A hacker can have any number of reasons to deface a website. They might want to attract attention to some political or social issue, damage someone’s reputation, boost their own reputation, demonstrate a vulnerability in a site’s security, or just have a bit of fun.
But the main reason, according to a team of Comparitech researchers that recently delved into the defacement community, is to be noticed.
Online vandalism has become somewhat of a sport among a large segment of black hat hackers. It’s a global community that competes and collaborates to deface websites. Although the frequency of their attacks has gone down in recent years, we’ve seen a recent resurgence in defacement activity, which could possibly be attributed to the COVID-19 pandemic: hackers might have more time on their hands and are possibly defacing websites to stave off boredom while in quarantine or lockdown.
Much of their activity takes place on underground forums and marketplaces for obvious reasons, but the most prominent hackers are surprisingly transparent, boasting about their exploits on social media with little regard for the consequences they may one day face. Comparitech researchers said it was easy to find hackers’ Facebook, Twitter, and ICQ profiles. Some even had LinkedIn and Instagram accounts where they boast about their attacks.
So as to not draw undue attention to Comparitech, we have elected not to share those accounts in this article. We have redacted all screenshots accordingly.
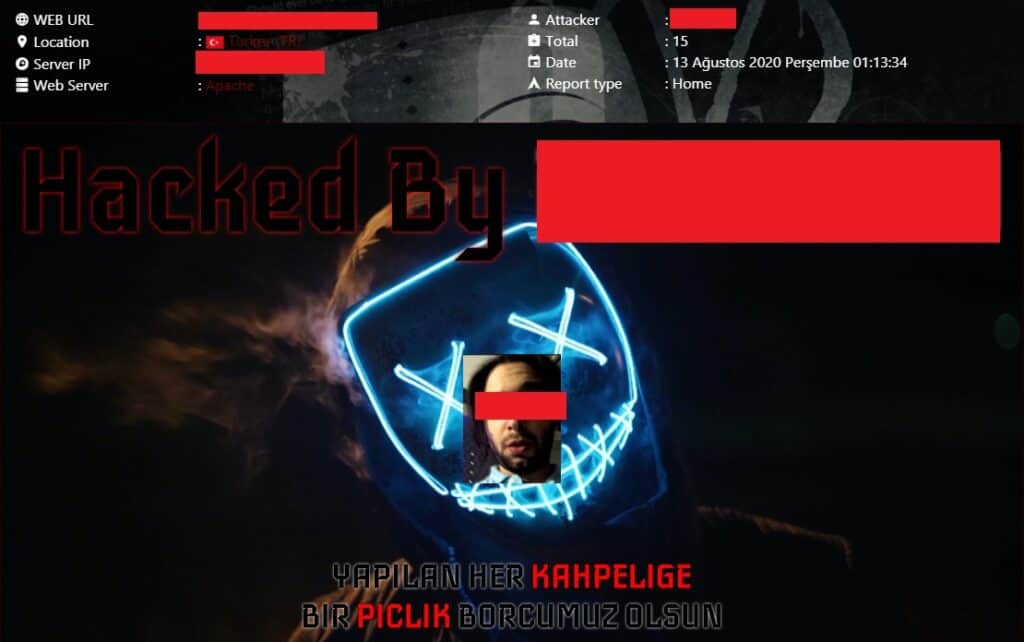
Defacing websites can be targeted or en masse. The motive for defacing a single website is often to make a statement or express an opinion. It’s similar in many ways to graffiti.
Defacing multiple websites at once is usually done for fun and respect among the hacker’s peers.
The owners of defaced websites typically revert to an earlier version of the site as soon as the damage is noticed. But that doesn’t erase a hackers’ efforts.
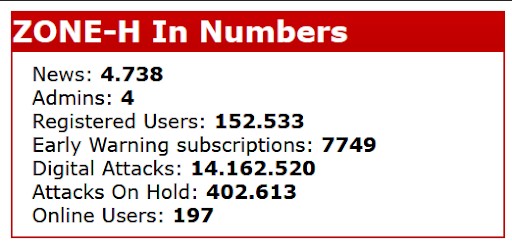
Hackers “mirror” websites as proof of a successful attack. Mirroring a website creates a publicly accessible copy of the defaced page before it’s taken down. Those mirrors end up on aggregator sites like Zone-H, which has been archiving defaced websites since 2002. At time of writing, Zone-H has cataloged more than 14 million defacement attacks.

