As your main point of access to the World Wide Web, your browser is exposed to potential online attacks every time you use it. The browser is a great channel for hackers to get access to your personal data, to manipulate your connections, to get tracking software onto your computer, and even to access your computer directly.
Browser security overview
As an entry point to your computer, your browser is constantly vulnerable to hacker attack. Hackers and the producers of malware pay close attention to the code that creates browser programs, and they also examine ways to manipulate the various programming languages that run in browsers in order to sneak malware onto your computer.
The producers of browsers are aware of these threats and research security weaknesses, trying to spot them before hackers do. In many cases, they only discover an exploit once a hacker has already launched a worm that uses it. However, browser producers regularly produce updates to their products that close off these loopholes.
The main security procedure that you can implement in your browser is to allow automatic updates. This will keep you ahead in the cat and mouse game against hackers.
Browser security falls into two main areas:
- Protection against browser weaknesses that can let in malware
- Protection against snoopers that covertly collect information about you and your online activity
In order to address the issue of browser weaknesses, you can easily close off the entry points that hackers use by altering the settings of your browser.
Snooper attacks are harder to deal with because these can be implemented outside of your browser, either on the internet or through the network procedures of your computer. With just a few network settings adjustments, a hacker can hijack all of the traffic that passes in and out of your browser and control all of your web access.
To reduce the amount of information stored in your browser, we’ll show you how to remove browser history, cached data, and cookies. Each browser contains a settings menu that allows you to clean out this information. However, you can prevent this data from accumulating in your browser by using its privacy mode.
The next sections of this guide will show you:
- How to use the privacy modes of your browser
- How to remove data stored in your browser.
- How to check your network settings to make sure that your internet traffic is not being hijacked,
- How to remove the capabilities of your browser to play JavaScript programs, Flash files, or display PDFs — both Flash and PDF files have become conduits used by hackers to sneak worms onto your computer.
Network settings
Although the network settings on your device do not pertain directly to browser security, some browser behavior is set by routing preferences that are dictated in the network settings of your operating system. These settings can sometimes be altered by viruses, Trojans, and worms. Even if your antimalware system detects the operation of this malware, once the network settings of your device have been altered the damage those viruses can do to your computer will still continue to operate.
Traffic redirection gives hackers the option of sending fake copies of well-known websites that exist to harvest your login credentials, force advertising on you, or sneak extra programming code onto your computer.
The two key settings that you need to address here are the proxy settings and the DNS settings.
Proxy settings
A proxy server mediates all of your internet traffic. Ordinarily, you should not have a proxy nominated in your network settings. If one is there, then all of your traffic on the web is being channeled through that server. The owner of the proxy server can block requests for web pages, or send back altered pages that look like the pages that you want but actually are fakes controlled by a hacker. If your proxy settings have been altered, your internet actions will be monitored and manipulated until you remove this setting.
DNS settings
A DNS server translates website names to the actual internet address of the server that hosts that website. When you enter the address for a web page in your browser, the first step in accessing that page is to lookup the internet address for that site. The root of a web address is called a “domain.” For example, “comparitech.com” is the domain of this web page. “DNS” stands both for “domain name system,” which is the network that provides internet address for given domains, and for “domain name server,” which is the computer that your browser will refer to when looking for the IP address of the page you want to see.
Ordinarily, the DNS server that you access is dictated by your internet service provider.
However, that preference can be overridden in the network settings of your computer. If a virus alters the DNS settings of your computer, a hacker-owned DNS server can return a different address. So, you may type in yahoo.com, but instead of getting the real Yahoo home page, the hacker DNS returns the address of a copy of that page held on the hacker’s server. If you then log into that fake page, you will just be passing your login credentials to the hacker. When you are looking at the fake page, your browser will show the web address of the real page, so it is very difficult to spot DNS hijacking.
Check network settings on Windows
In order to prevent both proxy and DNS hijacking, you need to make a point of visiting the network settings of your device to check that you haven’t been hit. If you have, all you need to do to restore your browser privacy is delete the values in your proxy and DNS settings.
The DNS settings and proxy settings on Windows are set in two different places. Firefox has its own proxy settings system.
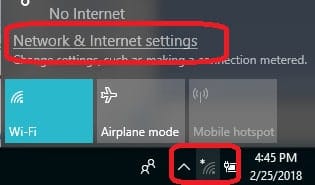
- Click on the network symbol in the system tray. Select Network and Internet settings.
