Illicit marketplaces selling access to hacked remote desktops around the world thrive on both on the dark web and the clear web. RDP access gives an attacker full control over a remote PC with almost no limitations. That makes RDP access an attractive target for hackers. Hacked RDP servers can be found for sale in the thousands on hacker forums and marketplaces.
Prices for hacked RDP (Remote Desktop Protocol) servers vary wildly. In a new analysis of black market RDP access, Comparitech researchers found listings ranging from 30 cents to more than $10,000. The difference in price is based on the remote PC’s specs, where it’s located, what it contains, and to what it has access. On average, prices are around $3 to $4.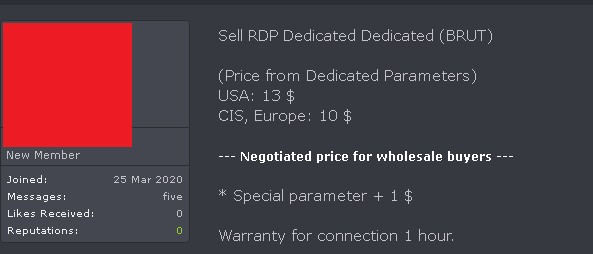
Comparitech researchers found the top countries with the most RDP servers are the USA, China, Canada, and Germany.
In January 2019, US authorities in Florida seized and shut down xDedic, a marketplace that facilitated more than $68 million in fraud. Kaspersky Lab found the site bought and sold access to more than 70,000 hacked servers from around the world. Victims spanned local, state, and federal government, infrastructure, hospitals, emergency services, call centers, transit authorities, accounting firms, law firms, pension funds, and universities.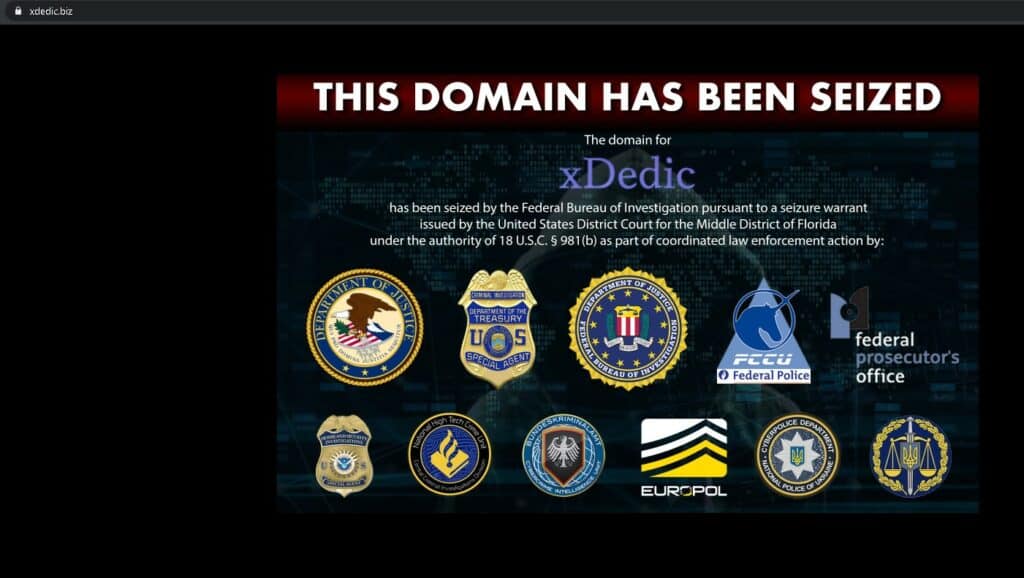
Although xDedic is now gone, the sale and abuse of stolen RDP credentials is still all too common online, Comparitech researchers have found.
Vendors on RDP marketplaces sometimes start out by running free RDP giveaways on social media, darknet forums, and chat rooms. This allows them to quickly build a reputation and customer base.
What is remote desktop protocol (RDP)?
RDP, short for Remote Desktop Protocol, allows one computer to control another over a network connection. With RDP, one computer (the client) can see the display and control the inputs of another computer (the server) over the internet as if it were right in front of them. Developed by Microsoft, RDP is one of the most common tools for controlling remote machines.
The servers—Windows computers and servers that have the Remote Desktop Protocol installed an enabled—can belong to consumers or organizations, but the latter is far more common. Enterprises use RDP to give remote employees access to corporate devices, networks, apps, and storage, among other uses.
Why RDP hacking is so dangerous
Let’s say your office has a Windows PC with the Remote Desktop Protocol installed and enabled. It allows remote employees to log in from their own devices so they can access office-only apps, files, and other resources. As the COVID-19 pandemic forces more people to work remotely, this is an increasingly common scenario.
An attacker manages to find the username and password for the Windows PC’s RDP access (more on how hackers do this below). They can now log into the PC remotely and use it as if they were an employee. The attacker can steal files, plant malware, and use the machine as a proxy to conduct spam and fraud operations.
Some examples of attacks conducted through RDP include:
- PayPal, eBay, and Amazon fraud
- Data theft
- Sniffing network traffic for valuable data such as credit card numbers
- Infecting devices on the server’s network with ransomware
- Cryptomining
- Botnets and distributed denial-of-service attacks
- Gambling fraud
- Dating scams
Moreover, if the remote PC is logged into accounts from previous sessions, or has autocomplete enabled on login forms, the attacker can now access all of those accounts. PayPal, Ebay, Amazon, and gambling sites are all common targets, but hackers will take advantage of whatever they can find on the remote PC. Cybercriminals often buy RDP access in a location near their victim to help bypass location-restrictions on those sites. Criminals can buy products and send money to themselves, often through mules so their transactions can’t be traced.
