”, and “users”.
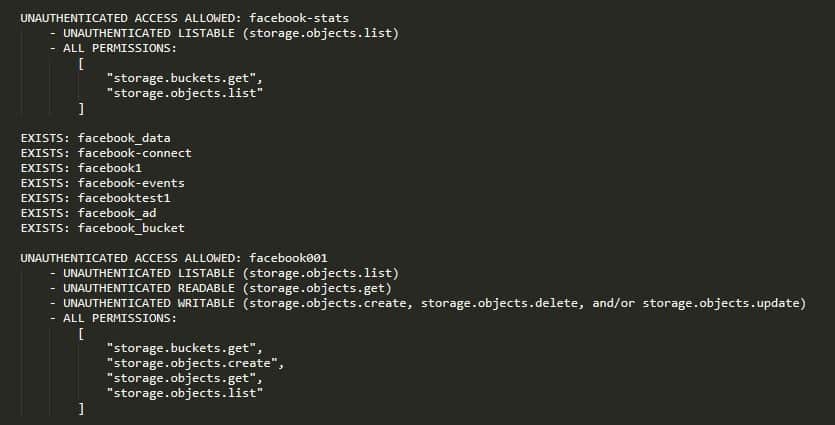
Filtering based on the search input and the naming guidelines, they were able to find more than 2,000 buckets in about 2.5 hours. Our researchers noted they could likely improve their analysis to cover even more domains. Note that just because a bucket name contains a particular company name, such as Facebook, it does not mean that the bucket belongs to that company.
With the list of buckets in hand, the researchers then went about checking if each one was vulnerable or misconfigured. About six percent of the buckets could be accessed without authentication.
This is where our researchers’ analysis stopped, but of course, an attacker could go much further. For example, an attacker could download all files in the bucket using the gsutils command line tool, an official tool from Google for managing buckets.
How to prevent unauthorized access to Google buckets
If you want to ensure your buckets are not exposed, start by scanning the web. Our researchers recommend using gsutil, Google’s official command-line tool, or BucketMiner to scan for your company’s name on Google and Amazon infrastructure. These will produce some statistics, images, and filenames, and tell you whether the bucket is open.
Google’s guidance on securing Google Cloud buckets is as follows:
- Turn on uniform bucket-level access and its org policy
- Enable domain-restricted sharing
- Encrypt your Cloud Storage data with Cloud KMS
- Audit your Cloud Storage data with Cloud Audit Logging
- Secure your data with VPC Service Controls
Routinely monitor your buckets, assets, and security parameters. This goes not only for Google buckets, but also Amazon, Microsoft, and others.