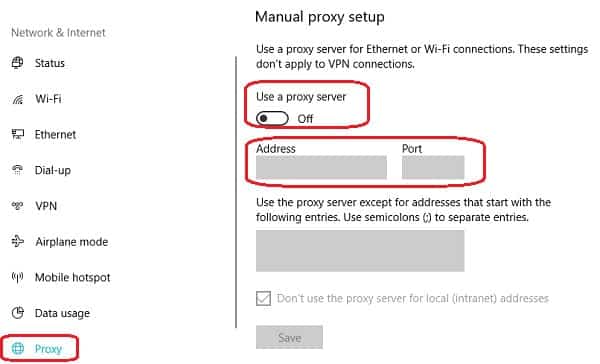
- In the Network Settings screen, click on Proxy in the left-hand menu.
- Scroll down to the Manual proxy setup section. Make sure that the Address and Port fields are blank and that the Use a proxy server slider is set to Off.
- Click on Status in the left-hand menu and then select Change Adapter Options. This will open a folder with a list of all the connection types available to you.
- Click on the connection you use the most. For example, Wi-Fi. If you use several different connection types you will have to perform the following sets for each.
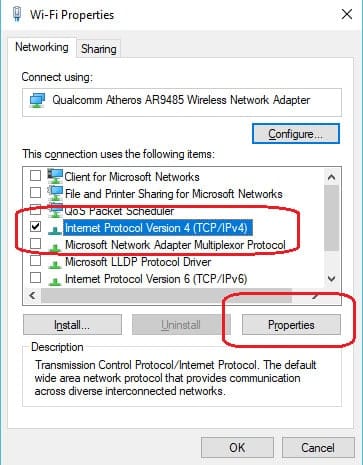
- Right-click on the connection definition and select Properties from the context menu.
- In the Properties screen, select the Internet Protocol Version 4 item and click on the Properties button.
- In the next screen, make sure that the two DNS address fields at the bottom of the window are blank. The Obtain DNS server address automatically radio button should be active.
- Click OK to close down the Internet Properties window and then press OK in the WiFi Properties window to close it.
If you use Firefox, you need to go into the settings of that browser to make sure than there hasn’t been a proxy server address entered there.
- Open Firefox and click on the Hamburger menu symbol at the end of the address bar. Select Options from the drop-down menu.
- Scroll to the bottom of the Options page to the Network Proxy section. Click on the Settings button.
- In the Connection Settings window, make sure that the No proxy radio button is active.
- Click on OK to close the Connection Settings window.
Check network settings on macOS
In macOS the DNS and proxy settings are organized per connection type, so if you use both a cable connection and wifi, you will have to follow these instructions for each type.
- Select System Preferences from the dock and click on the Network pane.
- Select the network type and click on the Advanced button to get the Advance Network window.
- Click on the DNS tab. Make sure all of the DNS entries are blank. Highlight each entry and press the minus sign at the bottom left of the window.
- Click on the Proxies tab in the network type screen. Uncheck all protocols in the left-hand list. Click Apply at the bottom right of the Network settings window to save your changes.
Check network settings on routers
Unfortunately, there are many router manufacturers and they all have different user interfaces for their software, so here I will show you an example of one router’s console and you will need to explore the user manual of your own router to find the same screens.
If you can’t find the manual, there are some basic tricks that you can try to get into your router’s settings. Open the Task Manager on your computer and click on the Performance tab. Scroll down to the WiFi section in the left-hand menu. Note down the IPv4 address shown in the main screen beneath the performance monitor.
Enter that address in your browser. However, change the last number to 1. So if your address is shown as 192.168.0.12, enter 192.168.0.1 in the address field of your browser. This should get you into the router’s console.
If you don’t know the username and password for your router, try user/user, system/admin admin/password, admin/admin, or system/password. In some cases you can even leave the password field blank.
If you don’t have the manual, you will need to explore the menu system of your router to get to the right screen. However, you need to look for the Network Configuration page.
If your router has been hijacked by a virus, that malware could also report back to a hacker when you modify the router’s settings. Before making any changes, reset the router to its factory settings to wipe out any malware.
