Every device connected to the internet has a unique IP address. Those IP addresses are public, and they allow computers to find and communicate with each other via the Internet Protocol. Normally, we want to allow legitimate parties to connect to our IP addresses, and keep out adversaries by using firewalls, authentication, and access control.
But what if we didn’t take any of those precautions? How long would it take for malicious hackers to find and attack your device? What methods would they use? What do they seek? And where do they come from?
Comparitech researchers sought to find the answers to these questions by setting up honeypots—dummy computers designed to lure in attackers so we can record their every step.
Researchers set up honeypot devices emulating a range of internet-accessible services and supporting a wide range of protocols including RDP, SSH, MySQL, VNC, and more. The honeypots were left unsecured so that no authentication was required to access and attack it. Using this method, Comparitech researchers sought to find out which types of attacks would occur, at what frequency, and where they come from.
In total, our researchers 101,545 attacks in a 24-hour period, or 70 attacks per minute. To give you some idea of how much attacks have increased, a 2007 University of Maryland study recorded a mere 2,244 attacks per day, a fraction of what we recorded in 2021.
Types of attacks: SSH tops the list
Brute force SSH attacks were by far and away the most common against our honeypot. SSH, or Secure Shell, is an encrypted protocol used to remotely access computers, manage servers, and execute scripts. It makes sense that this would be the most common type of attack because almost every device supports SSH in some way or another.