The bigger the site, the bigger the boost to the hacker’s reputation. High-profile “special” defacements are denoted by a star icon on Zone-H, for example. Popular websites are more valuable, but usually more difficult to hack. Hacking government (.gov) and education (.edu) sites tend to earn more fame and respect among the community.
Hackers even deface sites that others have defaced. Re-defacement is a way to join in and one-up other hackers.
What vulnerabilities are targeted?
Our team of researchers uncovered 89 zero-day vulnerabilities in popular content management systems (CMS) and their plugins. These include plugins for WordPress, Joomla, and Drupal, to name a few.
To find out how many websites are vulnerable to zero-day exploits, we scanned the web using our own dorks. We uncovered more than 100,000 sites with vulnerable plugins. Here’s a breakdown:
- WordPress: about 78,430 sites
- Joomla: about 16,360 sites
- Drupal: about 300 sites
- Opencart: about 6,240 sites
Researchers analyzed the source code of five popular mass-hacking bots, each of which can take advantage of 40 to 80 exploits. Arbitrary file upload vulnerabilities are the most common, which allow attackers to upload shell scripts onto web servers. Those shell scripts can then be used to remotely execute code and deface the site.
A surprising number of these exploits do not appear in any major vulnerability databases. Of the 280 total exploits used by the five bots analyzed, 154 had no CVE assigned. A CVE is a documented cybersecurity vulnerability with an identification number, description, and at least one public reference. Vulnerabilities without CVEs are more dangerous because security software and personnel are less likely to protect against them.
It’s worth noting that defacement is a relatively minor offense compared to what hackers could do using many of these vulnerabilities. Many of the exploits could also be used to distribute malware, set up phishing pages, redirect users to other malicious pages, install card skimming malware, add the server to a botnet, install a cryptominer, encrypt site data with ransomware, or launch a number of other attacks on the site and its visitors.
It starts with dorks
So how do these attacks occur?
It starts by finding a target, often using a specially crafted search request on Google or Bing. These requests are called “dorks”.
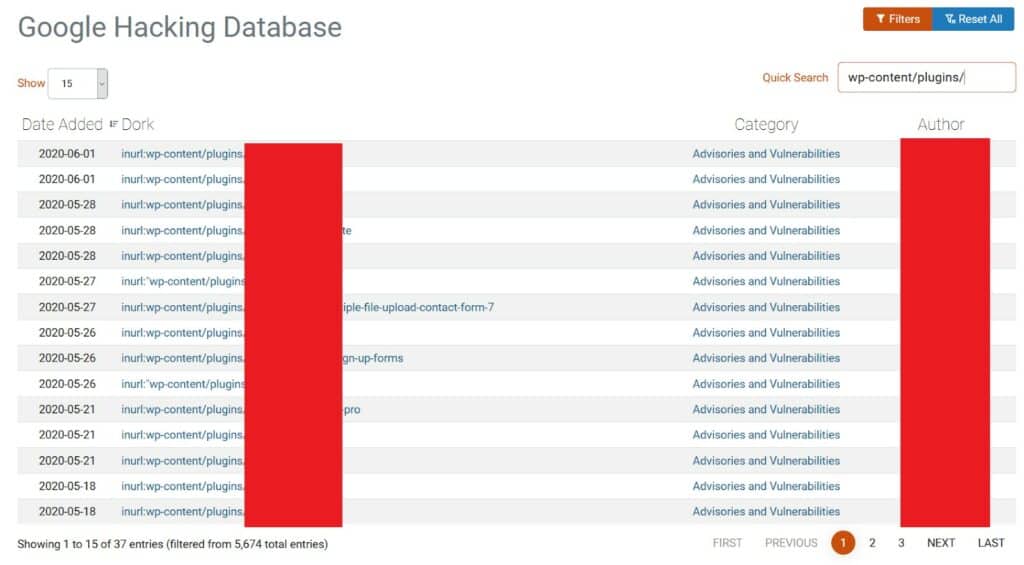
Dorks can be used to find and identify websites that have been indexed by search engines. They frequently use search operators like “intext” and “inurl” to scan specific parts of sites that hackers are interested in. There are plenty of websites with lists of dorks for hackers to use if they don’t want to craft their own. The search engine will then return a list of websites that identify a specific developer, type of database, plugin, or site theme that’s known to be vulnerable to attack.