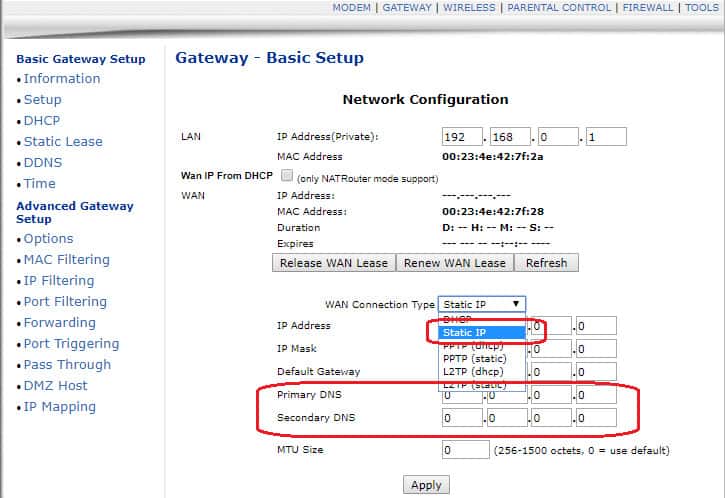
The DNS configuration is not available for DHCP settings. You have to switch to Static IP to change the DNS settings. So, if you arrive at the network settings and see that it is classified as DHCP, then you are safe. If your settings say Static IP, you need to look at the Primary DNS and Secondary DNS fields. If these have values, you need to set them to 0.0.0.0.
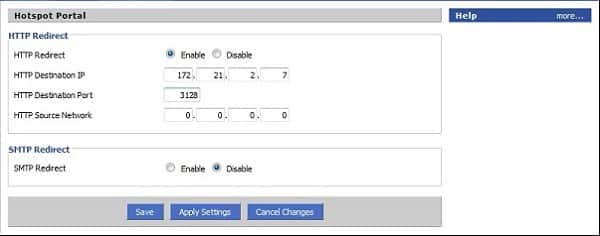
Look for the Hotspot Portal section of your router’s control panel. You need to disable HTTP redirects. If there is no Enable/Disable option, set the Destination IP to 0.0.0.0 and delete the port number. Press the Save button once you have finished.
Check network settings on Android
On Android, the proxy setting relates to each network that you connect to, so you have to follow these instructions for each.
- Swipe down from the top of the screen to expand the Settings menu. Click on WiFi. Tap on More Settings at the bottom of the list of available networks.
- Long press on the network that you want to check the settings for. Select Modify Network in the popup that appears.
- Tap on Advanced options in the next screen and then tap on Proxy. Click on Manual to see whether any proxy server has been set up for that connection.
- Check the Proxy hostname and Proxy port fields. If they have proxy.example.com and 8080 in them, you don’t need to do anything. If there are any other values in these fields, delete them.
- Check the IP settings field. This should be DHCP. You cannot specify a DNS server with this setting. If this field says Static, scroll down to the fields DNS1 and DNS2. If these fields have the values 8.8.8.8 and 8.8.4.4 you don’t need to worry. If there are any other values in those fields, delete them. Change the IP settings back from Static to DHCP.
- Tap Save at the bottom of the Advanced Options screen.
Check network settings on iOS
As with Android, the iOS network settings for proxy and DNS servers apply to the network, so the network you want to check needs to be in range and you have to repeat these instructions for every network that you connect to.
- From the Home screen, tap on Settings. Select Wi-Fi from the Settings screen.
- In the Wi-Fi screen click on the right-arrow next to the name of the network that you want to check.
- In the network settings screen, look for the DNS field. This should read 8.8.8.8. If there is any other value in that field, tap on it and delete it.
- Scroll down in the network settings screen to the section. Make sure that the Off button is active.
Security weaknesses in browsers
There are four basic problems with browsers that you can fix very easily by changing your browser settings:
- SSL security weaknesses
- Flash video cloaking for viruses
- PDF cloaking for viruses
- Malicious popups
In this section of the browser security guide, we’ll first explain those weaknesses and then show you how to secure your browser.
De-list SSL compatibility to use TLS
SSL was invented by Netscape Corporation as part of HTTPS. HTTPS is the Hypertext Transfer Protocol/Secure and you know that it is in operation on your web transfers when you see “https://” in front of a web page’s address. This system has been very successful on the internet. It includes server authentication procedures and encrypts all contents of internet communications. SSL stands for the Secure Socket Layer. This created ways to check whether the server that a browser connects to really is that computer and it makes it difficult for interceptors of internet traffic to pose as the intended destination of a connection.
The Secure Socket Layer was discovered to have a security flaw and so it was replaced with Transport Layer Security. This was because it was possible with SSL to provide a fake authentication certificate that changed the encryption key that the browser should use to secure all data sent over the connection. If a hacker can dictate the security key, he will know how to decrypt all subsequent communications.
Unfortunately, TLS was created with backwards compatibility to SSL. So if you use TLS and contact a site that is still using SSL, your browser will rollback to SSL and the old security exploit will be exposed. You can close down that weakness by de-listing SSL compatibility from your browser. You also need to prevent your browser from using the first version of TLS to block off the rollback to SSL.