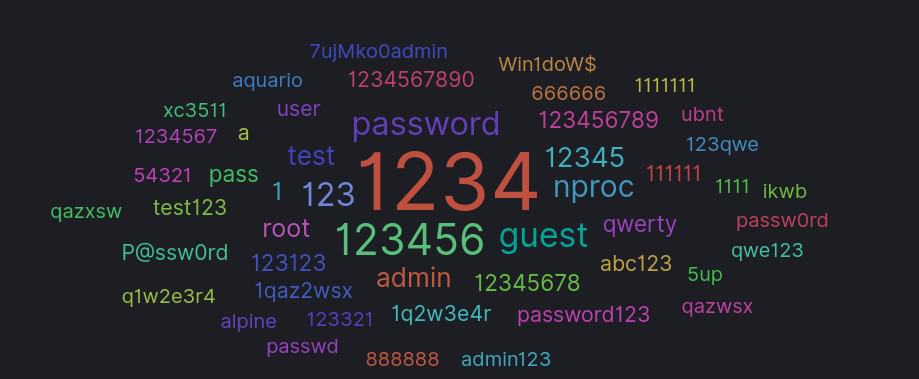
Brute force attacks attempt to guess the username and password for SSH access to the server. You can see which usernames and passwords were most frequently guessed in the word clouds below:

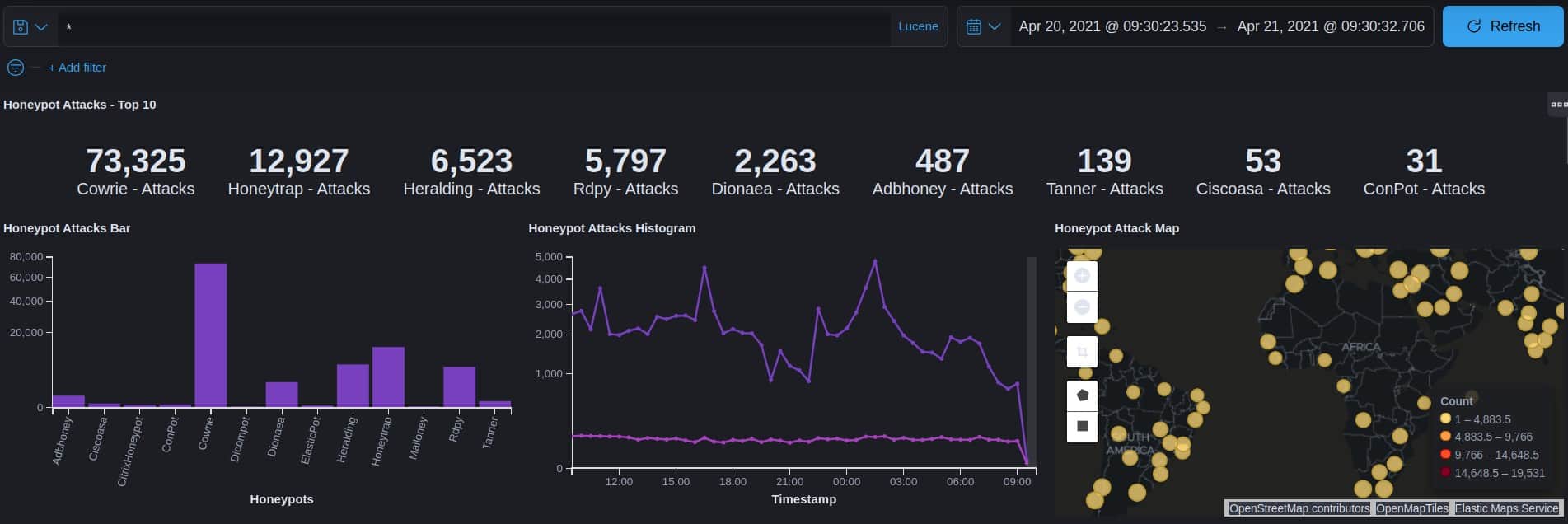
Here’s a breakdown of the top attack types recorded on our honeypot:
- SSH brute force – Attempts to guess the passphrase for access to a server (73,325)
- TCP/UDP attacks – Attacks on services that use these protocols and packets. (12,927)
- Credential stealers – Malware scans the victim device for passwords and authentication tokens (6,523)
- RDP hijacking – Microsoft’s Remote Desktop Protocol can be compromised, giving attackers full remote control over a Windows device (5,797)
- Shellcode attacks – Attacks that attempt to remotely execute attacker’s code on the victim device, usually to exploit a software vulnerability (2,263)
- ADB attacks – Attacks that leverage unsecured Android Debug Bridges, a command-line tool for Android devices including phones, streaming devices, and smart TVs (487)
- Cisco ASA CVE exploitation or DoS – A specific attack that targets unpatched Cisco devices. (53)
- Web attacks – Mostly attackers stealing credentials from web pages (139)
- SMTP attacks – attacks on email servers and clients. (31)
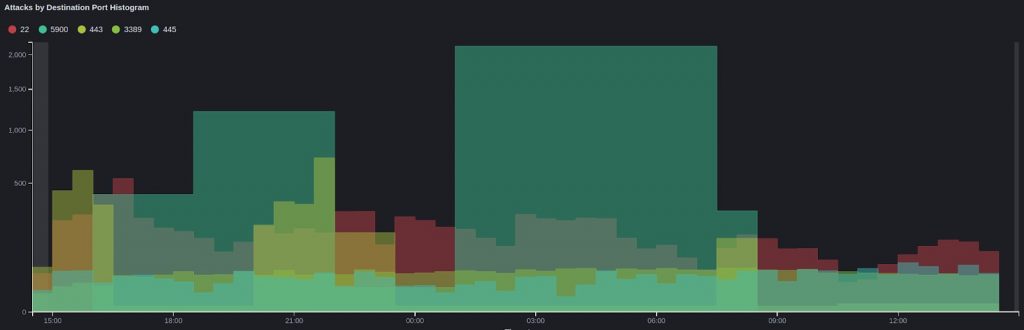
The top three ports attacked in descending order were 5900 (VNC), 22 (SSH), and 443 (HTTPS).
What were attackers after?