Many hackers prefer to use Bing over Google. Google blocks automated queries and dorks using CAPTCHAs—tests designed to distinguish humans from bots—but Bing does not.
Another way to find targets is to scan for vulnerable hosts using an IP scanning bot or IoT search engines like Shodan.io, Censys, and BinaryEdge. This approach is useful for hackers looking for sites that haven’t been indexed by search engines.
Once a hacker has obtained a target or list of targets, it’s time to unleash the bots.
The underground marketplace
The availability of hacking tools in recent years has lowered the barrier of entry into hacking communities.
Most of the hackers in the defacement community don’t write their own malware. Instead, they use bots and shell scripts that others have created to take advantage of specific website vulnerabilities.
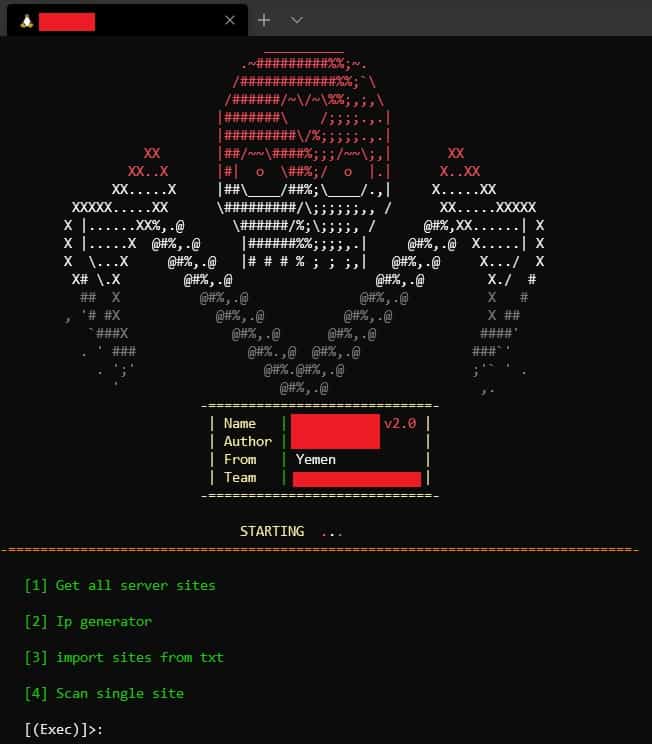
Bots are used to infiltrate sites and give hackers access to the server. The hacker loads their list of targets into the bot, then executes it to start the attack. Bots are automated and will attack all of the sites on the list in a short span of time.
The most common type of bot attack exploits arbitrary file upload vulnerabilities. This type of vulnerability allows the hacker to upload files to the hacked website’s server.
Enter shell scripts. Shell scripts are command files that are read and executed by the server. Once uploaded, shell scripts allow hackers to remotely execute code on the server.
This is where defacement actually takes place. Hackers can wipe out websites, replace them with pornography, steal databases, and generally perform any action they want as if they were the site’s administrator.
So where do all of these bots and shells come from? Some are free and some are paid. Hackers share and sell their tools on hacking forums and the Telegram messaging app. Telegram is popular thanks to its support for large groups and end-to-end encrypted messaging, which allows users to stay anonymous.