Block Flash and PDF files from loading in your browser
The Flash video standard and the PDF file format are both products of Adobe Systems. Unfortunately, both encoding formats include programming constructs that can provide cover for virus invasion. So, you need to block both Flash and PDF files from loading in your browser.
Block popups
Popups are more of an annoyance than a security weakness. However, they can be used to trap you into a site, add malware to your computer, and can even be deployed recursively to overload your computer. It is better to block popups.
So, let’s tighten up the security of your browser by preventing SSL backwards compatibility, blocking Flash and popups, stopping PDFs from opening in your browser, and stripping out JavaScript.
The menus for closing off some of the security weaknesses are exactly the same for Internet Explorer and Chrome, you just arrive at that screen by a different route in each case. However, if you have closed off these weaknesses in Chrome, then you already have done all the work to protect Internet Explorer and vice versa.
How to secure Chrome
- Click on the three dots symbol at the end of the address bar. In the drop-down menu select Settings. This will open a new tab.
- Scroll down in the Settings screen to the bottom and click on Advanced. The screen will extend. Scroll down to find the System section and click on Open proxy settings. This will open the Internet Properties window.
- Click on the Advanced tab and scroll down in the Settings window. Make sure that Use SSL 3.0 and Use TLS 1.0 are de-selected.
- Click on OK in the Internet Properties window to save the changes.
- Return to the Advanced Settings screen in Google Chrome and look for the Privacy and security section. Click on the arrow next to Content settings.
- Click on the arrow next to JavaScript and in the next screen, click on the slider to turn it to Blocked. Click on the back arrow at the top of the JavaScript screen to return to Content Settings.
- Click on the arrow next to Flash — this is the next entry down from the JavaScript setting. In the next screen, click on the slider so the message next to it reads Block sites from running Flash. Click on the back arrow at the top of the screen to get back to the Content Settings list.
- Scroll down to Popups and click on the arrow in that line. Click on the slider so that you see that popups are blocked. Click on the back arrow at the top of the screen.
- Scroll down to PDF documents, which is the next to last entry in the Content Settings list. Click on the arrow on that line. Click on the slider so that the message next to it reads Download PDF files instead of automatically opening them in Chrome.
How to secure Firefox
Make sure that you have Firefox version 57 or above. This newer version of Firefox automatically blocks PDFs from opening in the browser. In order to prevent Flash from running in the web pages that you visit with Firefox, you should install the Flashblock add-on.
To block of the SSL backwards compatibility exploit, follow these steps.
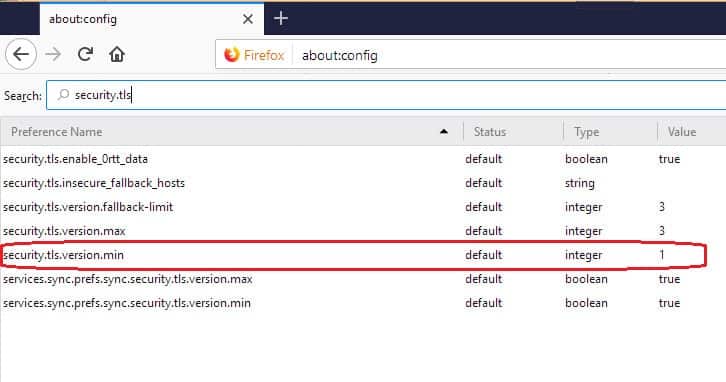
- Enter about:config in the address field of the browser. You will be shown a warning about proceeding. Click on I accept the risk.
- In the Configuration screen, enter security.tls in the Search field. Look for the entry for security.tls.version.min.
- Double click on the line and enter 2 in the popup box for the value in this field. Click OK to close the popup.
You can block popups through the browser options system:
- Click on the Hamburger menu at the end of the address bar. Select Options from the drop-down menu.
- Select Privacy & Security in the left-hand menu. Scroll down to the Permissions section and check the box for Block pop-up windows.
How to secure Internet Explorer
You remove backwards compatibility for SSL in Internet Explorer with the same screen as that used for Chrome. So, if you have already closed off this exploit for Chrome, you don’t have to do it again. If you don’t have Chrome, follow these instructions.
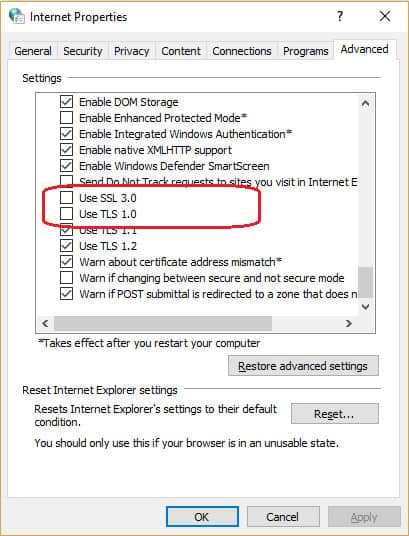
- In Internet Explorer, click on the cog symbol at the end of the address bar. Click on Internet Options in the drop-down menu. This will open a settings window.