In a corporate setting, a single RDP server can control several websites or other services, which could allow the purchaser to sniff for credit card numbers, access user databases, and launch attacks on other devices on the server’s local network. Reliable access to such a server could be extremely valuable.
How do attackers hack RDP?
Finding RDP servers is easy. Freely available tools like Shodan.io, ZoomEye, and Censys can scan the web for the ports and protocols typically used by RDP.
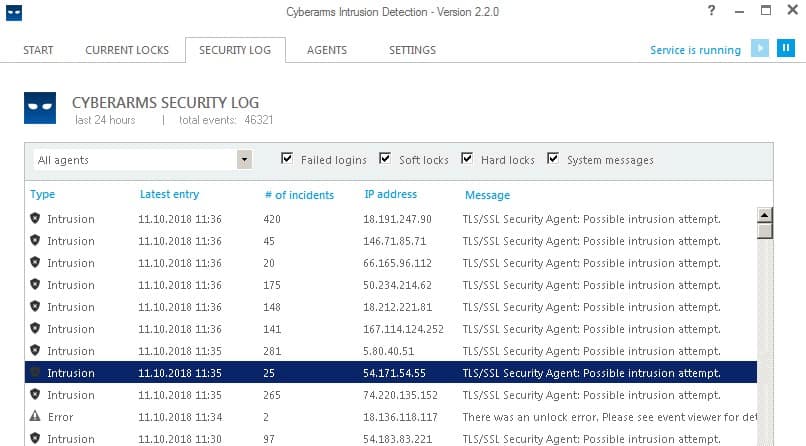
Our researchers set up a honeypot RDP server to find out the frequency and types of attacks made on RDP servers. Within 24 hours, the server recorded:
- 12,000 scan requests
- 850 brute force attempts
- 30 hard locks (permanent lockouts)
- 300 soft locks (temporary timeouts)
- 25 exploitation checks
The exploitation checks mostly consisted of hackers poking around for known vulnerabilities and reconnaissance commands.
Hackers have a few methods of gaining unauthorized access to an RDP server:
- Password spraying: A few common passwords are attempted on millions of IP addresses. This was the most frequent attack recorded by our researchers.
- Dictionary brute force attacks on a single IP range: Hackers attempt many passwords on a range of IP addresses where multiple RDP servers reside.
- Exploiting known vulnerabilities: Unpatched versions of Windows contain security flaws like BlueKeep, which allow for remote code execution among other attacks.
- ARP poisoning: In an already-hacked local network, the attacker can find and access more RDP servers by spoofing ARP messages.
- Stealer malware: A type of Trojan that logs access credentials for RDP servers, among other targets, then exfiltrates the credentials to the attacker.
Hackers don’t need to start from scratch when trying to gain unauthorized access to RDP servers. ARP spoofers, exploit kits, and RDP brute forcers are available on both the clear web and dark net.
Attackers want to maintain control over a compromised RDP server for as long as possible. To do so, they use a locker.
A locker is a Windows shell script that closes all applications on the server and does not allow the client to view the server until a password is entered. Because vulnerable RDP servers could be found and attacked by anyone, lockers prevent other hackers from hijacking an already-hacked RDP server. Granted, seasoned hackers can easily bypass lockers with buffer overflow attacks, by brute forcing the password, or by removing the locker via the Command Prompt.
How to detect and prevent attacks on RDP
Comparitech researchers advise individuals and organizations using RDP to monitor, if not limit, what IP addresses can connect to an RDP server. Admins should regularly check RDP logs for connections from unknown users.
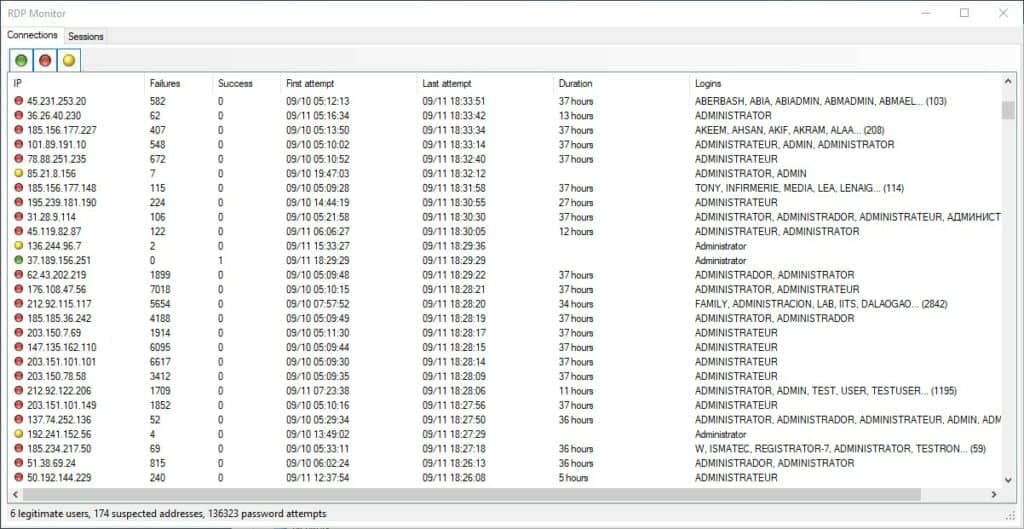
To help with this, our researchers recommend RdpMon, a free and open-source tool that shows real-time and past RDP connections. The program logs source IPs, success and failure counts, logins, active and past sessions, executed processes, and more.
Another useful tool is Cyberarms. It’s an intrusion detection and defense software (IDDS) that blocks brute force attacks on RDP servers, among other targets.
Other tips to protect your RDP server include:
- Use strong, long, and unique passwords
- Change the default port number to 3389
- Keep your RDP server updated
Comparitech researchers conclude that the sale of hacked RDP credentials is an ongoing and underreported issue.