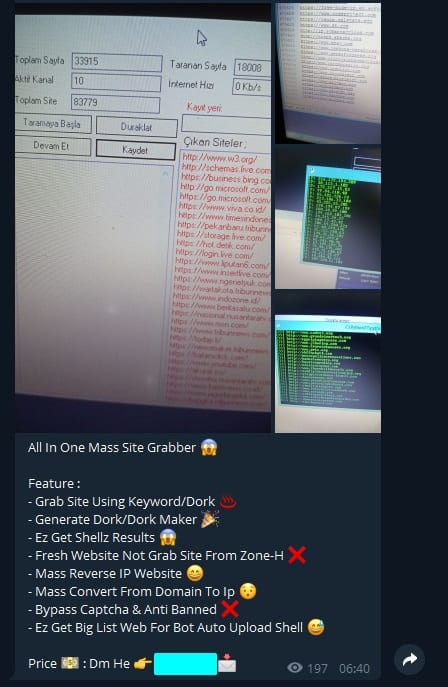
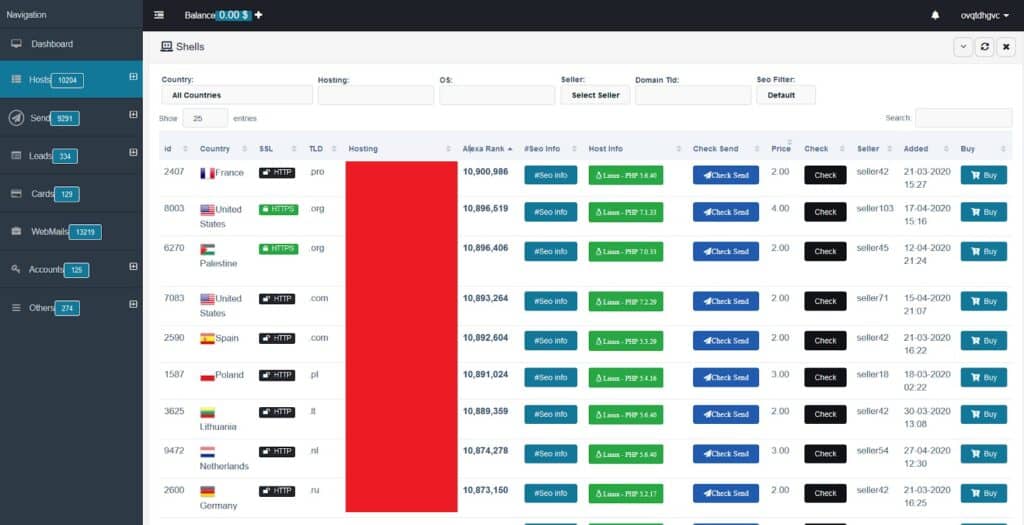
There are plenty of free and open-source bots and shell scripts out there. The average price for a paid shell script is about US$2 to $4. Additionally, vendors can sell lists of targets that are vulnerable to a particular shell script. Users can even sort vulnerable sites by Alexa Rank, SSL availability, CMS, and country, among other filters.
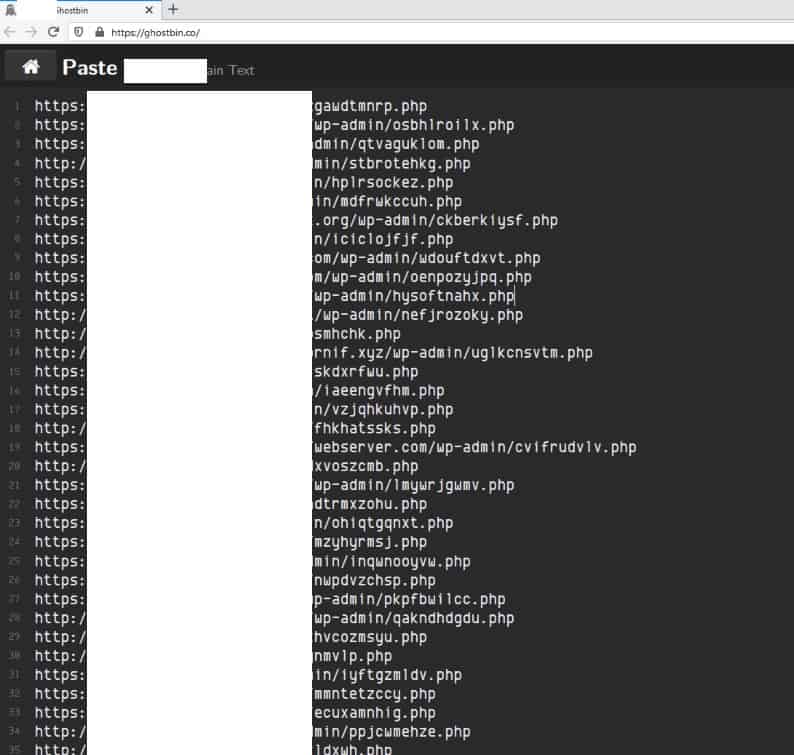
Some hackers even leak lists of websites where they’ve successfully planted shell scripts. Other hackers can then go in and re-deface sites that have already been hacked.