- Click on the Advanced tab and scroll down through the list of settings.
- Uncheck Use TLS 1.0 and Use SSL 3.0. Click OK to close the window.
To block Flash in Internet Explorer you need to control the ActiveX settings.
- Click on the cog symbol at the end of the address bar in the Internet Explorer browser.
- Click on Safety in the drop-down menu. If there is a check mark next to ActiveX Filtering in the Safety submenu, this setting is already blocked. If not, click on this line in the menu to activate it.
To prevent PDF files from loading in the browser, follow these steps.
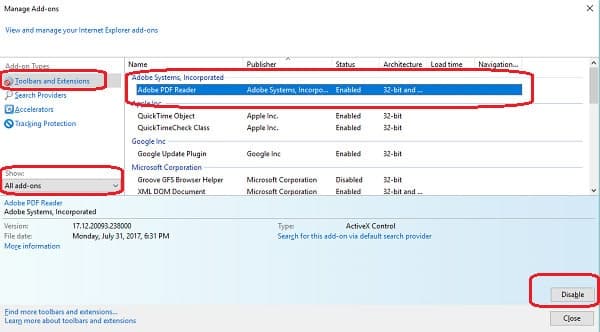
- In Internet Explorer, open the cog menu and select Manage Add-ons. This will open the Add-ons Manager screen.
- Select Toolbars and Extensions for the Add-on Type and pick All add-ons from the Show drop-down list.
- Click on then entry for Adobe PDF reader in the main panel of the screen.
- Click on the Disable button at the bottom of the screen. Click on Close to get out of the Add-ons Manager.
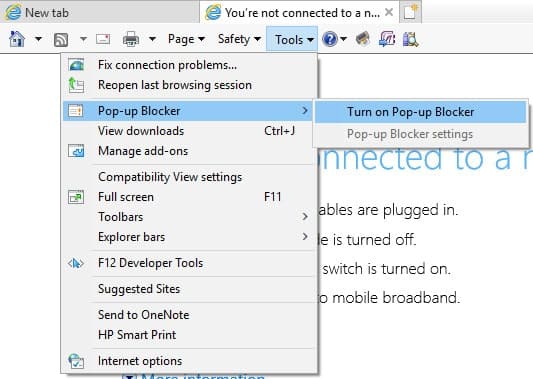
To block popups, you need to look for the Tools menu.
- Click on Tools in the utilities menu at the top of the open tab in Internet Explorer.
- Select Pop-up Blocker in the drop-down menu and then click on Turn on Pop-up blocker.
How to secure Microsoft Edge
You don’t need to worry about SSL backward compatibility in Microsoft Edge, because that option does not exist in this new browser. There is also no option to prevent PDFs from opening in the Microsoft Edge browser.
To stop pop-ups and block Flash in Edge, follow these instructions:
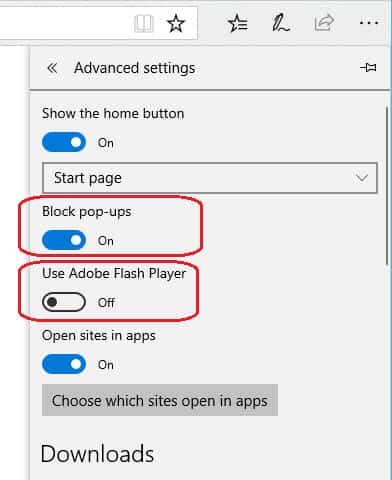
- Click on the three dots symbol at the end of the address bar. Scroll to the bottom of the drop-down menu and click on Advanced Settings.
- In the Advanced Settings menu, set the Block pop-ups slider to On and the Use Adobe Flash Player slider to Off.
How to secure Safari
Safari doesn’t include backwards compatibility for SSL, so you don’t need to do anything about that security weakness. However, here are some actions you can take to make your Safari browser more secure.
- Click on Safari in the top menu bar and select Preferences.
- Select Security and then click on Manage Website Settings.
- Select Adobe Flash Player and choose Block from the When visiting other websites drop-down list.
- Click on the General tab in Preferences. Uncheck Open “safe” files after downloading.
- Click on the Advanced tab in Preferences. Under Proxies, click on Change Settings. This will open a new window.