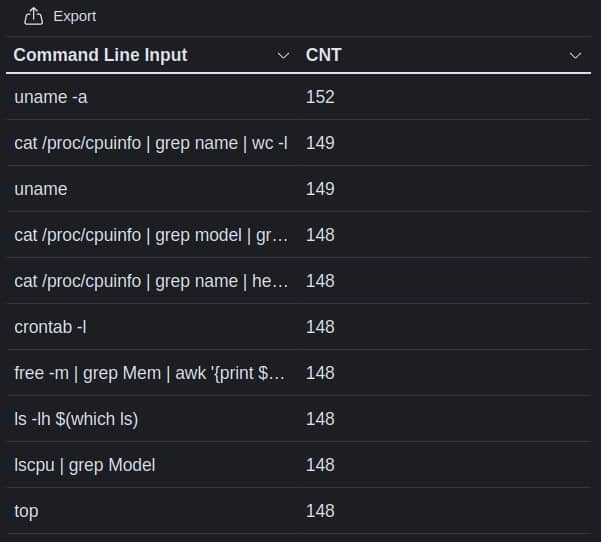
When attackers accessed our systems through SSH, most started out by trying to reveal basic information about the system. Here are the top 10 commands used by attackers recorded by our honeypot:
From there, attackers would presumably launch further attacks based on what they find. If they find an unpatched version of some software with a security vulnerability, they would then take steps to exploit that vulnerability, for example. If they find a database, they would then start exfiltrating data. Or they could plant ransomware, a cryptominer, or a range of other malware.
Researchers also noted attackers attempting to examine crontab, a task scheduling system on Unix systems. They were most likely searching for backup directories, system utilities, and installed software. Others were interested in CPU stats and running processes to see what was installed on the honeypot.
About the attackers
About 98 percent of the attackers’ originating IP addresses were already in publicly-available blacklists. We recorded attempts at unauthorized access from bots and crawlers (3), mass scanners (85), Tor exit nodes (101), and some disreputable IPs flagged by our monitoring tool (614).
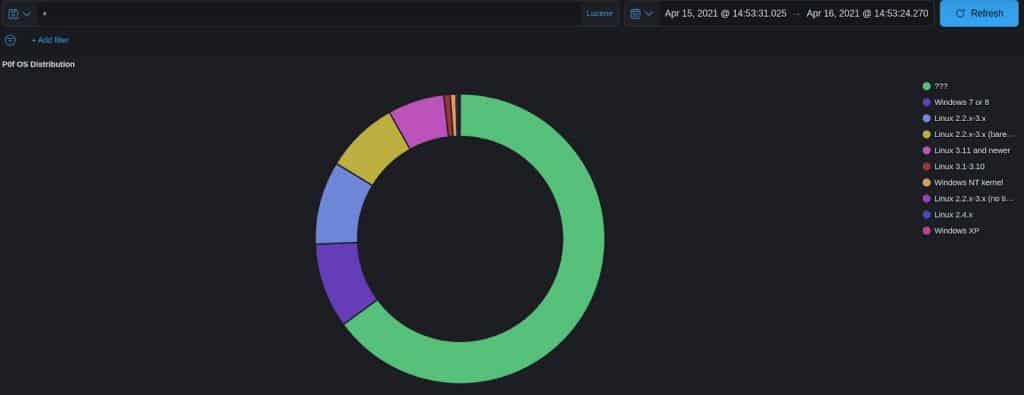
About two-thirds of the attacks came from unknown operating systems, which includes Macs among others. Of those we do know, 9.5% came from Windows devices, and 17.5% came from Linux devices.