A few hackers are more interested in hacking the paid tools sold by other hackers, a tactic called “cracking”. Once a shell or bot is cracked, the hacker can then re-sell it for a lower price or give it away for free.
Where do these hackers come from?
Although we can’t determine for certain where any particular hacker is from, our researchers were able to gather information about the origins of the 20 most popular website hacking tools.
The origins were evenly split between Iran, Yemen, Tunisia, Russia, Indonesia, and Bangladesh. A significant number of bots had documentation in Arabic but we were unable to pinpoint an exact country of origin.
Do security scanning tools catch these vulnerabilities?
We wanted to find out whether some popular automated security scanning tools would pick up on the security gaps discovered by our researchers. We chose two popular site security auditing tools:
- Sucuri.net, a commercial service for security auditing and protection
- WPScan, an open-source project that scans WordPress sites for vulnerabilities
We tried using these tools to scan sites that had already been defaced, meaning the attacker still had remote access to the server.
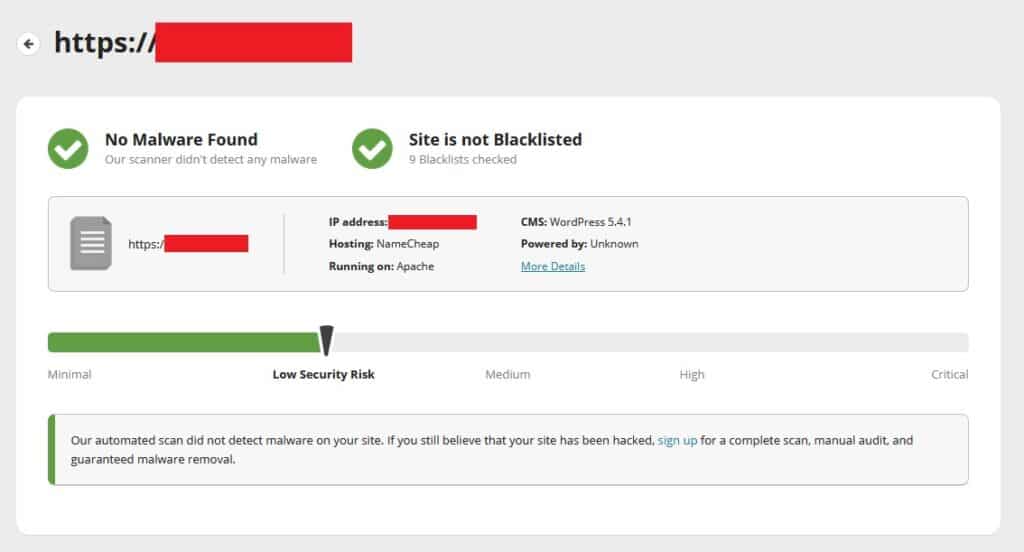
Unfortunately, neither tool* found any critical vulnerabilities or threats on the sites we scanned, despite the obvious defacement.
So administrators should not solely rely on them to ensure that their sites are secure.
Instead, our researchers recommend frequent routine CMS and plugin updates, and choosing those plugins carefully.
*We used Sucuri’s free SiteCheck tool to scan the defaced website so it’s possible the premium version of their product may have identified the vulnerability.