- Uncheck all the protocol entries. Click OK to exit the Proxies window.
Browser privacy mode
Each browser type has a different name for its privacy mode. However, in each case, this mode performs the same functions. It will delete your private data from storage together with passwords, cached page information, cookies, and browser history once you close the browser window. However, in order to take full advantage of this feature, you must remember to periodically quit the browser.
Here is how to invoke each browser type in privacy mode:
Microsoft Edge privacy mode
Right-click on the program icon and select New InPrivate window from the context menu.
If you already have Microsoft Edge open, click on the three dots symbol at the end of the address bar to get the browser menu. Click on New InPrivate window. You can also open an InPrivate window by pressing Control-Shift-P together.
Internet Explorer privacy mode
Right-click on the program icon and select Start InPrivate browsing from the context menu.
If you already have an IE browser wind open, Press Control-Shift-P together to open an InPrivate browser windows. Alternatively, click on the cog symbol at the end of the address bar to get the browser menu. Select Safety and then click on InPrivate Browsing from the Safety submenu.
Google Chrome privacy mode
The privacy mode of Chrome is called Incognito. If you have Chrome pinned to your taskbar, right-click on the icon and select New incognito window from the context menu.
If you already have a regular Chrome window open, press Control-Shift-N together to open a new incognito window. You can open an incognito window through the menu system: click on the three dots menu symbol and select New incognito window from the menu.
Mozilla Firefox privacy mode
The privacy mode in Firefox is termed a “private window.” If you have Firefox pinned to your taskbar, right-click on the icon and select New private window from the context menu.
If you have a regular Firefox session open already, you can open a private window by pressing Control-Shift-P together. You can also open a private session through the browser menu. Click on the hamburger symbol at the end of the address bar and select New Private Window from the menu.
Safari privacy mode
You can set the preferences of Safari so that it always opens in Private Browsing mode. To do this, click on Safari in the top menu bar and select Preferences. Under the General tab, click on Safari opens with and select A new private window.
If you already have a Safari session open, Click on Safari in the top menu bar and then select Private Browsing from the drop-down menu.
Malicious extensions
Malicious browser extensions are very difficult to spot. As we grow accustomed to smartphone apps telling us that they want access to data sources such as phone contact lists, we become desensitized to all the requests to access the operating system and data held in other apps. This has become a common occurrence in bona fide browser extensions and, as Zach Miller of online security firm, Cyberpoint explains, people tend to continue with the installation of a browser extension even when the browser points out the security risks.
Browser extensions have a surprising amount of power and control over a browser and the content that is displayed. An extension can inject scripts into rendered pages, create, redirect, or block web requests, or steal information that is entered into online forms.
-Zach Miller, Cyberpoint.
The system and services access that many legitimate browser extensions require really should make you stop and think before adding any extra functionality to your browser, no matter how useful and respectable it may seem.
Some malware uses browser extension functionality to hijack browsers. In January 2018, antimalware company, Malwarebytes reported on a clickjacking worm that directs victims to YouTube pages against their will. This malware extension is called Rogue.ForcedExtension and the Chrome and Firefox extension that it operates through is called Tiempo en Colombia en Vivo. You may think that you would be safe from this malware simply by choosing not to install that extension. However, none of the victims of this malware knowingly chose the extension. To this date, it is not known which action gets this extension installed.
Worse still, malicious extensions are able to defend themselves from removal. They can block access to the extensions and add-on management pages and redirect you away from searches in how to combat these forms of malware. Basically, once malware extensions get onto your browser, they are not going to let go.
Some malware extensions advertise themselves with the same name as legitimate utilities. Many of these fake extensions even manage to make it onto the Google Chrome Web Store.
Regular and recommended extensions can get hijacked. You might read good reviews of an extension and decide to install it. However, on installation you will be warned that the extension will be able to read and change your data on the web, read and change your browser history, modify text in your clipboard, and change the settings of your browser.
Although you may have trusted that company at that point, that trust should not be ongoing.
Chrome and other browsers will automatically update the extensions you have installed and they remain active without you knowing that the program has changed.
If the permissions required by the extension have changed with the new update, then the browser will disable that extension until you have approved the permission changes. The default requirements for system access that extensions regularly ask from you are more than enough for a hacker to get malware onto your system.
This makes extension updates a really easy route for hackers — not only do they piggyback on the large user base of popular extensions, but they only require one file to be uploaded to a server in order to proliferate millions of computers and phones. An example of this phenomenon occurred with an update to the Web Developer extension in August 2017. A hacker managed to get his own version with malware onto the update server, thus downloading his malicious software onto more than a million computers.