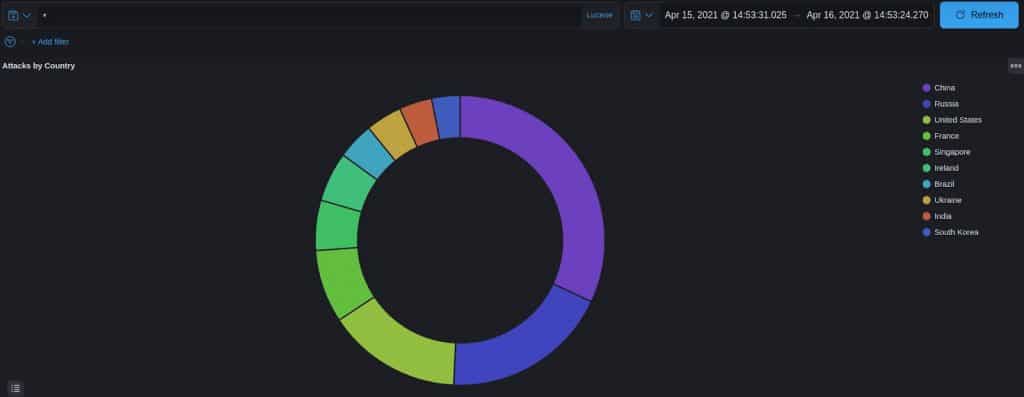
Tracing an attack back to a specific country is a bit dubious, as many, if not most, attackers will use proxies to hide themselves. That being said, here’s the breakdown of attackers’ originating IPs by country:
- China – 32%
- Russia – 19%
- USA – 15%
- France – 7%
- Singapore – 5.5%
- Ireland – 5.5%
- Brazil – 4%
- Ukraine – 4%
- India – 4%
- South Korea – 3%
Do hackers prefer targeting specific operating systems?
Comparitech researchers attempted to answer this question by disguising the honeypot as different operating systems including Windows, MacOS and Linux.
They did not record any significant difference in the number of attacks targeting a particular operating system.
That being said, researchers admit that attackers might be too smart for their ploy. Our researchers disguised the Linux honeypot as another operating system by changing the default TTL value, a parameter by which most automated scanners determine which OS and version is installed. But some scanners can see past this trick.
Furthermore, many of the services and protocols enabled on our honeypot are OS-agnostic, meaning they work on any operating system and are viewed equally by attackers regardless of the underlying operating system.
Notes on methodology
Comparitech researchers relied on T-Pot for much of this experiment. T-Pot is an open-source suite of tools used for honeypot monitoring, including:
- Cockpit – a lightweight WebUI and web terminal for monitoring Docker, operating systems, and real-time performance.
- Cyberchef – a web app for encryption, encoding, compression and data analysis.
- ELK stack – to beautifully visualize all the events captured by T-Pot.
- Elasticsearch Head – a web front end for browsing and interacting with an ElasticSearch cluster.
- Fatt – a pyshark-based script for extracting network metadata and fingerprints from pcap files and live network traffic.
- Spiderfoot – an open source intelligence automation tool.
- Suricata – a network security monitoring engine.
Those tools allowed our researchers to monitor the following honeypot services and protocols:
- adbhoney – a protocol designed to keep track of both emulated and real phones, TVs, and DVRs connected to a given host
- ciscoasa – Cisco ASA component capable of detecting CVE-2018-0101, a DoS and remote code execution vulnerability
- citrixhoneypot – emulates CVE-2019-19781 so we can scan exploitation attempts
- conpot – emulates complex infrastructures to convince an attacker that they just found a huge industrial complex
- cowrie – SSH and Telnet honeypot designed to log brute force attacks and shell interaction
- dicompot – a fully functional DICOM server with a twist
- dionaea – embeds python as scripting language, uses libemu to detect shellcodes, supports IPv6 and TLS
- elasticpot – simulates a vulnerable Elasticsearch server opened to the internet
- glutton – utilizes many well known protocols on top of the server
- heralding – a simple honeypot that collects credentials
- honeypy – emulates UDP- or TCP-based services to provide more interaction
- honeysap – research-focused honeypot specific to SAP services
- honeytrap – a network security tool written to observe attacks against TCP or UDP services
- ipphoney – simulating a printer that supports the Internet Printing Protocol and is exposed to the Internet
- mailoney – an SMTP Honeypot
- medpot – an HL7/FHIR honeypot
- rdpy – RDP, VNC, and RSS honeypots
- snare – converts existing web pages into attack surfaces
- tanner – supplement client for Snare