Another danger with useful browser extensions is that they are often developed by small companies or individuals that make no money out of them. Ask yourself, how often do you pay for a browser extension? The low income that developers derive from these facilities makes them vulnerable to offers to purchase the system.
Hackers and darkside marketers generate a lot of income from ransomware, DDoS-for-hire attacks, and pay-per-click marketing scams. It makes sense for them to reinvest some of that revenue into buying access to millions of computers for very little money. They only need to update that excellent utility by inserting a little bit of extra code, and their scam is installed automatically as a legitimate browser extension update. This is exactly what happened when the browser extension Particle for YouTube was sold off in July 2017.
Given that extensions are ongoing security weaknesses in your browser, it is better to practice caution and try to avoid adding them.
Security extensions
After you just read advice not to install browser extensions, it may seem odd that this next section gives recommendations on extensions you should install. However, these extensions will help you improve the security of your browser, rather than impair it.
Although it is possible to block tracking software in your browser settings, these options are not very comprehensive. It is better to install extensions in order to fully block tracking codes. Many tracker blocking extensions also block adverts. Standalone ad blockers are also popular with web surfers.
Blocking JavaScript is also a good idea. Although there is the option to prevent JavaScript from running in Chrome, the implementation of JavaScript blockers as extensions generally works better.
Other security extensions listed in this section include systems to generate passwords for you so you don’t make the mistake of using the same password for all of the sites that you visit. You can also read here about extensions that will check the security of the pages that you visit.
HTTPS enforcement
As explained above, the HTTPS schema protects your data during transfer. However, not all sites use HTTPS and those that still use HTTP don’t offer very good security.

Browser Cleaners
It is possible to delete all cookies and temporary storage from all browser types. If you use the privacy modes that the browsers offer, then you don’t need to delve into the settings of your browser to clean out all of that data. If you are not that keen on the idea of using privacy mode, you can install a browser cleaner to get rid of all of that hidden information for you. Even if you do use privacy modes, not all records of your site visits are deleted when you close the browser.
Here is a selection of data cleaners.



JavaScript Blockers
Web pages are written in a code that is called the Hypertext Markup Language, or HTML for short. HTML only contains instructions for formatting text. It is not a programming language. However, it is possible to embed scripts in HTML code, and scripts include programming constructs. JavaScript was invented to enable small programs in web pages.
Those little bits of programming code are all that a hacker needs in order to download a gateway program on your computer or manipulate the operating system in such a way that rootkit programs can get in and control the functions of your operating system. You need to block JavaScript from running in your browser.



Password protection
One of the easiest ways that hackers can get into your email account or other online services is to just try some of the standard weak passwords, which include “1234567890,” qwerty,” and “password.” You not only stand to compromise your privacy to hackers through weak passwords, but these are also a gift to stalkers and former friends.
You need to use more complex passwords for each of the sites that you visit and you need to make the password for each site unique. This task can be difficult to manage. You will find it difficult to remember the password for each site and keeping all of your passwords on a piece of paper in your computer or phone case is another bad idea.
Password vaults (also called password managers) solve the problem of knowing what constitutes a strong password and they also enable you to generate a different password for each site that you use. A password vault browser extension will store all of your passwords, so you only need to remember the master password for the vault. When you go to a site that has a password stored in the vault, the extension will fill in that field for you. Here are some of the best password vaults available right now.
 LastPass is available for Internet Explorer, Microsoft Edge, Chrome, Firefox, Opera, and Safari. This is a comprehensive security system that protects your identity. The free version of this utility gives you a password vault, which can generate passwords for you, making sure that you have a unique password for each site that you visit. Passwords are stored in the Cloud, but communications with the password vault are encrypted to prevent disclosure. This makes all of you passwords available to you no matter where you are and what device you log in through.
LastPass is available for Internet Explorer, Microsoft Edge, Chrome, Firefox, Opera, and Safari. This is a comprehensive security system that protects your identity. The free version of this utility gives you a password vault, which can generate passwords for you, making sure that you have a unique password for each site that you visit. Passwords are stored in the Cloud, but communications with the password vault are encrypted to prevent disclosure. This makes all of you passwords available to you no matter where you are and what device you log in through.

There is a free version of Blur that doesn’t include the above two services, but it still creates a very comprehensive online privacy service. There is a password manager module in blur that is every bit as complete as the service offered by LastPass. The utility also includes a browser fingerprinting prevention system. Tracking by social media buttons is blocked by Blur and the system also includes a tracker and ad blocker.
You can get an email address from blur to use when you sign up for online services. The mail sent through to that account is forwarded on to your regular email address. This ensures that you are very difficult to trace online.
Blur is available in both free and paid version for Internet Explorer, Chrome, Firefox, and Safari.

Tracker blockers
Retargeting has become a major marketing tool on the web. This method puts a little marker on your computer in the form of a cookie when you visit a website. Trackers usually go hand in hand with targeted advertising.
If you visit a website that participates in retargeting, you will notice that many of the subsequent sites that you visit display ads for that site or service. This is enabled by the website checking for one of its advertising service’s cookies on your computer before it loads content into the advertising panels on the page. Google is one of the biggest operators of retargeting advertising and it has developed the method into a very lucrative income stream.
Social media buttons and website analytics tools also practice tracking.
Although some argue that trackers enable people to see ads that they will find useful, rather than just promotions for random services, this method creates a privacy issue and the secretive way that retargeting is implemented angers many. Although businesses may claim that the method is only used for targeting adverts and no information about visitors is collated, marketers are notorious for monitoring the performance of ad campaigns and use trackers to gather data on your internet activities as much as they use them to deliver adverts.
The technology behind retargeting provides an excellent avenue for snoopers and data gatherers. The selective delivery of ads can be hijacked by browser viruses to earn hackers money and they can even be used to redirect your browser to show substitute pages rather than the sites that you thought you were visiting. All in all, it is better to block tracking libraries.
All the major browsers now include settings to allow you to enable tracker blocking or to send a “do not track me” request. However, knowing that retargeting is a major source of revenue for very large corporations, those browser developers didn’t really make their blocking systems completely foolproof. For example, Apple made its tracker blocker in Safari so that it allowed the trackers, but deletes them after 24 hours if you don’t visit any page on the same domain within that period. Rather than blocking tracking, this methodology gives a supreme advantage to the two biggest retargeting systems that are run by Google and Facebook.
Tracker blocking is better when it is implemented by extensions rather than by relying on the settings in your browser.




Ad blockers
As explained above, retargeting, with the use of trackers, has become a major technique for advertisement management used on the web. The tracker blockers will prevent retargeting agencies from loading the adverts of their clients in your browser because the delivery processes won’t find any of those essential tracking cookies on your computer.
Tracker blockers are often advertised as tracker and ad blockers. However, they usually focus on blocking ads that use tracker codes and that doesn’t cover all online advertising. It is better to use both a tracker blocker and an ad blocker.


Security checkers
If you can live without all of the above extensions then just focus your attention on this category.
The extensions in this category will examine the contents of the web pages that you visit and give you reports on the trackers and other privacy and security weaknesses that each page includes. In the case of CyberSec and Secure.link, the extension will prevent your browser from encountering dangerous web pages.

If you are not a web programming or networking expert, you may find these details a little overwhelming. However, once you become familiar with the report format that is displayed in the extension’s drop-down panel, you will learn to graze the information made available to focus on the important bits.

The extension also monitors for botnet activity. Even if your computer has already been infected, CyberSec will block your communications with the Command and Control mechanism that launches attacks on other computers. This extension will also block trackers, pop-ups, ads and videos. The NordVPN browser extension is available for Chrome and Firefox.

The secure.link system is also integrated into the Windscribe VPN browser extension where it give you the option to generate a safety report on every page that you visit on the web.
This extension also includes an ad blocker, a cookie cleaner, and a tracker blocker. Another feature will scramble your browser’s user agent information to prevent browser fingerprinting and you can also elect to let the extension strip out social media buttons. The Windscribe browser extension is available for Chrome and Firefox.
Online protection
As an entry point to the computer from the internet, your browser is one of the most vulnerable pieces of software that you have on your computer.You canblock off the avenue of attack into your computer by using an online service called a VPN. You will probably remember that there have already been three VPN services mentioned in this guide: TunnelBear, Windscribe, and NordVPN. All three services can be operated through an app or through a browser extension.
A VPN establishes an encrypted link between your computer and the VPN server. Going out from the VPN, all of your traffic has that server’s internet address on it and not yours. The VPN software on your device takes control of your network card, so no internet communication can get into your computer unless it first passes through the VPN server. This adds massive security to your browser as well as other apps that use the internet.
Stay safe on the web
Being very selective about the extensions you install is probably the best way to keep your browser secure. Make regular checks on the proxy and DNS server settings of your browser to ensure that your internet traffic is not being hijacked. Also, make sure that your browser updates automatically to keep up with the latest version and install a good antivirus program.
Now you are aware of the potential threats to your browser, you will be better equipped to prevent intrusion and modification. Enjoy the web, but be cautious about what you download and what you install.









nice